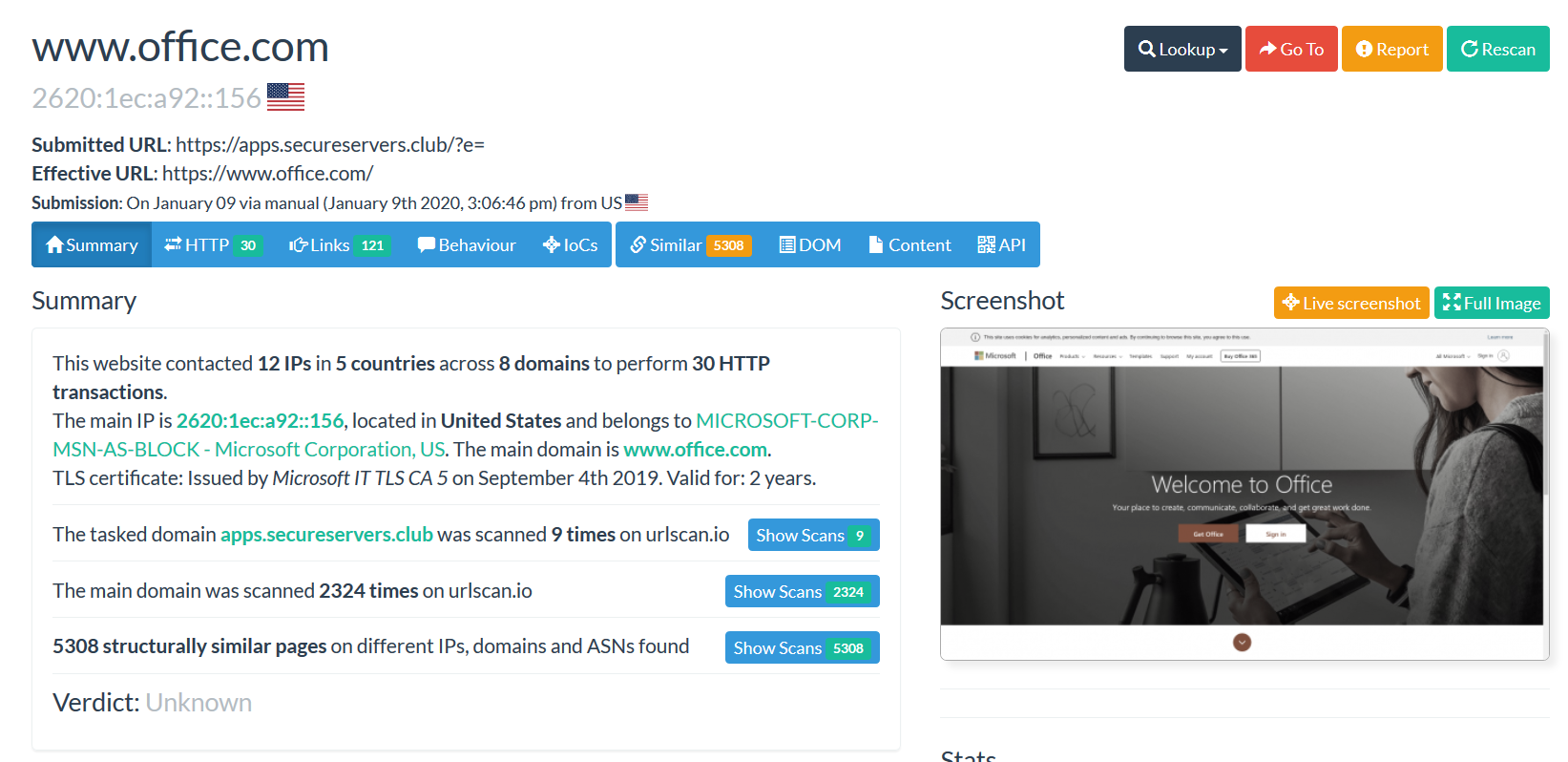
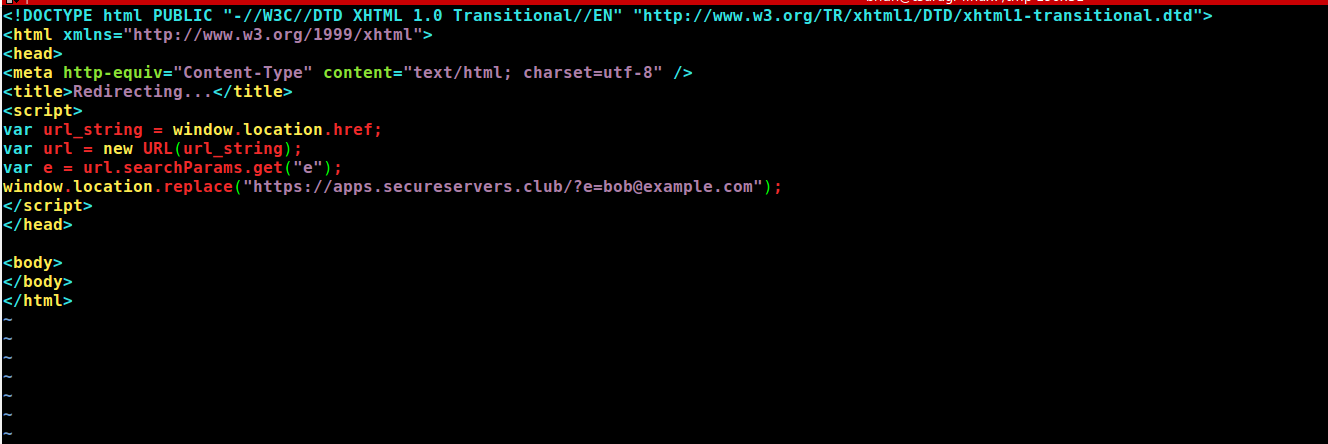
Last week we came across an increase in captured messages in one of our phish trap mailboxes and decided to look further into the cause of the increase. Upon extracting the phishing domain using our scripts