So after investigating hundreds of compromised websites, you begin to get a feel for what malware is pretty garden variety, like if I see another WSO shell, color me extremely unsuprised. But every once in a while something novel shows up. This is one of those.
This little piece of code, was both simple and brilliant in its purpose. It targets WordPress sites as a persistence mechanism. In its simplicity it still play pretty well in keeping a malicious actor in to the victim machine and is not detected by any AV as of current date testing on Virustotal.
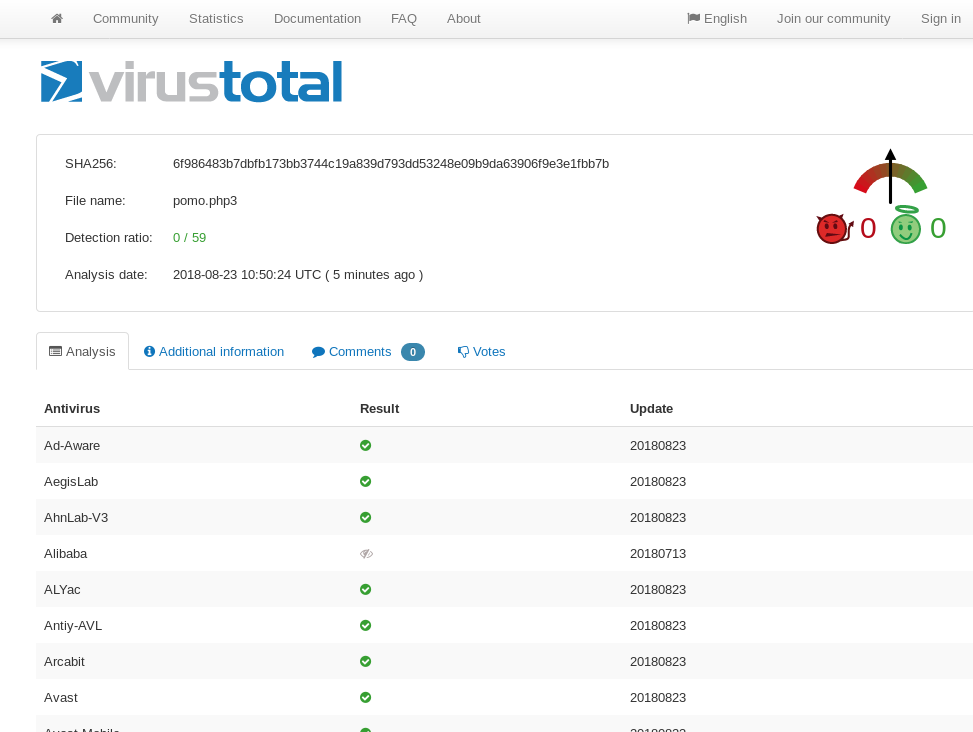
So here’s a brief demo on my malware.lan VM for testing.
So you simply navigate to the file in question…
And you are automatically logged into the wordpress admin back-end, as the administrative user. That’s it, simple yet effective.
I have added signatures for the malware to my Blazescan malware scanner tool and it underlying lw-yara rule set. Have questions? Find me on twitter @laskow26.