Investigating a malicious email the other day, came across a bit of a more widely deployed infrastructure than what I tend to see in day to day malspam campaigns.
We received a single email that linked to a site at the IP 23.95.97.56. But after preliminary investigation we found the site ended up at hxxps://www[.]eastendbuzz[.]com/vosg/report
This domain was not on the previous IP but instead on 216.172.168.138.
After some more pivoting using Urlscan.io we found that there were at least 5 different domains acting as pivot points for the campaign.
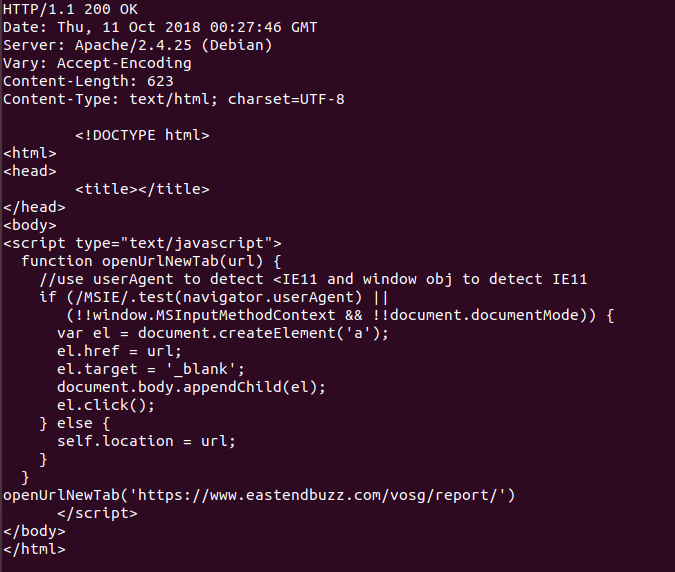
Here we can see the redirect from the pivot point. The following 5 domains were found based at 23.95.97.56 and redirecting to the final site.
hxxp://gfafoods[.]com/v3/report/id29173 hxxp://laborss[.]com/v4/report/id26364 hxxp://prestoquest[.]com/v5/report/id23779 hxxp://laborss[.]com\v1\report\id25329 hxxp://teachpulse[.]com/v5/report/id27246
Once arriving at the site the user tries to view the document promised only to be greeted by an error message. This page uses javascript to execute the popup hiding the true link to the download from traditional automated analysis.
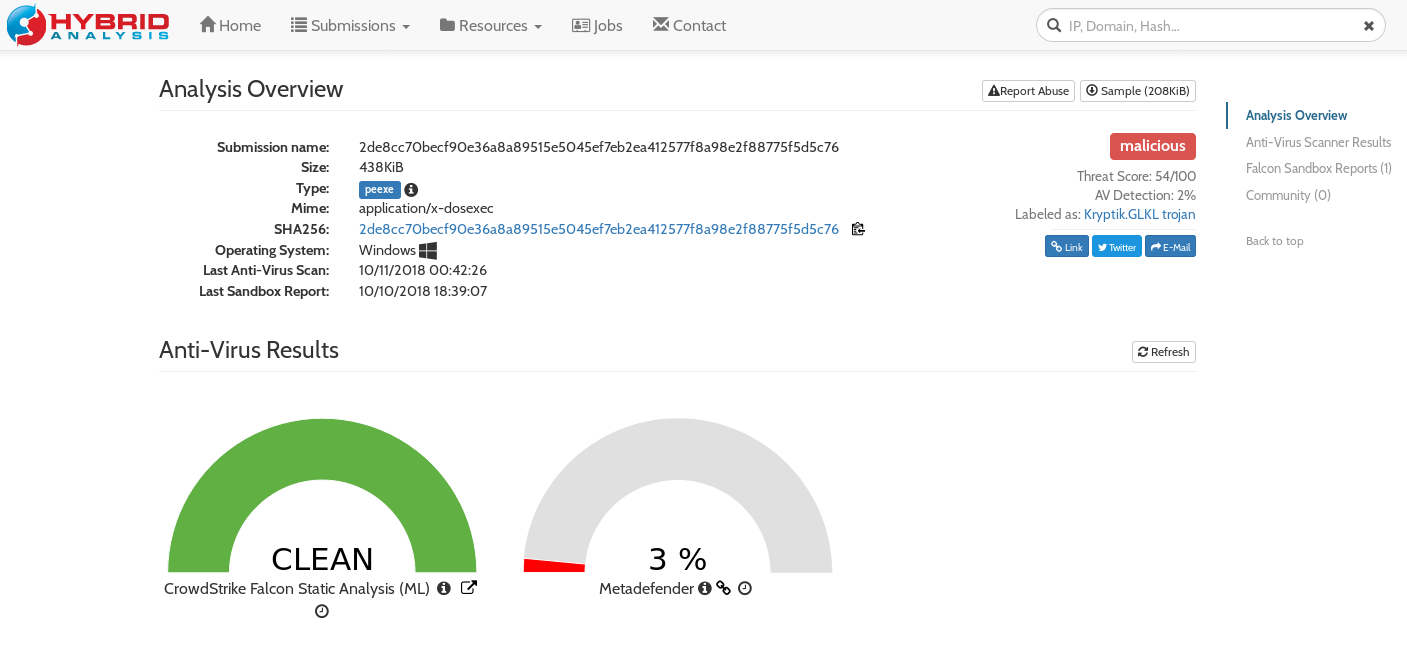
