Lately Empire has been showing up more frequently in my sandbox testing with Emotet/Trickbot generally being the sample that brings the Empire afterwards for recon and active directory exploitation. One thing that had confused me about these Empire samples however is that they look like the defaults, no customization to the stager. With one sample I happened to pass it to one of my favorite tools UrlScan. Doing that led me down a rabbit hole of some great OSINT data for getting an idea on the use of Empire and a way to look for future Empire Command and Control.
Let me take you through the journey and share the results.
Step One the first sample:
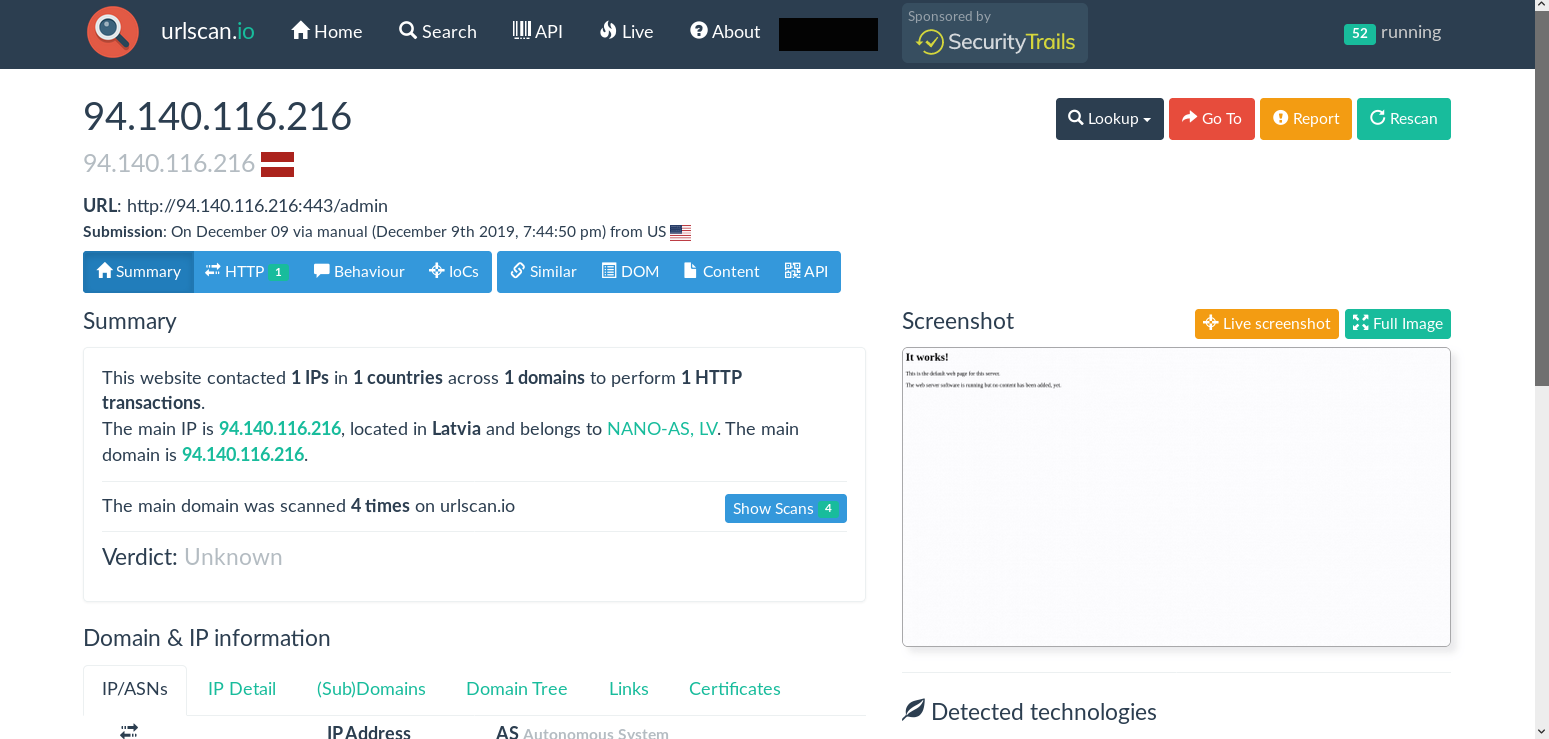
So initially I started with a single sample which I submitted for scan. While the stager was as basic and default the page returned via a scan did not match my knowledge of a default Empire C2 setup (turns out it was the default for an older version on Empire but I did not know that at the start).
