So I have been using ClamAV for a while now and have found it to be a very effective and modular tool, especially due to the fact that you can use it with you own custom signatures using sigtool and yara to create your own signatures. One other tool that has been very effective for me as it pertains to incident response and threat hunting has been TheHive, a security operations ticketing, reporting, and investigation tool. So I thought, what if I could put these 2 together?
Well the team over at TheHive has an API and python module that you can use to create your own analyzer. Technically the analyzers are down by a back end service called Cortex, not by TheHive itself, but anyway, I have taken the time to build said Analyzer for Cortex/TheHive. You can take a look at, and download the code for it here:
https://github.com/Hestat/ClamAV-CortexAnalyzer
Let’s take a minute to go over the basics to getting this up and running. We will assume that you already have TheHive and Cortex deployed a properly configured, if you need assistance with setting those up refer to the Docs for those here and here.
First lets begin with cloning the analyzer to the location of your analyzers, in this case I use the following:
cd /usr/local/src/Cortex-Analyzers/analyzers/ git clone https://github.com/Hestat/ClamAV-CortexAnalyzer.git
Then you will need to make sure the requirements are in place. The analyzer only has 2 requirements, the cortexutils package and pyclamd, but the following will work:
cd ClamAV-CortexAnalyzer pip3 install -r requirements
Once you have the Analyzer downloaded and python requirements installed, lets make sure that Cortex recognizes it:
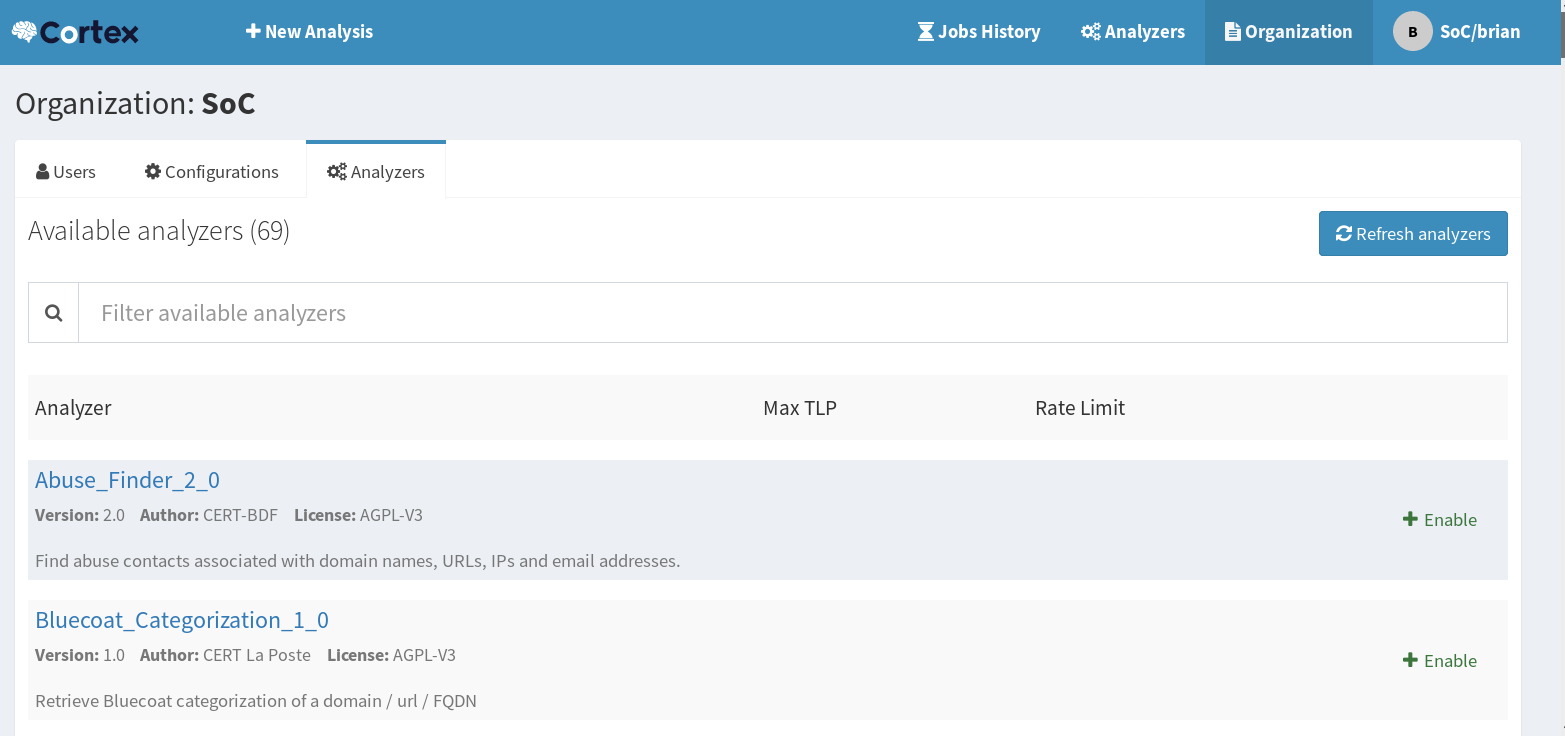