we submitted the URL to standard automated scanning services. It was there that we got the first hint that more sophistication than the average phish was present. Often phishing kits use the URI to include the email of the intended recipient to prefill the phishing page with that address. Most of the time you can strip that and the kit will still load just with the username field blank. In this case removing the email from the URI resulted in a redirect to office.com, a common tactic for phishing kits to perform post credential capture but rarer pre-capture.
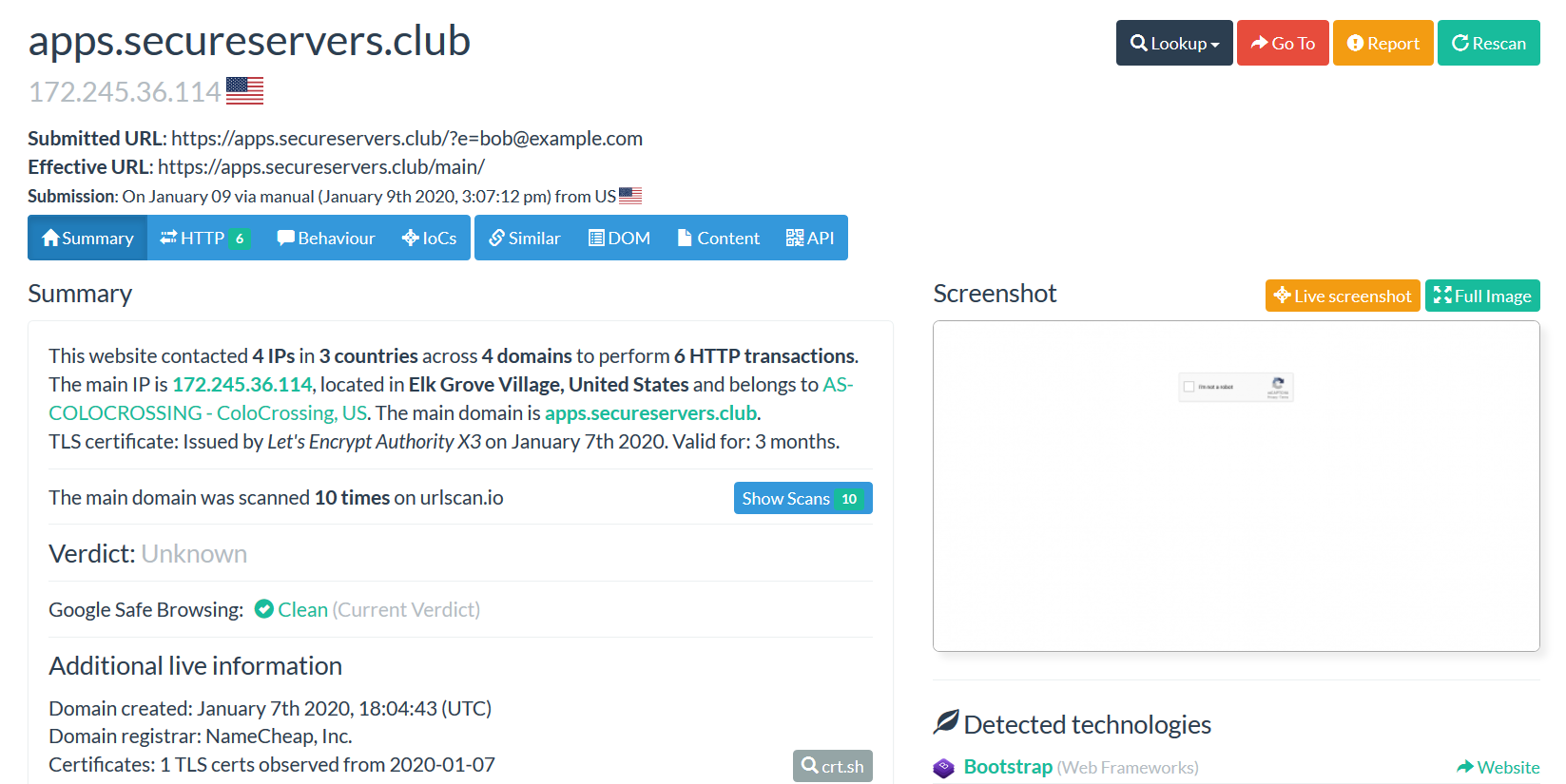
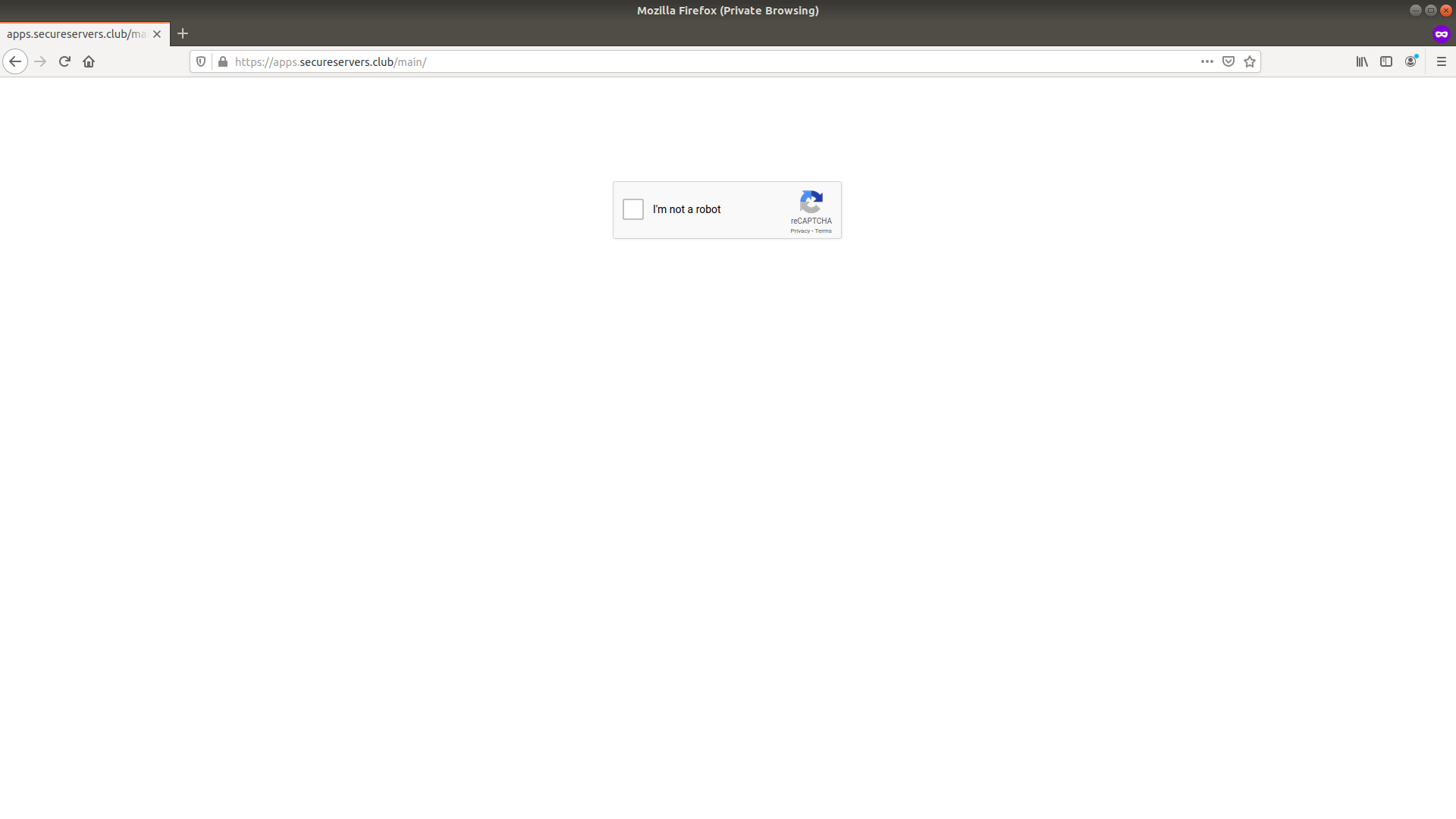
So then we submitted a second scan using a fake email address and had a new surprise. The screenshot for the phishing page now showed that a reCaptcha needed to be passed before we could see the phishing kit.
