So if you haven’t been here before, I’ve been looking into instances of malware using crypto-mining as a means of monetizing hacked servers on the network I work on. In that research, we found that compromised servers had been mining over $600,000 USD of Monero coins. With this kind of money in play, we expect to see a rise in this being used to monetize hacked systems.
You can read prior stories and see the data involved at the following:
With that in mind I have been working on a project to help detect these miners, and way to help prevent malicious mining. I am proud to announce the beta release of Minerchk. Minerchk takes the data gathered and put it to use in helping sysadmins, incident responder’s, and others track down crypto-mining in web servers. This tool is geared for use on Linux servers running Cpanel, Plesk, default Apache, or default Nginx. If you want to help your endpoints, take a peak at the snort and miner block lists in the github to perform some network level prevention.
Lets take a look at how it works:
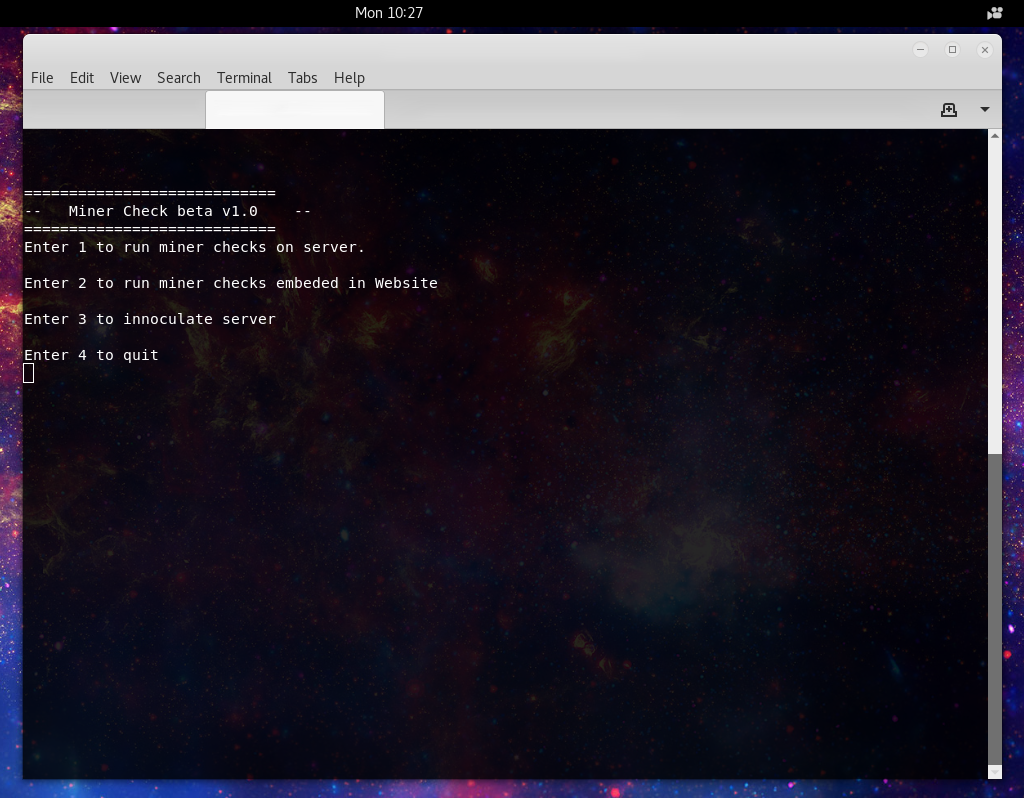
Step one pretty easy we have a nice little menu.
Now the next question we need to answer, what kind of action do we need to take. If we are seeing a lot of load on the server you’re going to want to run option 1. If you are seeing strange load on clients visiting the site, or received an alert from an outside scanner or party, you’re likely going to want to look into option 2. And if you are wanting to be proactive, or after cleaning up if you want to help prevent reoccurrence you’ll want to check option 3.
