So many malware today is now distributed by phishing sites and malicious sites. Many of these are tracked by various outfits and they offer a great resource in the form of threat feeds. One of my favorite methods to take advantage of these feed is to set up network level DNS black holes. There is the fabulous software package out there known as the pi-hole project which allows you to deploy an ad/malware DNS blocker on a simple raspberry pi.
But I am also a fan of the flexibility offered by the pfSense firewall/router project. So here’s how to deploy DNSBL on pfsense, currently running version 2.4.2.
First of all head over to the package manager and grab the pfBlockerNG package.
Next head over to the Firewall / pfBlockerNG
Head over to DNSBL
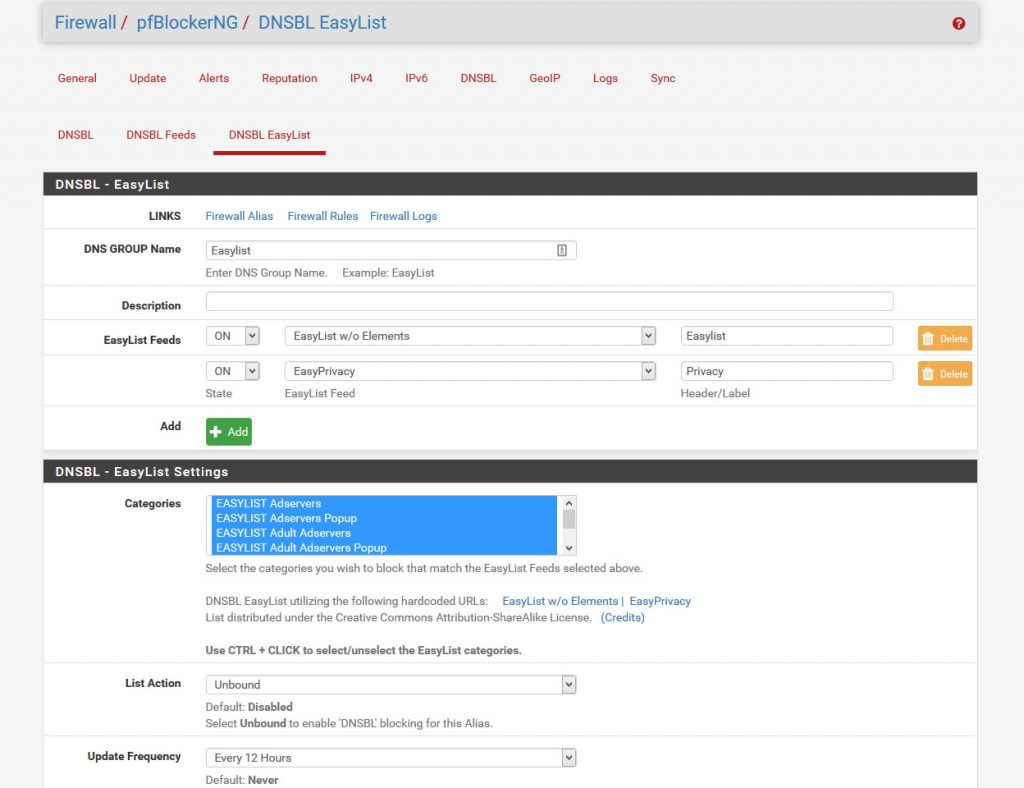
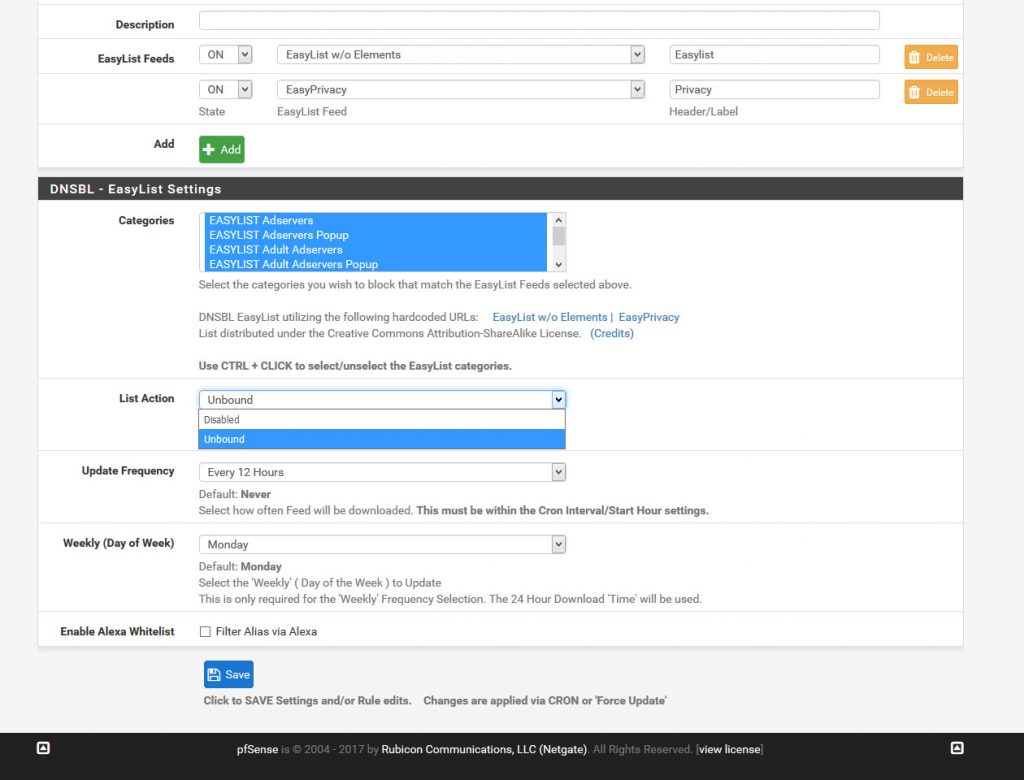
Lets turn on the EasyList first.
Next make sure to change the list action from default to Unbound.
This will add in Ad-blocking as that is the majority of the list in the EasyList, but let’s take this a step further and add our own custom list.
Head over to the DNSBL Feeds and click add.
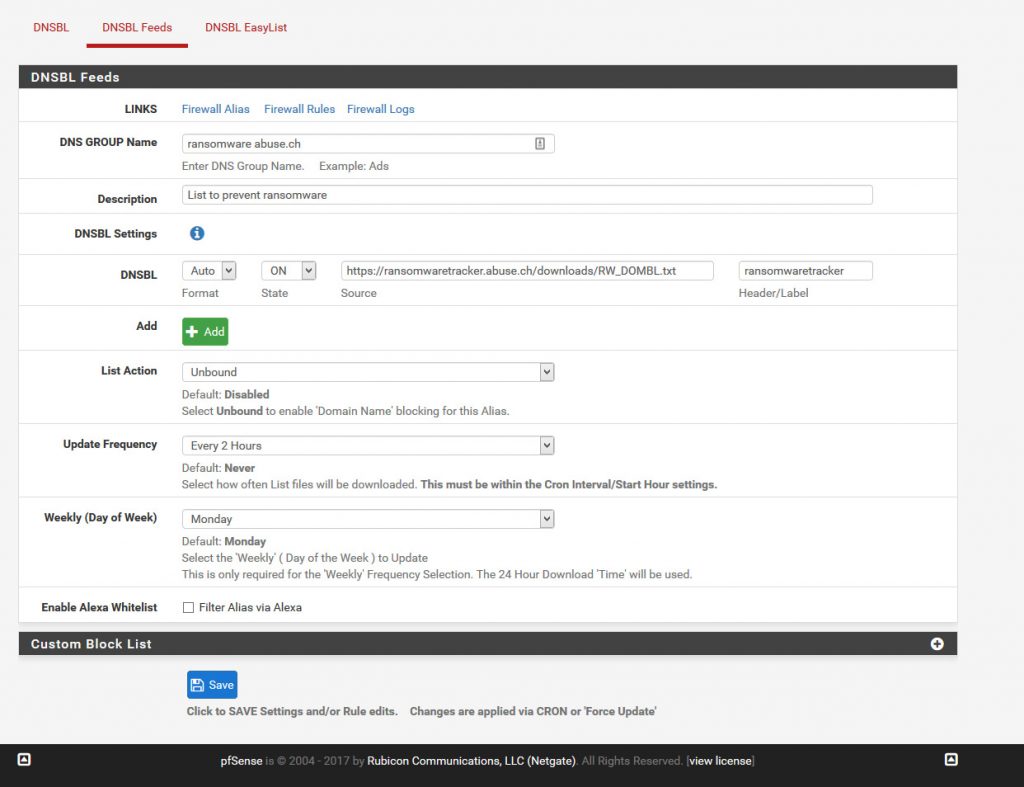
Here I’m going to be adding the Abuse.ch ransomware list.