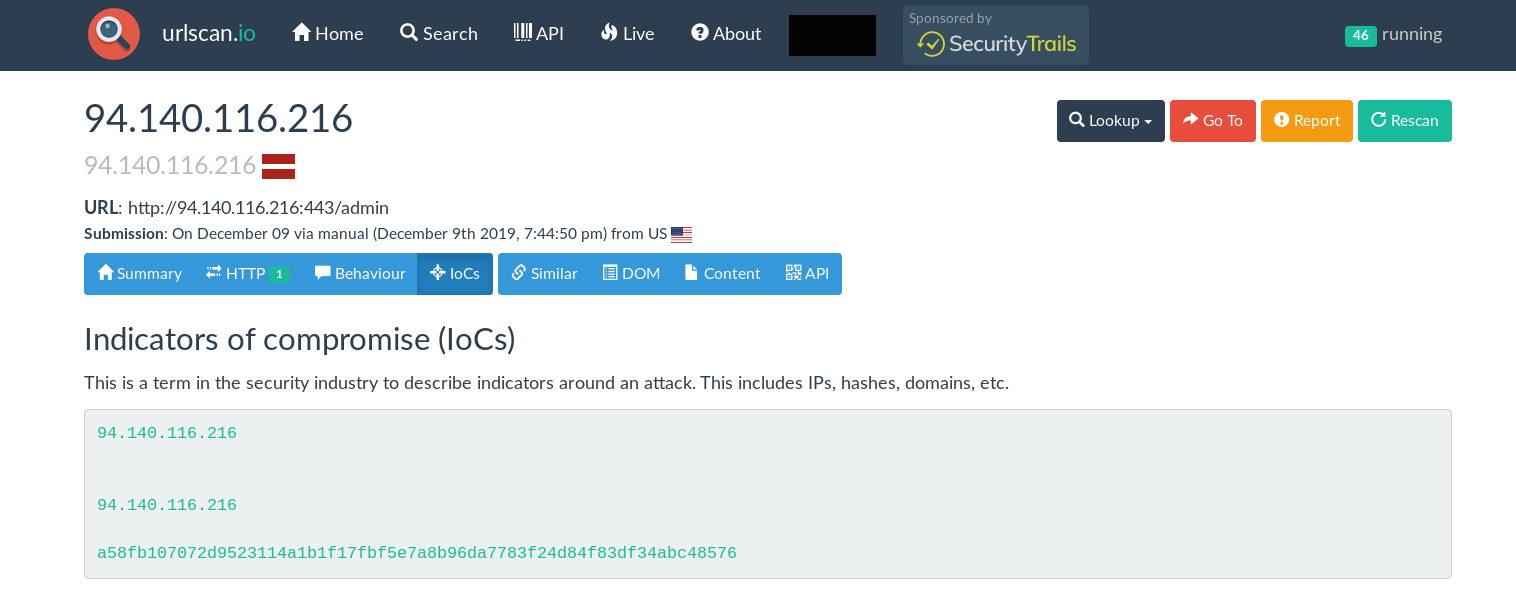
This led me to check the IoC page of the scan. Urlscan take a hash of all assets on the page it scans and drops them in the results that allow you to select and run searches to pivot on those indicators, which is exactly what I did here.