Log into cortex with an account with the proper privilege level and go to the Organization menu and select the Analyzers tab, there you should see an option to refresh the Analyzers. If all goes well you should see in the list now as Clamscan_1_1, go ahead and enable it, there are no major configuration options to set, and all info is processed locally so just choose you TLP setting and you should be set here:
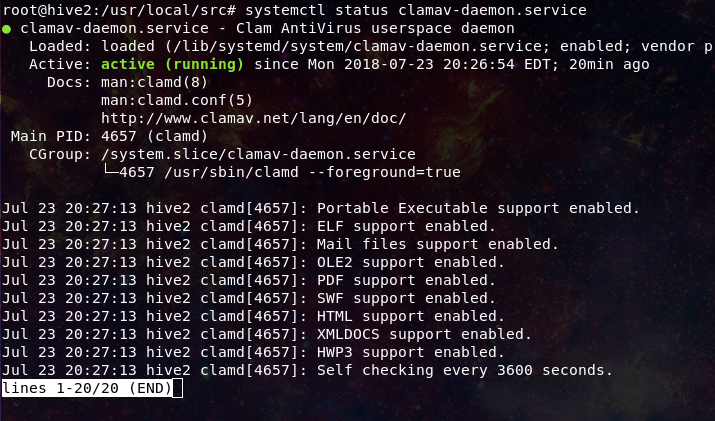
So Cortex now knows you have the Analyzer, but we also need to have an instance of Clamd running for the analyzer to talk to.
You can always refer to the ClamAV docs to get the specifics for your OS and version, but here I will be running past the install on an Ubuntu based system.
In this case the package is available in the main repo:
apt-get install clamav-daemon
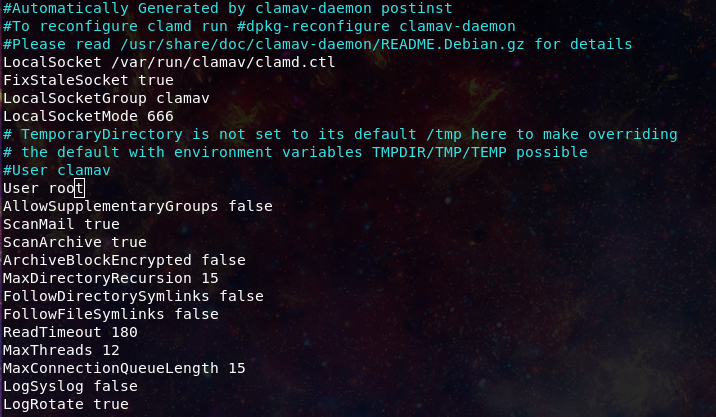
Now once you have installed Clamd, you will need to adjust the configuration a bit. Cortex which will be running the scans on behalf of TheHive will get an error for denied perms if you use the standard clam conf, we will need to adjust the user the Clamd process runs as from clamav to root:
You will need to edit: /etc/clamav/clamd.conf
As well if you want to add in your own custom AV signatures you will want to add or edit the following line:
DatabaseDirectory /var/lib/clamav
You can choose to add additional directories, or remove the main and set to only your own. Make sure that you restart Clamd after making any configuration changes and that it is working after the restart as if you give the configuration an incorrect option it may crash the service.
Now we have Cortex setup, and Clamd running, lets finish the setup by getting TheHive prepped.