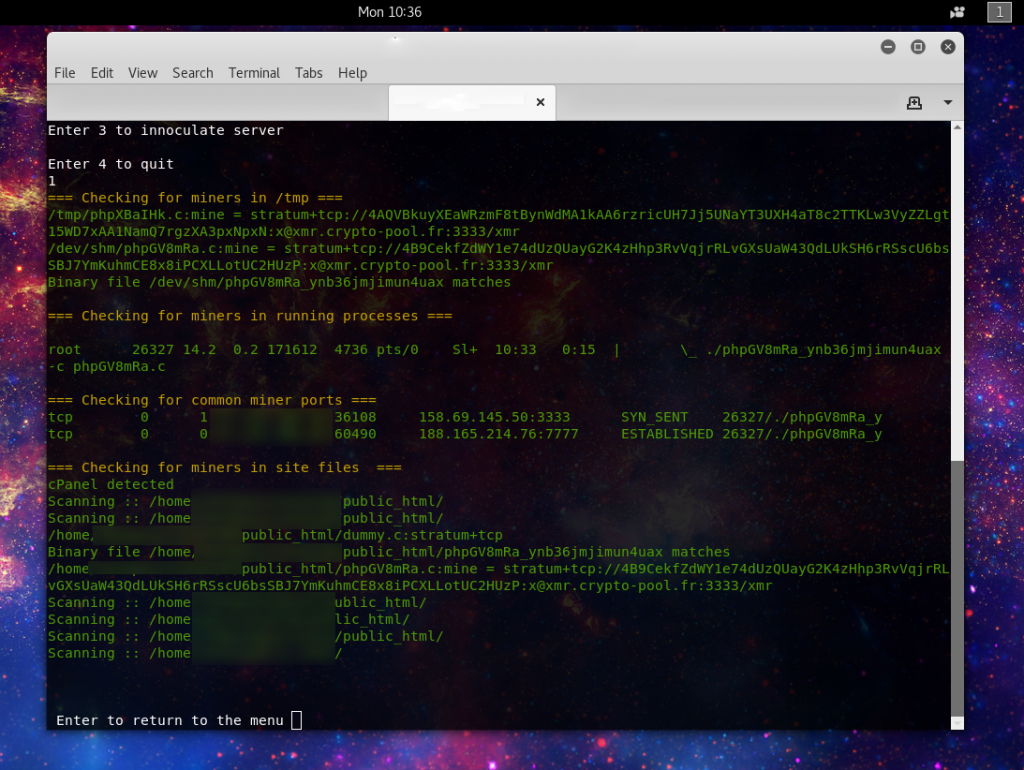
So lets look at what choice one provides:
Here we are looking for places in which mining on servers is most often deployed. First we check in the /tmp and /dev/shm as these are often used to hide from sit scans, and are easily access by the users of the running web processes. Next a check is run for any actively running miners looking at both known miner processes and network traffic using known mining ports. Finally a check is run in the website directories, this should scan based on the environment and can enumerate multiple sites on a single server.
Now what output do we see for choice 2:
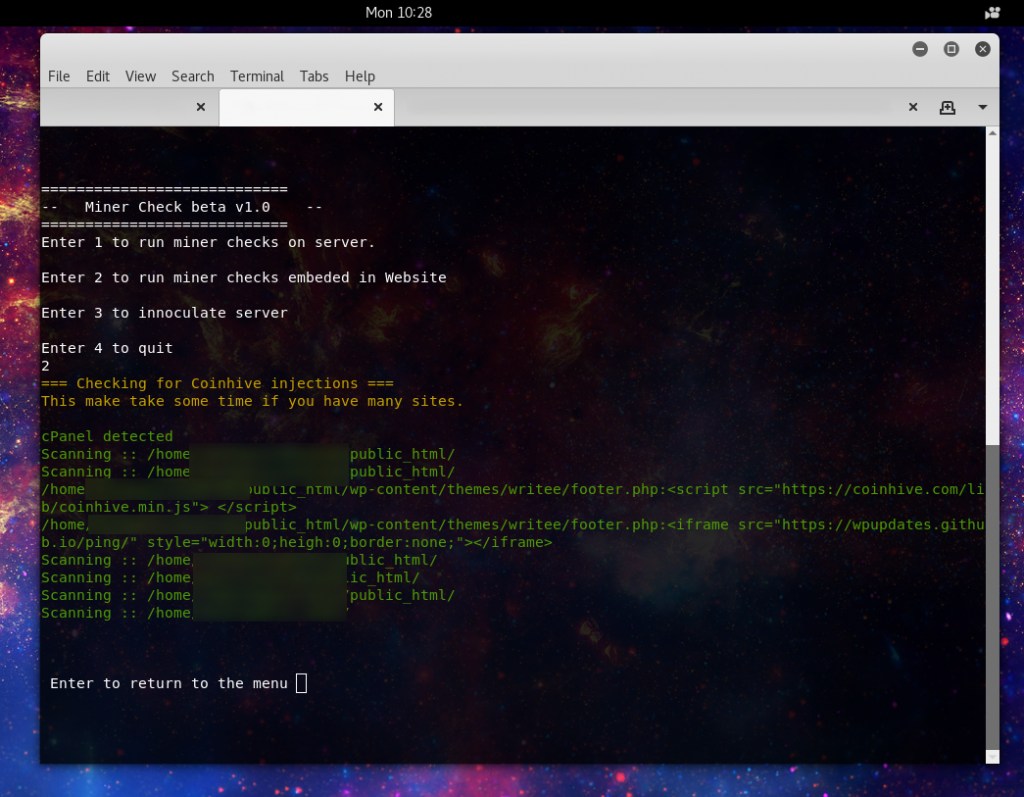
He we see the enumeration of web directories looking for injected javascript, which is the most common way to use a site to make endpoints perform the mining.
