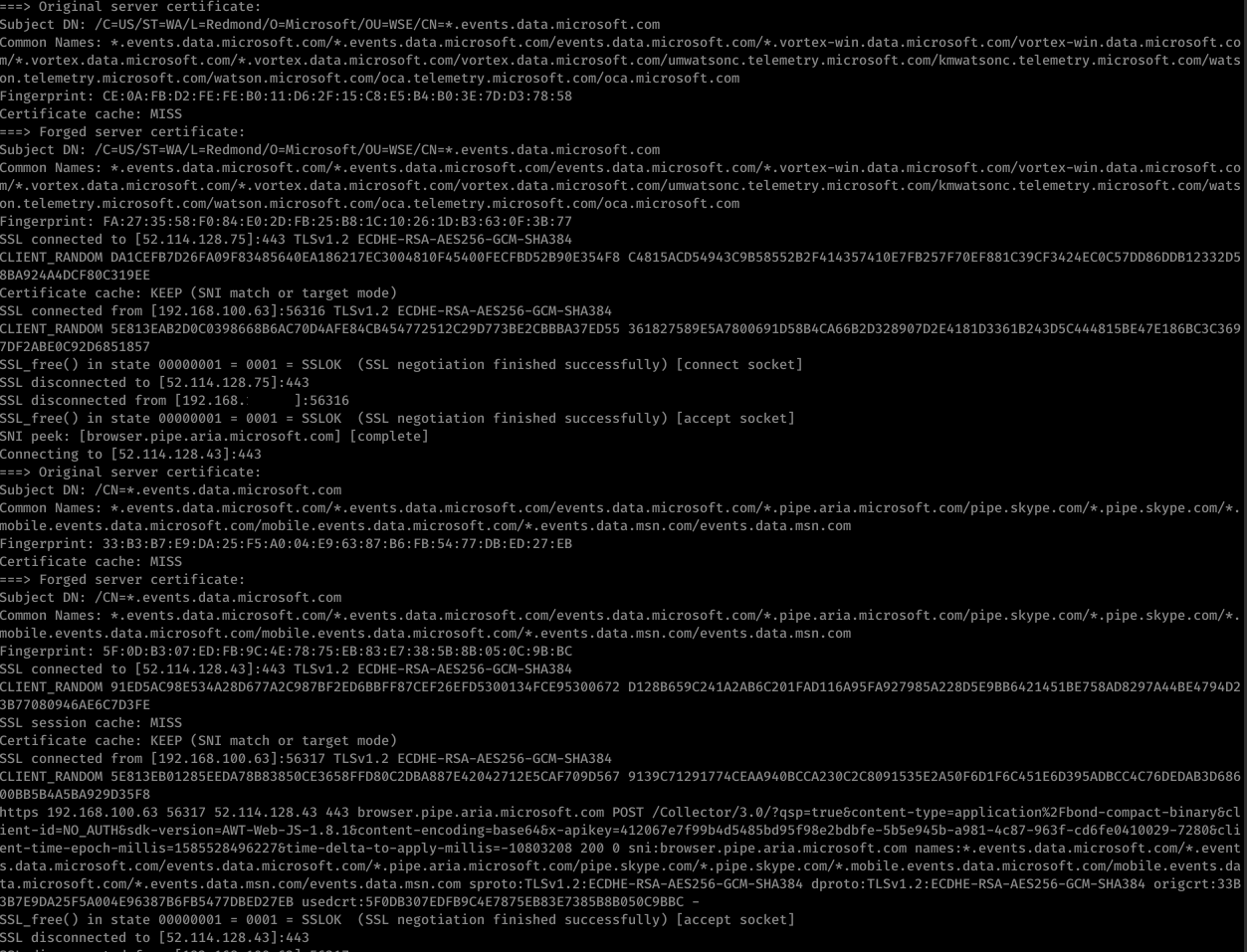
Today as more and more traffic continues to move to a encrypted world you might think that traditional NSM (Network Security Monitoring) has gone out the window. There is a good deal of truth to that and that has made things like
Read More
So if you talk to most infosec professionals I think you find most would agree that malware goes in and out of fashion, back in 2016 ransomware was hot, at the end of 2017 cryptominers were everywhere. Today I don’t think many
Read More
Originally published at Eforensics magazine: Today when you look at the market of malware you will find an overwhelming domination of malicious windows software. So looking for security products you can find many that exist for Windows, and write up after write
Read More
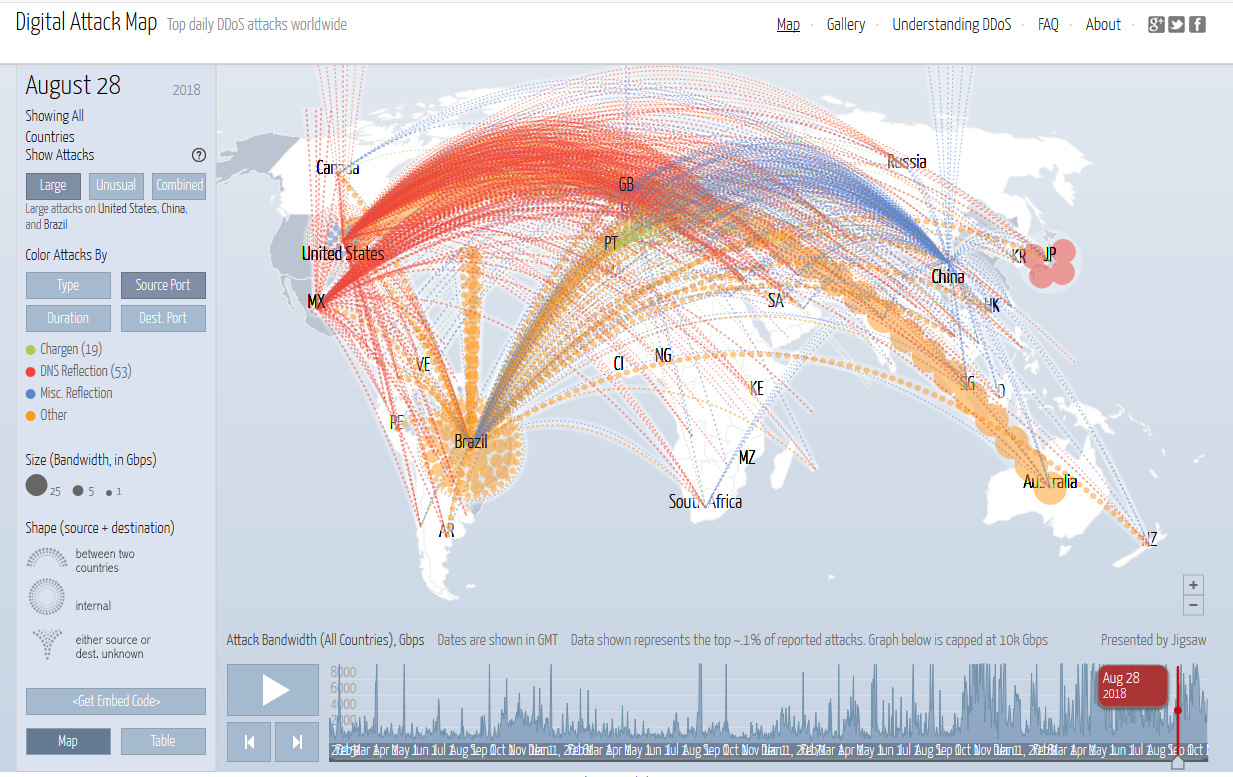
