So today key reinstallation attacks (KRACKs) came out providing a reliable method to crack the highest available method to safeguard both home and enterprise networks. The good news, it can be patched! The bad news you will never know if the everything is patched. As it appears this can affect both clients and the WiFi accesses points, you may only have control of some of these devices you may connect to and some devices(looking at you Android handsets) may never receive updates from the manufacturer.
I have been a proponent to of doing the best you can to take security into your own hands, not to rely on others when you can avoid it. One of the best method for years has been to use VPN services when connecting to open WiFi at your local coffee shop. But today’s release shows that even the highest level of WiFi security can be breached. This leaves your data vulnerable even when you think it secure.
Take the most reasonable steps to protect yourself, in this case using VPN to encrypt your traffic can give you another layer of assurance when you can’t trust the network(WiFi access). I have written before how you can easily deploy the free and open source OpenVPN technology on hardware from anything like a raspberry pi to building your own router, you can look at those guides here.
Today though I want to point out the easy of this tech using the pfSense opensource router technology. You can easily roll this in your own custom hardware or buy a prebuilt product through them. You can get an idea of the basics of starting up the server here: https://doc.pfsense.org/index.php/OpenVPN_Remote_Access_Server
The biggest take away I can say for all of this is that the pfSense software allows you to configure the openvpn software via a GUI, that is missing from much of the other openvpn deployments unless you look into OpenVPN AS which could be free or not depending on your deployment.
Next lets look at getting a user setup for our Android mobile device whose patch may never see the light of day.
Create a user in the pfsense router for the phone
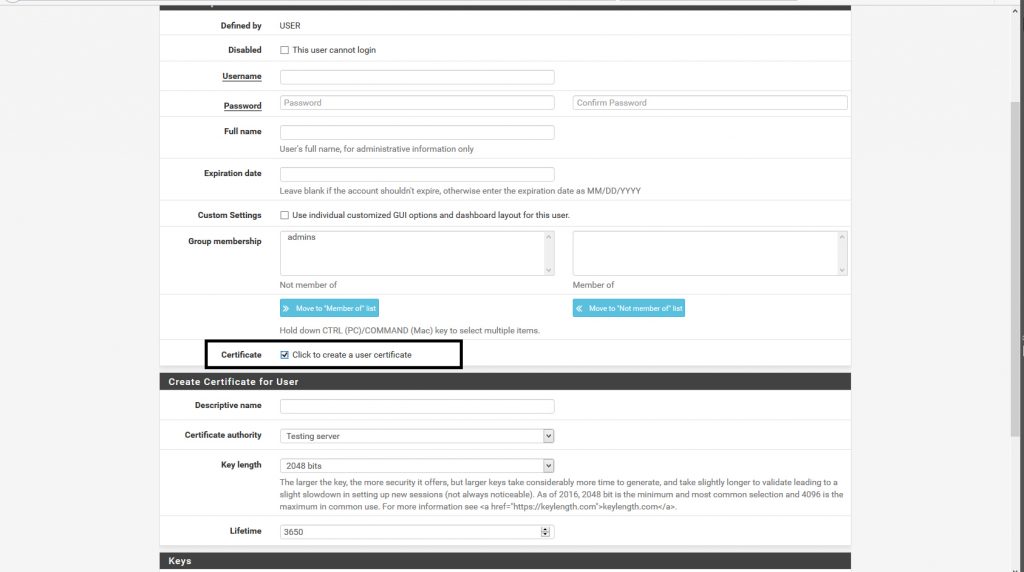
While creating the user make sure to also create a client certificate for them as well or they will not be able to use the vpn service.
Next if you have not added it yet install the openvpn-client-export package which makes the next step a piece of cake.
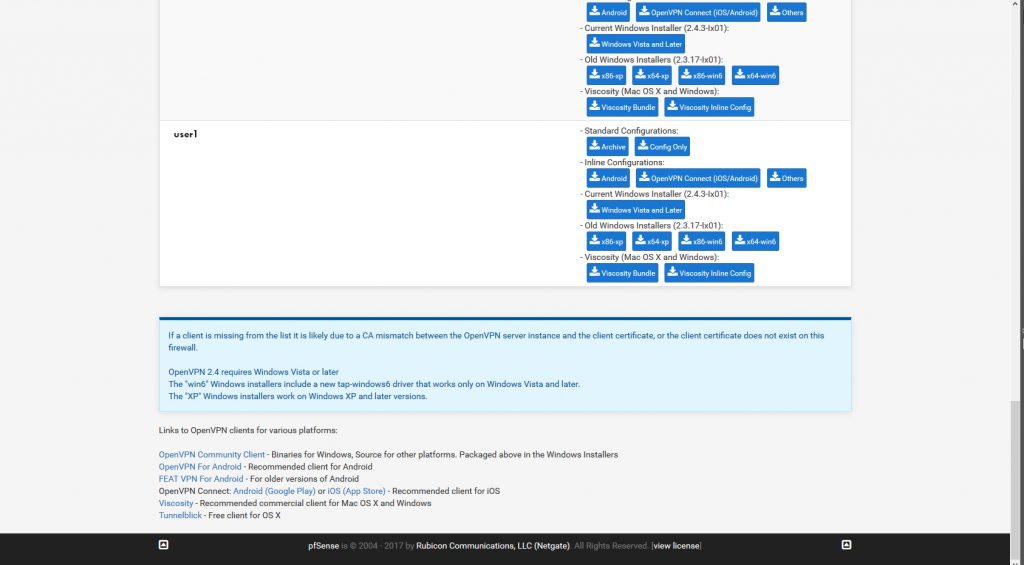
simply scroll down to the client section and grab the config you need for the proper device, in this case I’m completing the set up for my phone and will be using the OpenVPN connect app.
If you haven’t already grab the propper app from the app store.

The grab the file that is generated from the openvpn-client-export tool on the pfsense router, it will be a file ending in .ovpn and download it to the mobile device in question. Fro there go to the app settings and import the Profile from the device memory.
After that you should be able to connect, I have mine set up to require the username and password but you have other ways you can set it up as well, but regardless you have one more layer of security to keep your data safe on untrusted networks.