Now onto choice 3:
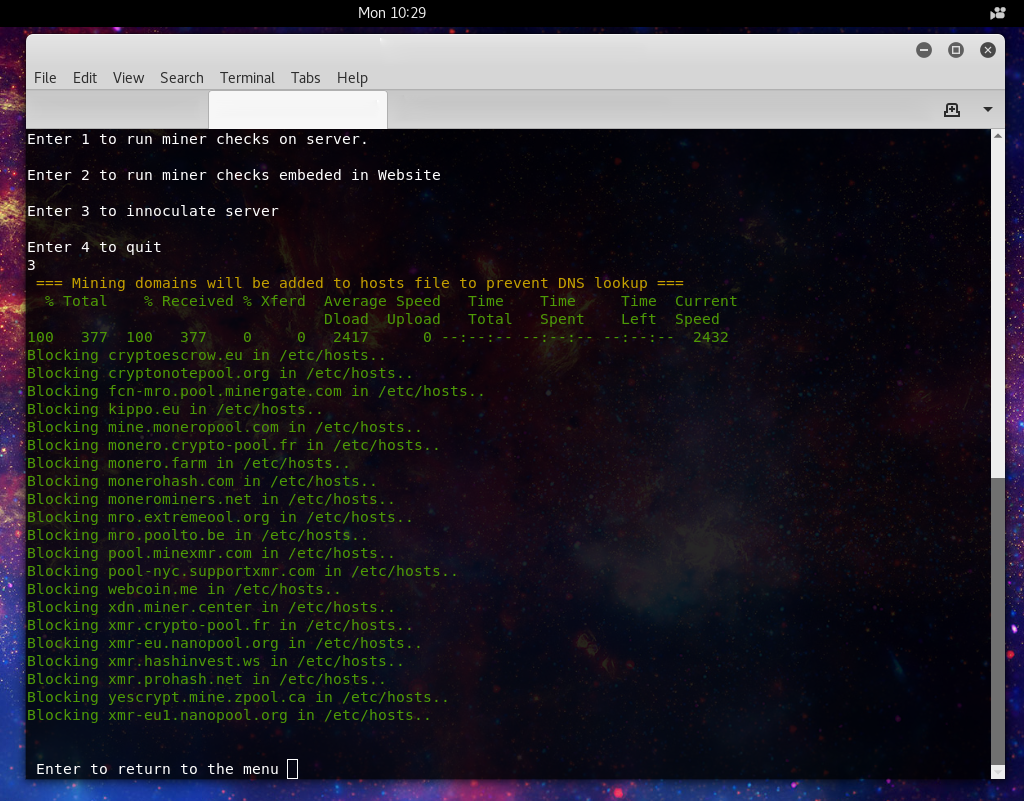
Here we add known mining pools to the servers host list, resolving to localhost, so if mining malware does get on the system there is a lower probability that the miner will be able to make a successful connection and start driving up load on the system. Another proactive measure that can be taken is to block outgoing connections to the standard mining ports, as different linux distro’s use different firewalls, I have not yet implemented any code to add firewall blocks, but feel free to add you own using the port list.
So, built into the script is checks back to the github repo so that signatures can be easily updated. You can view all signatures at the repo.
Possible plans for the future:
Add an update feature, either into the script, or perhaps investigate apt/yum packages.
Add automatic firewall port blocking to prevention features.
Cron, to automatically check and report findings via email.
Provide feedback @laskow26 on twitter, let me know if you found this helpful, provide samples you’ve seen, or what you might like to see.
Finally, thanks to Mark Cunningham for reviewing and providing some code to help keep things nice and efficient. Also remember, not a replacement for good security practices or traditional malware scanning tools.