So I’ve run into a problem lately. I’ve got access to O365 and Office 2003 for my malware lab. O365 lets me execute most current malware, and sometimes I have to pull out Office 2003, like with a recent Racoon Stealer sample. However I’ve had a spat of malware documents and excel sheet over the past year exploiting CVE’s such as 2017-11882 and 2018-0802 requiring the Microsoft Equation editor software. If you remember this was the software package Microsoft admitted to having lost the source code to and having to directly patch the binary. Even after patching additional vulnerabilities were found this led Microsoft to just kill Equation Editor all together and remove it from the Office suite.
This has led me on a strange hunt asking friends and family for old, but not too old copies of Office to be able to execute malware taking advantage of the vulnerabilities from 2017/2018. Well as of today, that’s not an issue anymore as I found out how you can reintroduce the old vulnerabilities into O365 and get that juicy malware execution information. While I know I could just toss the malware to sandboxes like hybrid analysis or any.run I find that running it yourself in a lab produces more data and can reveal things that just don’t happen in modern sandboxes.
Let’s take a look at this sample from this week.
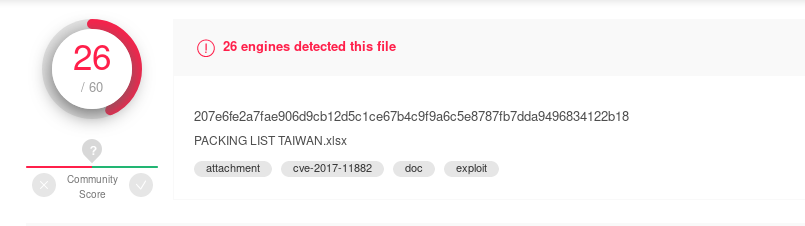
207e6fe2a7fae906d9cb12d5c1ce67b4c9f9a6c5e8787fb7dda9496834122b18
Mine was named ‘SOA AS AT 29 FEB. 2020.xlsx’. We can see using olevba that no vba’s exist in the suspicious document.
olevba 0.55.1 on Python 3.7.6 - http://decalage.info/python/oletools =============================================================================== FILE: SOA AS AT 29 FEB. 2020.xlsx Type: OLE No VBA macros found. =============================================================================== FILE: /tmp/oletools-decrypt-ec53peo_.xlsx in SOA AS AT 29 FEB. 2020.xlsx Type: OpenXML No VBA macros found.
The Virustotal data indicated CVE-11882.
We have excel 2003, but that can’t open xlsx format, and O365 has equation editor removed, so let’s learn how to unpatch our Office suite.
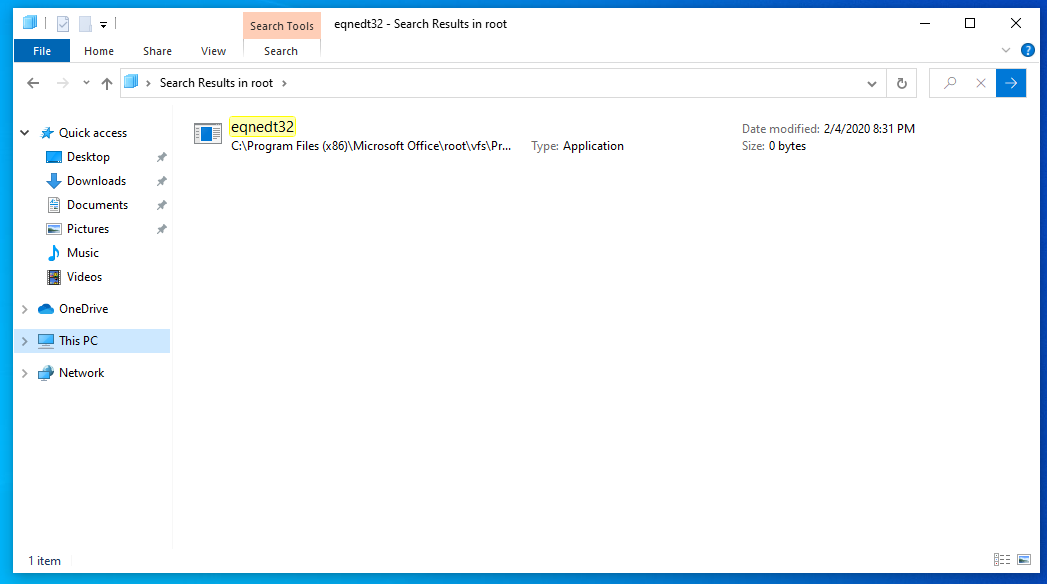
So if you install a fresh copy of O365 you should be able to find a 0 byte file present in the file system. This is the first step, locating that file.