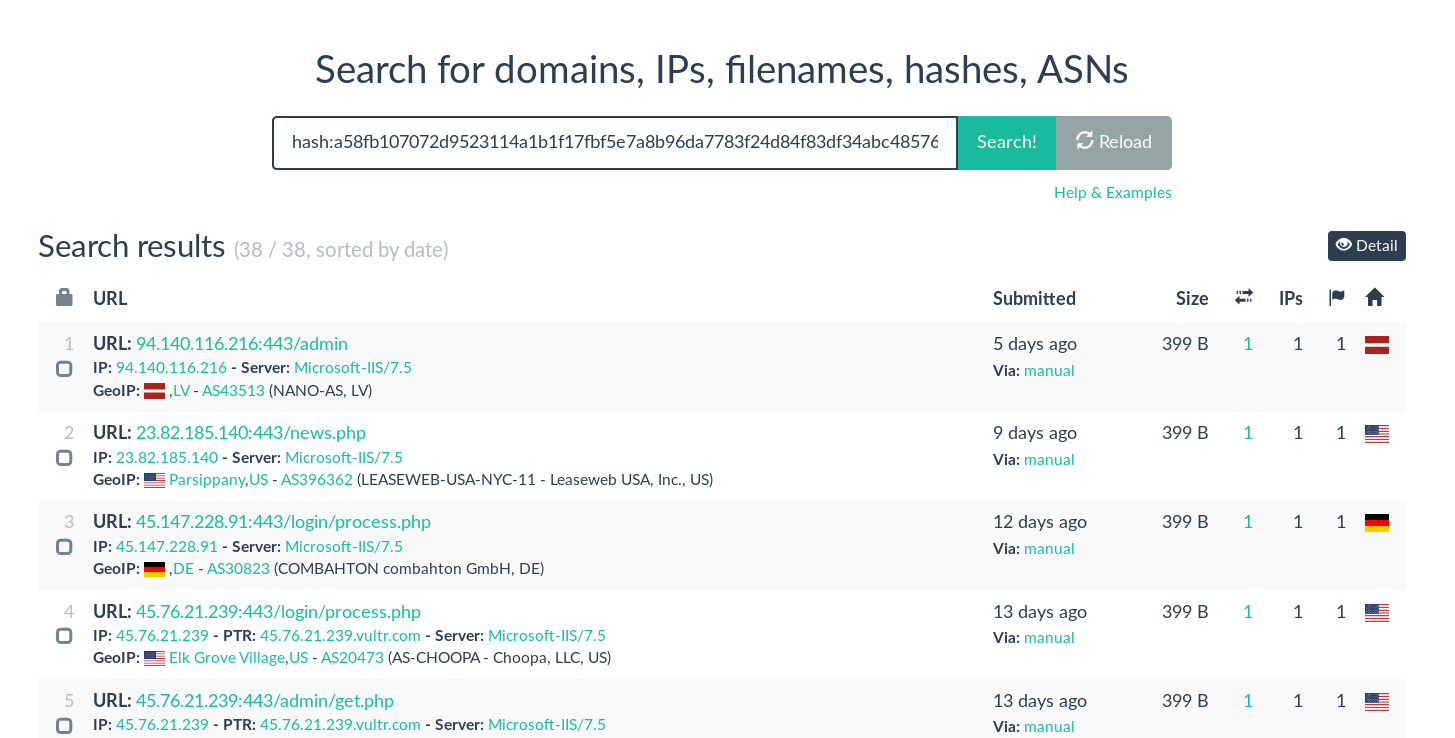
I used the sha256 hash of the page to search on and found that many other scans had the exact same hash and if you look at the URL’s present they match a default powershell empire c2’s with /admin and /login directories and news.php, get.php, and process.php being default uri enders for the c2 setup.
Urlscan includes a helpful search API so I collected that data via the API and stored it in a CSV after some json-fu.
