Hello there interwebs. If you don’t know or perhaps if you do I’ve been working on a project to assist Incident Responders and Systems Administrators detect and remediate malicious cryptomining. Development has come quite away since the first beta release. So since there have been so many improvements, lets go over the program in its current state.
First thing to update installation instructions, to install:
git clone https://github.com/Hestat/minerchk.git cd minerchk/ ./install.sh
With a good install you should see the following:
root@ubuntu-malware:~/minerchk# ./install.sh Installing minerchk '/root/minerchk/minerchk.sh' -> '/usr/local/minerchk/minerchk' '/root/minerchk/ip-only.txt' -> '/usr/local/minerchk/ip-only.txt' '/root/minerchk/miners.yar' -> '/usr/local/minerchk/miners.yar' '/root/minerchk/remotelog' -> '/usr/local/minerchk/remotelog' Install Complete
If already installed:
root@ubuntu-malware:~/minerchk# ./install.sh Minerchk is already installed, if you want to update use option 5 in the script
Once installed you can then run with a simple:
root@ubuntu-malware:~# minerchk
Okay lets run down what happens next. On running minerchk will confirm its signatures and IP lists and the script itself are up to date:
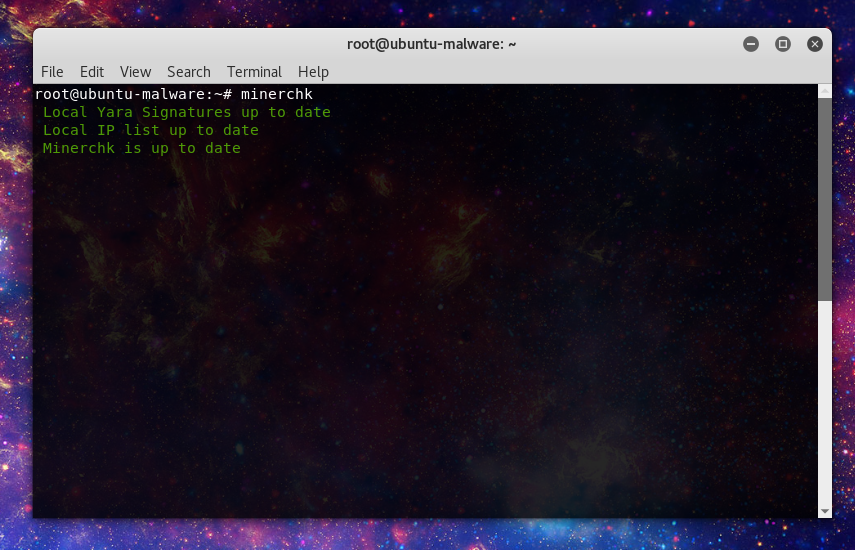
If the signatures are not up to date it will automatically update those. If the script itself is not up to date then it will alert the user and point them to option 5 in the menu to perform an update.
Next let’s look at an overview of the menu:
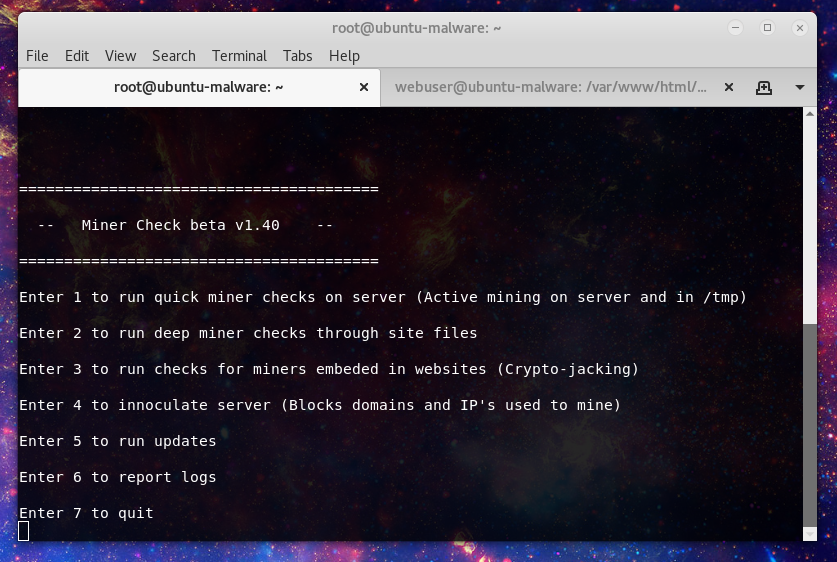
Option 1 is the first go to if you think that there is active mining on the server. One of the new features is if ClamAV is installed it will use that along with YARA signatures to scan for evidence of miner files. as well active miner checks now use IP database on mining pools known to be used by malicious actors to identify active mining.