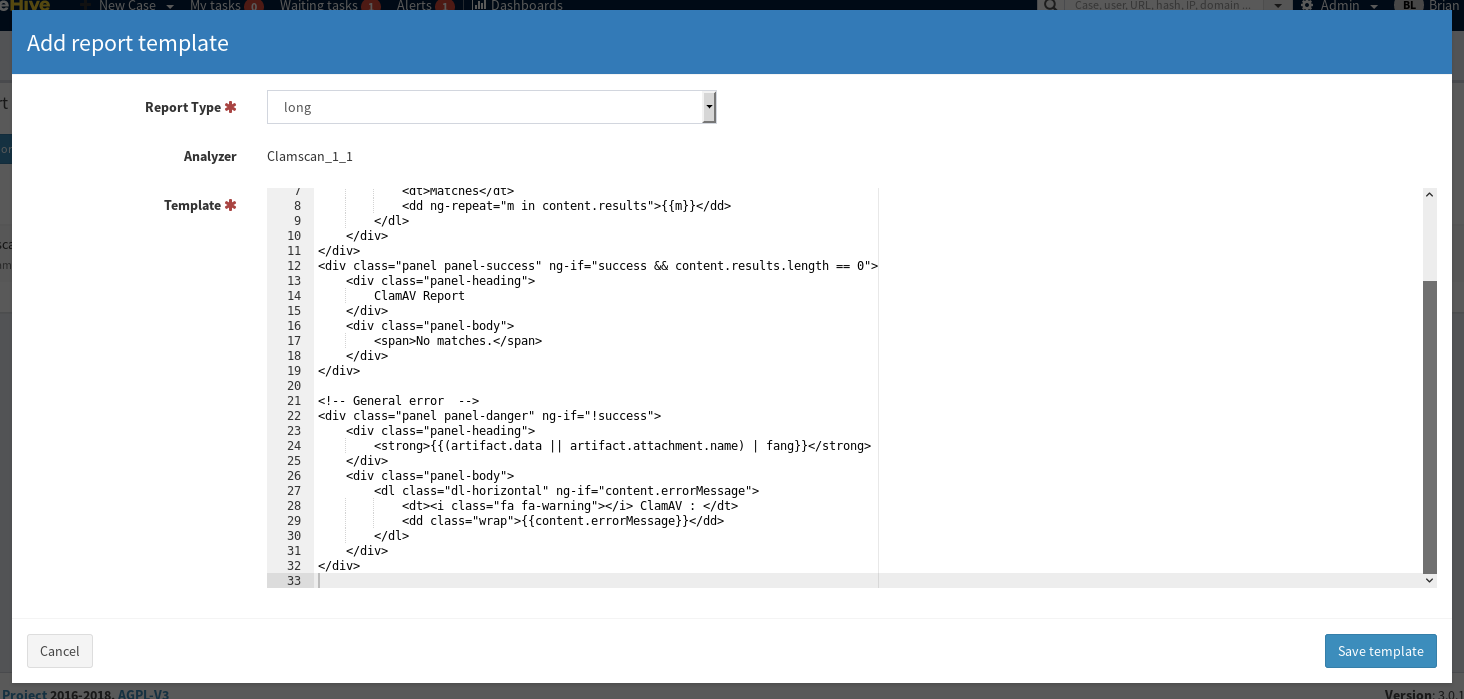
Login to your instance of TheHive with the appropriate privileges, and head over to the report templates menu:
There is both a short and long template, make sure to add both of them into TheHive configuration menu. Once finished there we should now be able to scan with the analyzer.
