So I investigate a lot of compromised WordPress sites. Pretty much all of these investigations end in one of two places for a cause. Out of date software and/or plugin, or a password compromise.
Unless you have been under a rock, you know that data breaches containing user names and passwords are a very common occurrence. And due to password reuse these data sets often allow attackers to continue compromising linked accounts for some time after a breach.
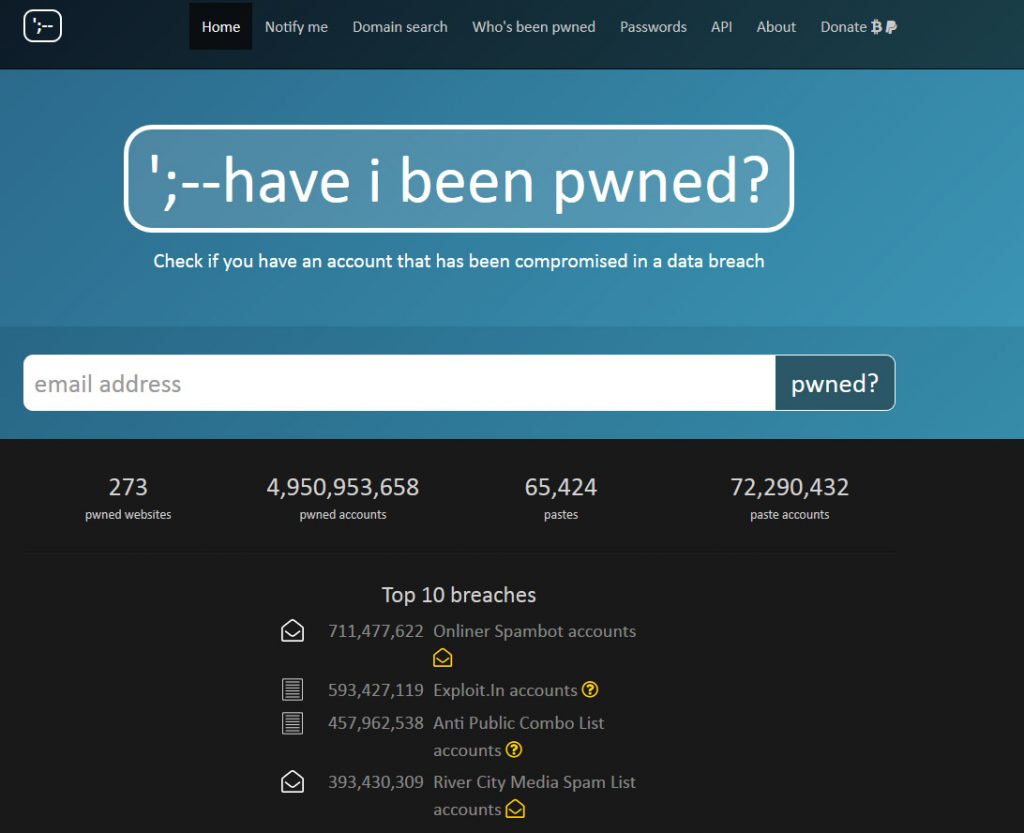
To help individuals learn if their accounts have been in major data breaches Troy Hunt has for a few years now been running a service call haveibeenpwned.com(HIBP). This site allows you to supply an email address and it will check among all known data breaches to see if that email address has shown up in the dumps. Troy has refined the server now so that you can check passwords against an API to let you know if a password that you use has shown up in a data breach. Many enterprising developers have been working to add this API to many different software products.
This week I came across a new plugin for wordpress called Passwords Evolved(https://wordpress.org/plugins/passwords-evolved/) by the developer Carl Alexander. Looking across the code, it looks to implement 2 features quite well. One is it interfaces with the HIBP API to protect accounts from using a previously compromised password. Here’s what that looks like in action.