Step 2 next pivot
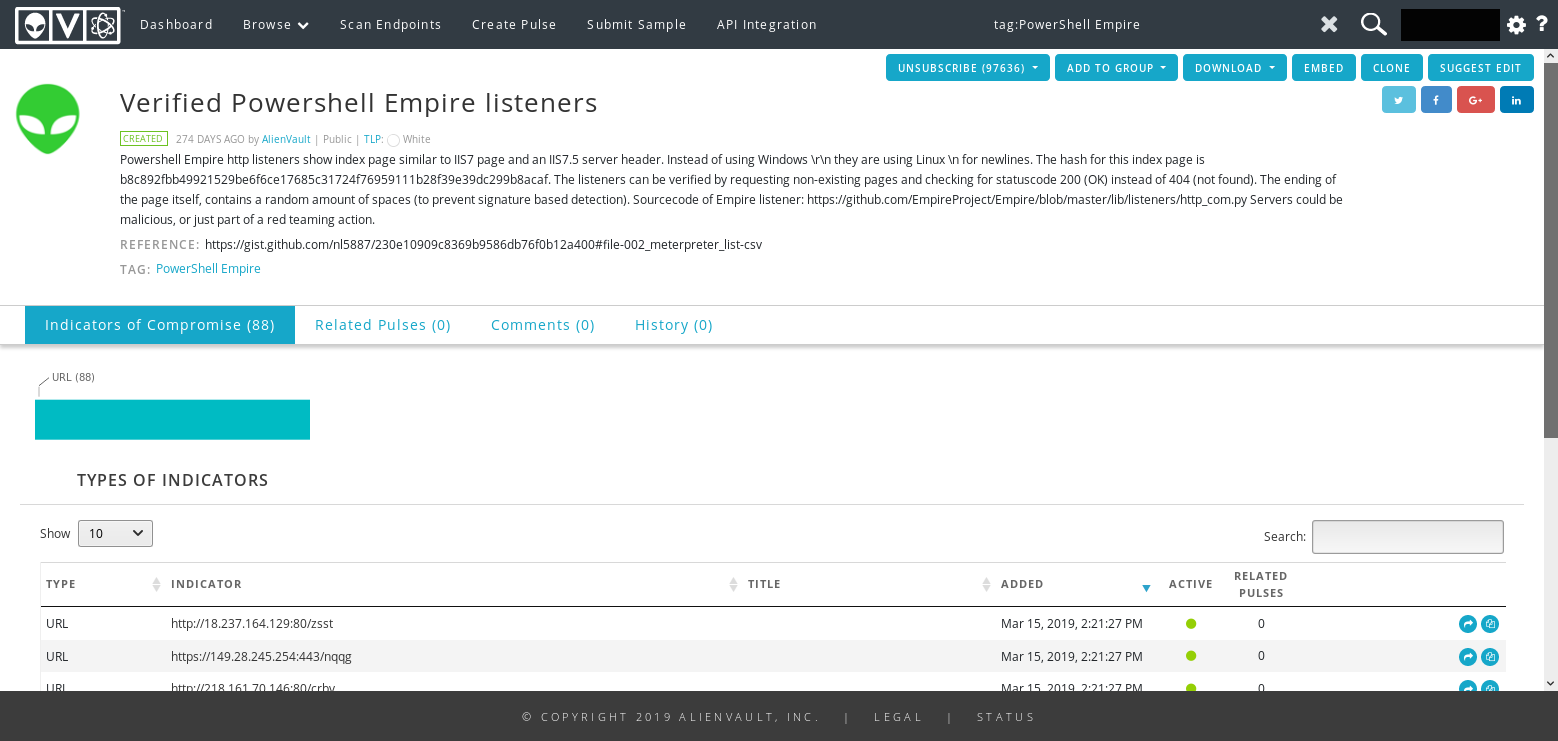
Next I wondered if I could get Empire c2 hits based on the c2 page I was familiar with…Turns out someone over at AlienVault had the same idea earlier in the year.
