So in my day to day work I come across many servers that have been compromised. Far and away the majority of these compromises use either phishing or spam as their monetization method. In the past year or two crypto ransomware has been on the rise, however in the last 12 months I have come across only single instance of a ransom-wared server. There’s another piece of crypto though that has seemed to be on the rise from my experience. That is malicious crypto-mining.
With Bitcoin hitting 16K this past week the timing seems almost to convenient for this appearance. As such I took it upon myself to dig some data points out of the compromises that I could get data on.
First for web servers the miner focus on the Monero currency. This particular currency is preferred over bitcoin as the processing power required to mine bitcoin is so intense that most bitcoin mining is performed on optimized ASIC‘s at this point. Monero on the other hand is well tuned for mining on general CPU’s something that are often more powerful on servers than endpoints.
The majority of miners at this point participate in pooled mining, this allow them to form a network to increase their chances of finding a new block of the blockchain and then they get paid out based on their contributions. This is the method observed in the cases outlined here. And is seems to make sense as a reasonable way to monetize a compromised server. Lets dig into the data.
In this case we have records from 17 incidents from the last 12 month period. In some of these instances there were multiple compromises, or more than a single method used. However some trends in the data are quickly apparent.
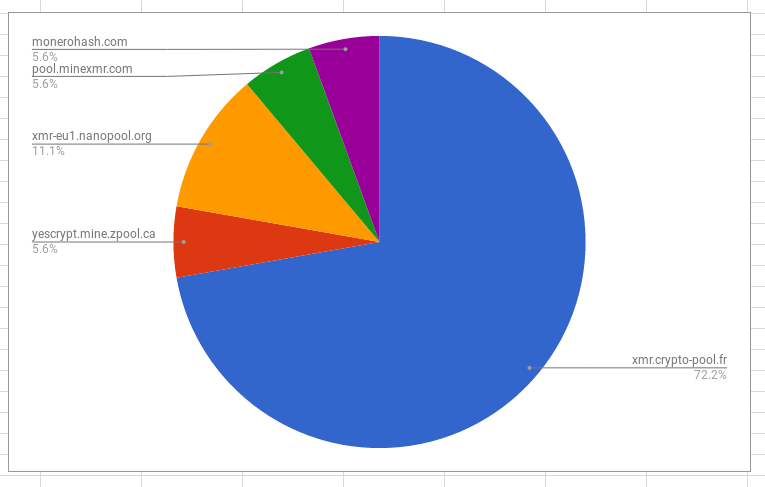
Below are the mining pools used in the incidents investigated.
Below are the ports used to communicate with the mining pools.
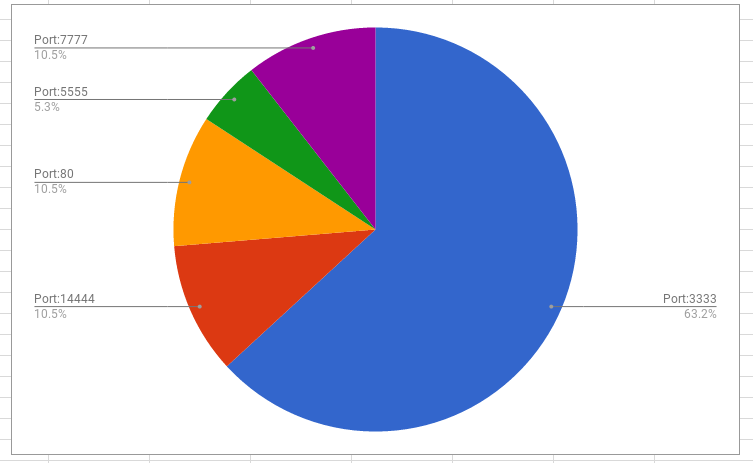
So the data shows that in the incidents investigated the majority were communicating with the crypto-pool.fr pool over port 3333.