Or how your sever gets used in a reflective DDOS, an anecdote… So many platitudes in the infosec community go : As a defender you need to be right 100% of the time, the attack only needs to get it right
Read More
So back in the day I began working with OSSEC, the open source host based intrusion detection system. OSSEC has been running sonce around 2008, and been shepherded by Trend Micro since 2009. I ran the base package for some years, but
Read More
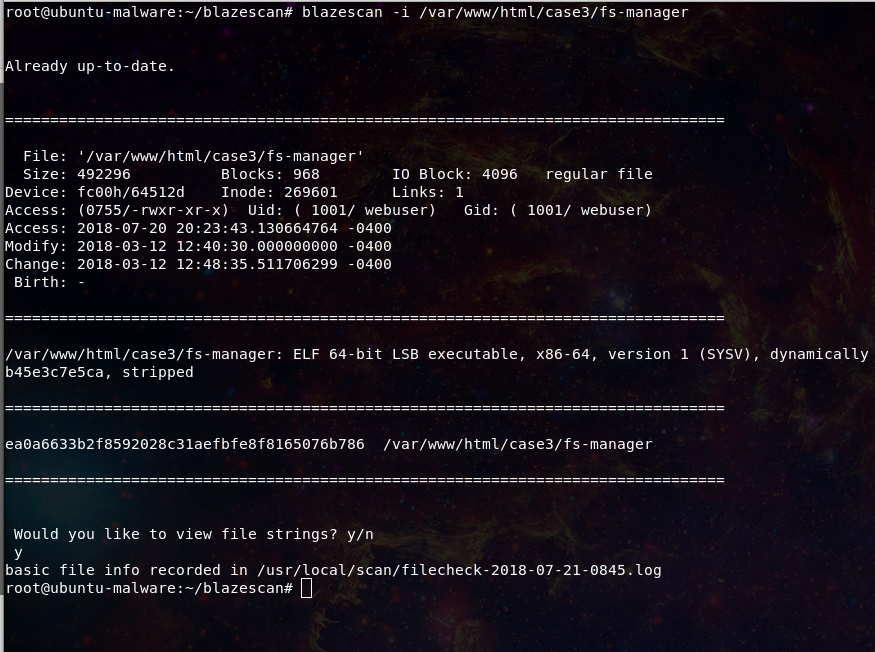
Update time, I added a few additional features to blazescan. One requested feature was the ability to email a report produced by blazescan, this has been added to the -m flag. The mail address is set in the blazescand.conf file: Additionally a
Read More
So I am speaking again, this time I am presenting on my workflow for incident response using free and open source tools. I’ll update this after the talk but for those attending here is the link to the slides: https://laskowski-tech.com/downloads/FOSSv1.pdf