Once clicked the user is asked to download an exe file update_v1201.exe. Passing this to VT and HA we see the following:
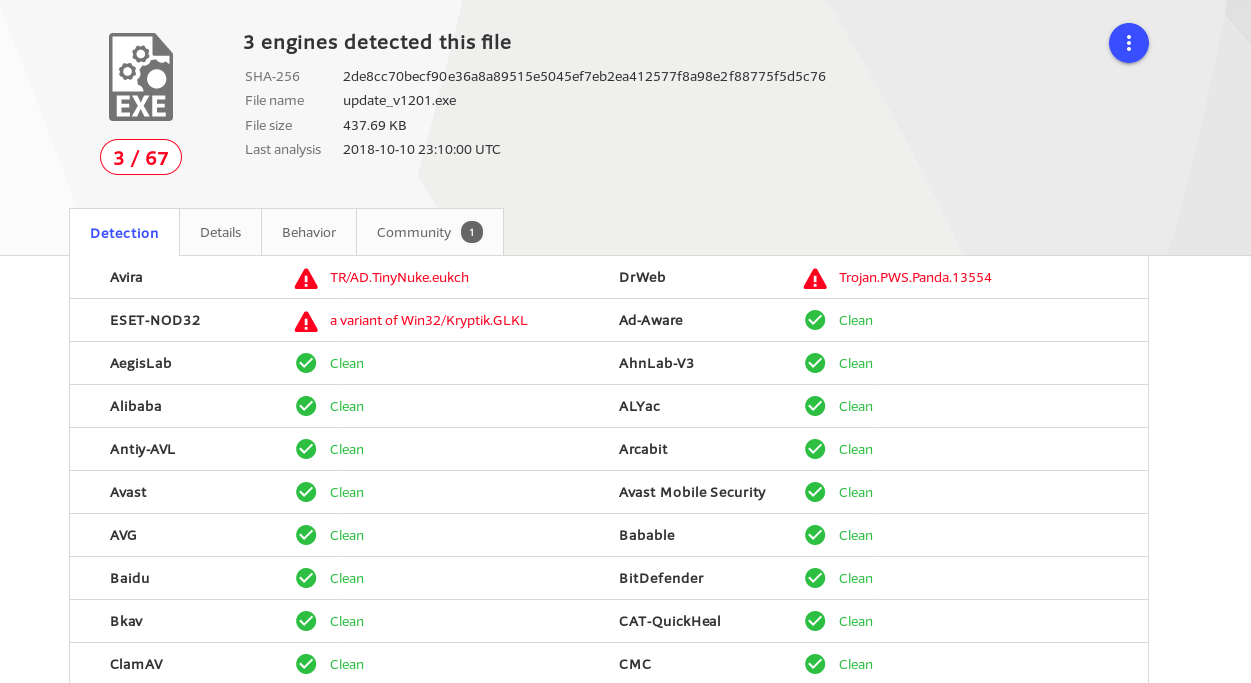
This looks to link this to a variant of a trojan/banking malware. Looking deeper into the strings it looks as though the code contains pieces of the powerarchiver software package from conexware.com.
Based on the malware family names report in the VT reports I found this article for the TinyNuke malware, which seems to mimic the distribution pattern seen both in the delivery and being include inside of other software packages.
https://www.bitsighttech.com/blog/break-out-of-the-tinynuke-botnet
All in all a little more than the average malspam, have insights let me know @laskow26 on twitter.
IOC’s
hxxp://gfafoods[.]com/v3/report/id29173 hxxp://laborss[.]com/v4/report/id26364 hxxp://prestoquest[.]com/v5/report/id23779 hxxp://laborss[.]com\v1\report\id25329 hxxp://teachpulse[.]com/v5/report/id27246 hxxps://www[.]eastendbuzz[.]com/vosg/report 2de8cc70becf90e36a8a89515e5045ef7eb2ea412577f8a98e2f88775f5d5c76 update_v1201.exe
Pre-release update, before publication occurred I followed up on the VT report for a reanalysis, and wow have the rates of detection changed, what a difference a day can make.