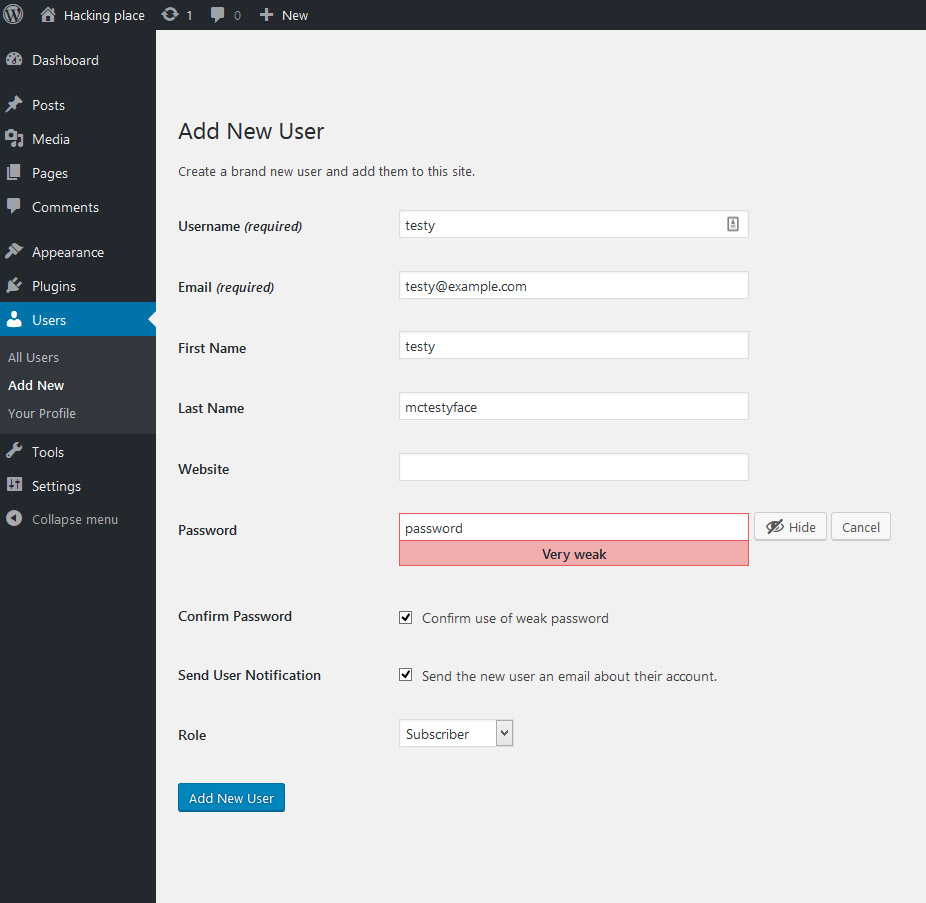
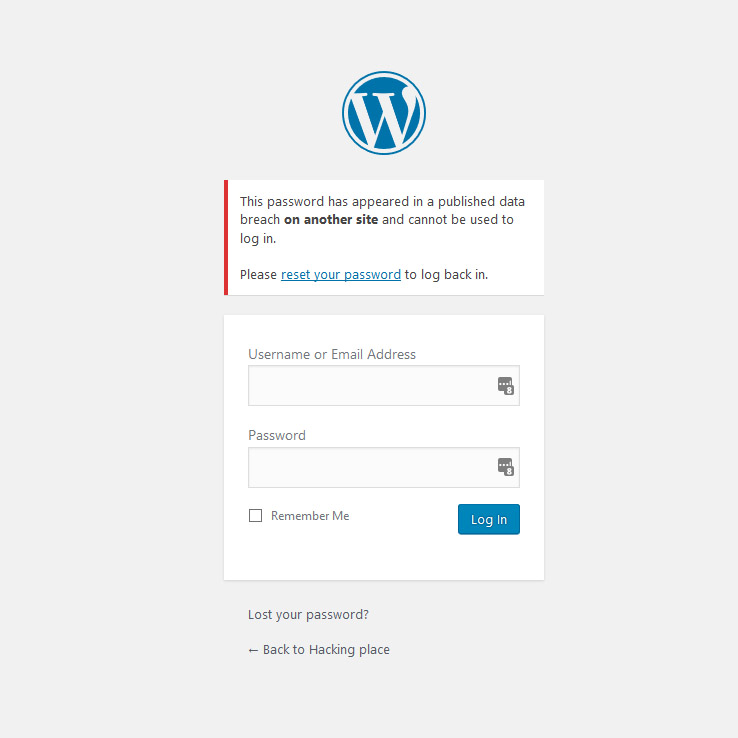
Here’s our user using a pretty insecure password….After adding the Passwords Evolved plugin here’s what the user would see trying to login with said insecure password:
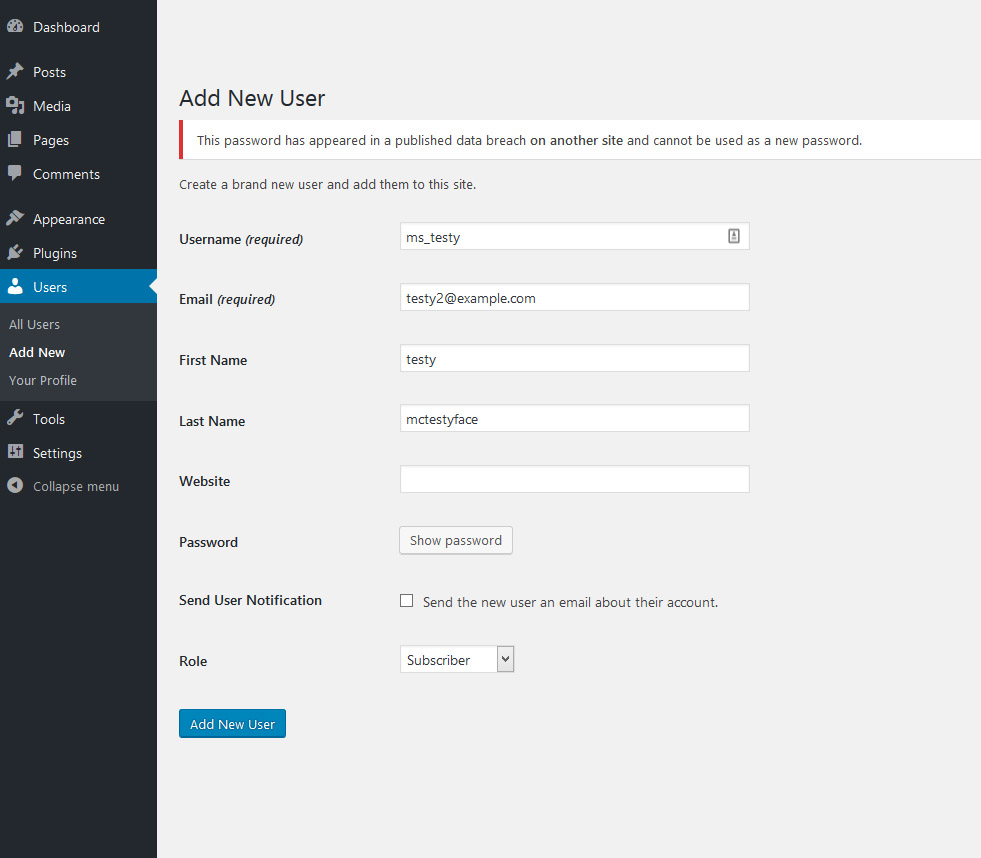
Should a user try to choose a compromised password after the plugin is activated:
But this only part 1 of what the plugin does, its second feature is that is provides a higher level of protection of passwords stored in your password database. By default wordpress still uses the md5 hashing algorithm to protected store passwords, it does provide a salt and performs multiple rounds but the use of md5 makes this a risk should a malicious actor gain access to the database. The current best practice to store passwords is by using bcrypt instead of md5.
This plugin will update passwords stored from md5 to bcrypt the next time a user logs in increasing the protection should your site be involved in a database leak.
Here’s an example in what the 2 formats look like:
md5 stored password:
$P$BJVHSpuC9s25RyfyGiV4smDSXAzz3j.
bcrypt stored password:
$2y$10$DYiJ8i3i16NMoXH8J1ZKq.db4wwg7kfOXyffargICPo3R3vFPCmMS
As any good security person will tell you as password length grows the time required to crack grows exponentially.
So I plan to add this to my list of security best practices for WordPress sites, I’d recommend the same for you.