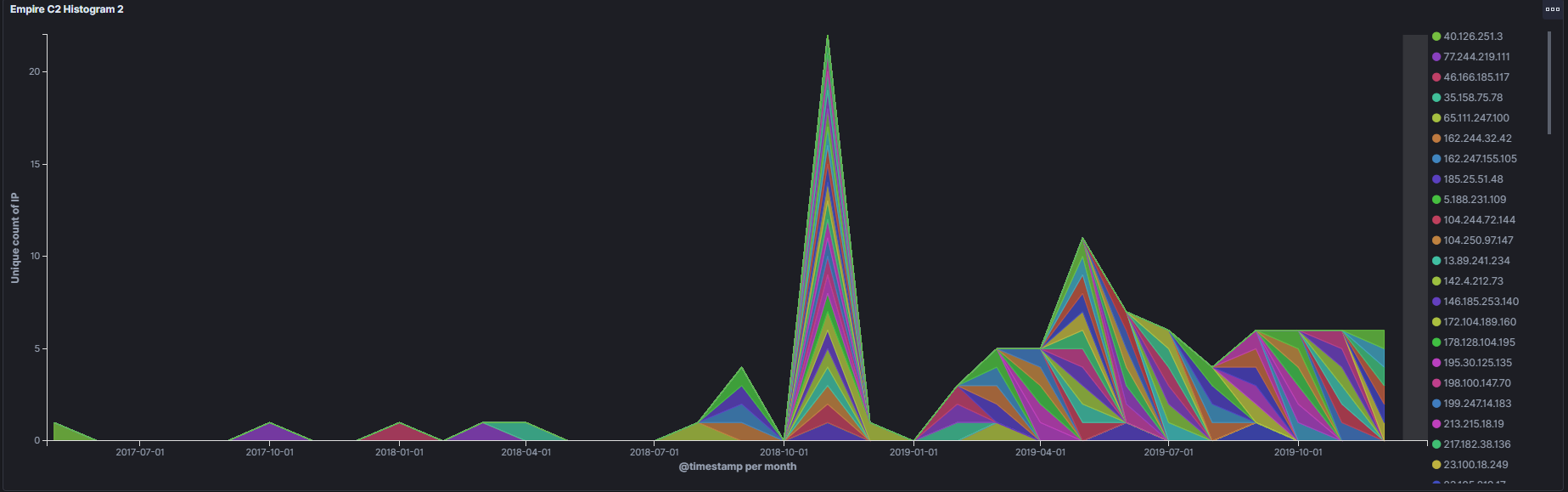
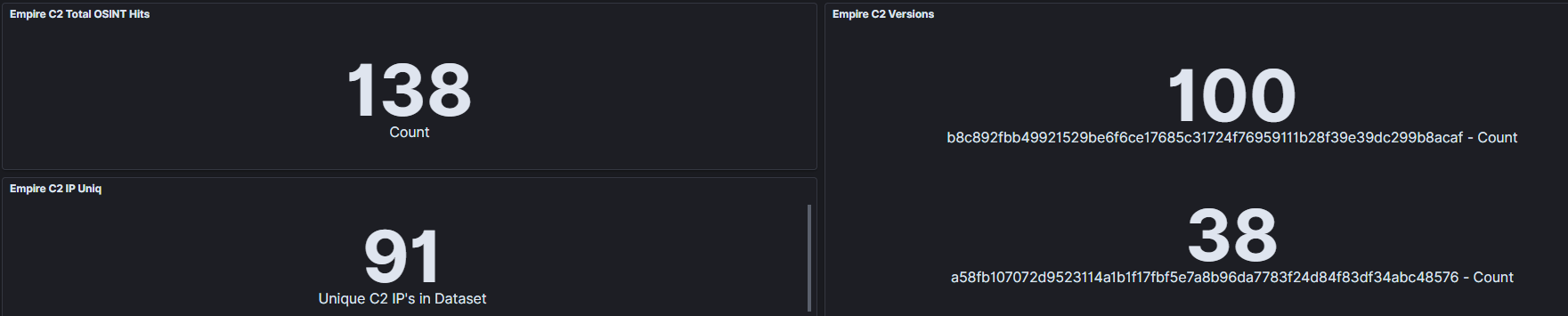
 Armed with the new hash I went back to UrlScan and ran another search with the 2nd hash. In total that revealed 138 results in the UrlScan dataset between the 2 Empire versions. there were 91 unique IP addresses and we can see that the tool is very much still in use by malicious actors today with several results in the past 2 weeks.