Add the group name: ransomware abuse.ch
Give a description for your notes.
Add the source of the list in this case:
https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt
Give it a Header/label: ex ransomwaretracker
Make sure to change list action from Disabled to Unbound.
Choose an update frequency, I picked 2 hours.
And let’s save!
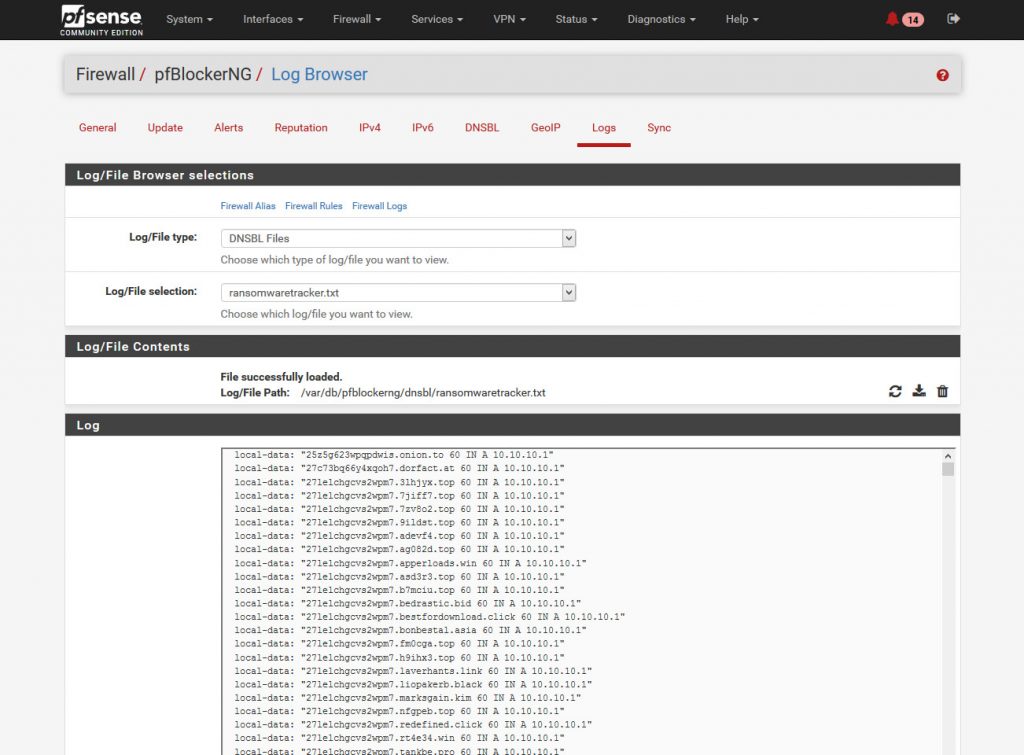
Let’s check our work, head over to Firewall / pfBlockerNG / Log Browser
Select the Log/File type to DNSBL files and select the header name you gave the list, in my case I used ransomwaretracker(.txt).
You should then see the following.
This means if any malware droppers try to direct your endpoints to go to any of the DNS names in the list here they will instead load a blank resource located at your router/firewall and not the malware server to deliver the next stage of the payload.
Here’s some other good lists to add:
Another list via the Abuse.ch project:
https://zeustracker.abuse.ch/blocklist.php?download=domainblocklist
https://www.openphish.com/feed.txt
Phishtank, a part of OpenDNS now owned by Cisco
http://data.phishtank.com/data/online-valid.csv
Malwaredomains the oldie but goodie.
https://mirror1.malwaredomains.com/files/justdomains
Monero Miner pools to block malicious crypto mining
https://raw.githubusercontent.com/Hestat/minerchk/master/minerlist-all.txt
Have others that you like? Let me know @laskow26 on twitter
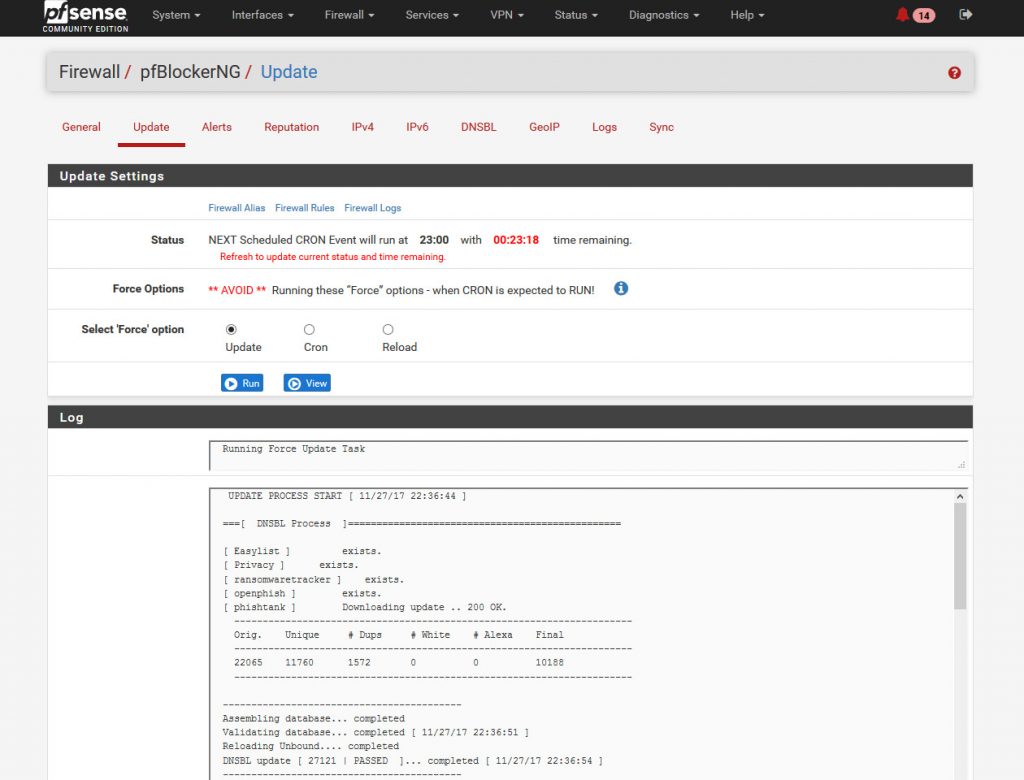
Oh and a last trouble shooting step, if your list doesn’t show up right away you may need to run a manual update of the feeds.
Firewall /pfblockerNG / Update
PPS.
Don’t forget about the whitelist DNSBL section to whitelist domains that may appear in the list and are parsed wrong, such as google.com, amazon.com etc.