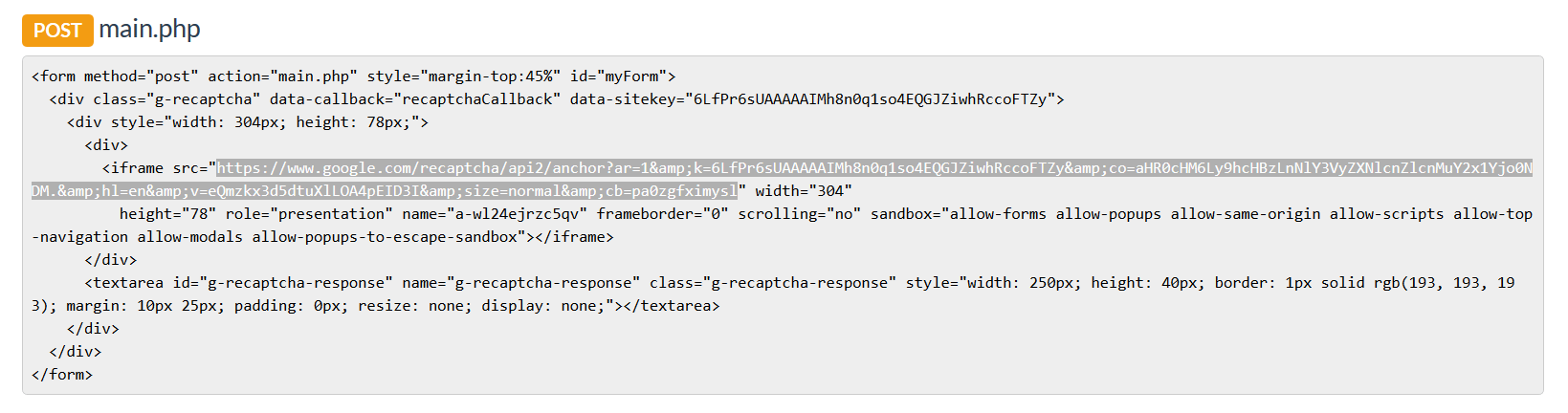
Analysis of the site code reveals that it is indeed using the legitimate google reCaptcha system, and while there have been many reports of usage of fake reCaptcha linking into the actual reCapcha system seems to be a more recent and rarer affair. (ex. https://cofense.com/new-phishing-campaign-uses-captcha-bypass-email-gateway/)
Let’s take a walk through filling out the phishing info to see what a user would see.
Step 1 the user opens the attachment, this should immediately cause a redirect to the phishing site.
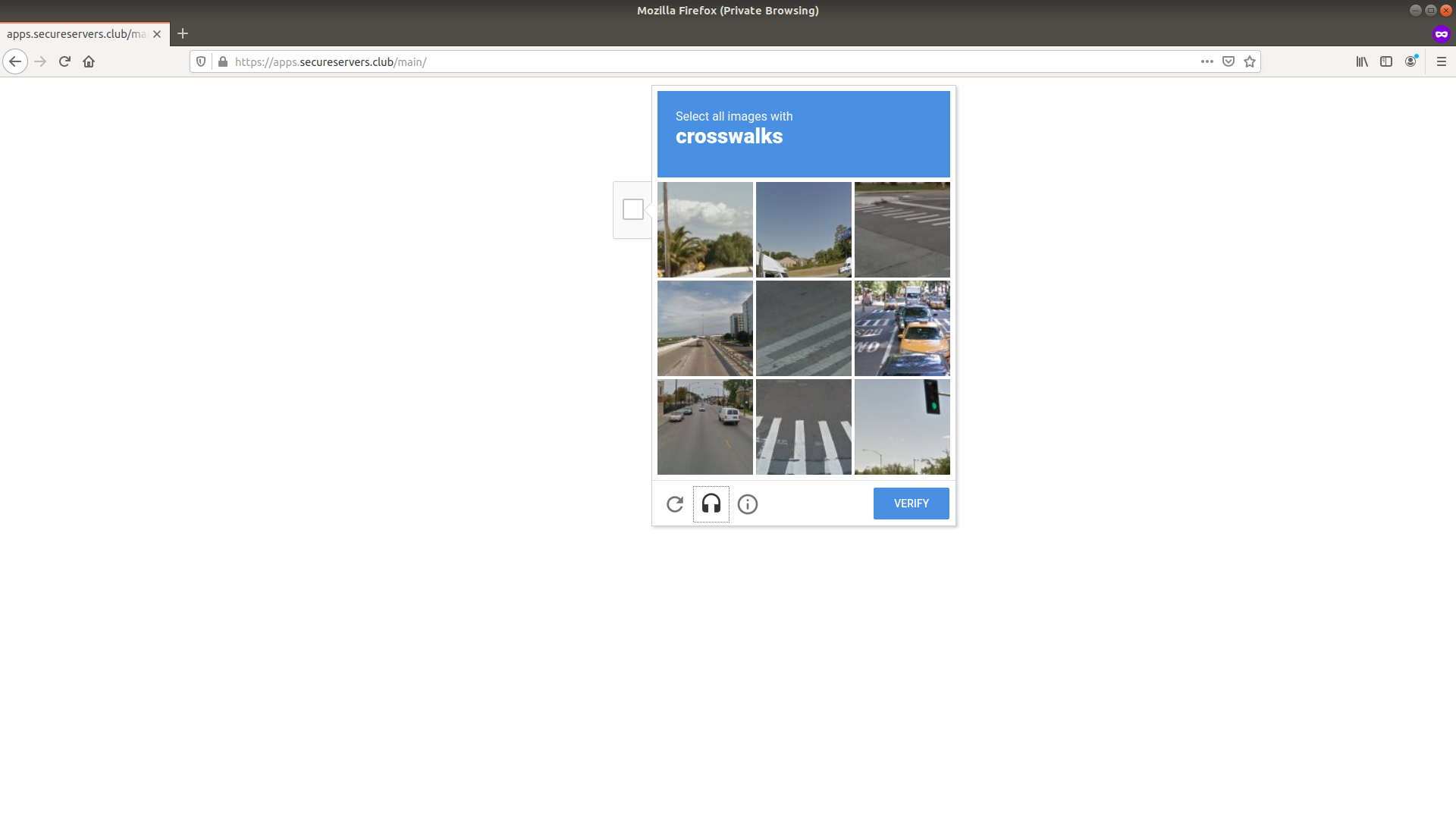
Step 2 the user is greeted by the Google reCaptcha.
Step 3 the user then has to complete the reCaptcha challenge.
Step 4 upon completing the reCaptcha the user is delivered to /main.php and prompted to enter their credentials. The credential are then sent with a POST request is sent to /action.php.
Step 5 The user is presented with a prompt indicating an error, we assess that this is likely to capture the password twice to confirm the user entered it correctly.
