So this morning I was wanting to update the original snort crypto miner rules to my minerchk tools. I thought it would be nice to create detection based on all of the domain and IP addresses that I’ve uncovered using the infection cases I deal with. Well, I’ve not written too many snort rules in my time yet, and those I’ve written have been pretty basic.
So starting I took a look at some of the current rules written in the standard Snort packages. Taking a look I see them formated like this:
msg:"ET DNS DNS Query for Suspicious .co.kr Domain"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|02|co|02|kr|00|";
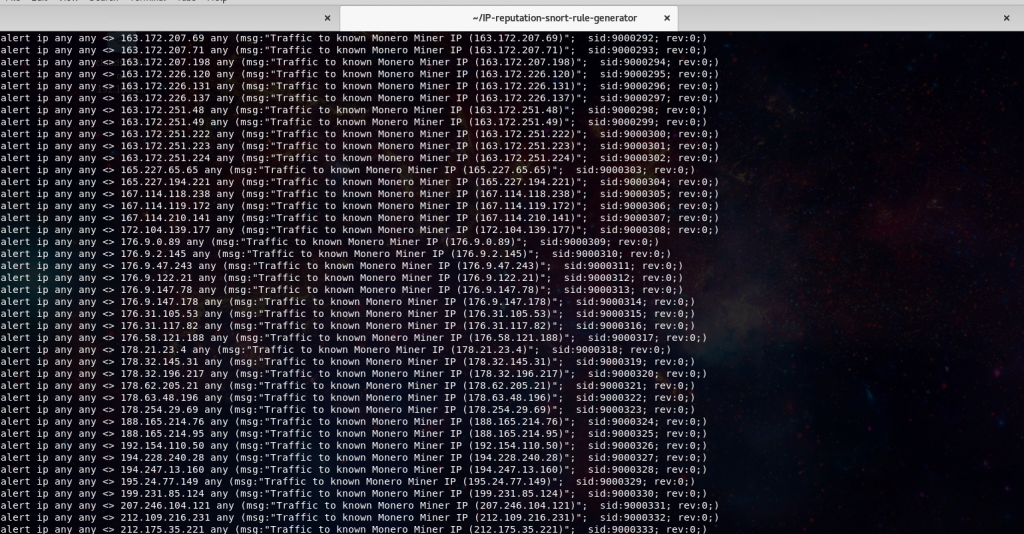
Well, I’m not quite sure what format they are using to create the content: filter required for the rule to process. After a short while of fruitless googling I find the nccgroup IP-reputation-snort-rule-generator. This tool is exactly what I was looking for! Feed it a IP or domain list from a remote URL, or a local file, and it will perform all the formatting required to create a proper Snort rule.
./tepig.pl [ [--file=LOCAL_FILE] | [--url=URL] ] [--csv=FIELD_NUM] [--sid=INITIAL_SID] [--ids=[snort|cisco]] | --help
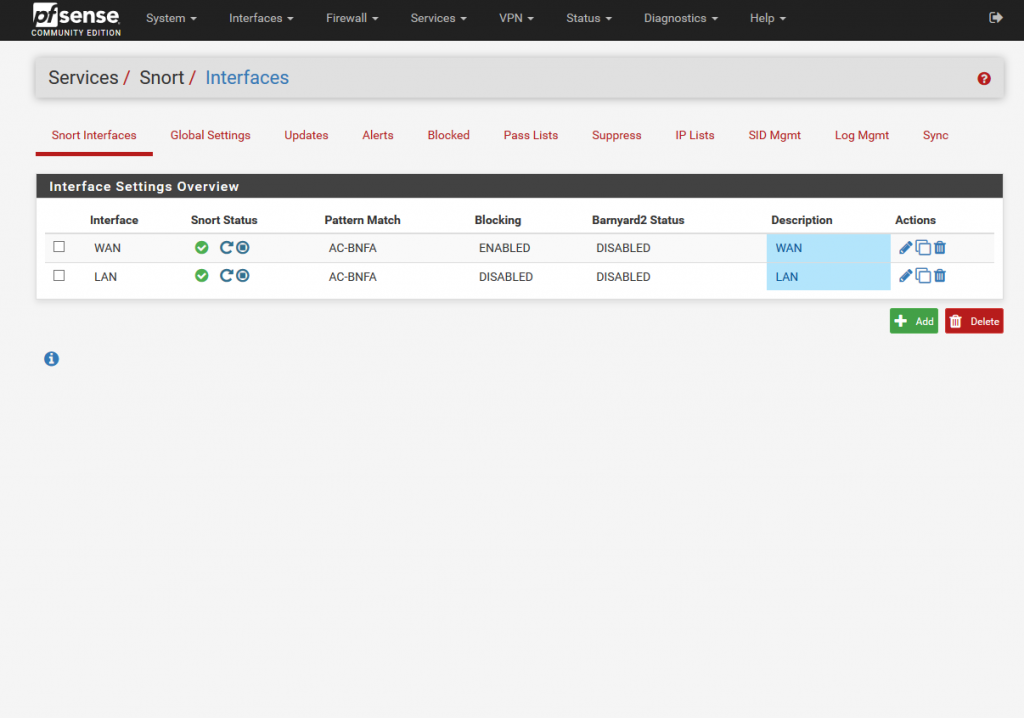
Then performing some tests, I went to my pfsense firewall and set up the custom rules under one of the interfaces.