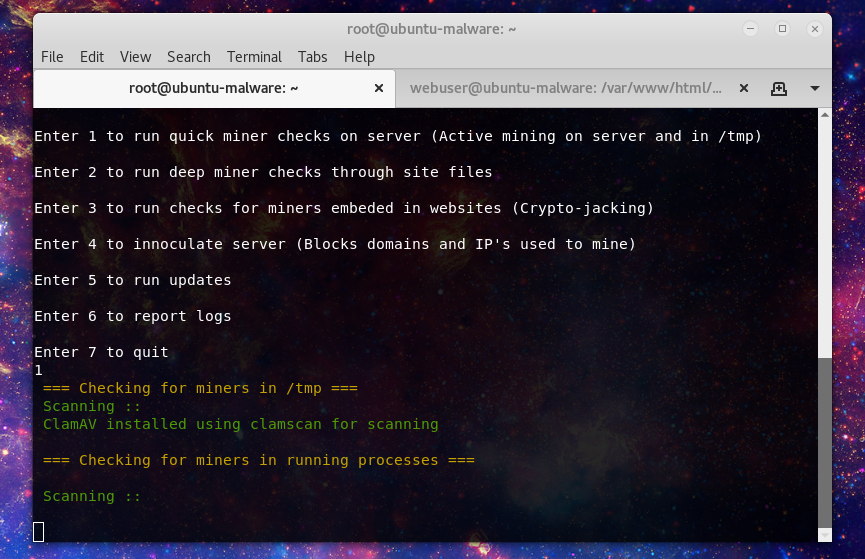
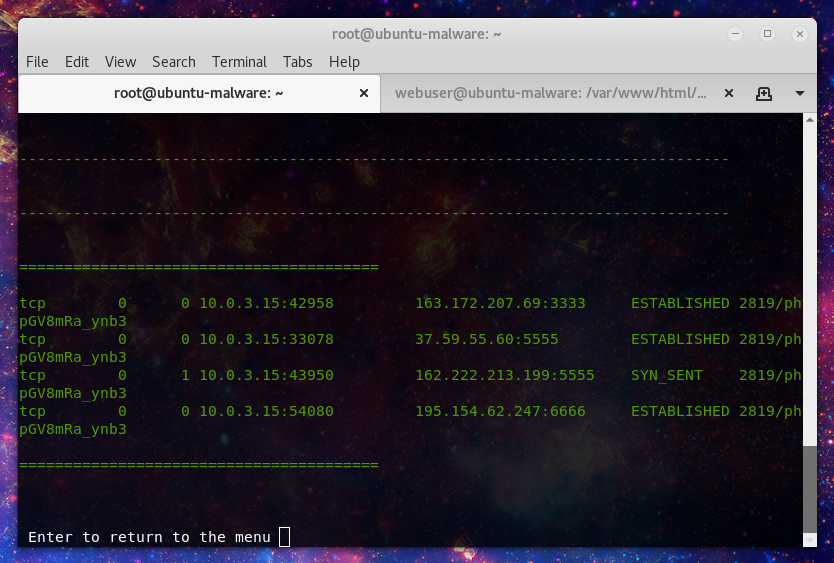
Now not all mining is run in tmp, or if you have cleaned up the initial malware, you may want to run a more broad scan. Option 2 will look through website directories and user home directories:
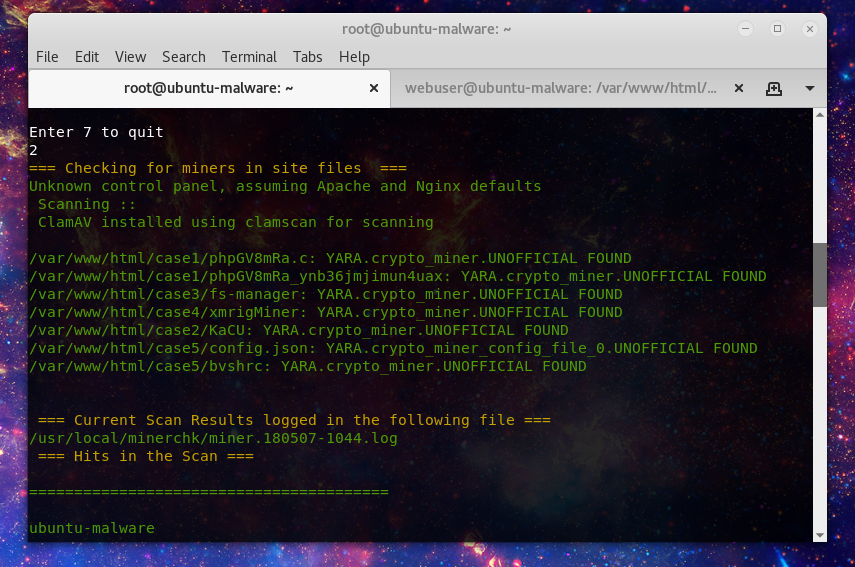
Option 3 will look for in browser mining injected in to website files.