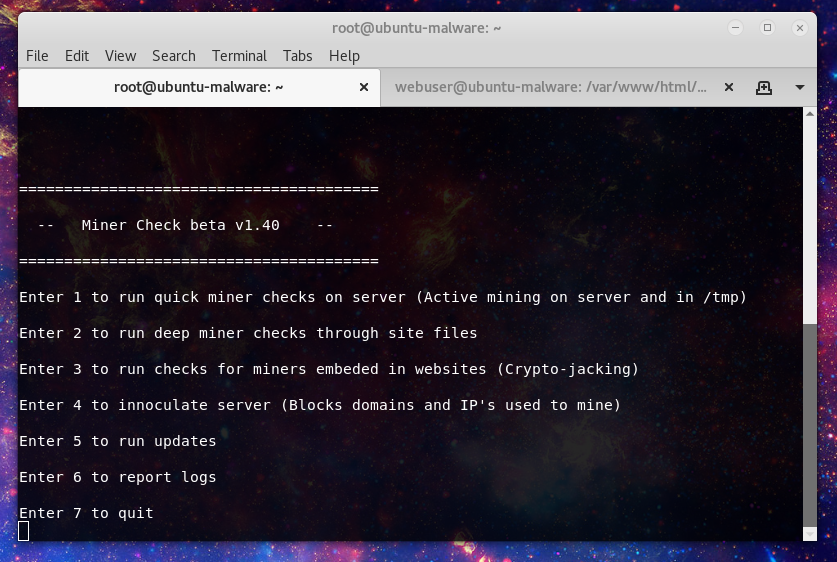
Hello there interwebs. If you don’t know or perhaps if you do I’ve been working on a project to assist Incident Responders and Systems Administrators detect and remediate malicious cryptomining. Development has come quite away since the first beta release. So since
Read More
So if you haven’t been here before, I’ve been looking into instances of malware using crypto-mining as a means of monetizing hacked servers on the network I work on. In that research, we found that compromised servers had been mining over
Read More
One of the biggest issues in many organizations is lack of detection capabilities of lateral movement. We all know the breach will happen at some point, but the real question is will you know when it happens? Most data we have is
Read More