Armed with the new hash I went back to UrlScan and ran another search with the 2nd hash. In total that revealed 138 results in the UrlScan dataset between the 2 Empire versions. there were 91 unique IP addresses and we can see that the tool is very much still in use by malicious actors today with several results in the past 2 weeks.
Step 3, graph that data:
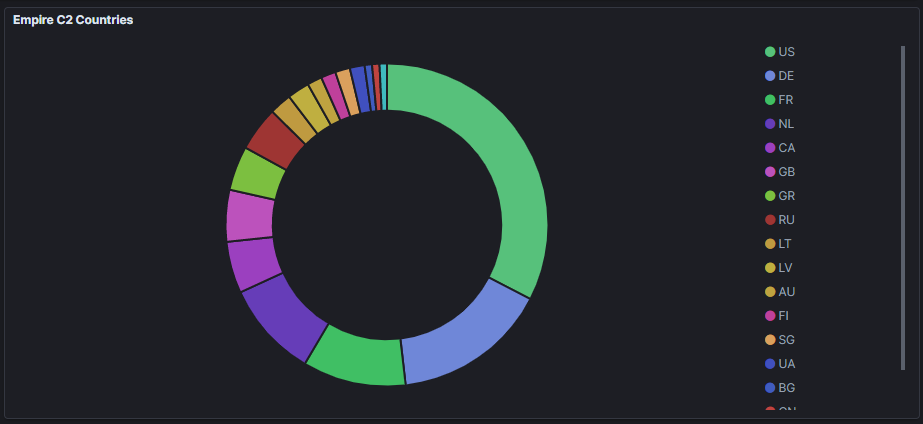
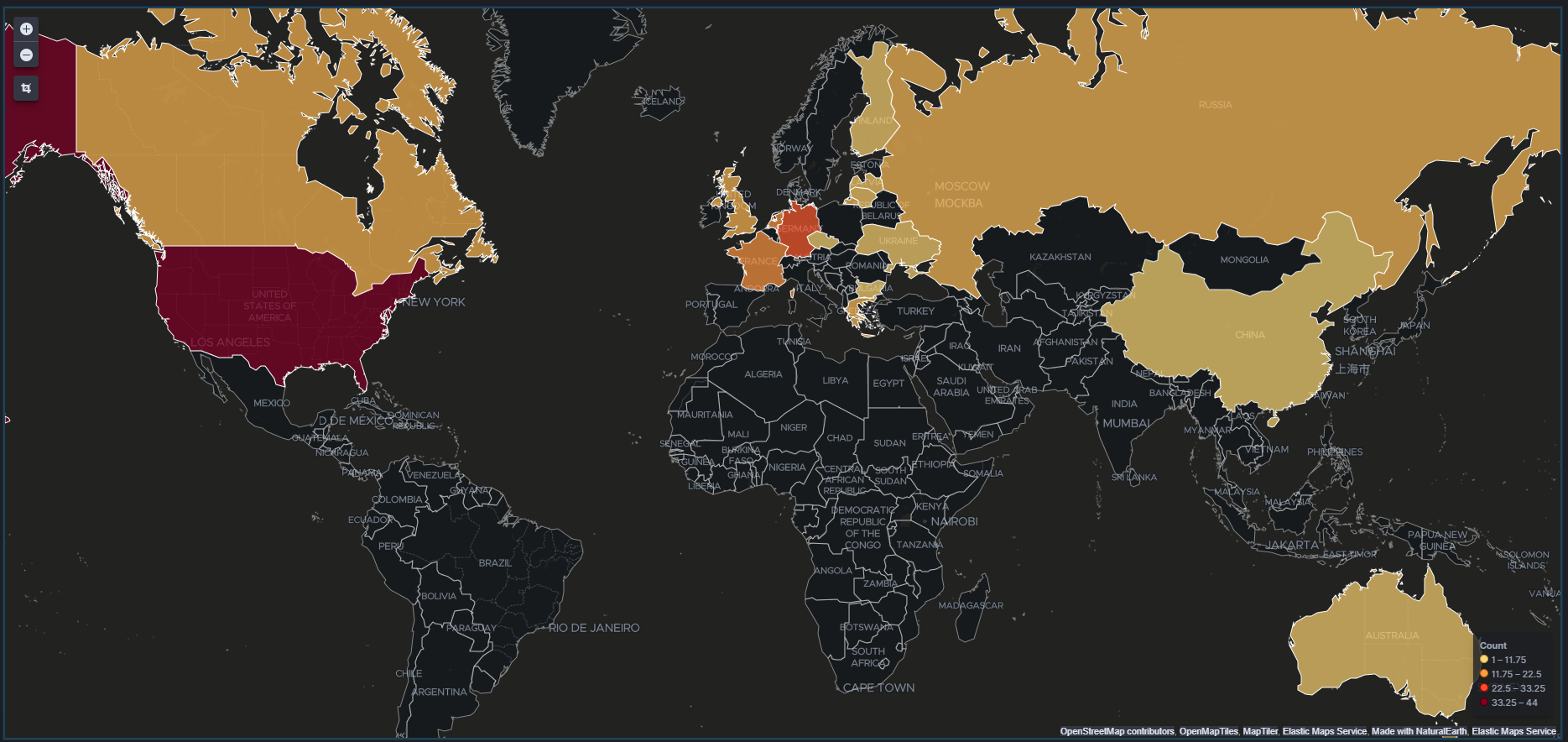 Geographically C2 is diverse with some favoritism to the United States, likely due to many data centers being based there, and perhaps to deter Geo-restrictions that may come with other Geo-locals.
