So I have done a few write ups on the prevalence of malicious crypto-mining on servers. These previous write ups have mostly focused on Monero (XMR) as this has been the currency of choice do to the ease of mining due to the Cryptonight algorithm. However over the last few weeks I’ve seen an new crypto currency starting to gain favor in infections. That is Sumokoin.
Well no surprise…Sumokoin is a fork of Monero… I suspect since it takes advantage of the same cpu friendly mining algorithm, but it is a fresh start we’ll see more of these miners show up as the crypto currency is much easier to mine right now even if the current price of the coin is much lower the the price of Monero currently.
Let take a look at how this shakes down.
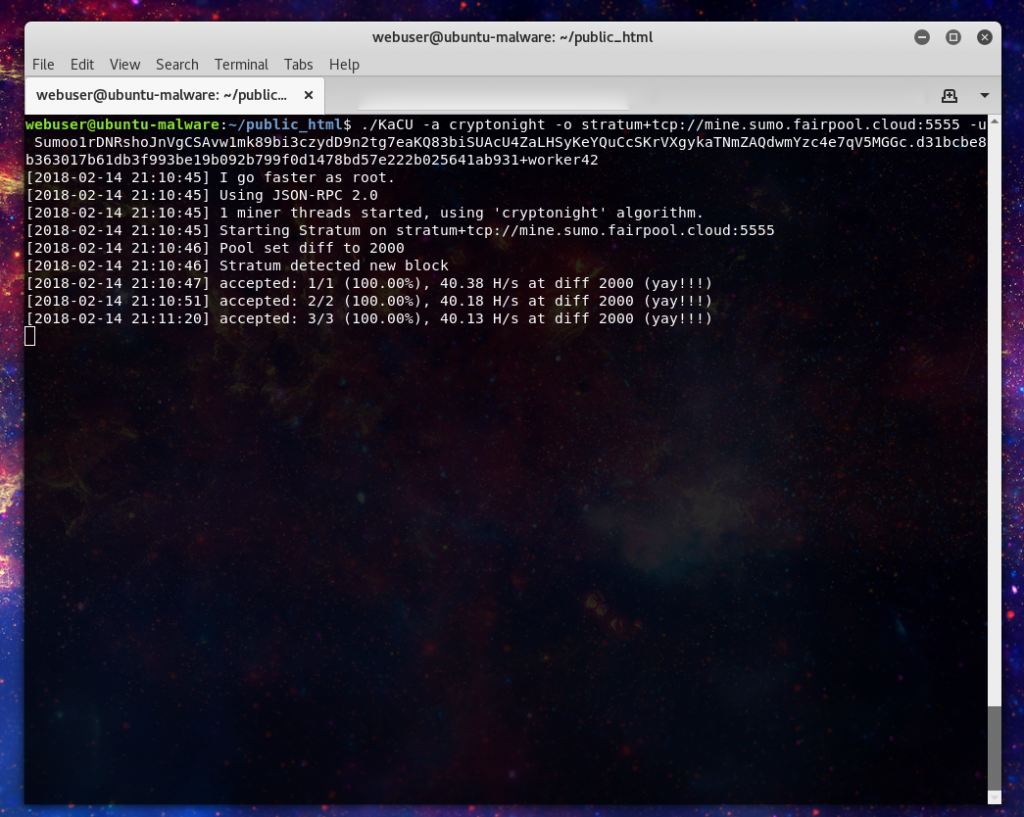
So first up we see the same kind of miner programs being used, in this case the YAM miner which we have seen in use for Monero mining.But here we can see in very short order hashes accepted compared to the much lengthier reward cycle for crunching for Monero. The pool that has appeared in the recent samples has been again and again mine.sumo.fairpool.cloud. The pool for public access resides at sumo.fairpool.cloud.