Go to your Snort setup under services, edit one of your interfaces, in this case I’m setting up on my LAN interface.
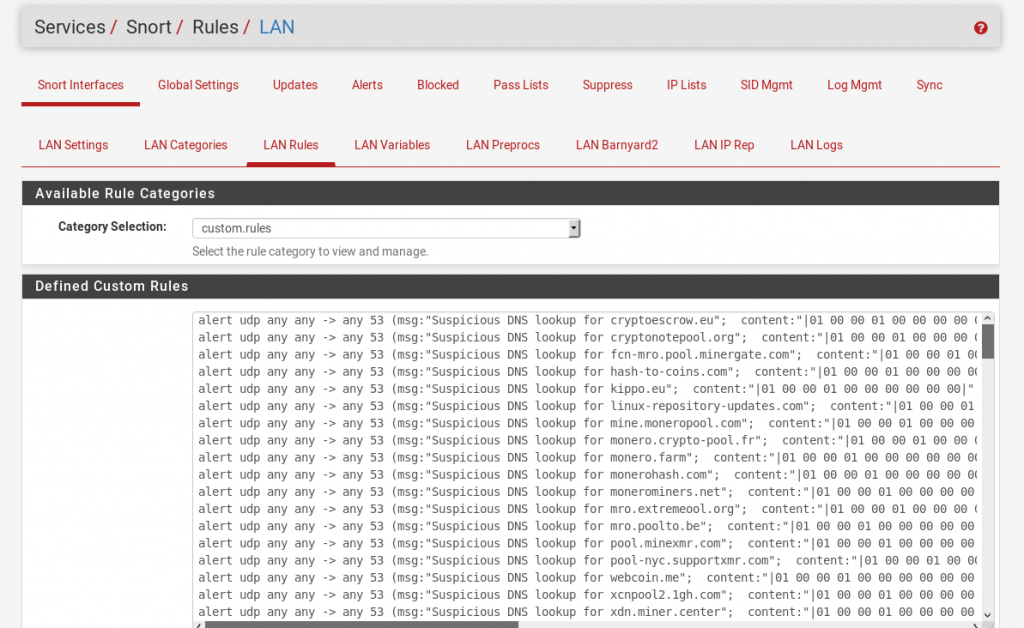
From there head to the LAN Rules tab. And select custom.rules
Add in the custom rules you’d like, in this case I’m using my monero-snort.rules from the minerchk repository.
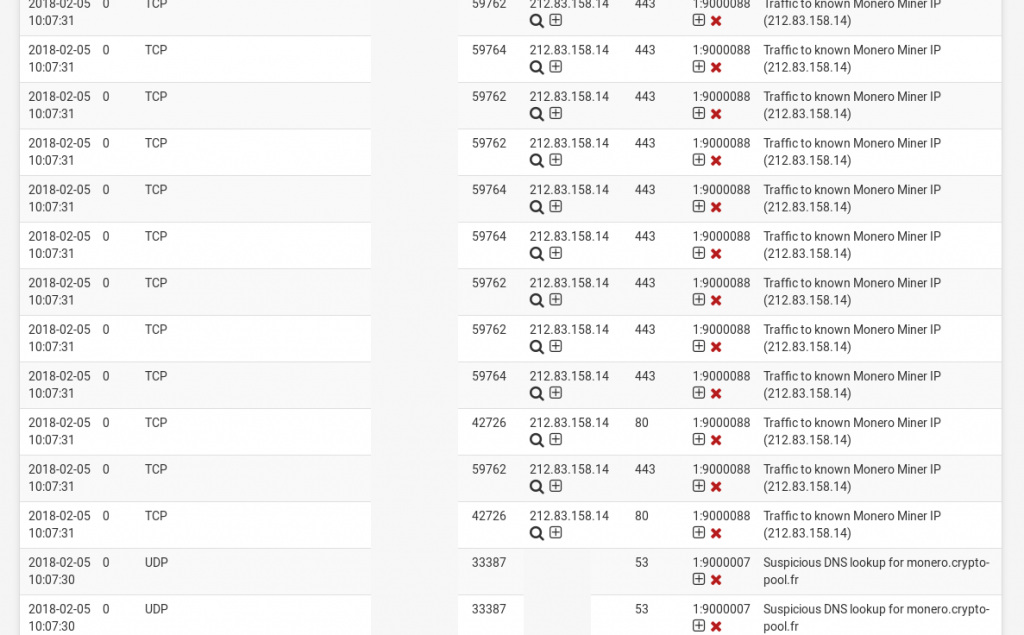
Then running the test I hit one of the miner pools using a machine on the LAN.
Nice actionable alerting to systems running Monero Miners locally. Now, does anyone know if you can get pfsense to load custom ruleset on a cron, instead of having to dump manually? Hit me up on twitter @laskow26.