So after catching some post con bug finally had a chance to watch Mr. Robot, so binged through to season 3 episode 5 (lastest out at the time) and one thing stood out to me. Oh also if you’re not caught up spoilers ahead.
Almost all of the hacks are pulled off due to a malicious insider, not crazy 0-day or tunneling through firewalls. And one of the biggest things we fail to prevent is insider threats. Let’s examine a few of the hacks from the show, how they were pulled off and what might have helped prevent/detect the compromise.
ps. I am not flaming the show, I enjoy the program thoroughly just want to use some of the hacks as thought experiments.
Case No.1 The CD of d00M:

So in the first few episodes of the first season a member of a criminal hacker group is tasked with getting an exploit into a security companies network. The method displayed in the show is a combination of social engineering followed by blackmail. I’m not sure that I can make a good case on what specifically infosec could have done to prevent that, but as is usually advised don’t plug in untrusted media of any kind. But more to the point the malware actually gets onto the internal network of the security firm, are they only counting on firewalls to protect them?
Where is the monitoring capability? Are they not running some kind of internal IDS looking for C2 or unusual traffic a la Sec Onion? What about any kind of behavior alerting like an employee logging in to their work station outside of normal work hours as there is literally no one in the office at the time. Do they not implement application whitelisting, is the employee’s account local admin? How is the software able to install.
I feel that there are many missed opportunities for how this could have been prevented.
What could have prevented this:
- Monitoring (EDR, Network monitoring, behavioral).
- No running as local admin?
- Application whitelisting.
Case No.2 Countermanding Orders:

Next there’s the event when a simple email puts a compromised server off a restricted honeypot network back into production via a simple support ticket request. This first takes place via a distraction that gives the Elliot access to his bosses mobile device which appears to be providing a timing 2FA authentication code to log into the support system’s ticketing system. First step that could have prevented this, lock your mobile. Enforce Mobile Device Policies requiring locked devices, anything to lock the device helps better than nothing. And just because its your office doesn’t mean its safe to keep unlocked.
Second this code that is displayed that appears to be 2FA, for some reason appears to only be a time based password for this system, so uhhhh how about real 2FA here, a string of numbers on your phone alone is still 1FA, combine something you have, something you know, or something you are in combination please.
3rd whaling is becoming a more and more common event now a days. We need to have more resilient methods in place to prevent a single email from the CEO’s inbox from ruining a company. For critical systems have protocols in place to require checks. Get a request like this require a follow up call to confirm, or a in person check in, two people to sign off on it. Just a single email being able to unlock such a critical system is a single point of failure.
What could have prevented this:
- Mobile Device Management (enforce locked devices)
- Real 2FA
- Polices to confirm critical business/system changes.
Case No. 3 Plug and Play Network:

Owning the FBI is as easy as dropping a box? First as seen in prior scenes there’s a complaint of the lack of secure access to the floor by an FBI agent. We do have on thing that’s helpful you at least have to be a employee to reach the floor, but if this is the FBI is there a reason they can’t post agents to prevent walk on ‘s to the floor or some kind of access security better than uhhh none.
Next up we can just plug in a machine to the network and boom its up an functioning. We should be able to have some kind of switch port security or monitoring for new devices that connect to the network that can prevent access without authorization or at minimum alert to their presence.
Similarly in the office environment we need to be aware of unknown wireless networks popping up, especially in secure areas. Use of some kind of wireless monitoring should find this pretty quick.
What could have prevented this:
- Effective Physical Access Control
- Don’t allow new devices to just jump on the network
- Monitoring for new Wireless access points
Case No.4 Why not Share:
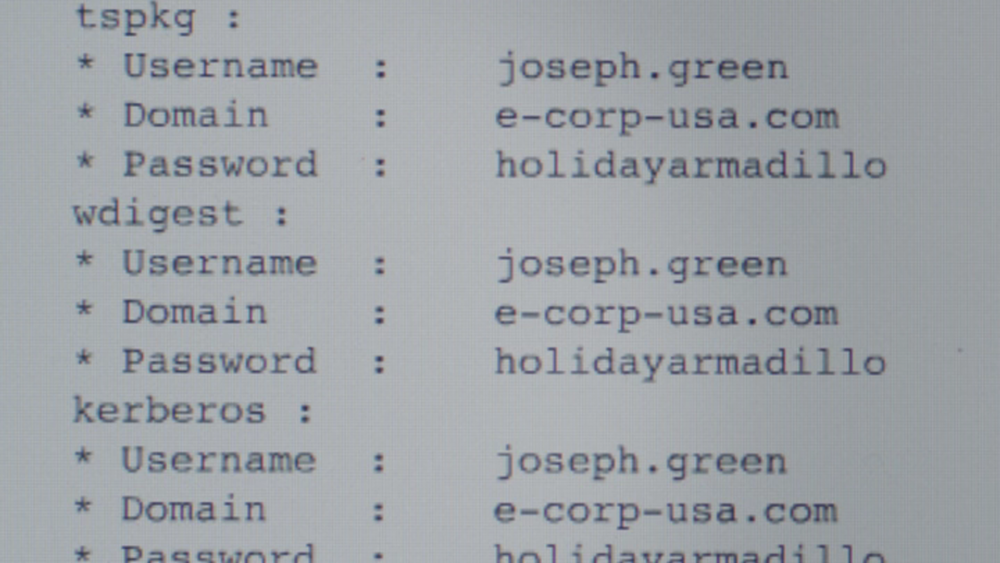
Angela, who appear in most of these incidents as the insider strikes again here. This time she get the secretary to leave under false pretenses and gains physical access to her targets workstation. From there the use of the USB rubber ducky grabs creds likely using a mimikatz payload. From there she then accesses that users account from her workstation and then downloads sensitive files from the network shares that account has access to.
So if you can enforce it, disable USB devices and again with the physical access controls. Less likely to have a means to lock down in this case, but perhaps close (and lock, {not foolproof I know})your office door while out.
How about back to the monitoring, detections for mimikaz? Or again behavioral analytics alerting when a users account is used on a PC they’ve never accessed before or is in an unrelated office department? Use of honey tokens in file shares to detected unusual access.
What could have prevented this:
- Prevent physical access
- Monitoring (EDR, behavioral)
- Honeytokens
Case No.5 Separation of Duties or just Ship it up! :

The final case I’d like to look at here is the shipping mess that Elliot is able to achieve to try and prevent stage 2. How pray tell is a Security analyst have access to the logistics system? pretty sure that shouldn’t be a thing. So….I’m going to guess he’s likely using pilfered creds from another employee with access. Similar to before how about some behavioral analytics? Perhaps some 2FA on these accounts… Perhaps some employee training to report irregularities like the two gents out in Sioux Fall, SD. No one apparently reports these kind of things.
- You know the drill monitoring (behavioral)
- 2FA
- Employee training
So these are a few of the big ones that I noticed that took advantage of the inherit trust relationship we give to insiders, and as some one wiser than me said once an outsider compromises an insider account, they follow the same patterns as a malicious insider so if we get better at detecting malicious insiders then by proxy we’ll be better at detecting external actors as well. What do you think, send thought insights on over @laskow26 on twitter.