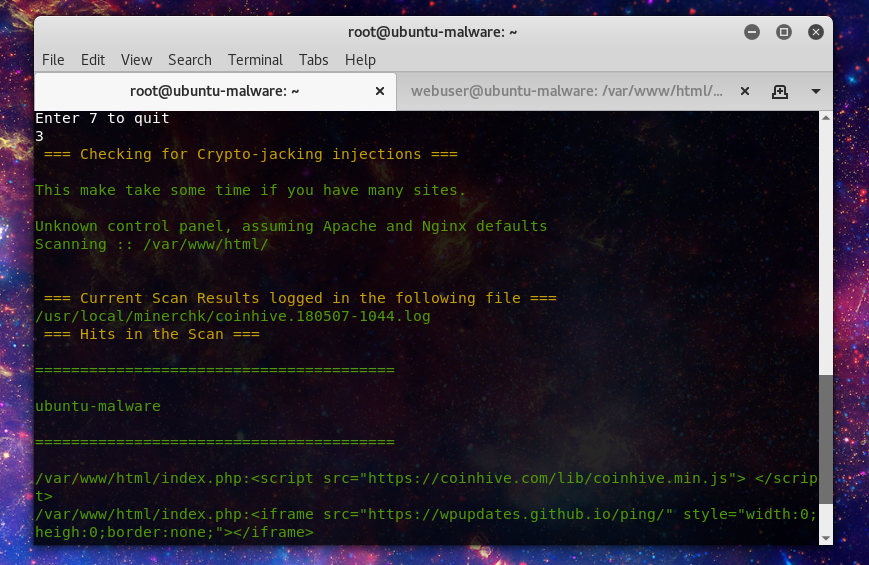
Option 4 will block mining pool IP’s or domains. If the server is using the Config Server Firewall package it will take advantage of the csf.blocklists fesature, otherwise it will use the /etc/hosts file to route the mining pool domains to localhost.
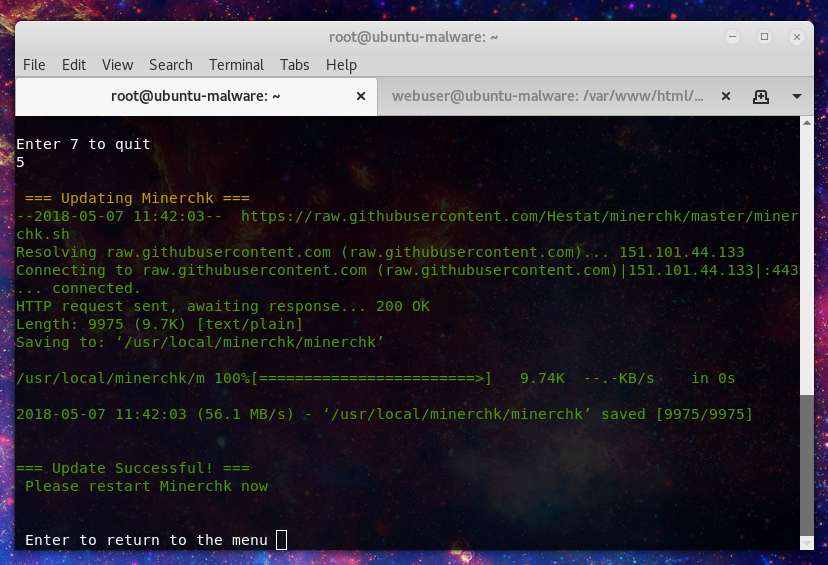
Option 5 runs the update routine for the script:
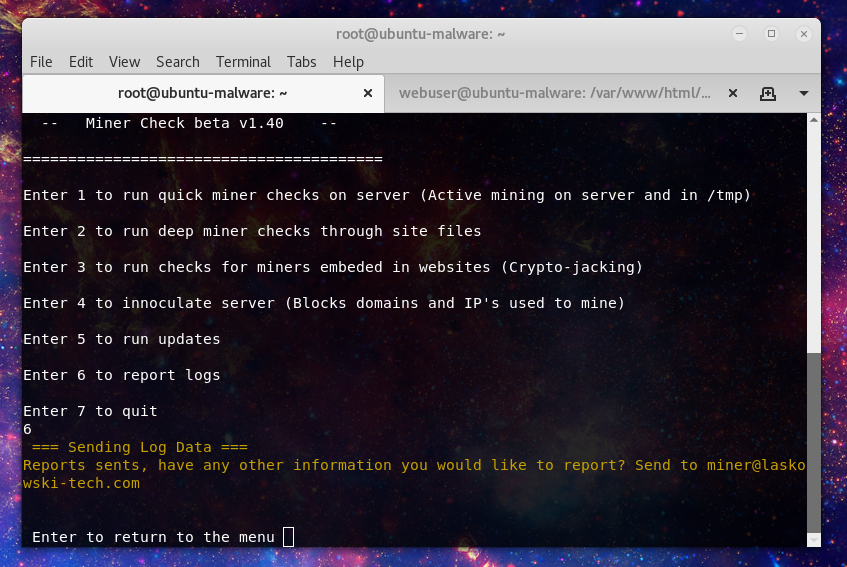
Option 6 will send anything caught in the current scan to a remote mail address, by default the miner address I have set, but you can change this by editing file:
root@ubuntu-malware:~# cat /usr/local/minerchk/remotelog miner[@l]askowski[-]tech[.]c o m
That should be enough to get you started check out other crypto-miner writeups here:
https://laskowski-tech.com/category/cryptomining/
Have questions or comments hit me up on twitter @laskow26.