Geographically C2 is diverse with some favoritism to the United States, likely due to many data centers being based there, and perhaps to deter Geo-restrictions that may come with other Geo-locals.
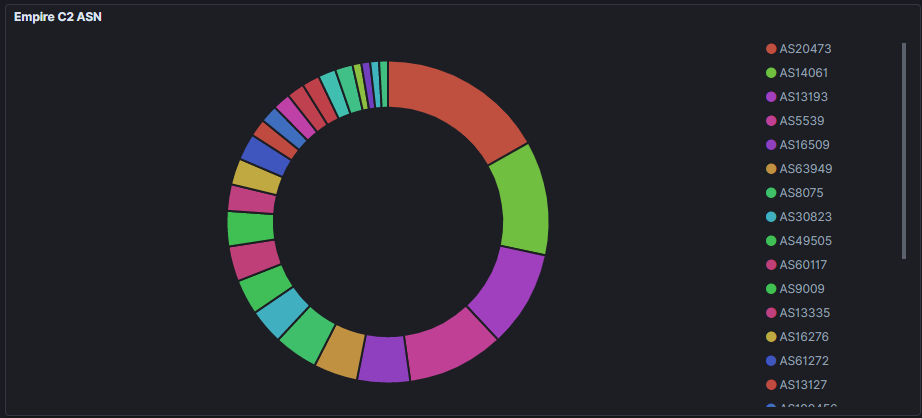
We see 4 ASN’s account for half of the hits in the dataset:
- Choopa AS20473
- DIGITALOCEAN AS14061
- NERIM AS13193
- SPACENET AS5539
To see the full list of IoC’s go grab the misp event on github.
https://github.com/Hestat/intel-sharing/blob/master/powershell-empire-12-16-19/misp.event.7941.json