So last night I gave my talk at the Lansing MiSec meetup and released the hacked VM for you to practice your skills and web shell detection an perform IR on this server. I plan to do a full writeup when time permits.
Grab the .ova file here (please use for training purposes only and do not ever directly expose to the internet):
https://laskowski-tech.com/downloads/malware.lan.ova
Its a Virtualbox .ova file that you can import into that program on your host. It has a host only adapter and NAT adapter. please make sure that you set your Vbox to have the following host adapter settings for proper connection.
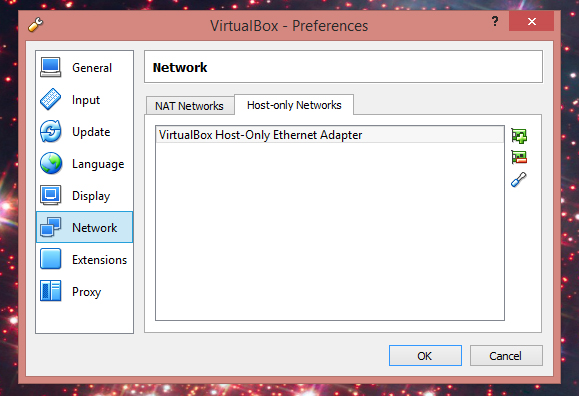
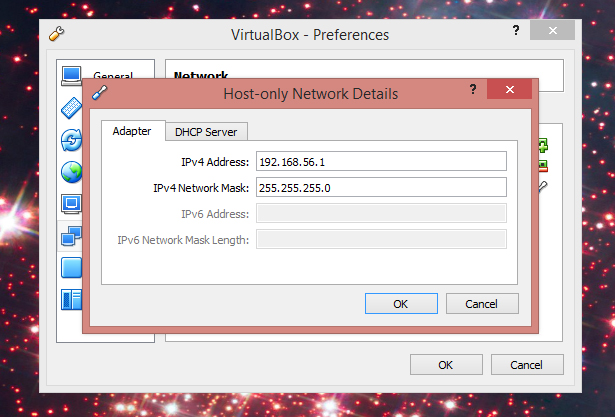
Then you will need to add the following to your hosts file for DNS to properly display the site:
192.168.56.102 malware.lan
in the following files:
Linux/Mac /etc/hosts Windows C:\Windows\System32\drivers\etc\hosts
(make sure to edit these files as the host machines admin user)
After that you should be able to boot the VM and in your browser go to malware.lan and see the following:
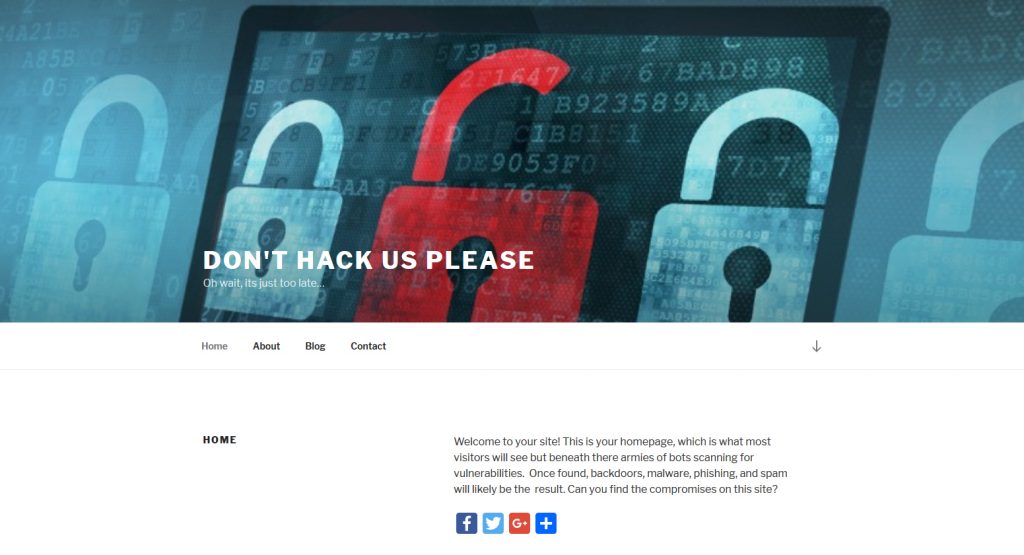
If so things are up and running properly, next ssh into the server in your favorite terminal program:
Host: 192.168.56.102/malware.lan User: webuser Password: password
From these begin your search! Feel free to reference the following for ways to locate the malicious content.
Thanks as well to the github user bartblaze whose tireless php websell collecting made this all possible.
See the talk to learn more here: