So while I may have had a lot of fun looking into malicious crypto miners, the number one thing we find on compromised servers is phishing, and spam associated with phishing. Recently Duo Security did a great survey of phishing kits, so I figured I’d post a breakdown of one of the more polished kits that we tend to see day to day.
These kits are generally deployed when the malicious actor already has access to the server, either via a legitimate login, or a previously place webshell. The phishing kit will be uploaded as a zip archive:
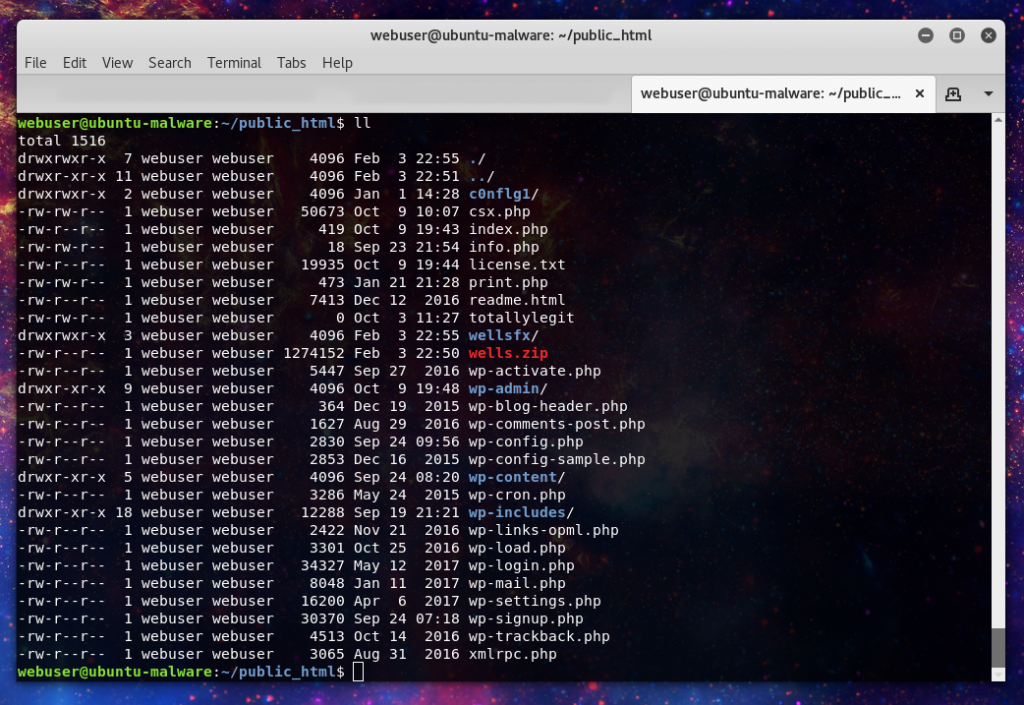
Here we see the wells.zip file which unzips into the wellsfx directory.
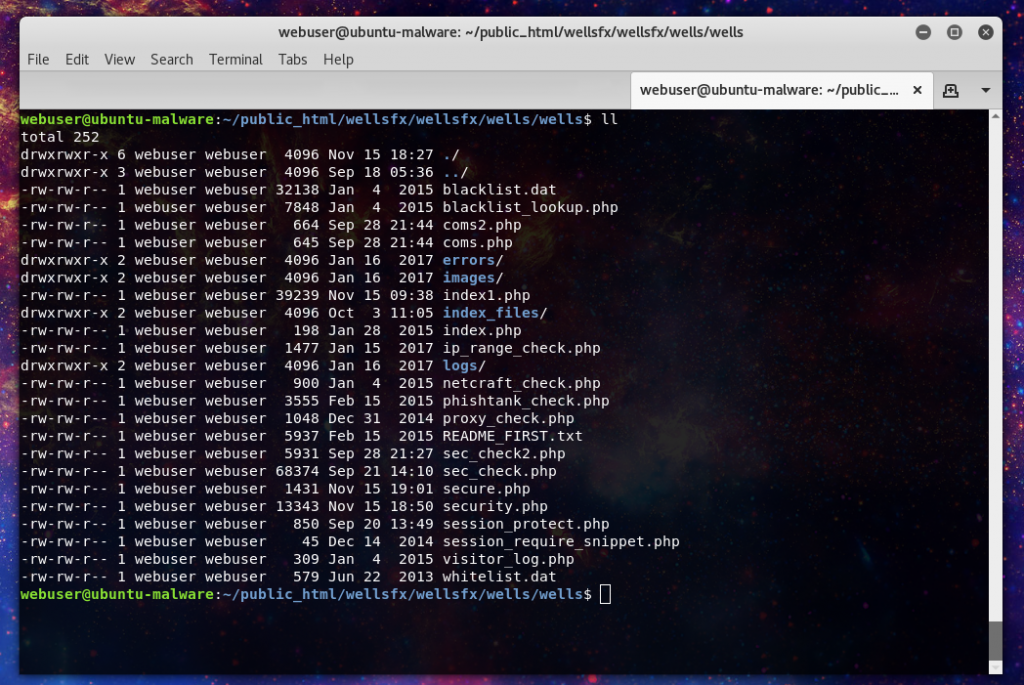
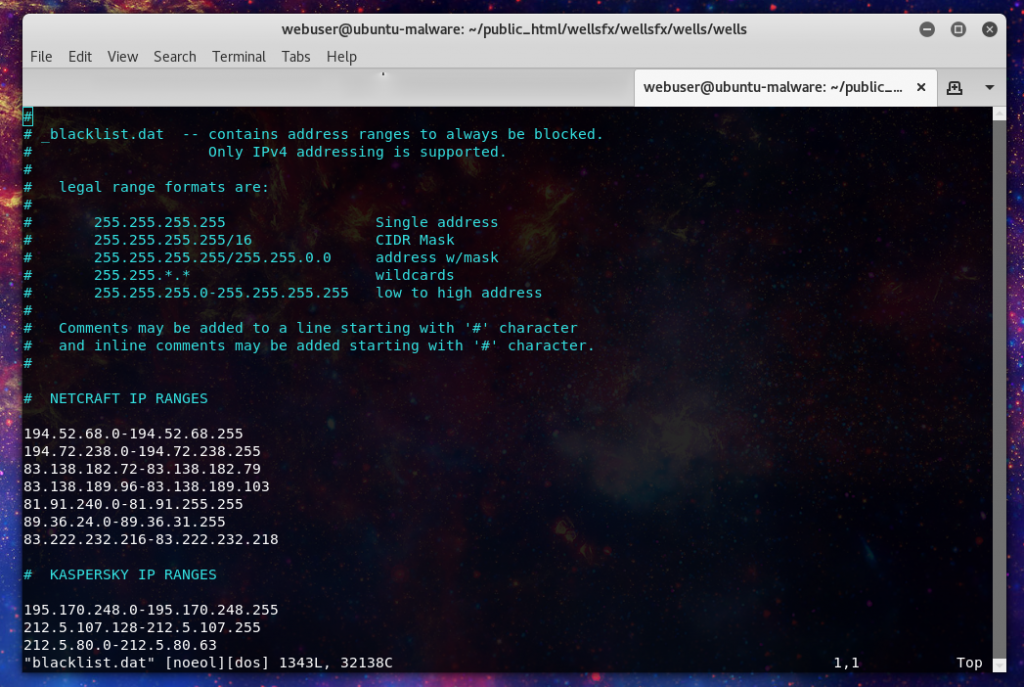
In the wellfx path we can see the file structure. In here we can see a rather comprehensive set of anti-phishing measures, including a blacklist of the major information security companies who work to combat phishing.
The blacklist include IP ranges for 120 different organizations. From ones you would expect like OpenDNS/Phishtank to most VPS providers like AWS and OVH.
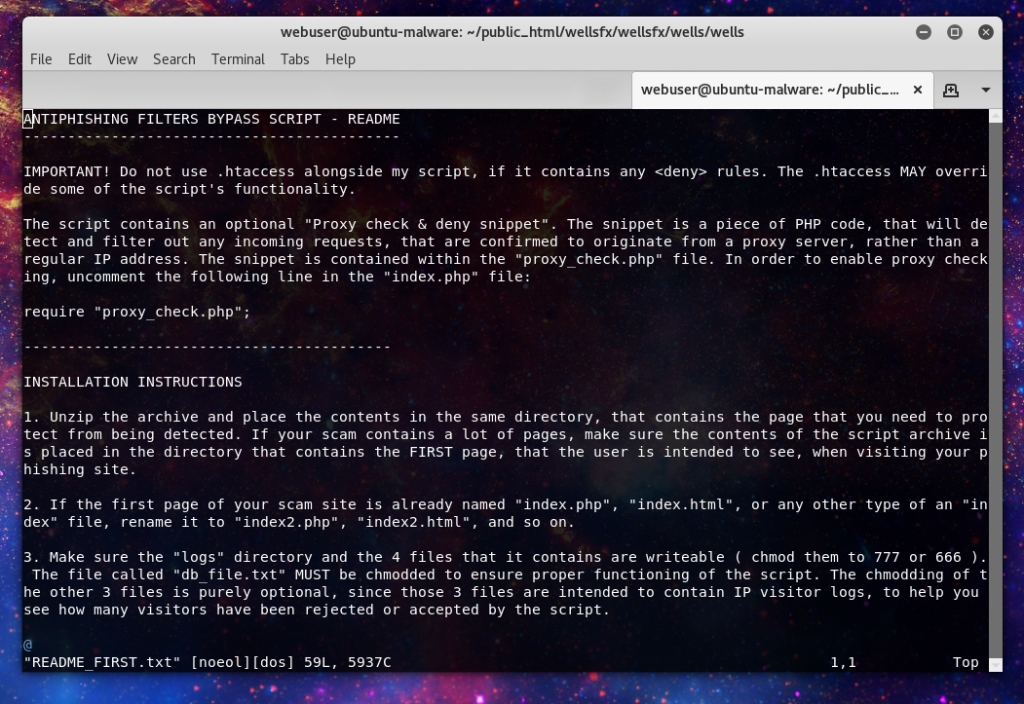
The kit includes it’s own installation instructions, even a way to get support(over ICQ of all methods) for the kit should it not function as intended.
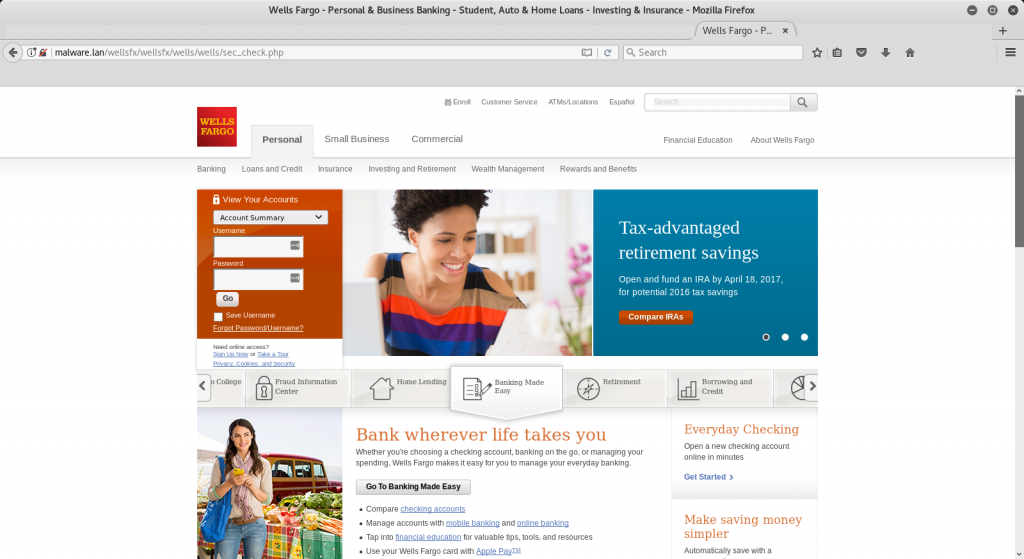
Well once your kit is up an running what do your “customers”(targets) see?
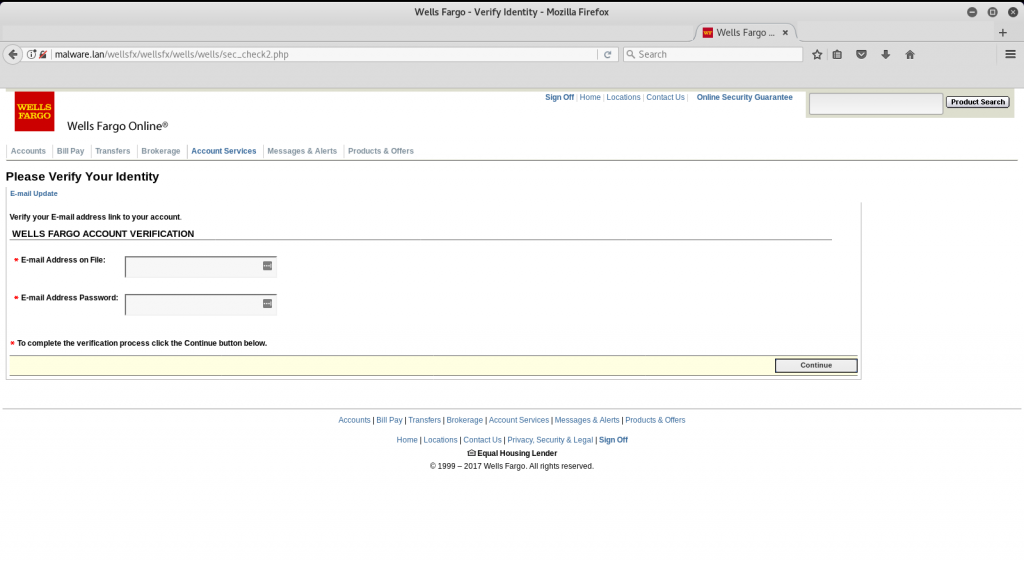
Looks pretty believable… other than that URL… But assuming you continue.
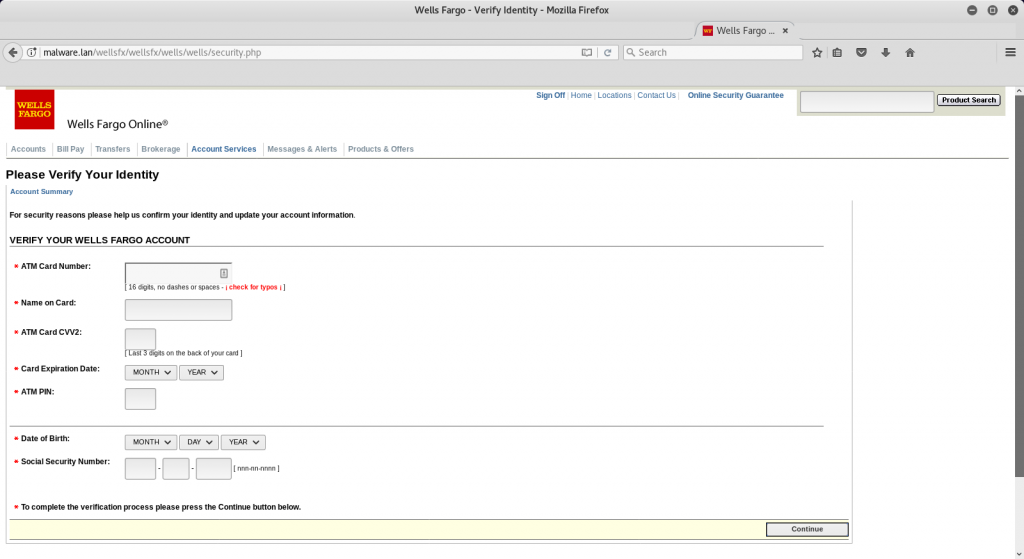
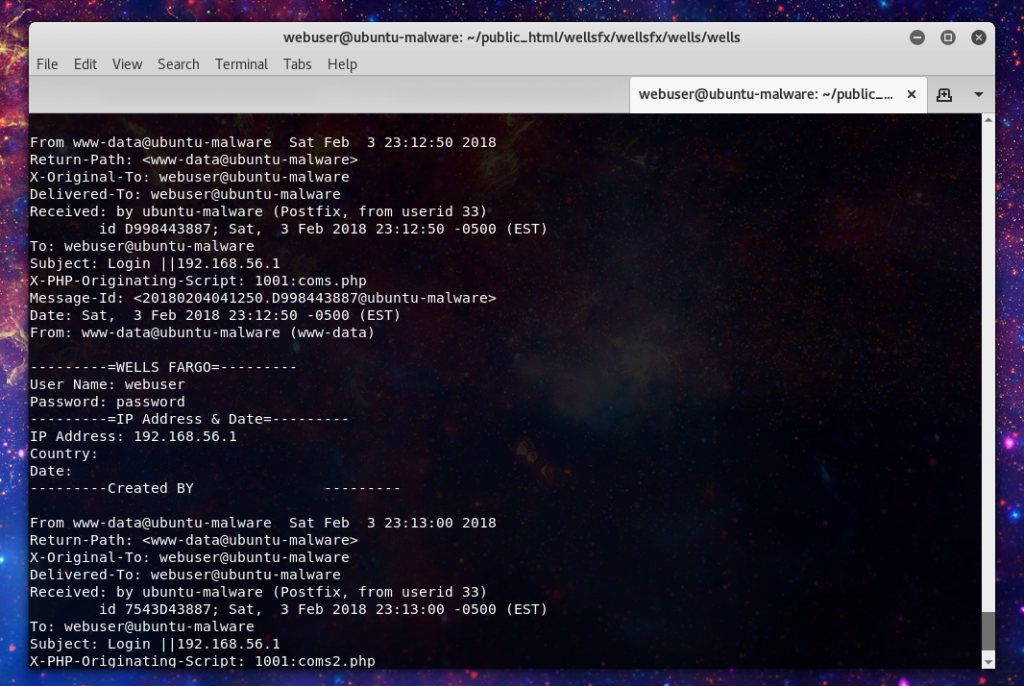
And after you have entered the info the kit redirects you to the legitimate site to throw off any suspicion. And what does the malicious actor get, a nice tidy email with all the info necessary to commit fraud.
Want to learn more, check out the Duo Security report, or Phishtank. Have questions, ask @laskow26 over on twitter.