Here you can see it under:
C:\Program Files (x86)\Microsoft Office\root\vfs\ProgramFilesCommonx86\Microsoft Shared\EQUATION\
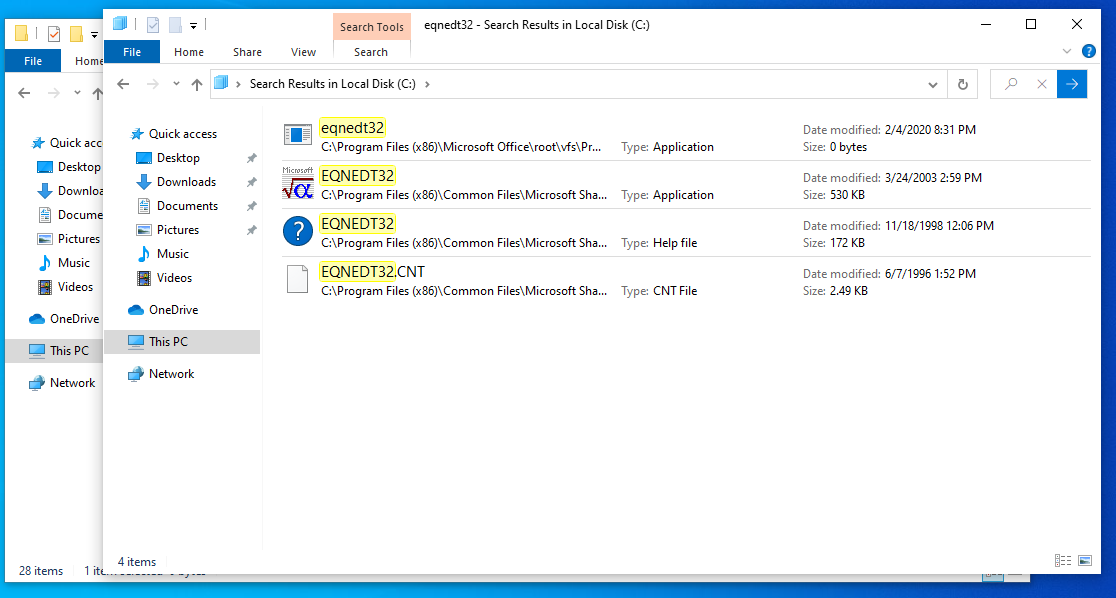
This is the fresh install of O365 on my lab machine, but I also have Office 2003 installed, so lets locate that version’s equation editor. We can see that other version’s application is still good to go.
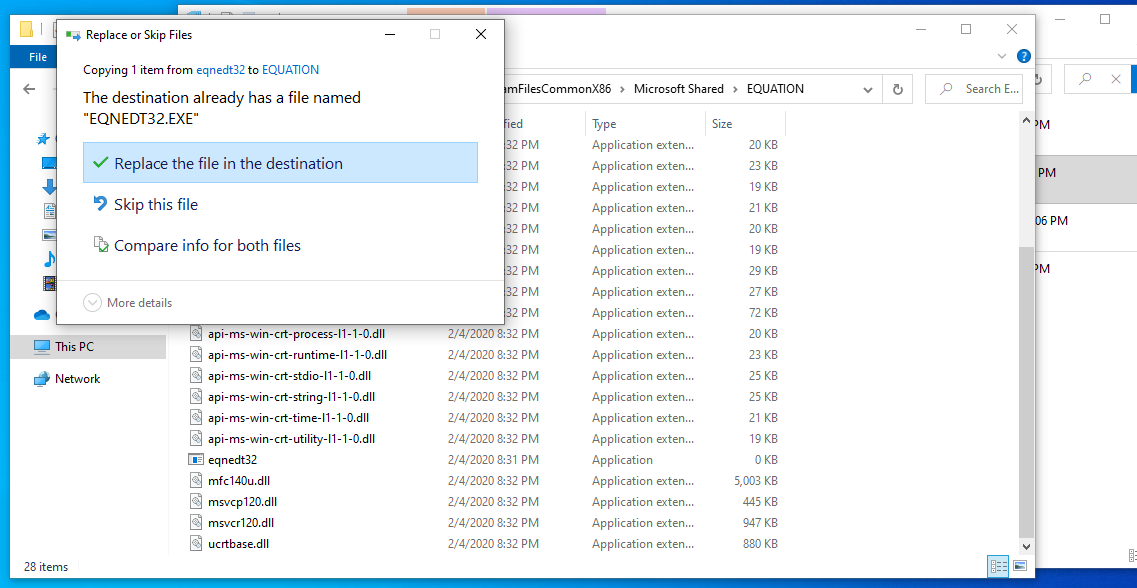
Now you might be thinking, it can’t be as easy as I am about to explain. I didn’t believe it myself at first, but yeah its this easy. Copy the old Office 2003 application over the 0 byte file. That will reintroduce all the old vulnerabilities…
Voila O365 exploited by equation editor!