The most commonly observed method of running the malicious miners appeared to be compiled php binaries running in /tmp on servers, an example of one below:
[root@host public_html]# cat /tmp/php0lvovH.c threads = 16 mine = stratum+tcp://42uxsmEbzh93QQJLf9B7fHazBomQbrcPKVUPPg2SyRqBc7q4ZV9juUejSCrDtMfGnEZHrgMujBemsRhkBmG5Y2LxR3Fwgcm:x@xmr.crypto-pool.fr:3333/xmr
The file presented here is the pre-compiled file. Which is most commonly present alongside the compiled binary. The syntax used heavily indicates that they are using the YAM miner which is currently hosted on the MEGA file sharing service.
| YAM Miner (by yvg1900) | CPU | MEGA |
Example: yam -c x -M stratum+tcp://YOUR_WALLET_ADDRESS:x@xmr.crypto-pool.fr:3333/xmr
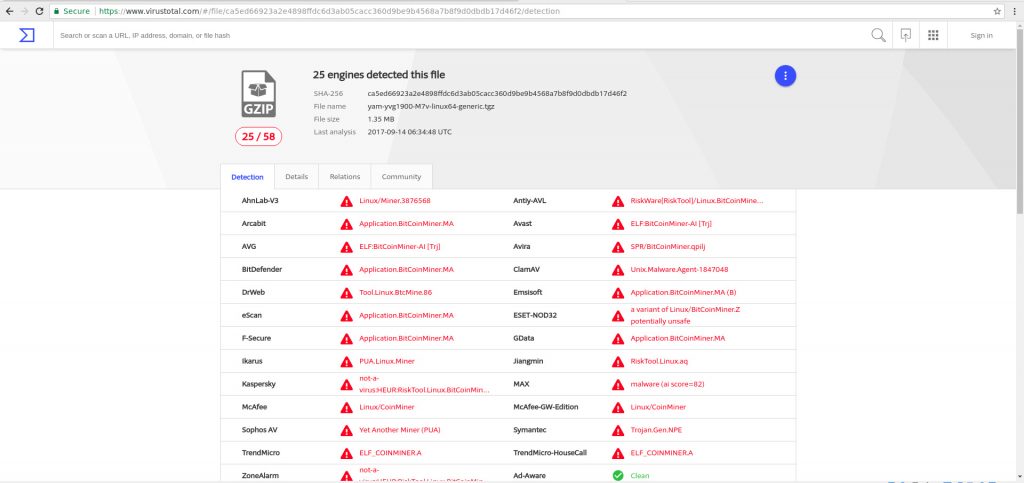
Grabbing a copy of one of the software packages and sending to VirsusTotal reveals plenty of hits identifying the package as a miner with pretty good detection numbers.
Since these miners are participating in the mining pools these pools allow for the ability to track the profits of the actors.
Of the miners in the data the vast majority had earned between 1.5-1.8 XMR. At the point of writing a single XMR is going on the market for around $280 USD.
However one actor was identified to have mined 1711 XMR, which equates to around $479,080 USD. That is a tidy sum of money. However that particular wallet had the accompanying text present in its results looked up at the pool:
You addresse mining is suspend for botnet usage.Send me email to mine@crypto-pool.fr
This indicates that you may be able to reach out to many mining pool administrators and submit take down requests should you come across a malicious miner on your server.
Overall in the data the returns equated to around $634,000 USD at the current exchange rate. With this kind of money present and until the processing required goes above what a standard intel processor can crunch there seems to be a reasonable incentive to use this as a monetization method for the near future.
Stay tuned for part 2, I’ll be looking at some of the common detection patterns, and methods protect against these kind of compromises.
Find me @laskow26 on twitter.
*while this was an interesting dive, data on these is still from a rather small sample size. Overall this is self selecting and only representative of server detected. I do believe that there’s more of this going on out there. If you have some examples of similar incidents I’d love to add some of that data to my set.
**while rising in incidence, this is still rather rare compared to the amount of servers used as spam or phishing boxes.