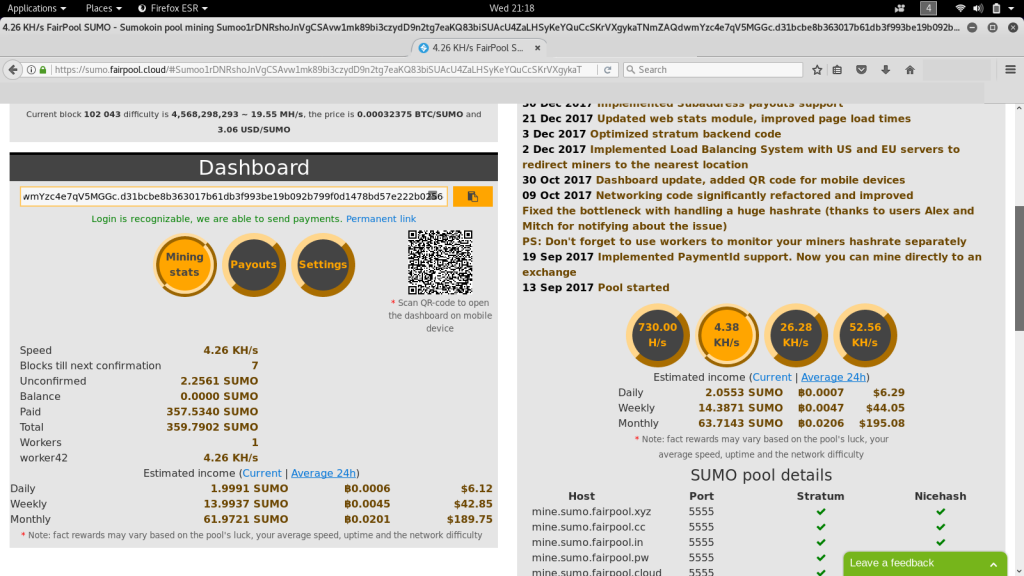
Here like at other pools you can query the rewards by dropping in the public key used in the miner config.
Here we can see that the reward for our little malicious miner here has been 359 Sumokoin, or around $1,177 USD as of the time I pulled the stats.
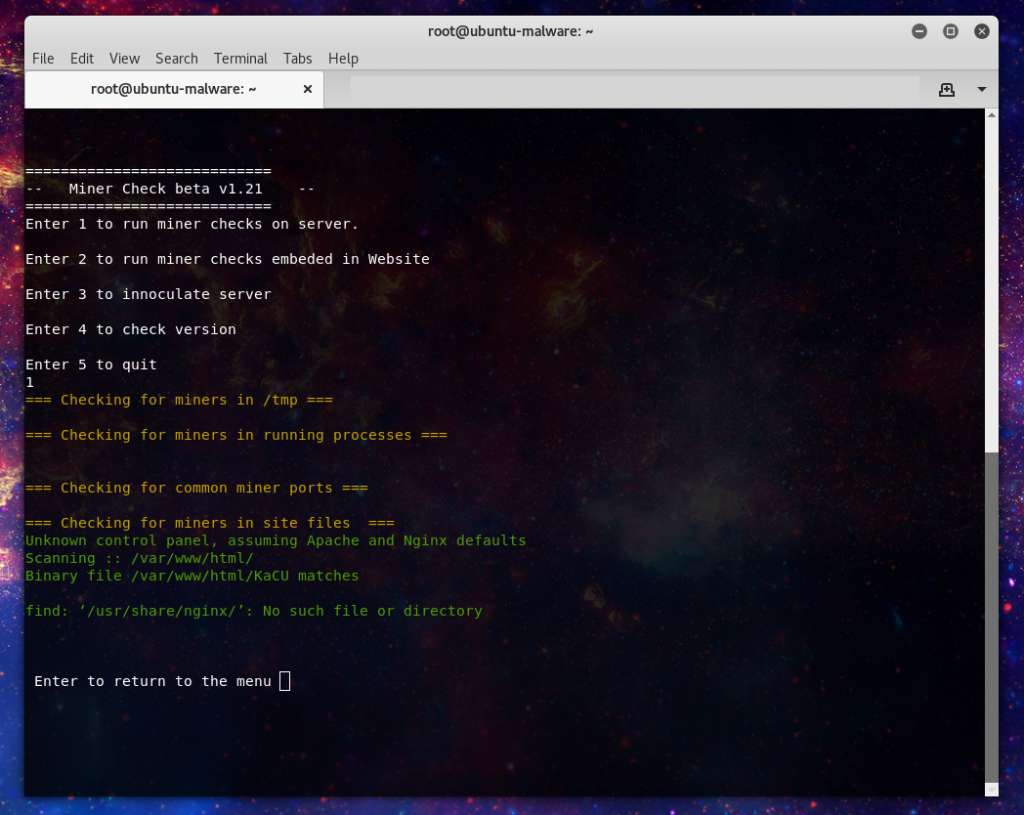
As usual I have taken this info and included it in the latest release of Minerchk, the tool for locating and preventing malicious mining on linux servers. The pools have been added to blacklists, and now if your server is using the Config Server Firewall I’ve included an update to use that to block access the mining pools that are included in minerchk.
Have questions or want to report miners you’ve seen hit me up on twitter @laskow26.