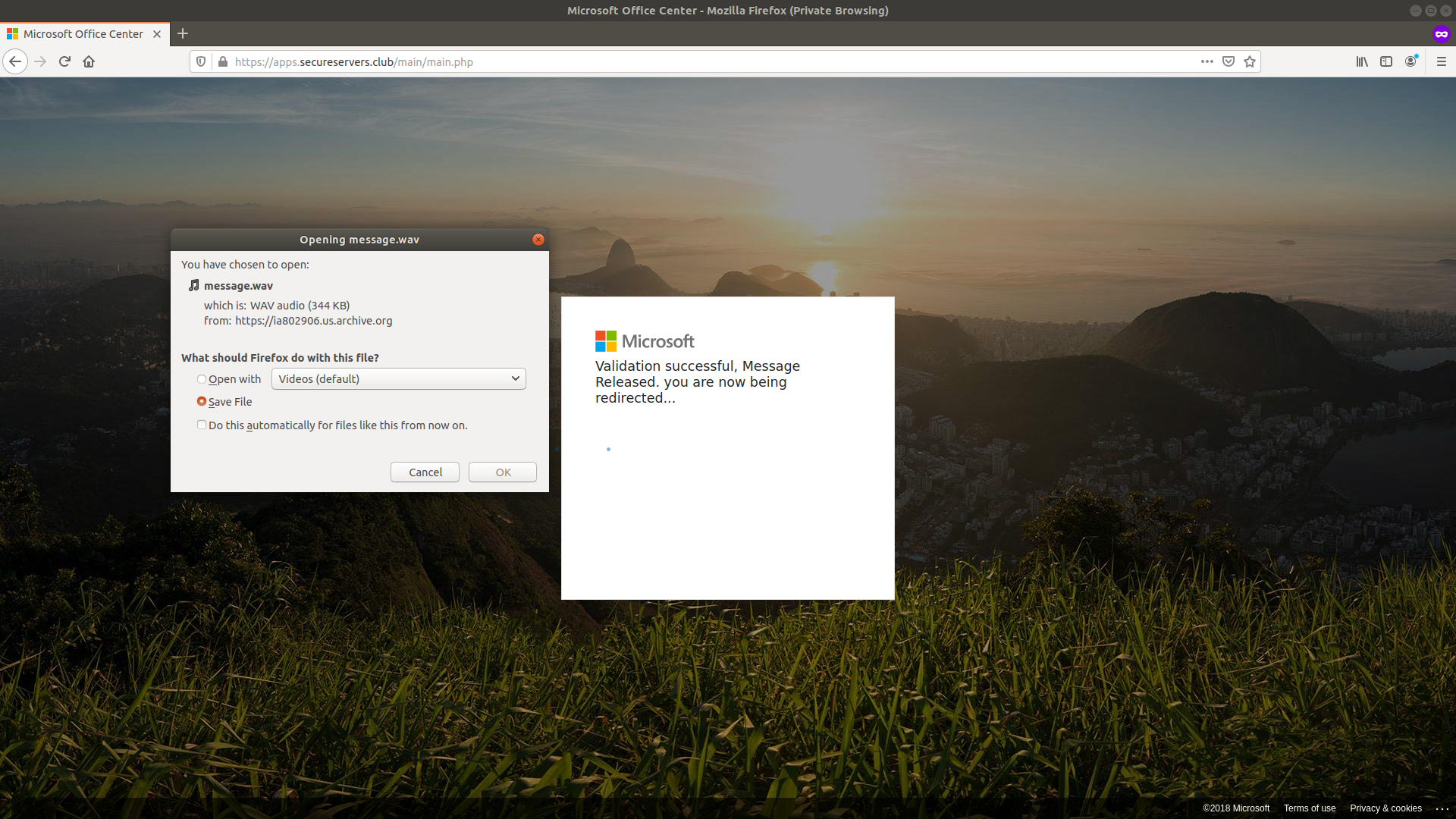
Step 6 After entering the information the user receives a wav file pulled from archive[.]org that actually contains a voicemail returning a sales call about office supplies.
With the way this kit was deployed we assess that it has a pretty high likelihood of being able to social engineer many users. With the combination of Google reCaptcha, Microsoft graphics, delivery of an actual voice message, trusted SSL certificate, analysis evasion, realistically the only thing that they really missed on was the domain, with a TLD like .club this may allow users to pick up the deception, but if executed with azurewebsites, windows.net, or similar legitimate services to further mask the source it could be a very effective attack.
Full MISP event available here: https://github.com/Hestat/intel-sharing/blob/master/club-phish-recaptcha/misp.event.7949.json
IOC’s
apps.secureservers.club https://apps.secureservers.club/?e= https://apps.secureservers.club/main/main.php https://apps.secureservers.club//main/action.php 172.245.36.114 http://notmsg.esms1.xyz?e= http://notmsg.esms1.xyz/main/main.php http://notmsg.esms1.xyz/main/action.php 192.119.111.226 https://msgvoip.esms1.xyz/main/action.php https://msgvoip.esms1.xyz/main/main.php https://msgvoip.esms1.xyz/?e= msgvoip.esms1.xyz https://audionote.vsms1.xyz/?e= https://notevoip.vsms1.xyz/?e= https://voicmg.vm-c.xyz/?e= https://geraldojuniorpalestrante.com.br/?e= https://apps.extensioncalls.online/?e= https://voicemanager.businessconnects.online/?e= 107.174.253.208 162.241.203.20 192.3.1.146 192.119.111.230 104.168.136.214 apps.extensioncalls.online geraldojuniorpalestrante.com.br notmsg.esms1.xyz voicemanager.businessconnects.online www.geraldojuniorpalestrante.com.br app.audioserv.club mail.seversync.club ted.mecoreing.com voice-app.audioservice.club voiceapp-resource.msvoicewave.club voip.vpreviews.club