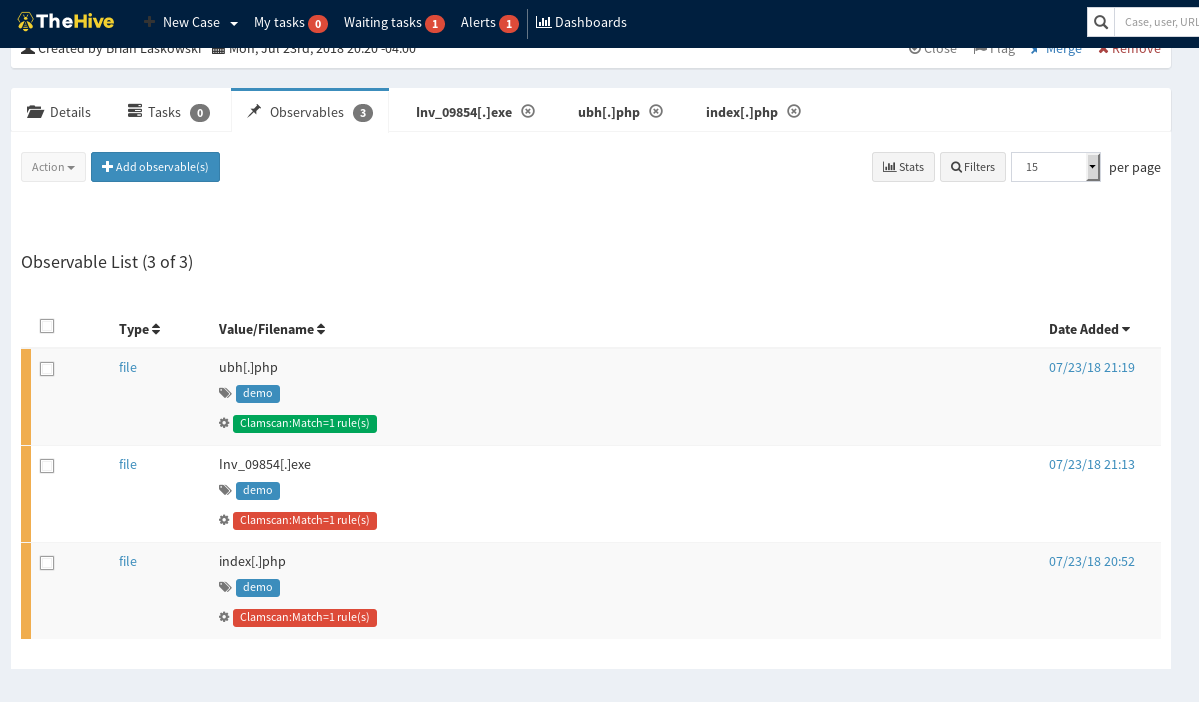
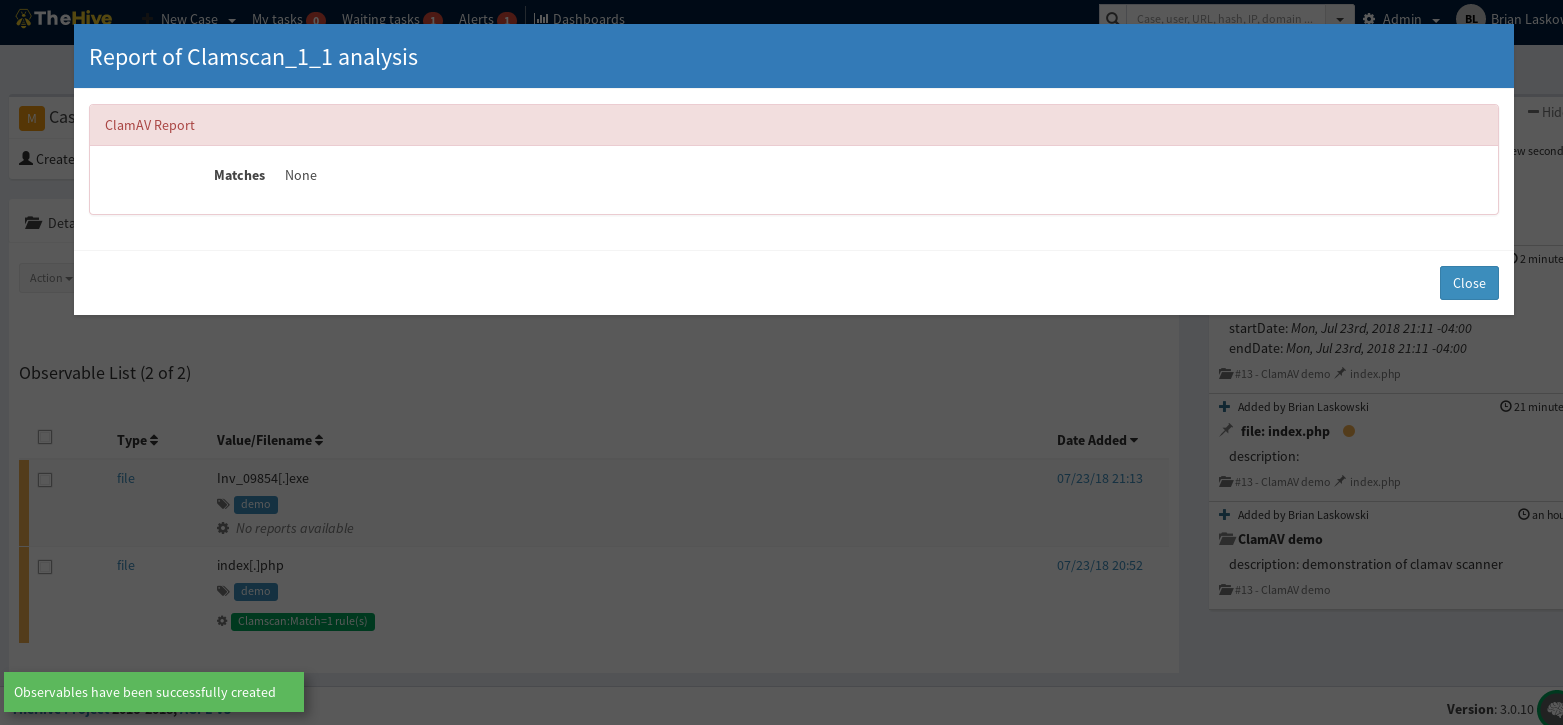
When running the analyzer if there is a malicious hit you will get your observable marked in red, otherwise it will report back green:
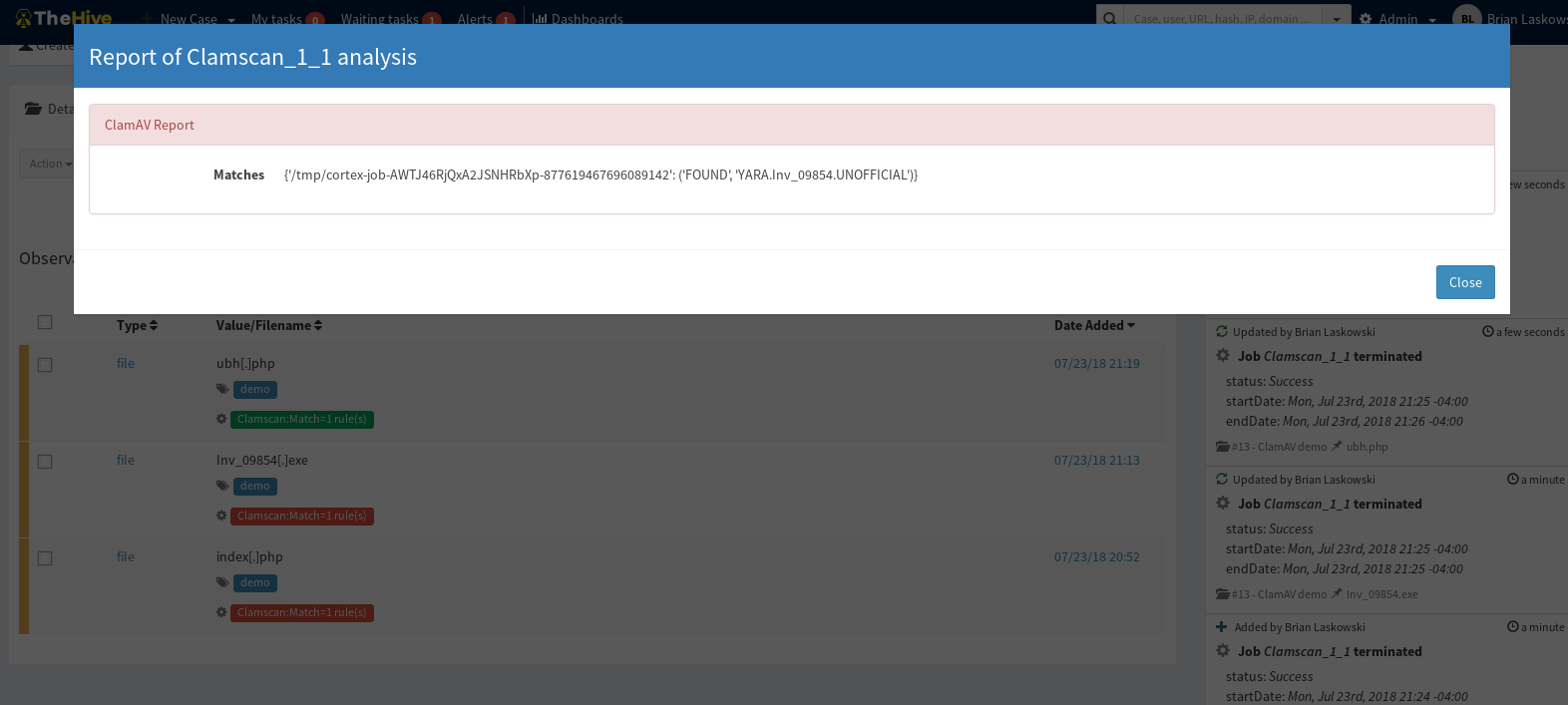
Looking at the reports kicked back for malicious hits it will report in the following manner:
And if it does not match a malicious rule:
Take a look at the project again here:
https://github.com/Hestat/ClamAV-CortexAnalyzer
Have question, comments, or improvements? Find me on twitter @laskow26, or report it via Github.