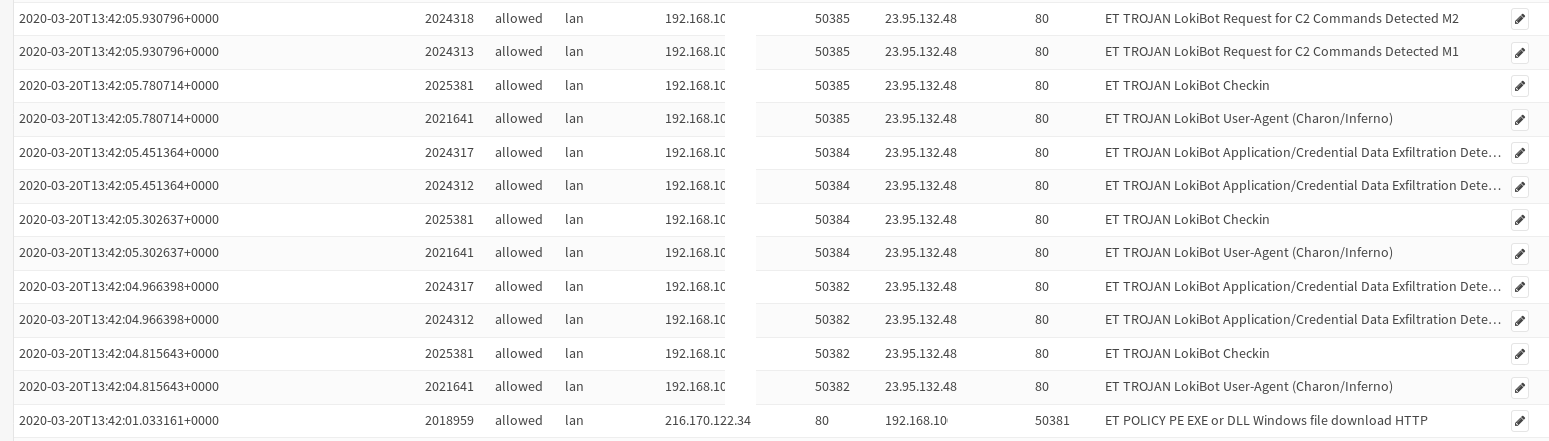
Turns out this sample brings down Lokibot.
Fill MISP event available here: https://github.com/Hestat/intel-sharing/blob/master/lokibot-03-20-20/misp.event.35116.json
IOCs:
23.95.132.48 216.170.122.34 SOA AS AT 29 FEB. 2020.xlsx|71f2c5eb6d2e98447d1716cacba2b561 71f2c5eb6d2e98447d1716cacba2b561 87fa9e824272c8ef8c465b589362b8a13941f403 207e6fe2a7fae906d9cb12d5c1ce67b4c9f9a6c5e8787fb7dda9496834122b18 vbc.exe|588f7435c0f60c626ef1aa6686d498c3 588f7435c0f60c626ef1aa6686d498c3 8ae273618ff5a22bf2ee880d6ce8327aa8a1a4ba d04f19307af75f77ec2e418bc6a16454906b93f1117fc5b4ba84a73764b089c4 http://shgshg9nationalobjwsdyindustrialgoogler.duckdns.org/shgdocument/vbc.exe http://23.95.132.48/~main/.isuoxiso/w.php/tOEYLz76bbT79